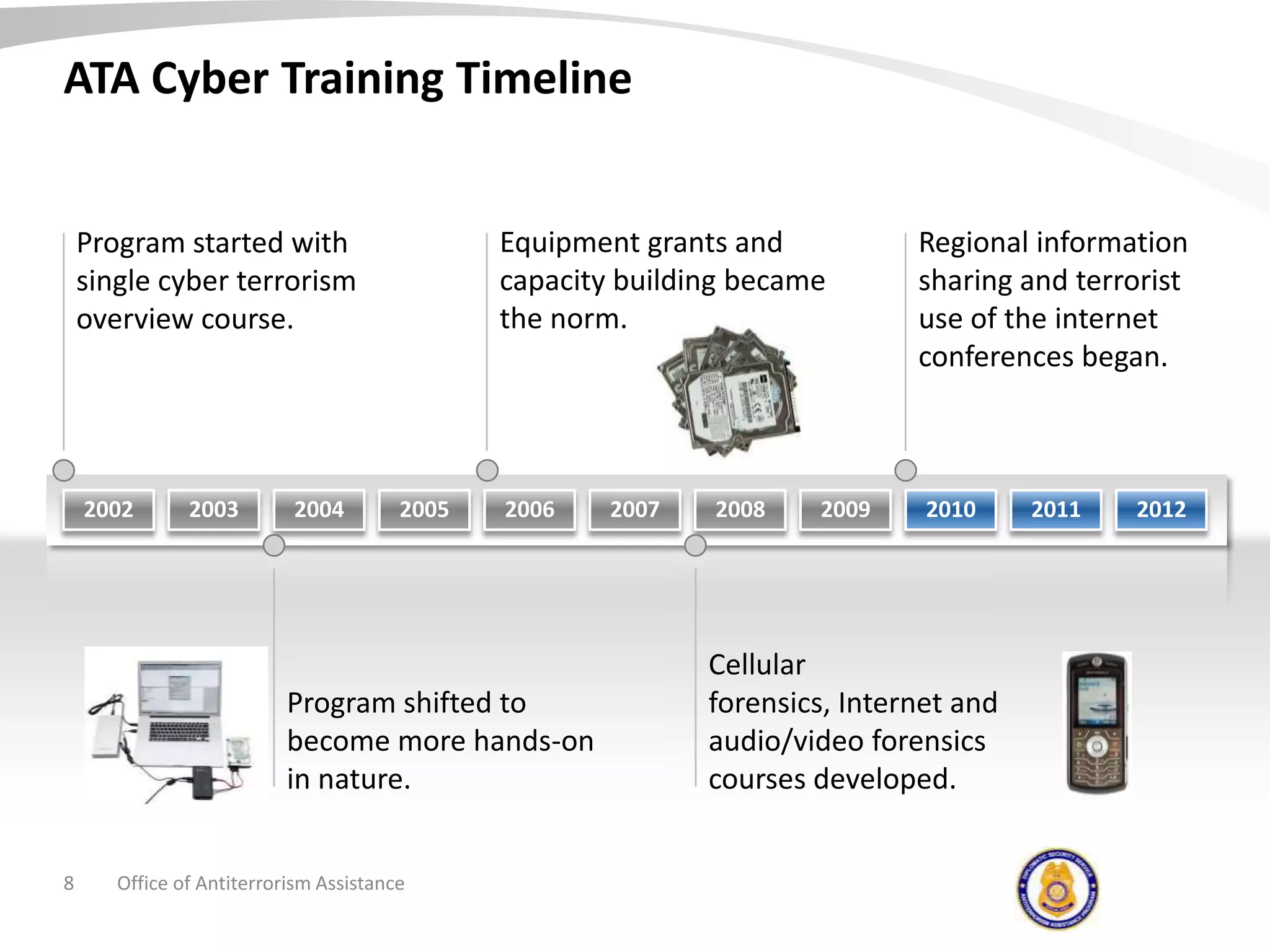
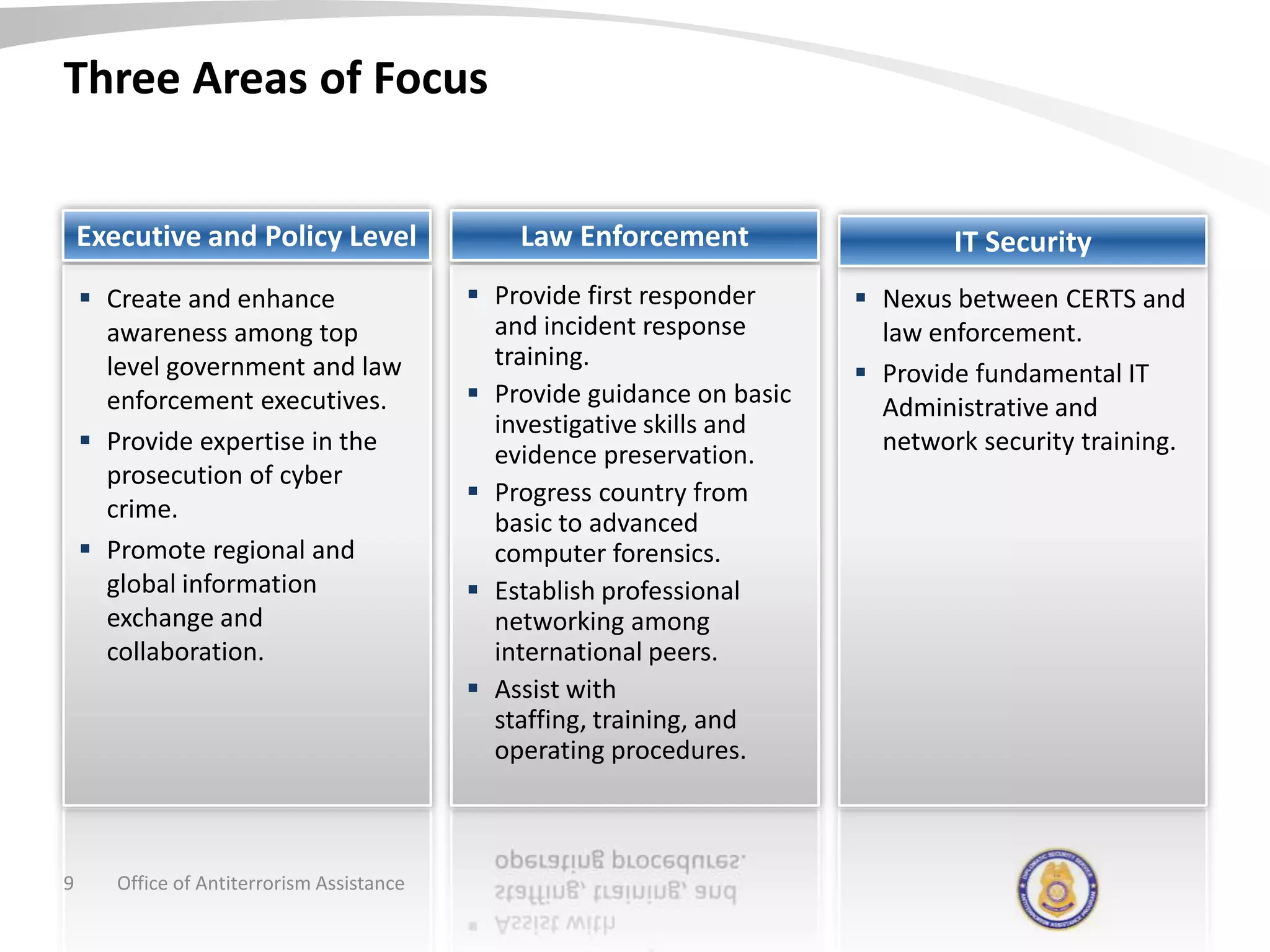
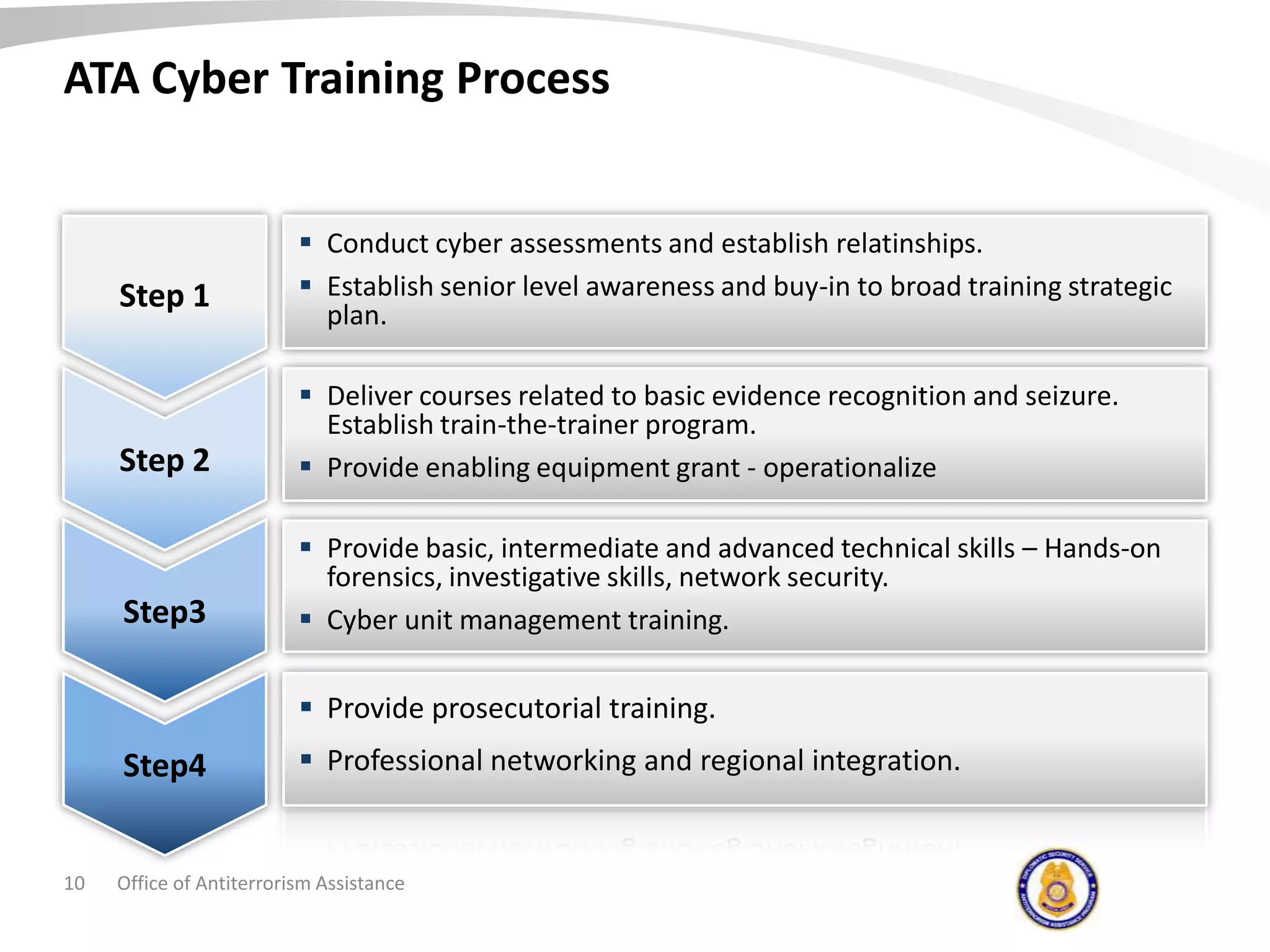
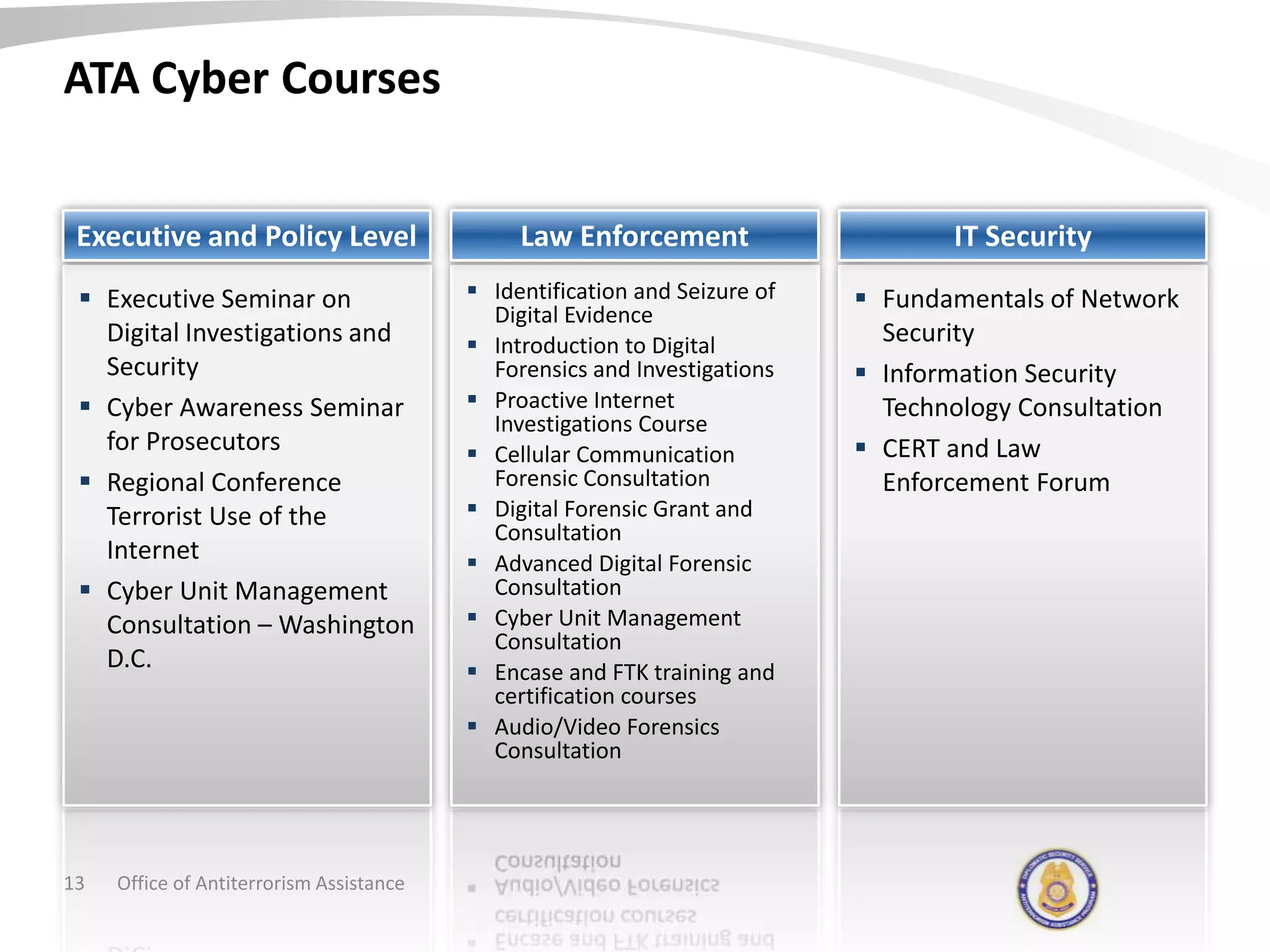
