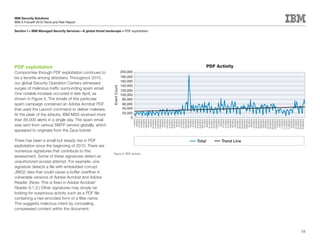
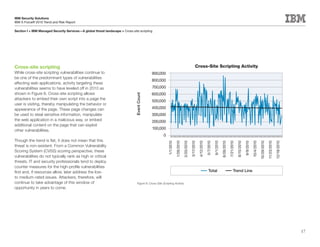
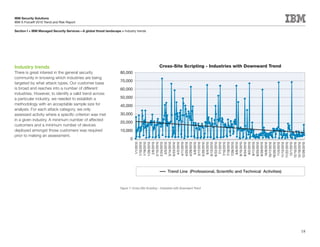
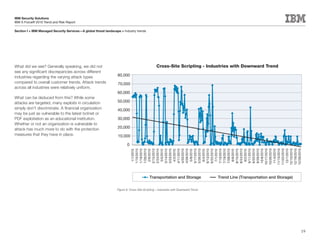
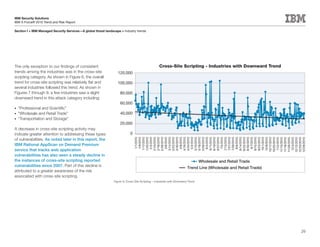
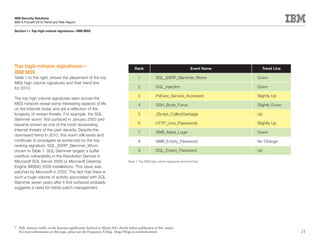
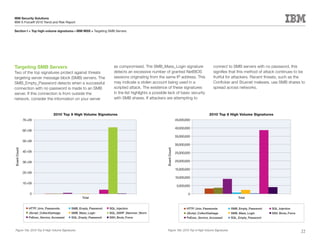
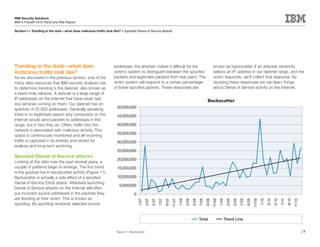
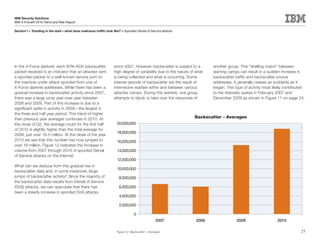
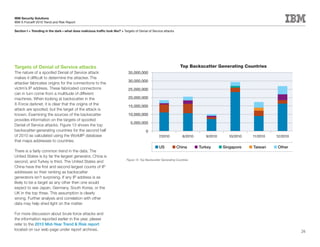
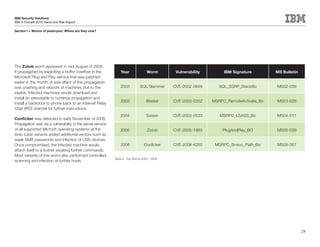
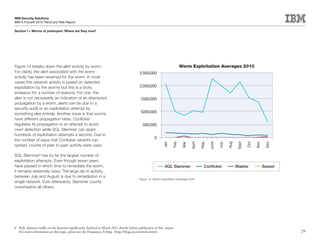
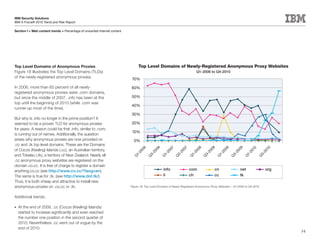
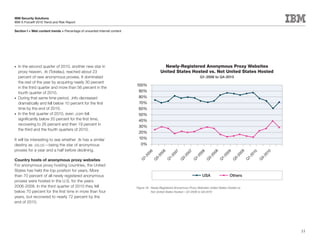
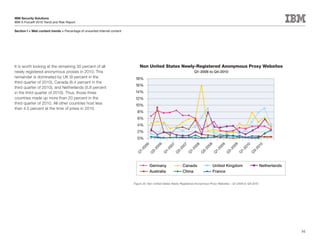
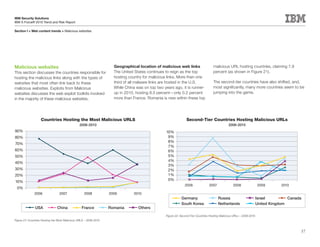
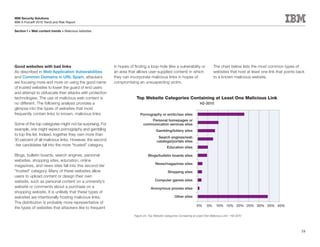
