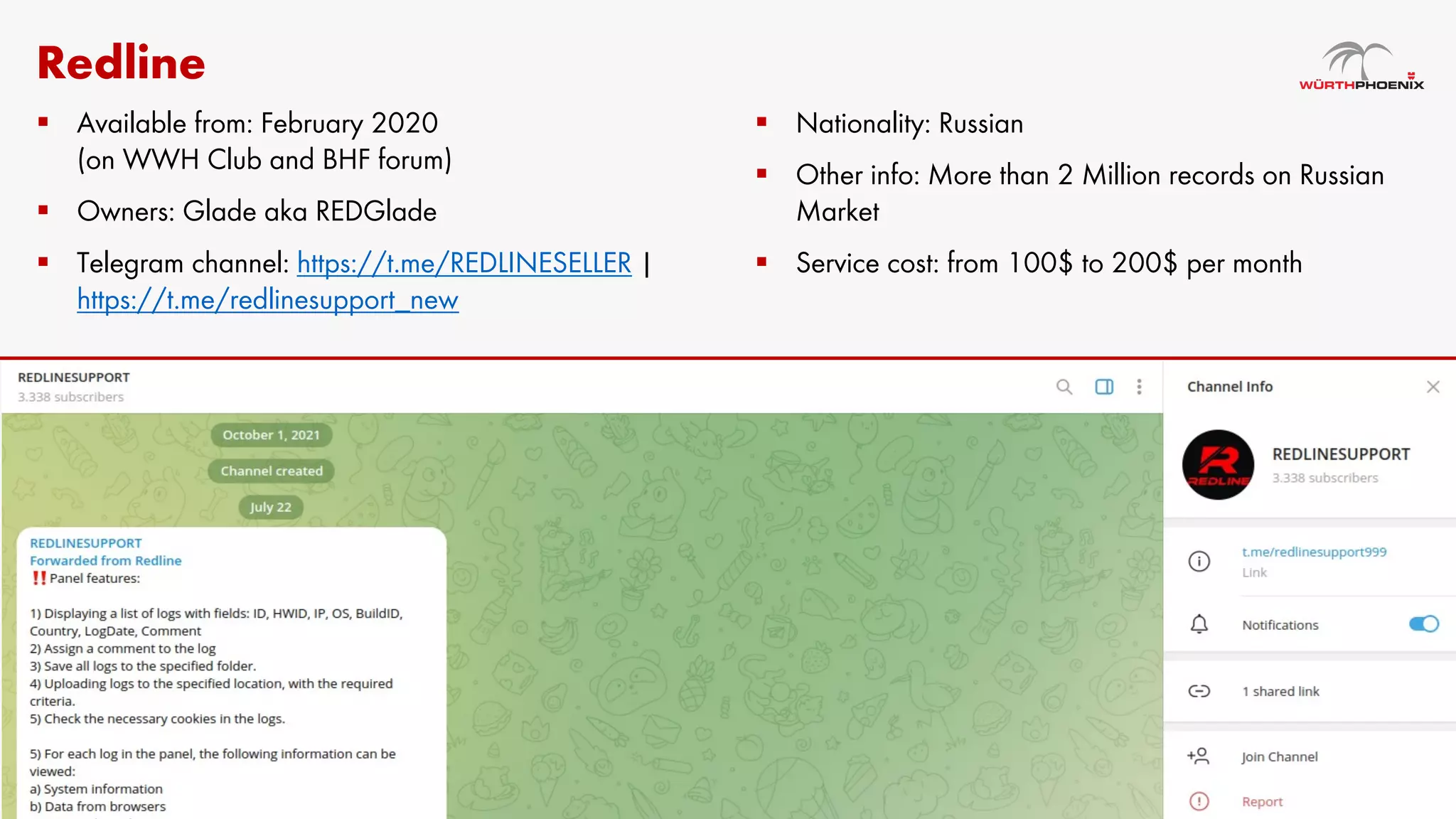
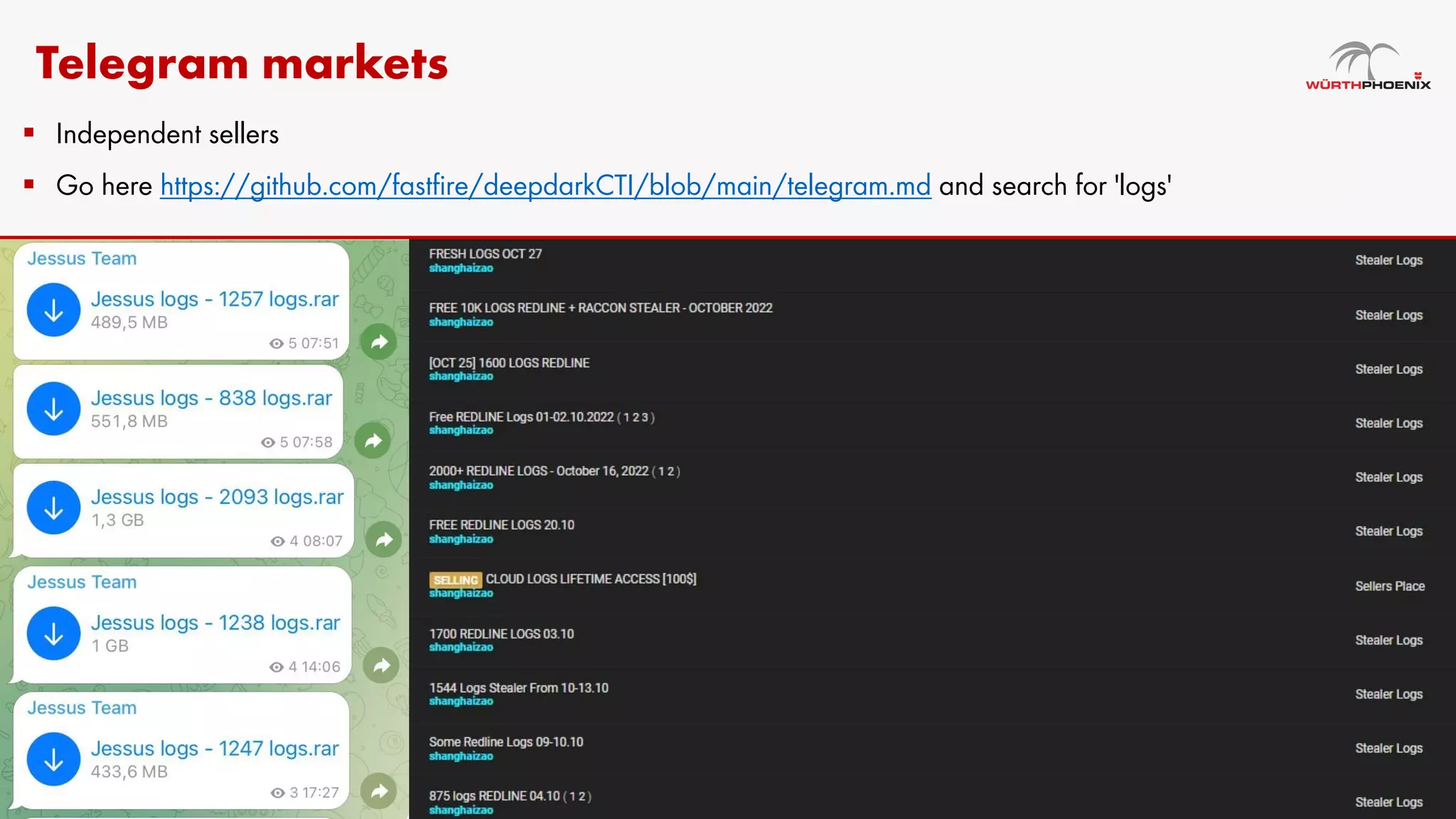