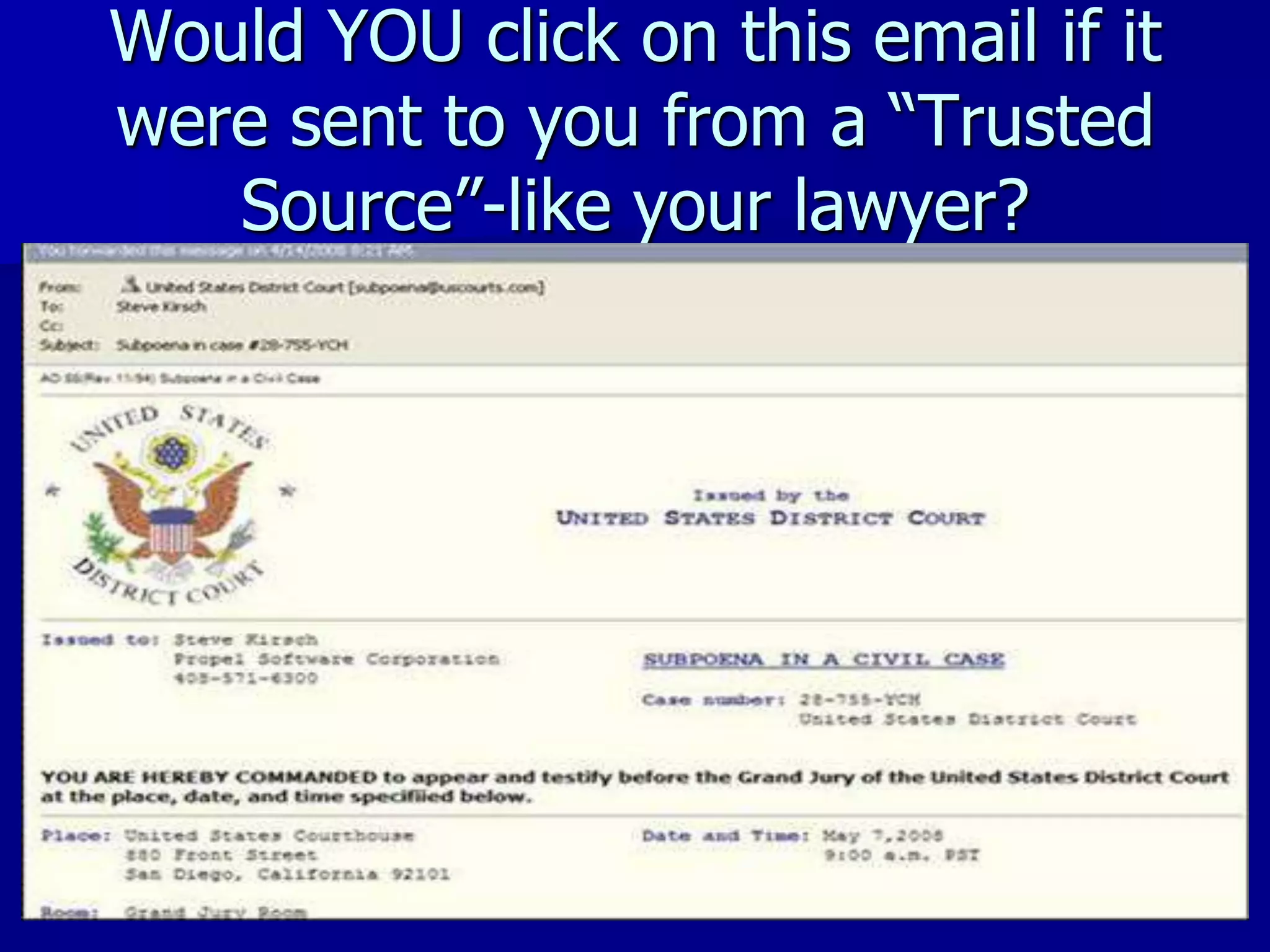
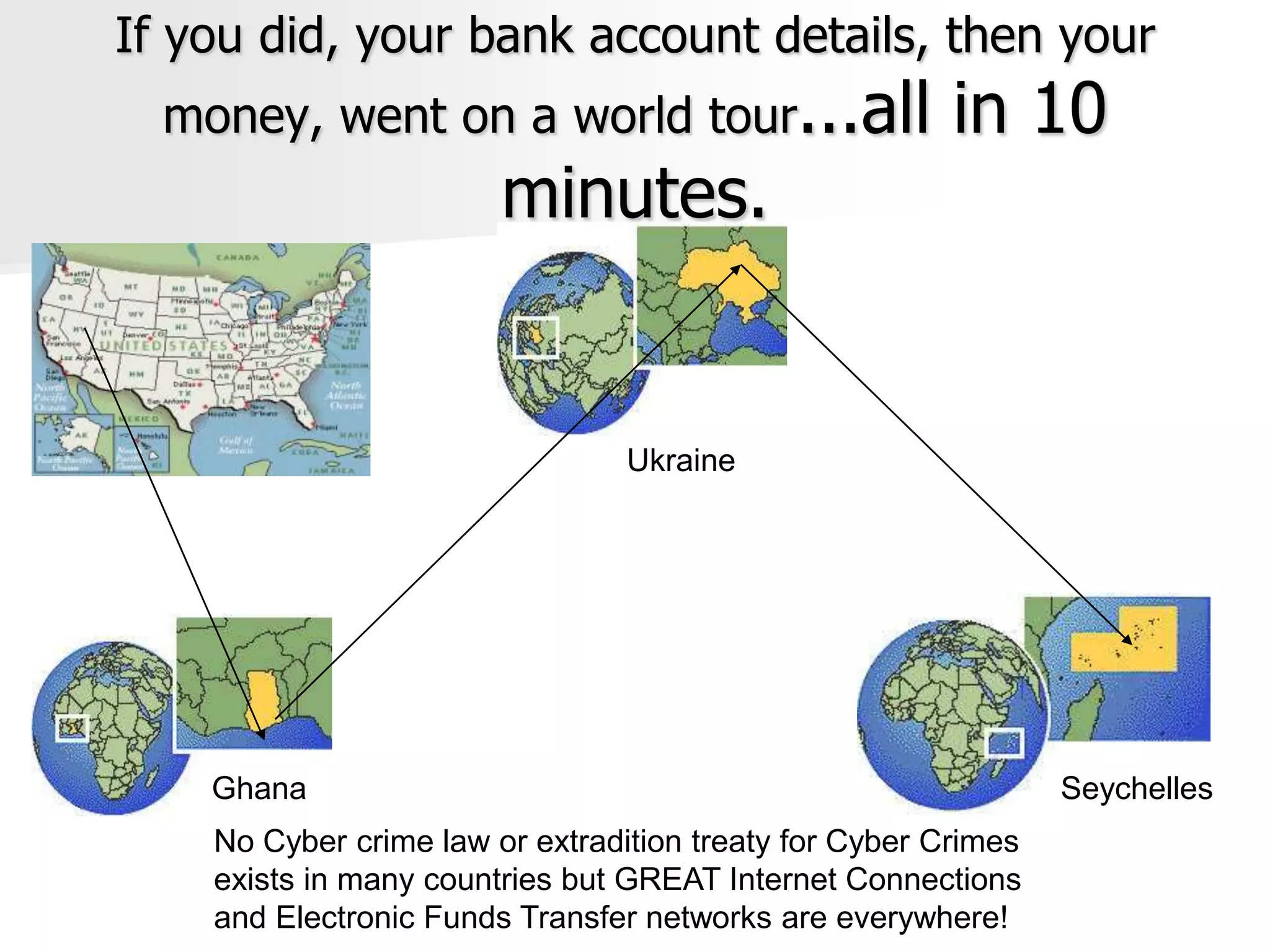
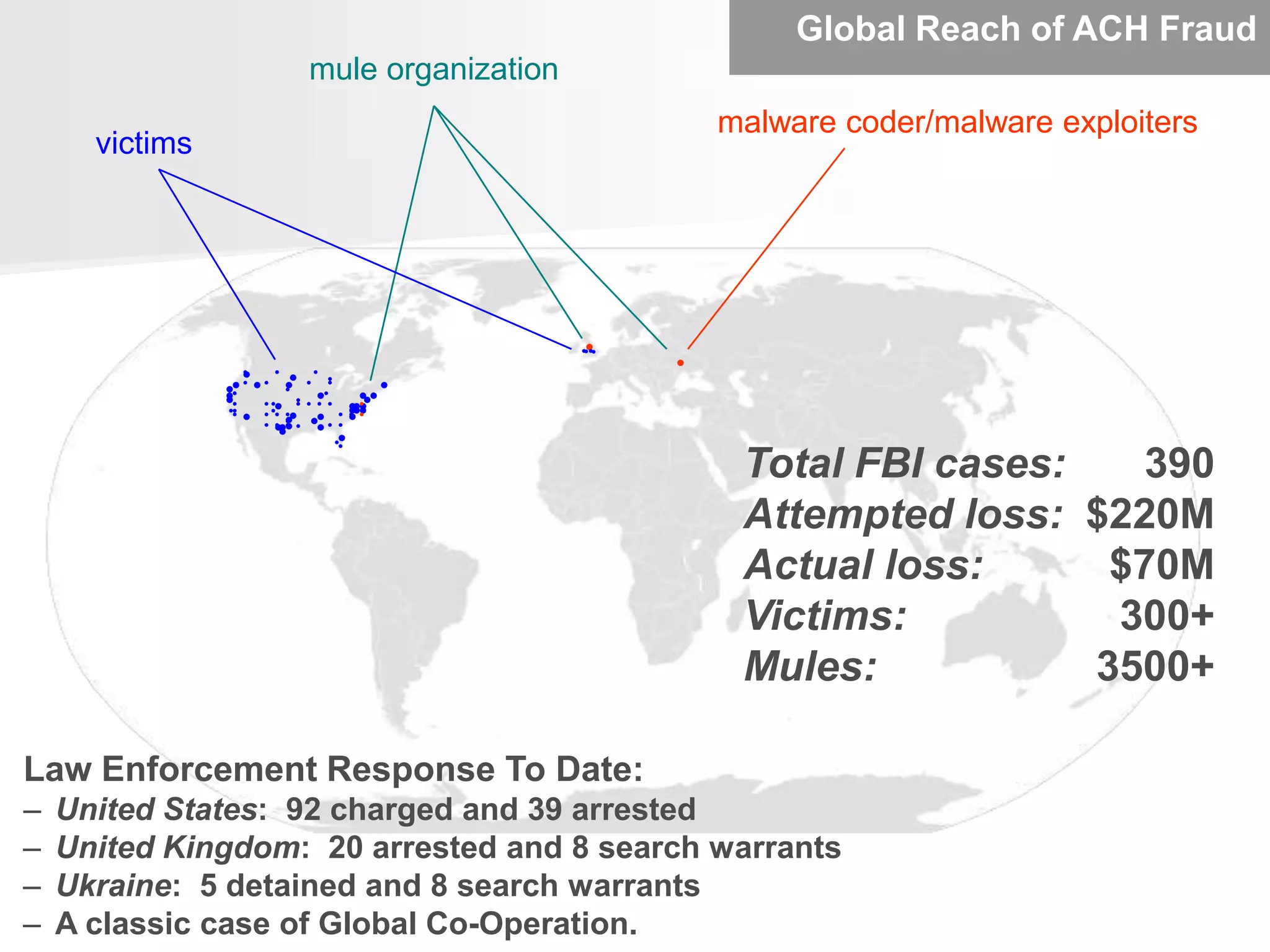