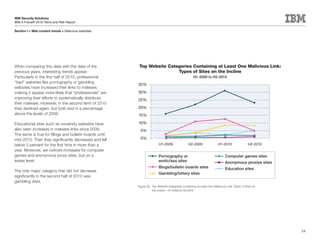
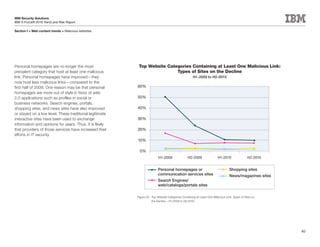
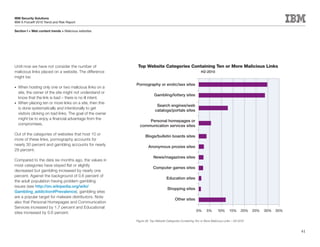
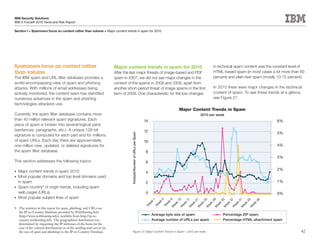
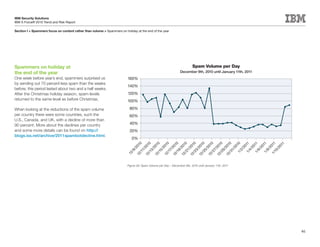
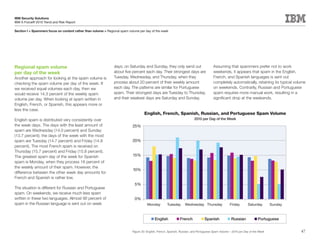
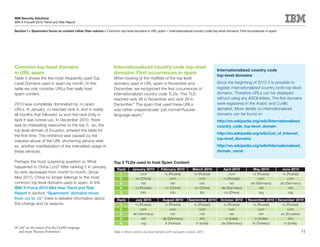
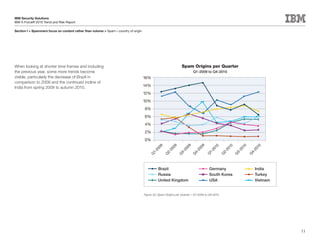
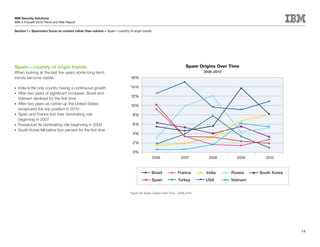
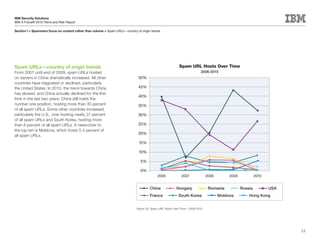
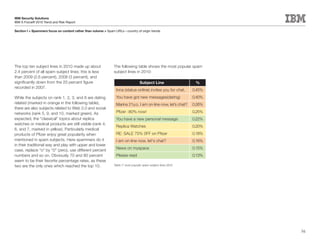
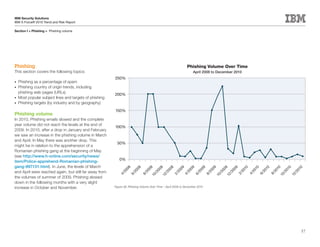
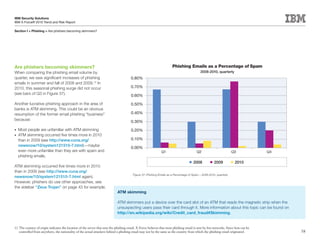
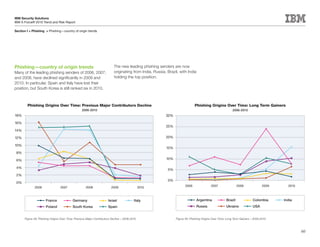
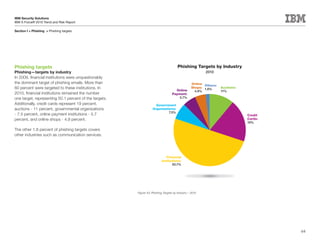
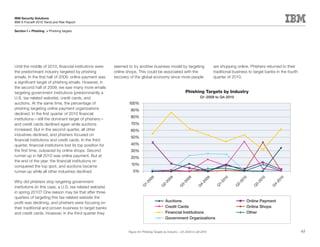
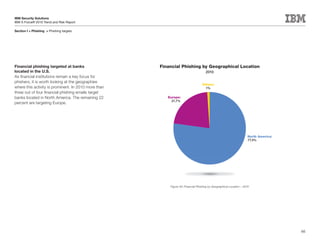
