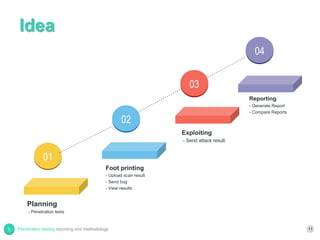
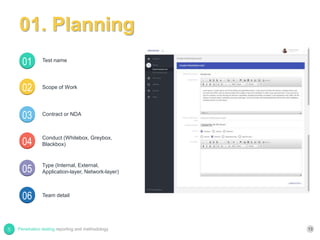
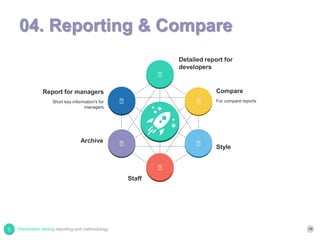
The document provides a comprehensive overview of penetration testing, contrasting it with security audits and vulnerability assessments. It outlines various methodologies for conducting penetration tests, alongside guidelines for reporting the findings effectively, emphasizing the need for standardized reporting and comparison systems. Future work includes enhancements to the penetration testing process and tools.



![Report format - Styles
American Psychological Association (APA) Style[1]
Page design, Document Control, List of Report Content, Executive
Summary, Methodology, Detail findings, References, Appendices,
Glossary [2]
A Cover Sheet, The Executive Summary, Summary of Vulnerabilities,
Test Team Details, List of the Tools Used, A copy of the original
scope of work, The main body of the report, Final delivery [3]
[1] Thomas Wilhelm. Professional Penetration Testing. Syngress, 2009.
[2] Mansour A Alharbi. Writing a penetration testing report. SANS Institute, April 2010.
[3] Mike Sheward. The art of writing penetration test reports. January 2012.
Penetration testing reporting and methodology](https://image.slidesharecdn.com/rashadaliyev-penetrationtestingreportingandmethodology-170124050937/85/Penetration-testing-reporting-and-methodology-9-320.jpg)