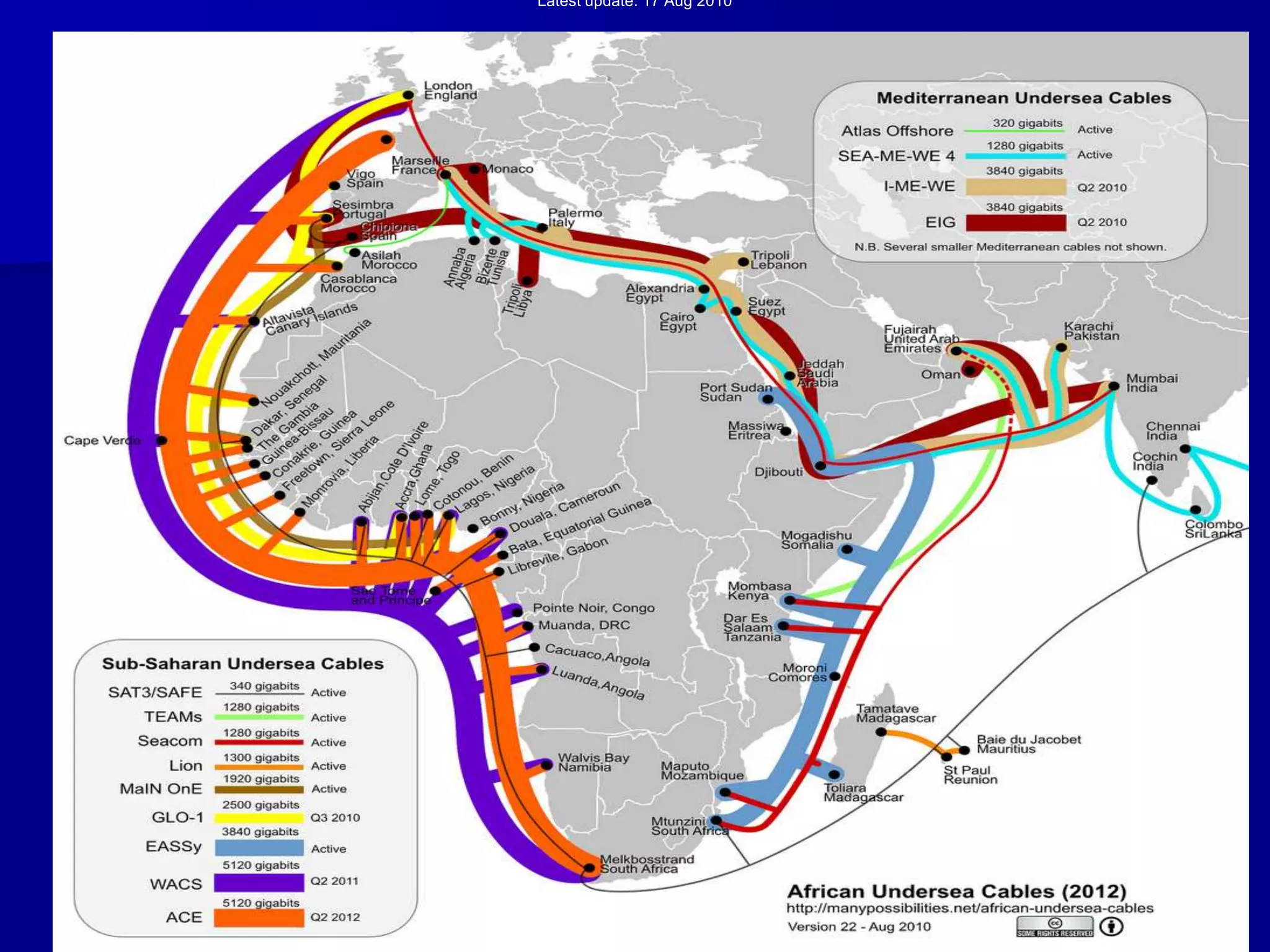
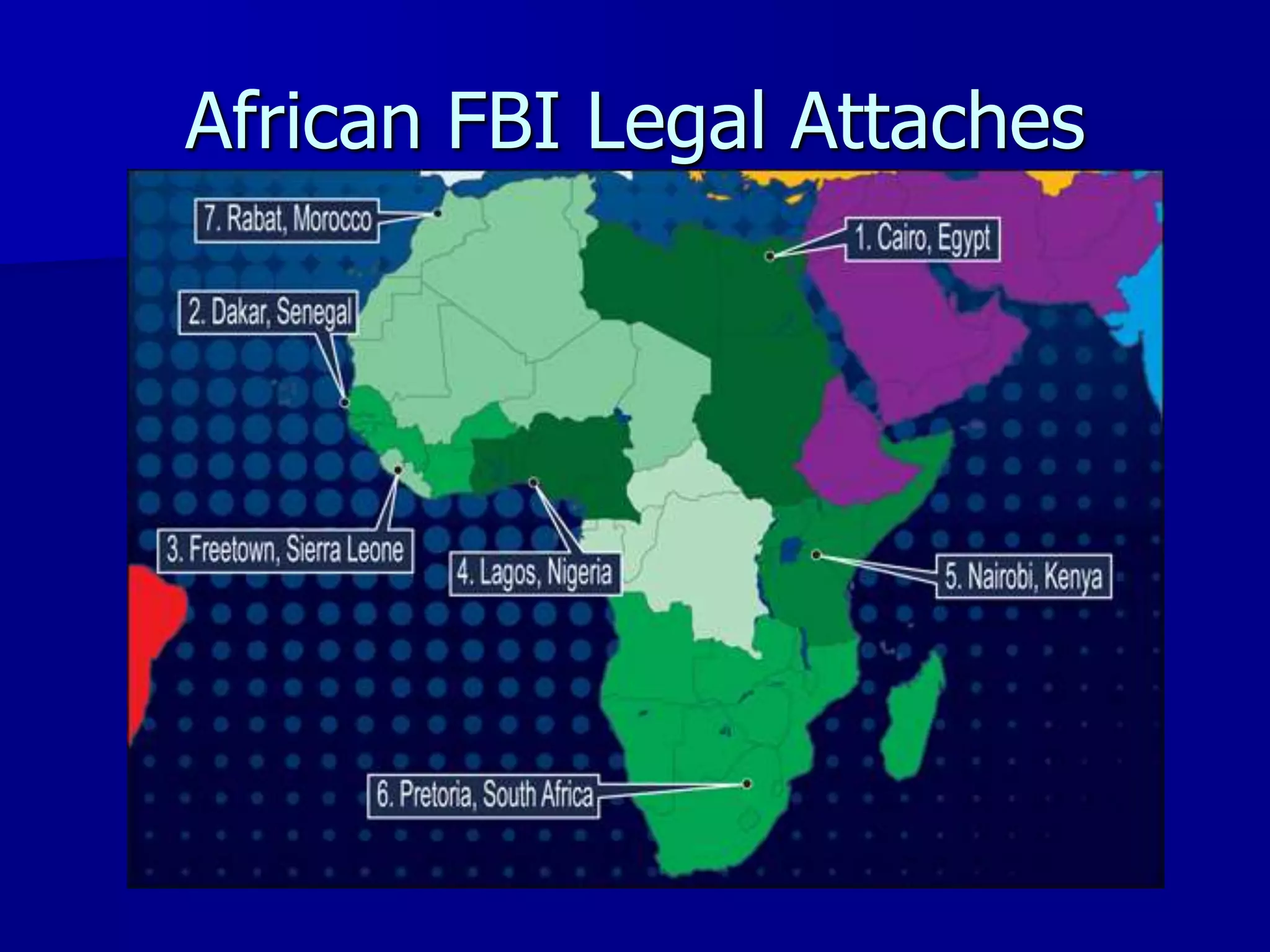
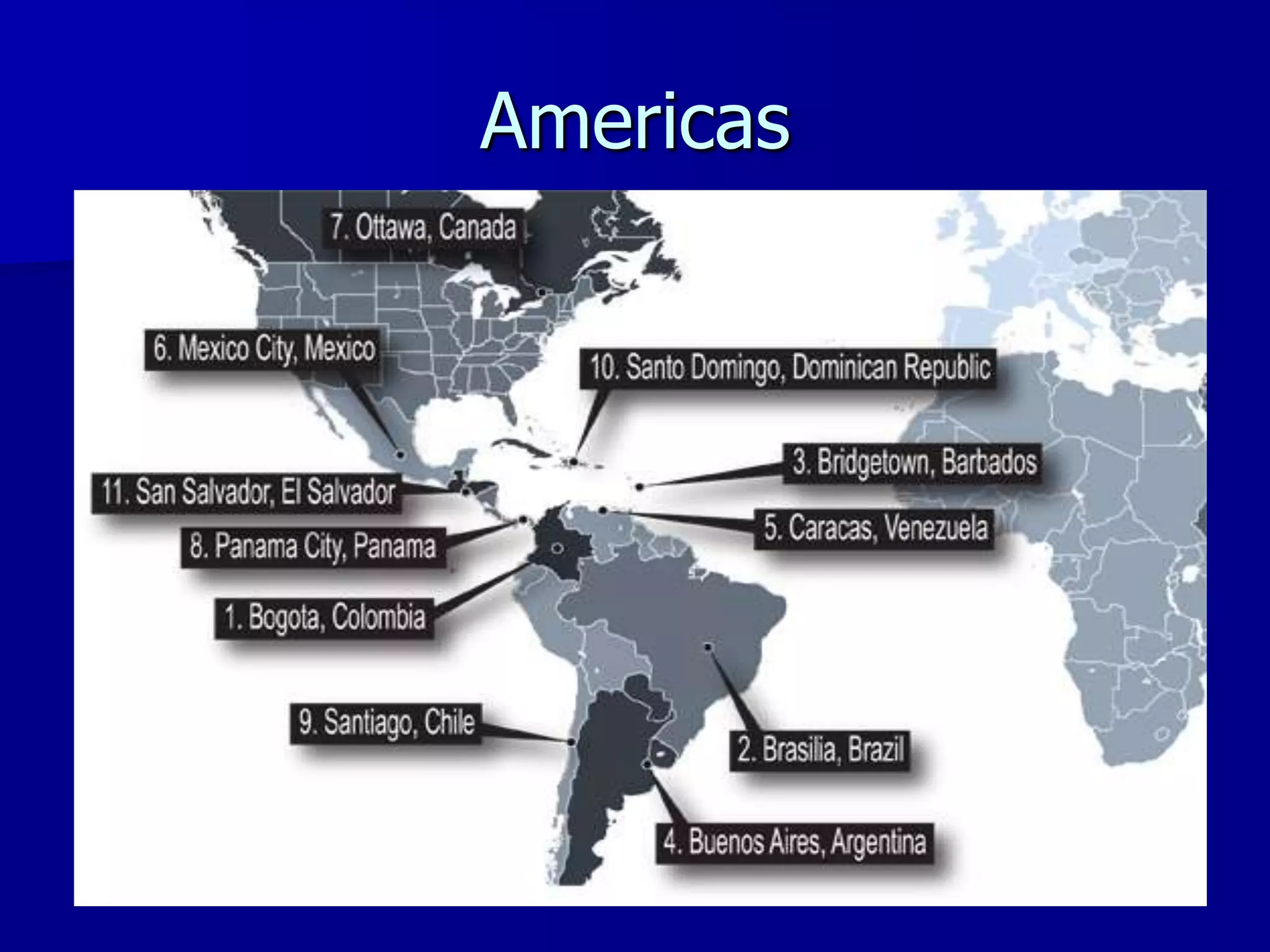
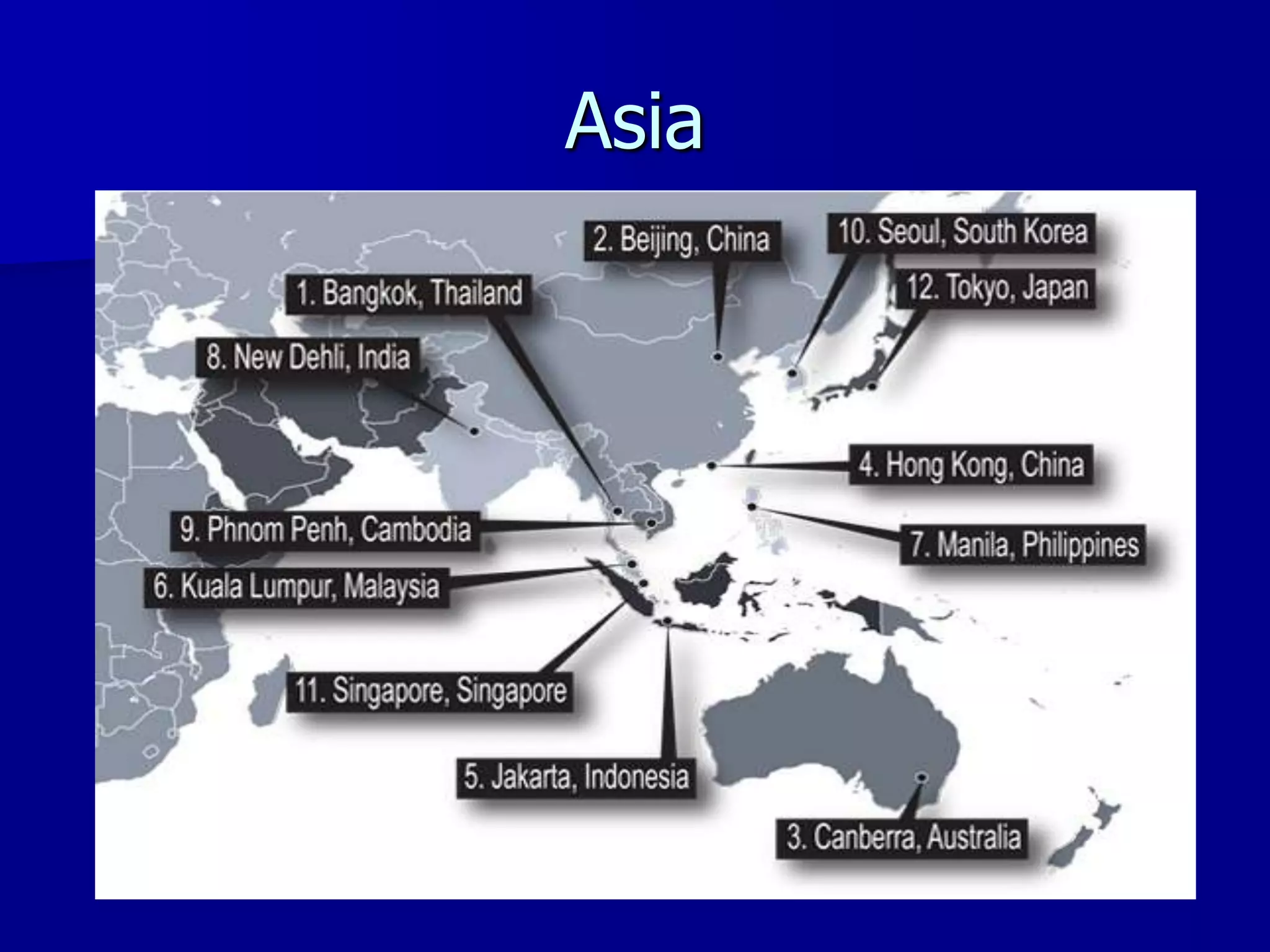