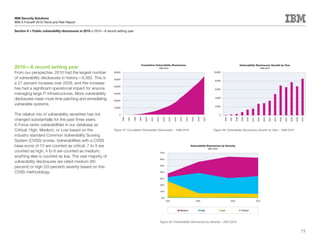
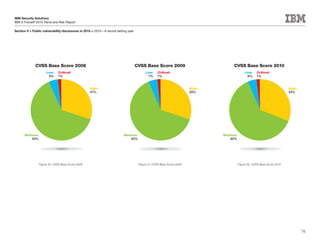
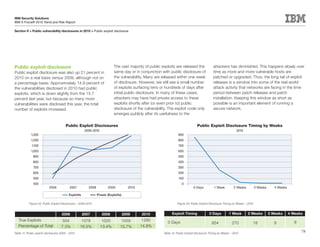
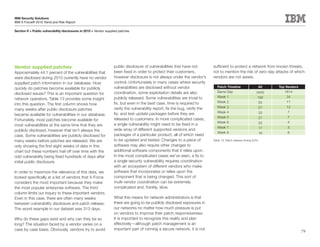
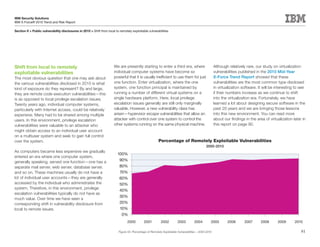
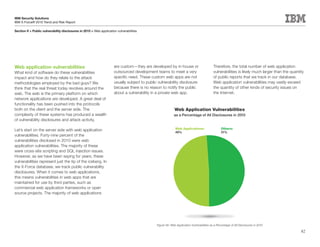
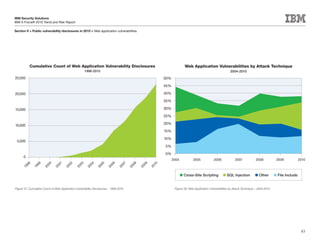
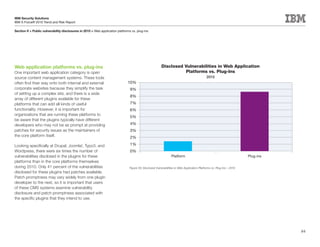
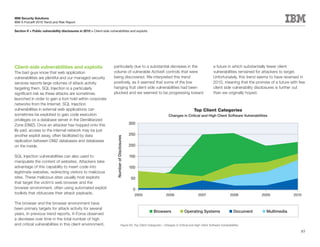
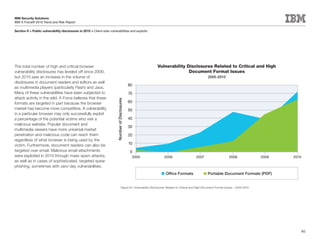
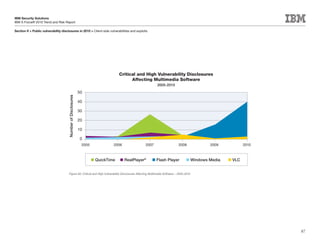
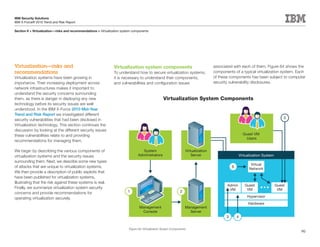
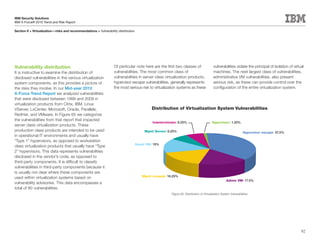
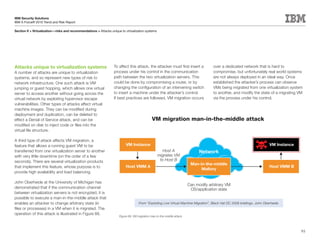
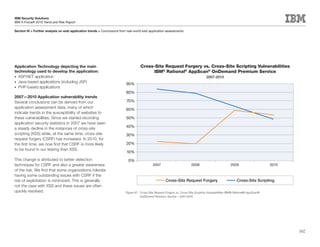
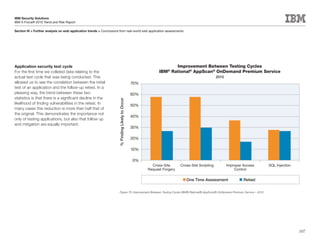
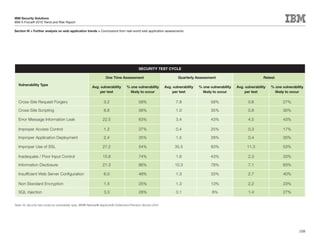
