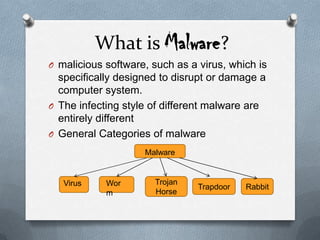
The document provides an overview of malware, including its definition, types (like viruses, worms, and trojans), historical malware examples, and detection methods. It discusses notable malware incidents such as the Morris Worm, Code Red, and SQL Slammer, and highlights future trends in malware like polymorphic and metamorphic viruses. Methods for malware detection include signature detection, change detection, and anomaly detection, each with their advantages and limitations.