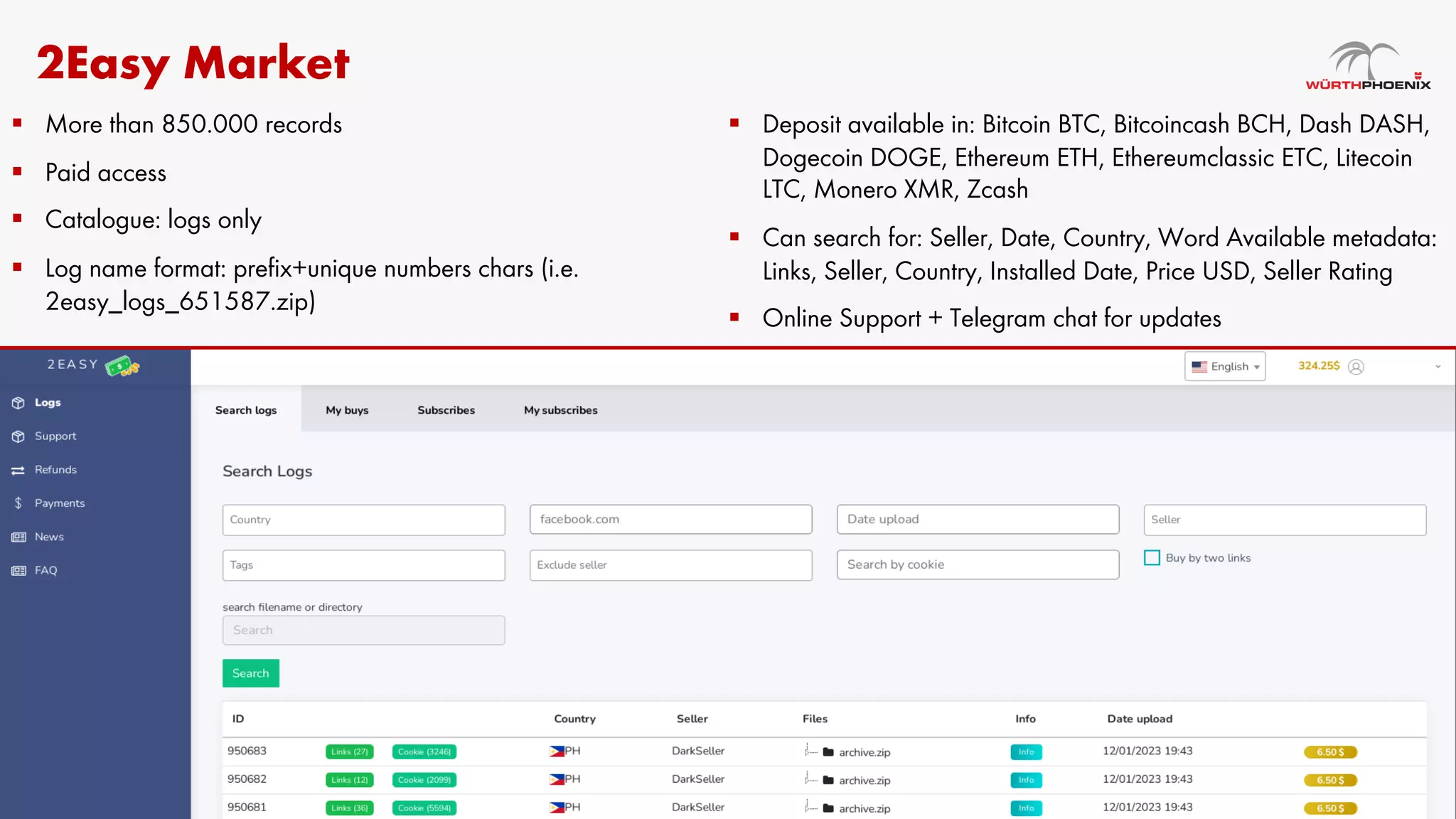
