MainnetZ’s vision is to empower the use and creation of decentralized applications (Dapps) and to not only be the leading edge communal blockchain, but to also focus on the revelations of developers releasing innovative projects with high potential.
MainnetZ is committed to becoming the origin of innovative Dapp technology, promotion, business, and manufacturing within the cryptocurrency sector.
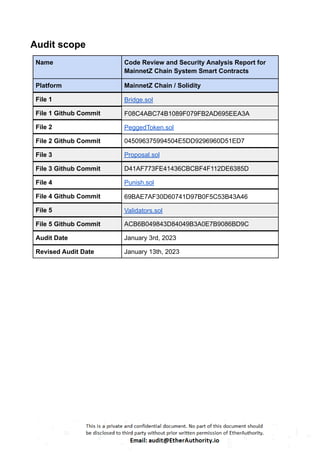
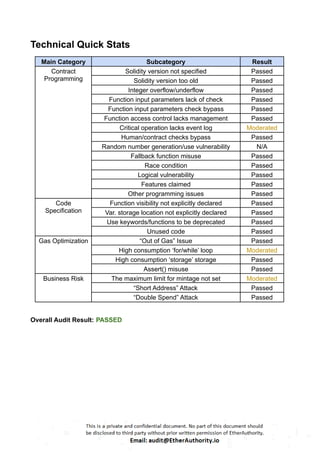
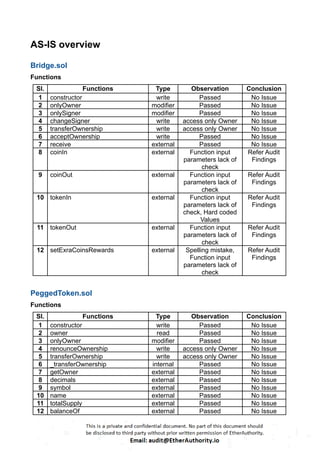
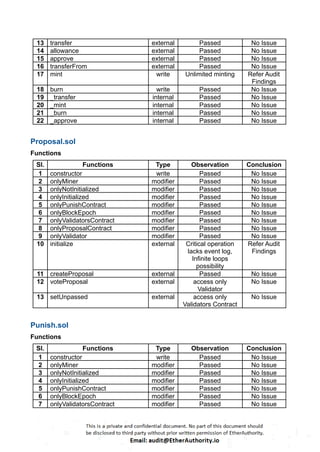
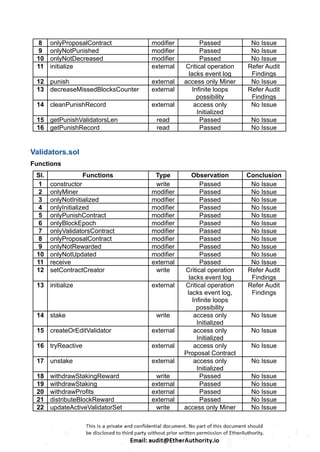
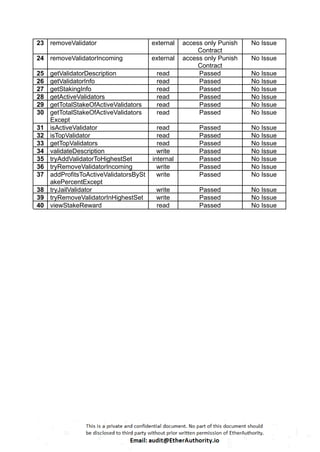
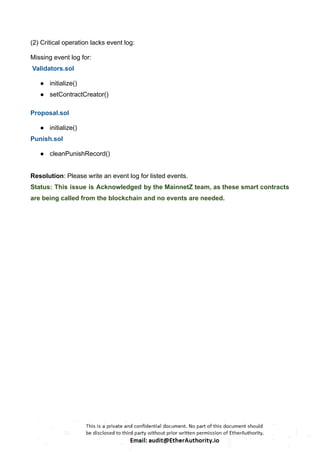
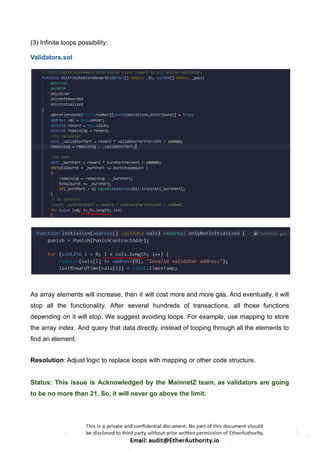
