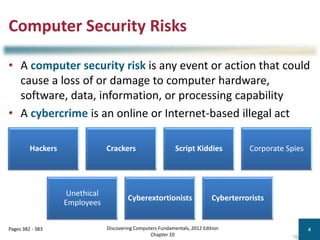
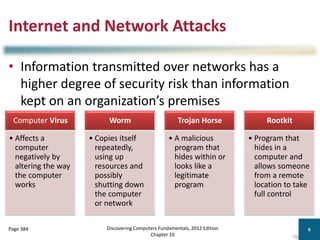
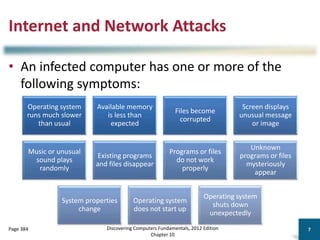
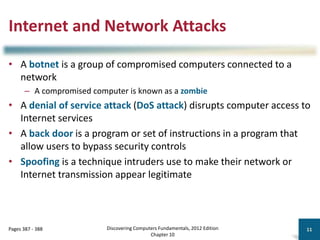
Module-8-Introduction-to-Cloud-Computing (1).pdf Module-8-Introduction-to-Cloud-Computing (1).pdf Module-8-Introduction-to-Cloud-Computing (1).pdf Module-8-Introduction-to-Cloud-Computing (1).pdf Module-8-Introduction-to-Cloud-Computing (1).pdf Module-8-Introduction-to-Cloud-Computing (1).pdf