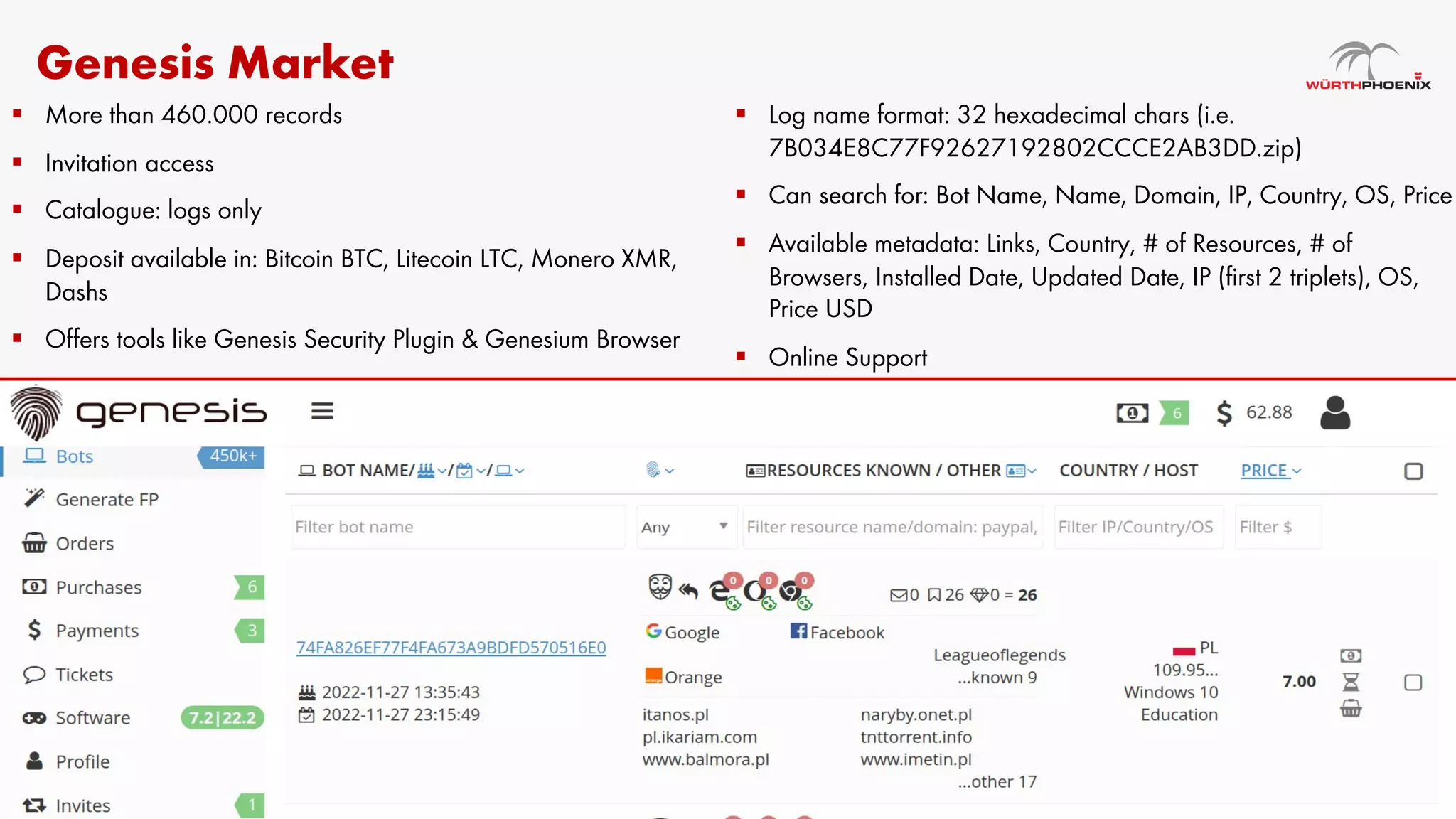
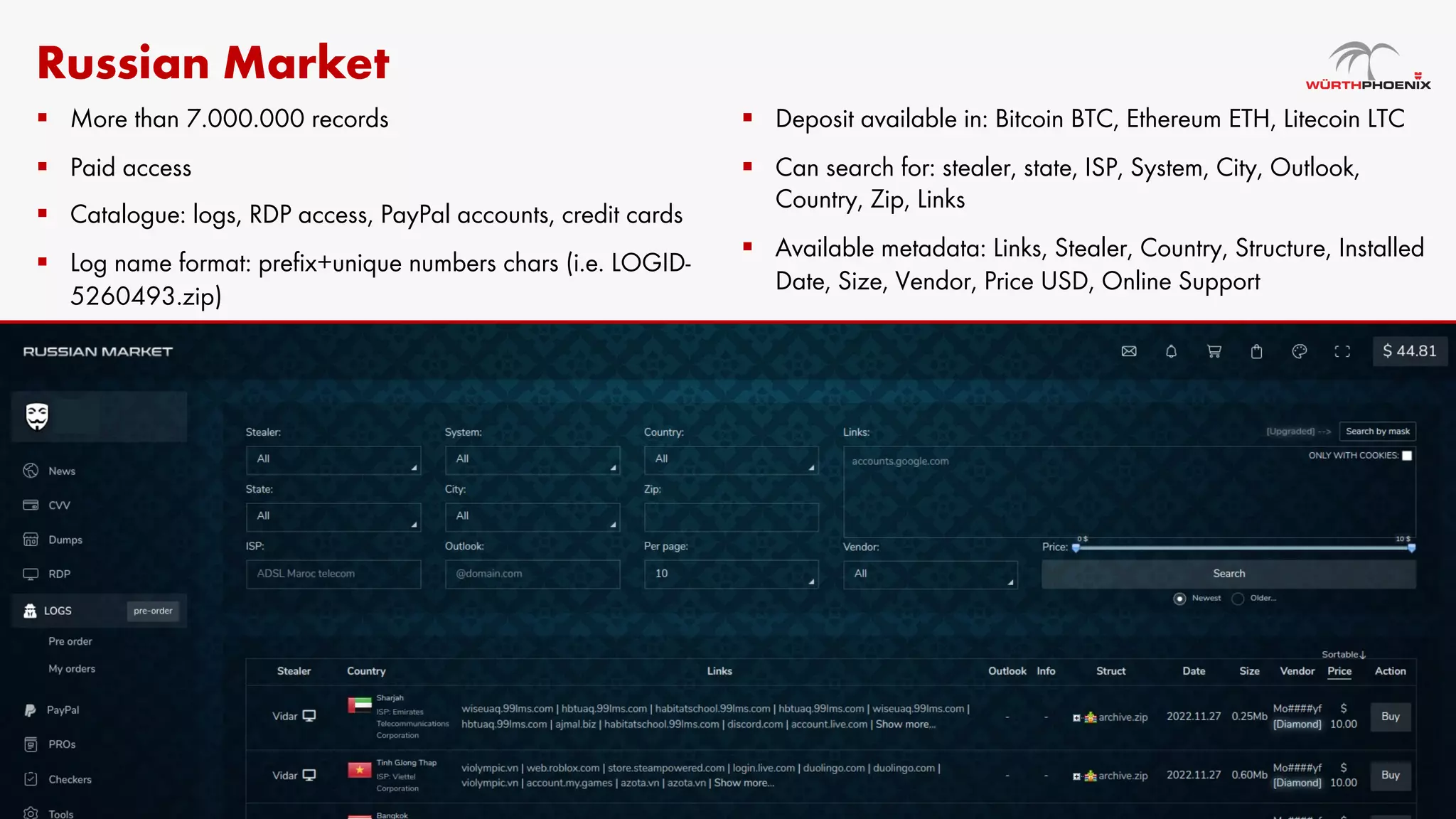