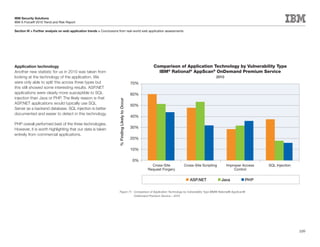
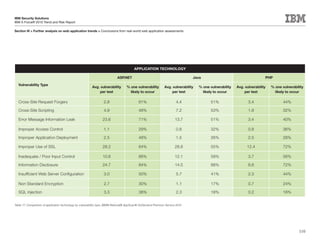
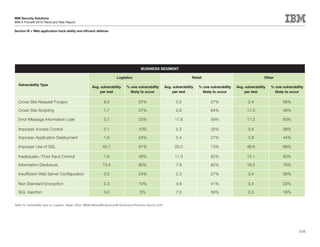
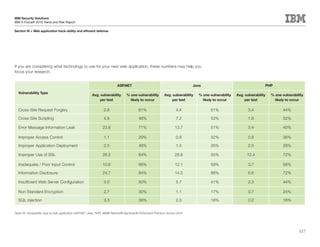
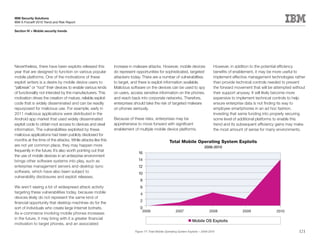
This document is the IBM X-Force 2010 Trend and Risk Report contributed to by many IBM researchers and analysts. It provides a summary of major cybersecurity trends and threats observed over 2010, including advanced persistent threats, targeted attacks, vulnerabilities, malware trends like Stuxnet, and recommendations for operating secure infrastructure and developing secure software. It also covers emerging security trends observed by IBM that may impact 2011 and beyond.