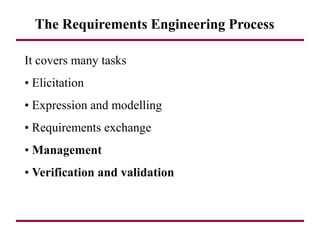
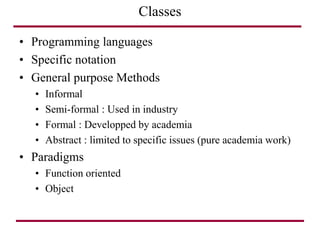
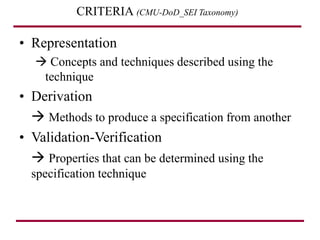
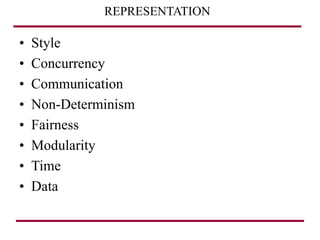
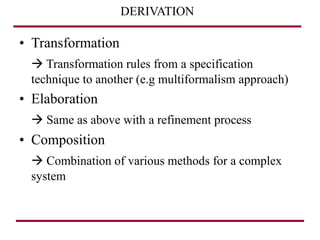
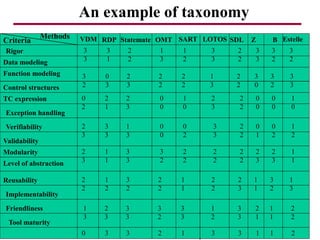
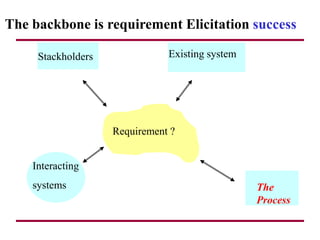
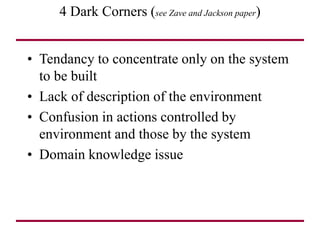
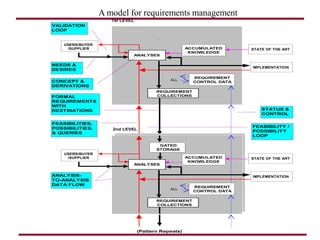
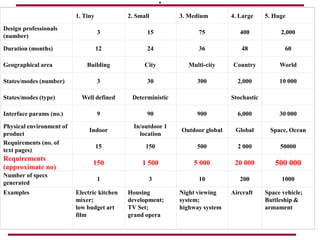
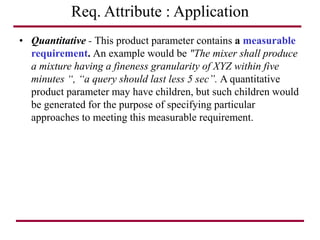
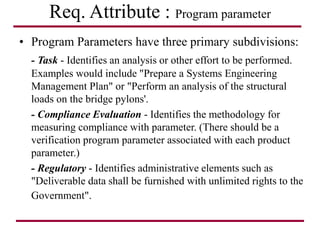
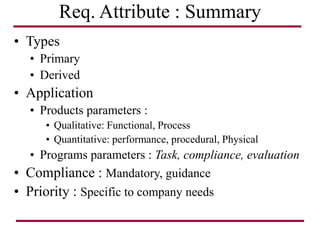
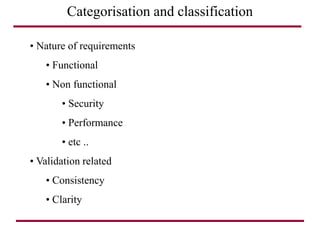
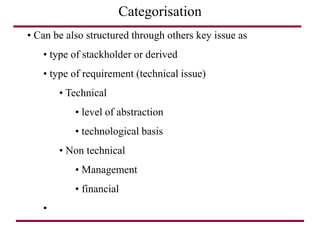
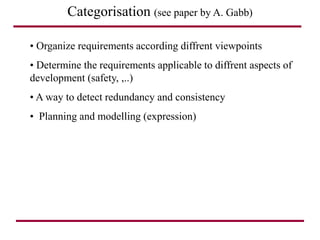
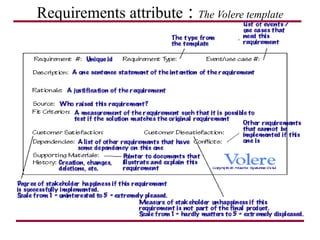
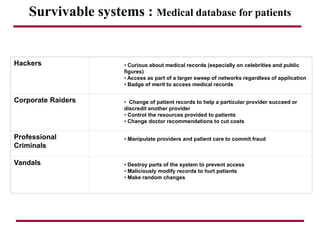
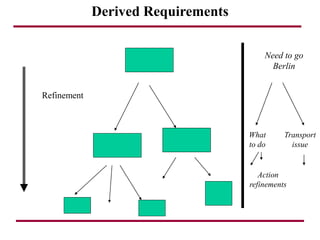
The document discusses requirements management and engineering. It covers key aspects of requirements management including the requirements engineering process, formalizing requirements, classes of languages and models used, and criteria for evaluating techniques. It discusses representation, derivation, and verification/validation of requirements. Important attributes of requirements like type, application, compliance level, and priority are summarized. The importance of traceability and categorization/classification of requirements is also covered.