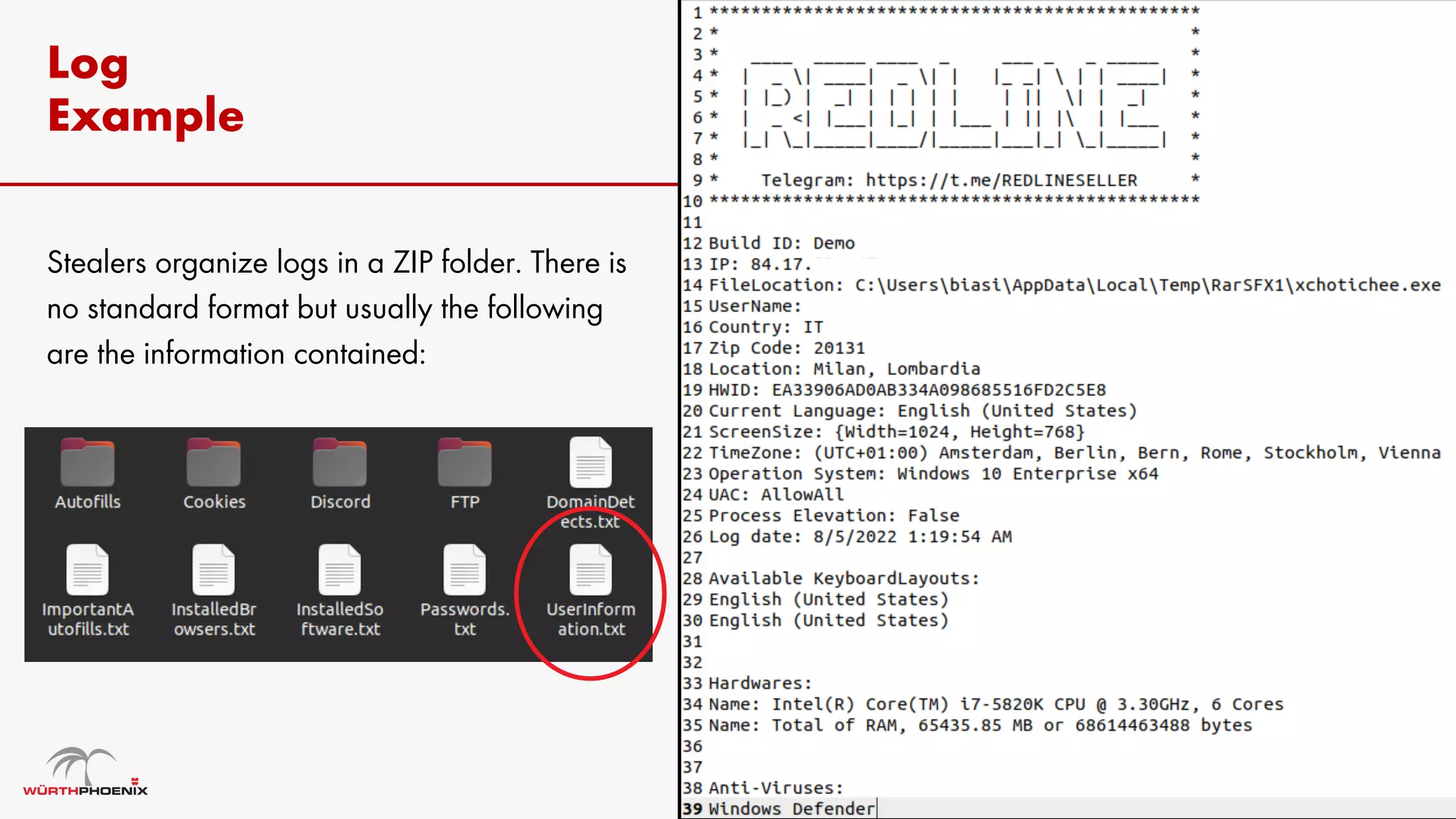