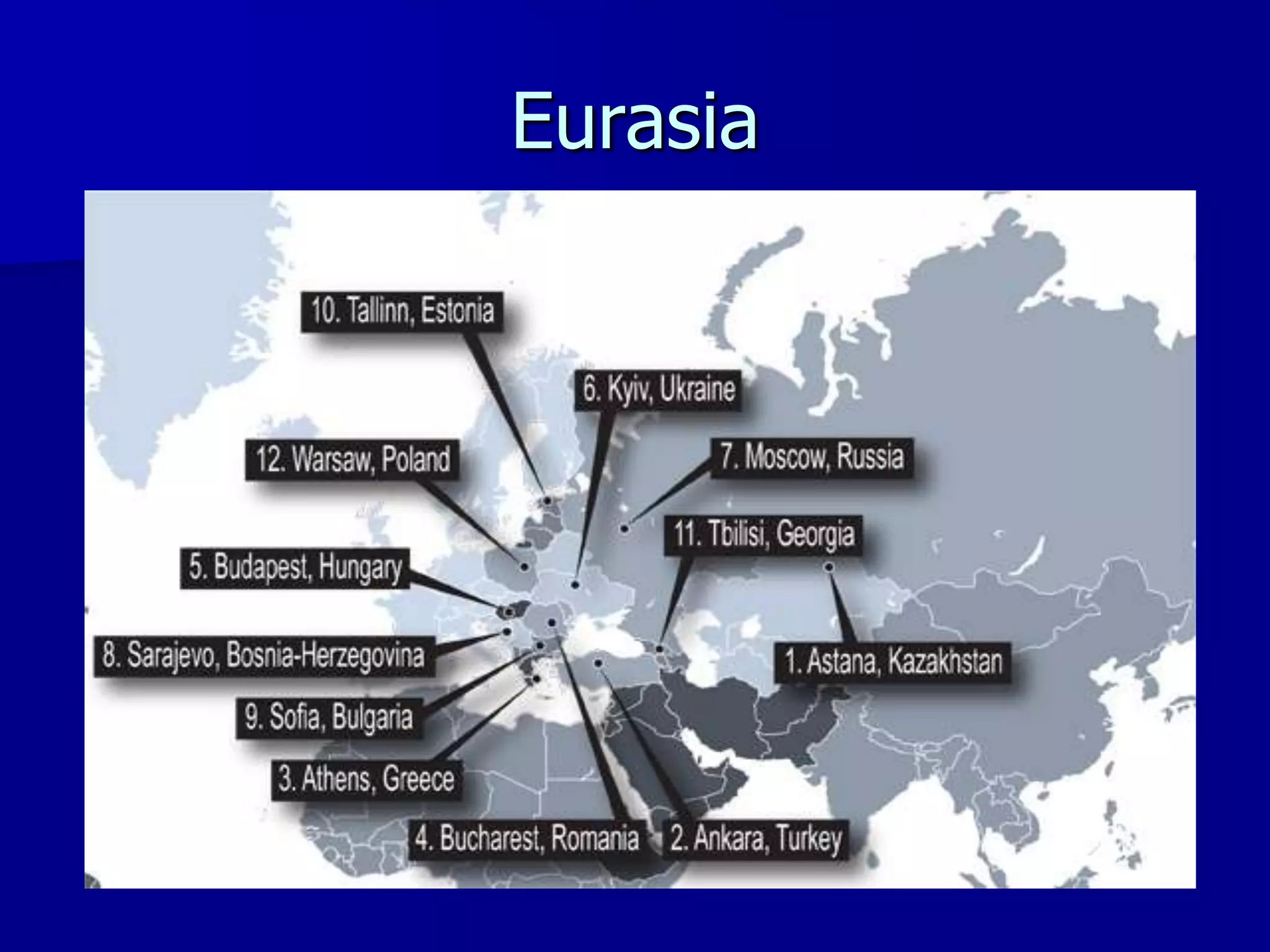
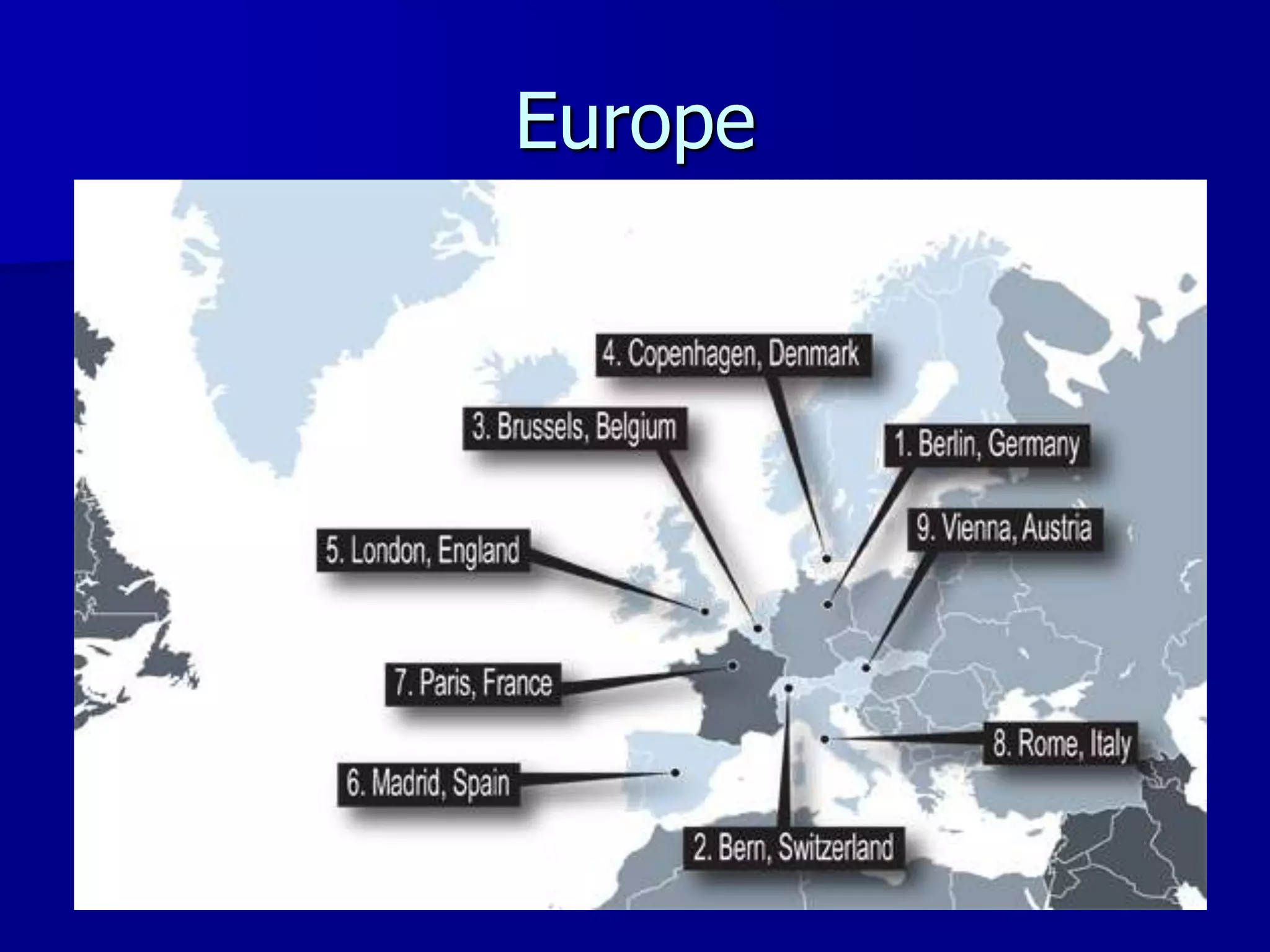
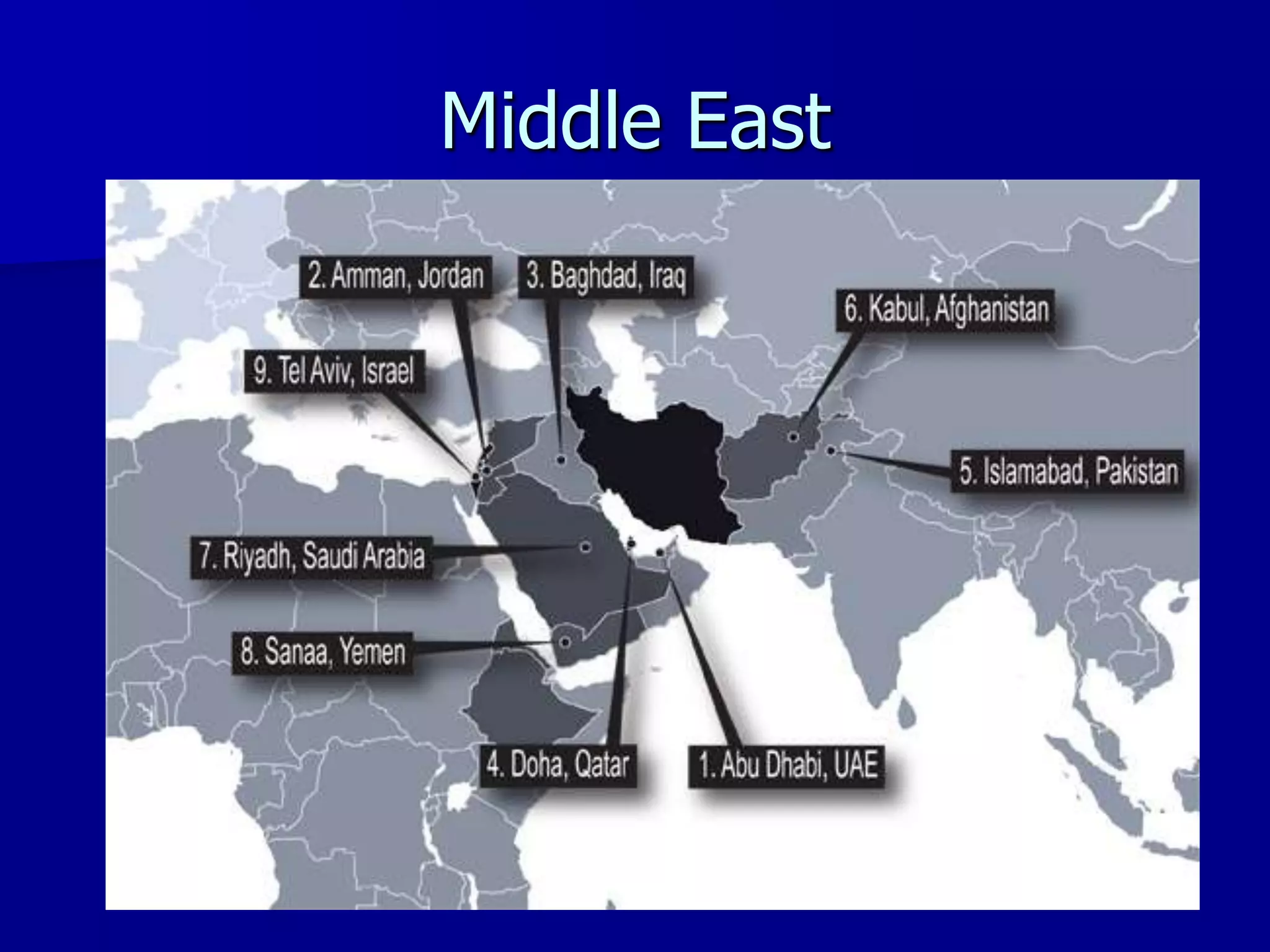
The document discusses the Office of Antiterrorism Assistance (ATA), a program within the U.S. Department of State that provides counterterrorism training and equipment to foreign partners. It was created by Congress in 1983 to strengthen bilateral ties and provide assistance to deter terrorism. Since 1984, ATA has trained over 57,000 individuals from 151 countries. ATA's cyber training program works with countries to strengthen their ability to address cyber threats through skills training, networking, and equipment grants. The document outlines ATA's training courses and process for assisting partner countries with cyber capabilities.