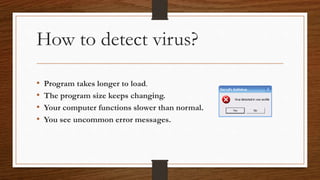
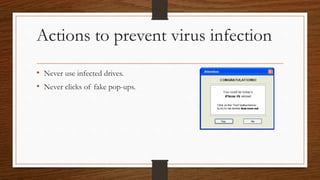
The document provides an overview of computer malware, detailing its types such as viruses, worms, and trojan horses, along with their functions and history. It discusses how these malicious software programs spread, the economic impact of viruses, and emphasizes the importance of using antivirus programs for protection. Preventive measures against malware infection are also highlighted, including keeping software updated and avoiding suspicious emails and downloads.