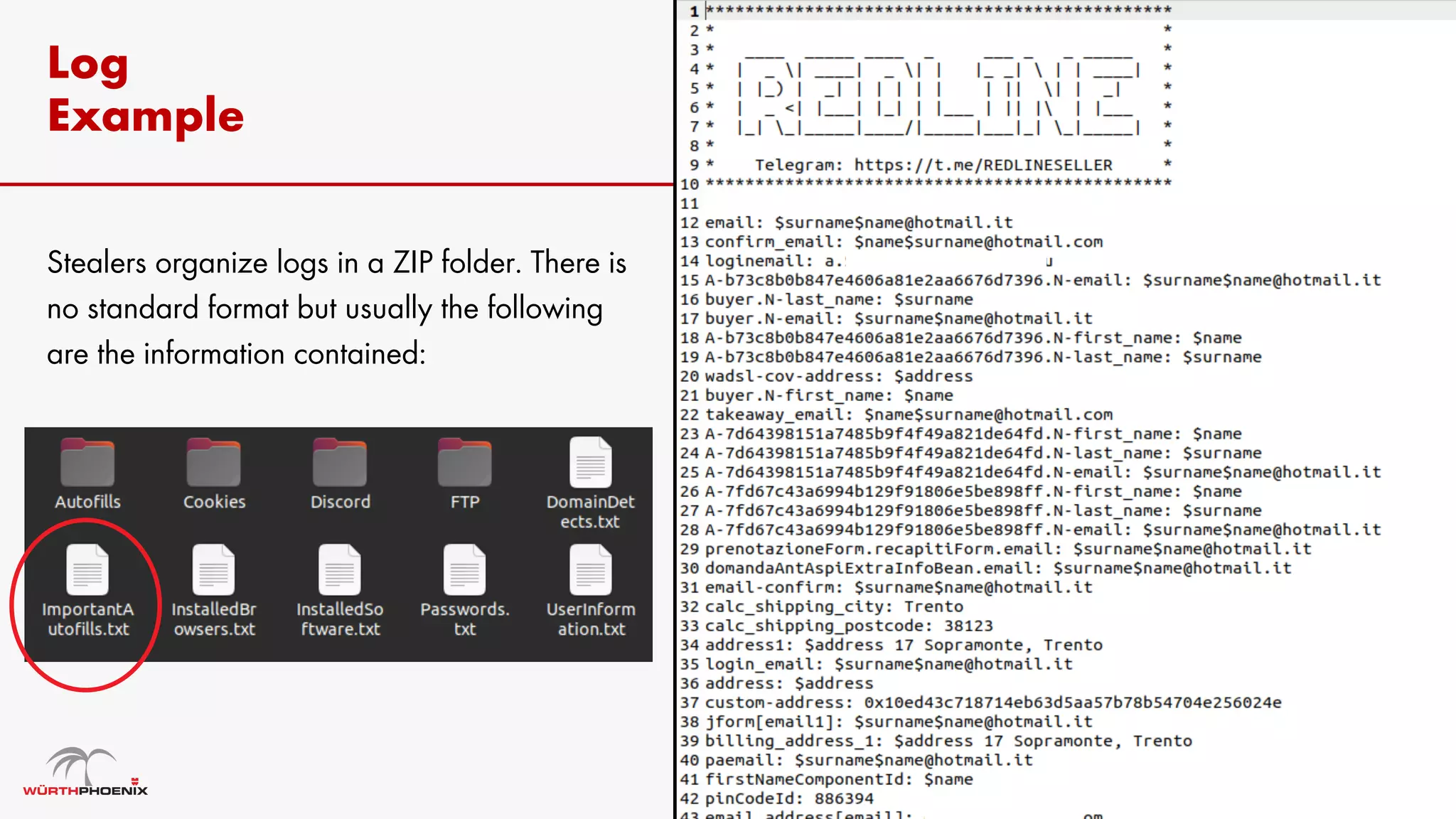
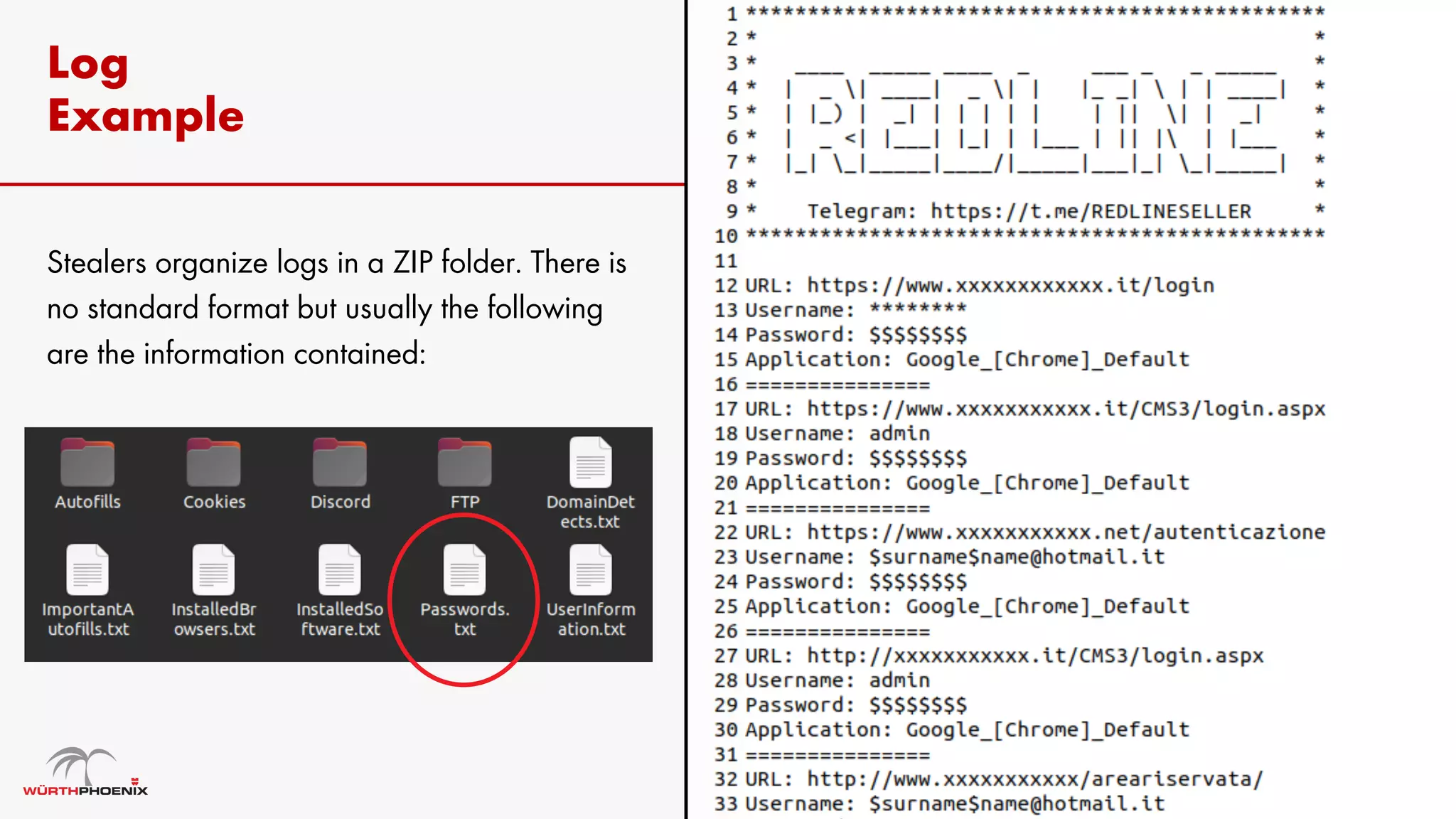