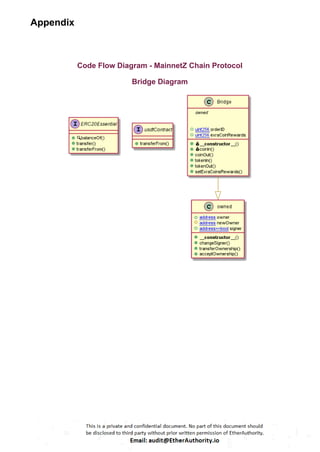
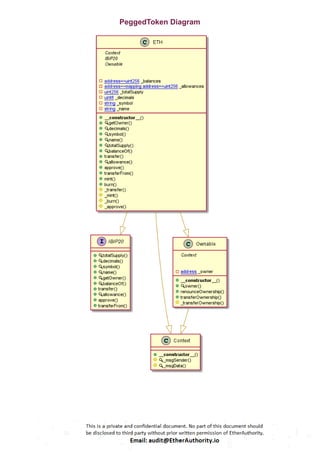
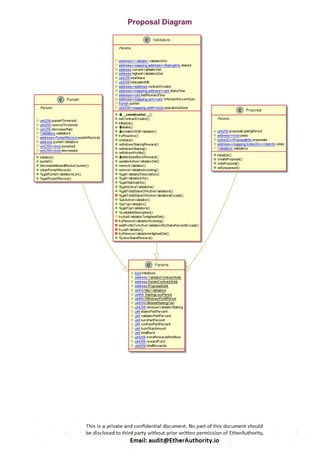
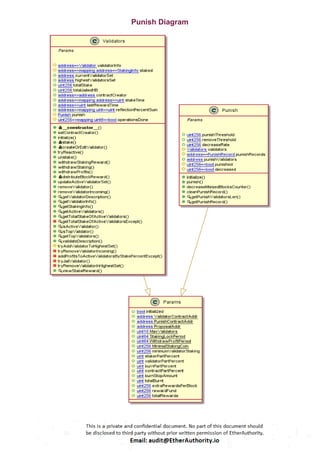
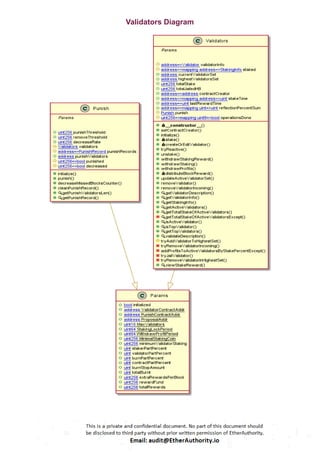
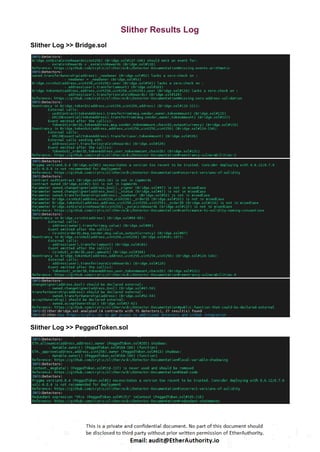
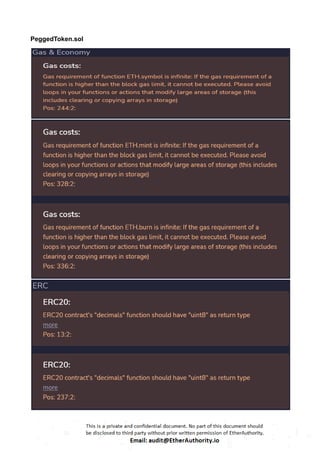
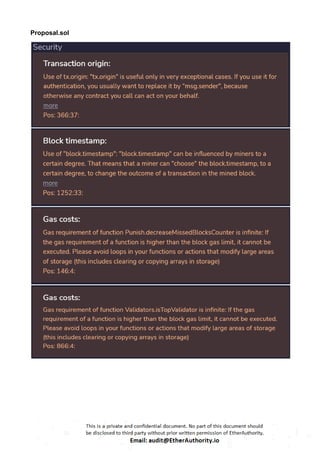
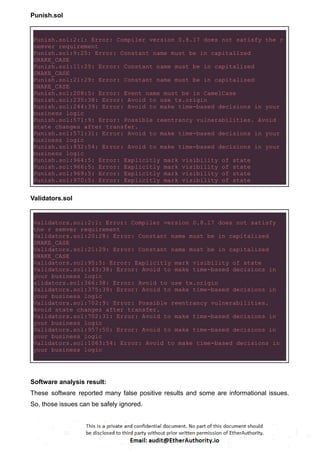
The audit scope consists of system smart contracts of the MainnetZ Chain. The system smart contracts contribute heavily to the consensus mechanism.
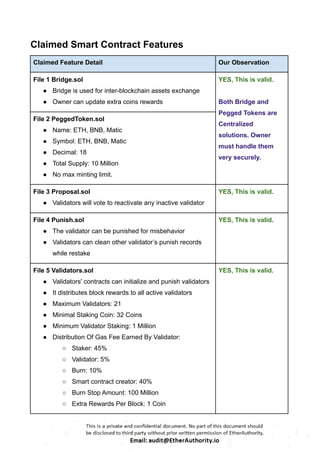
The system smart contracts performs actions such as Create/Update Validators, Vote for Proposals, staking for validators, Bridge, etc.