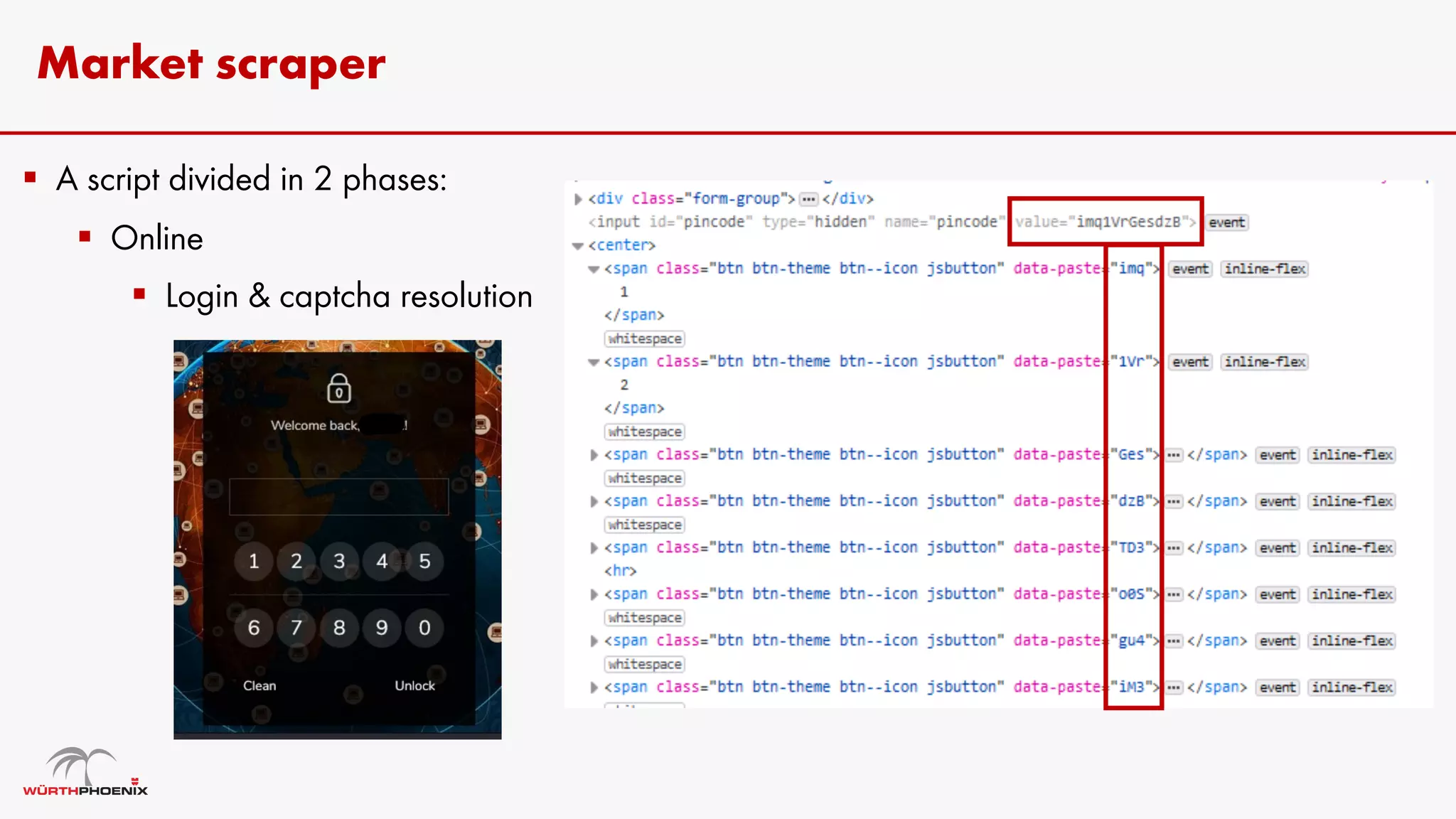
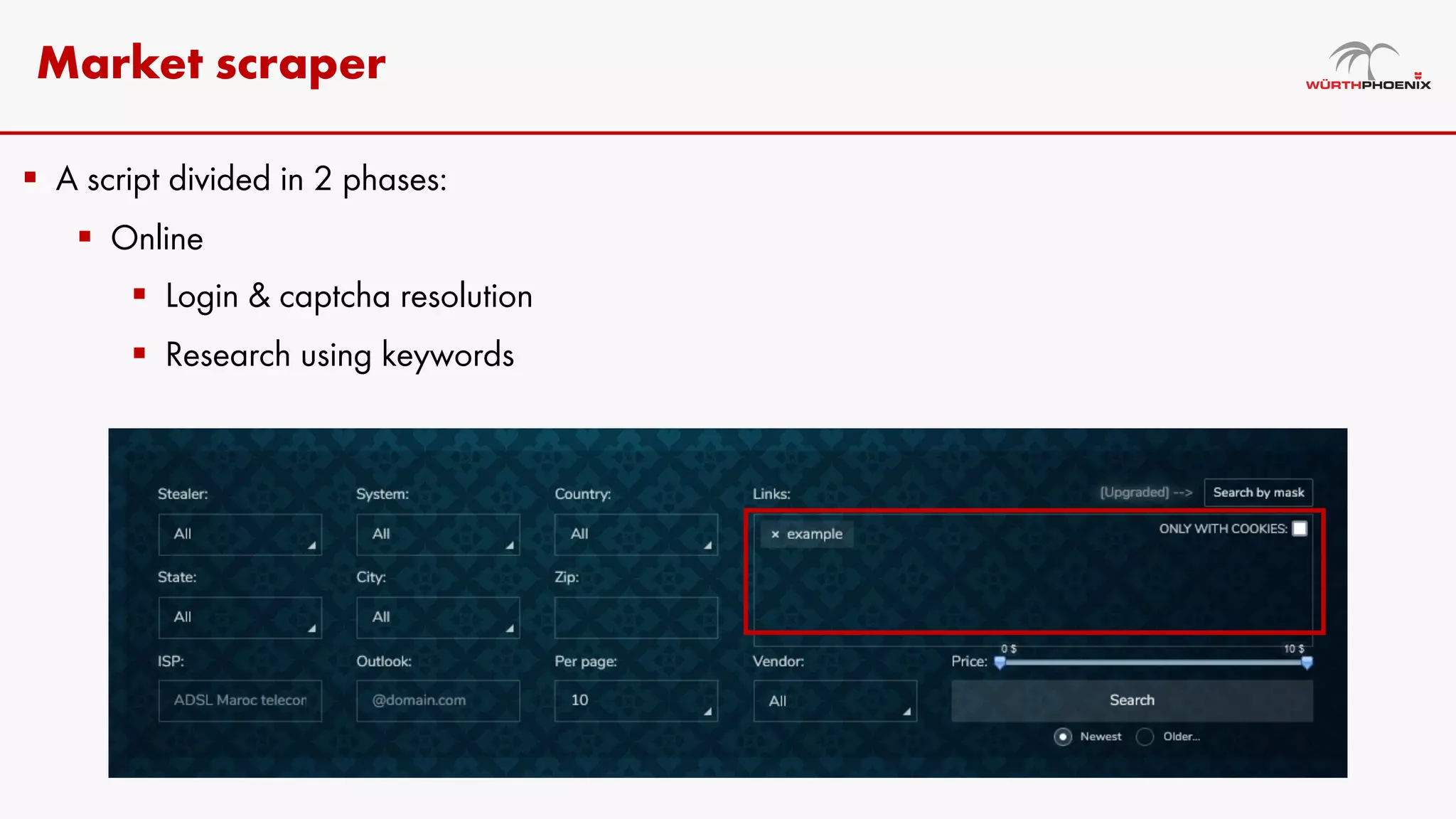
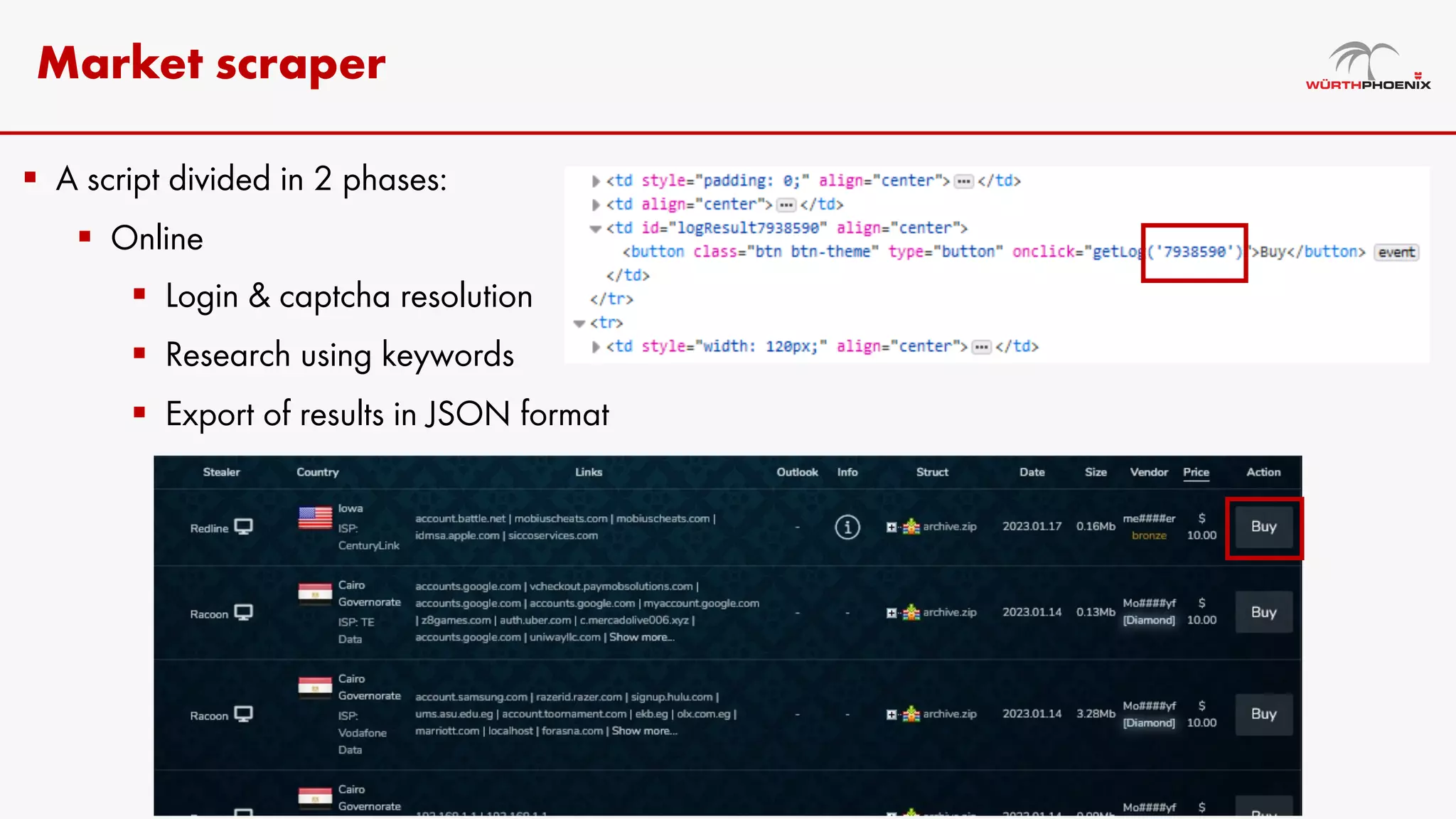
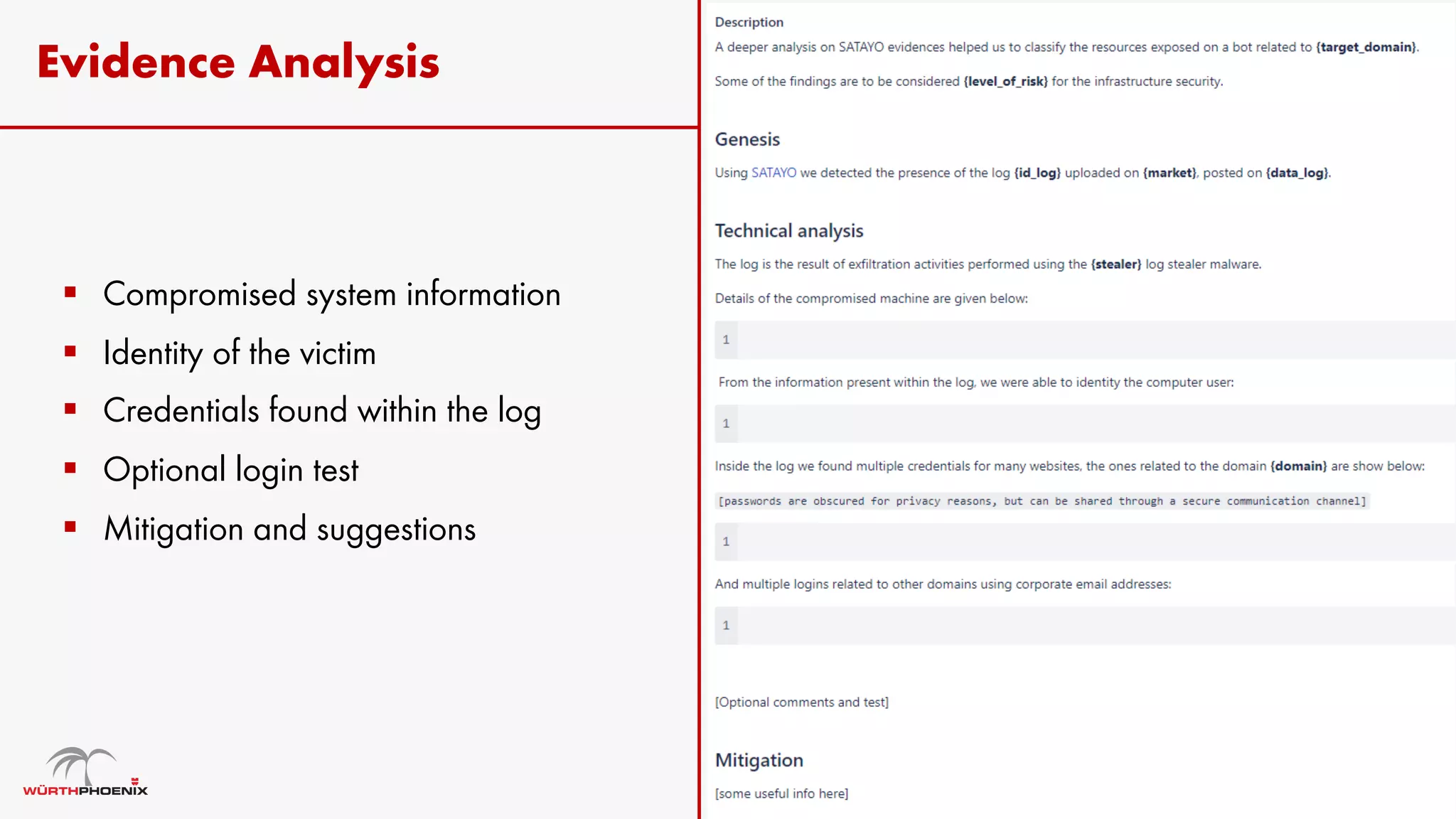
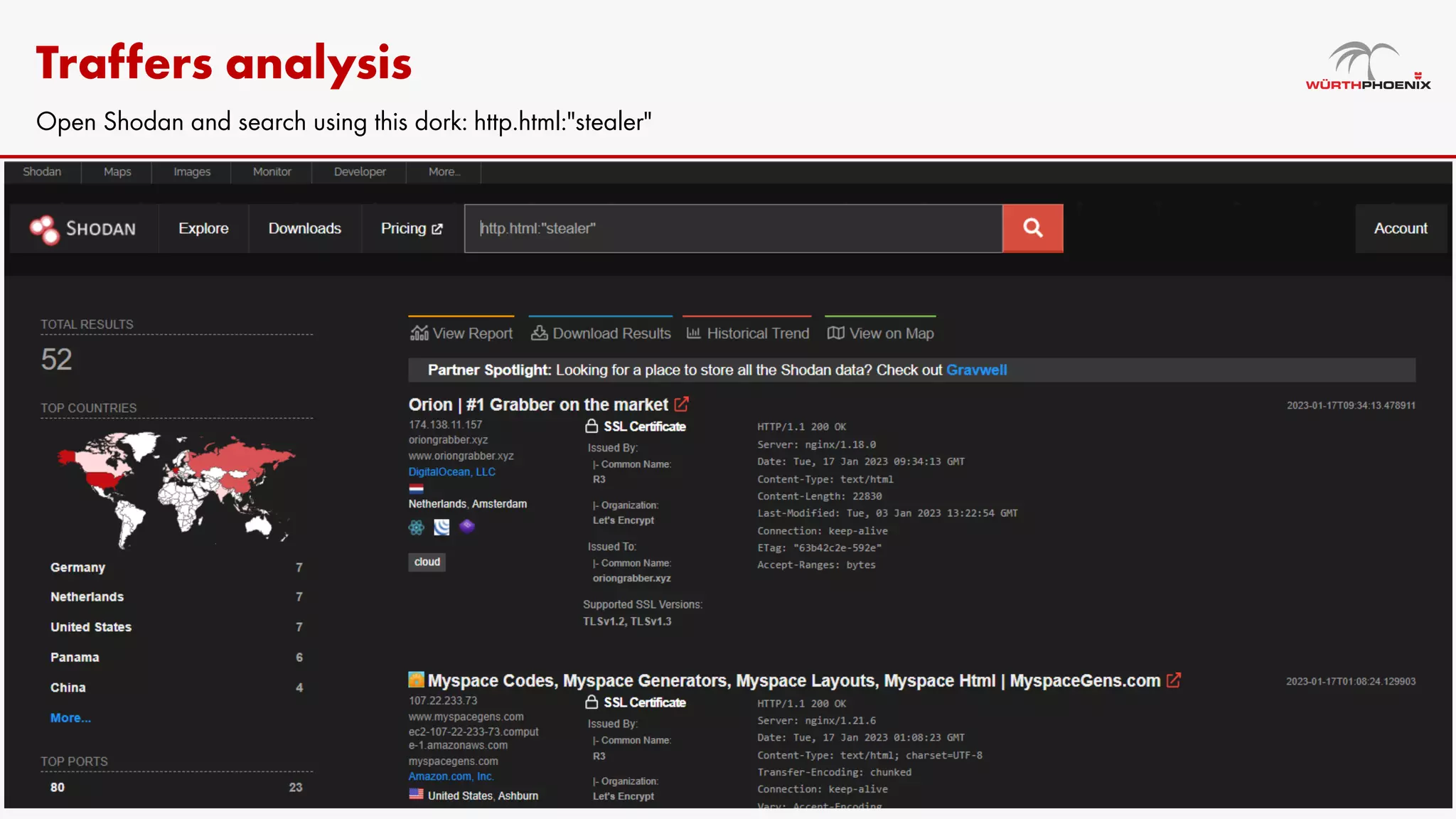
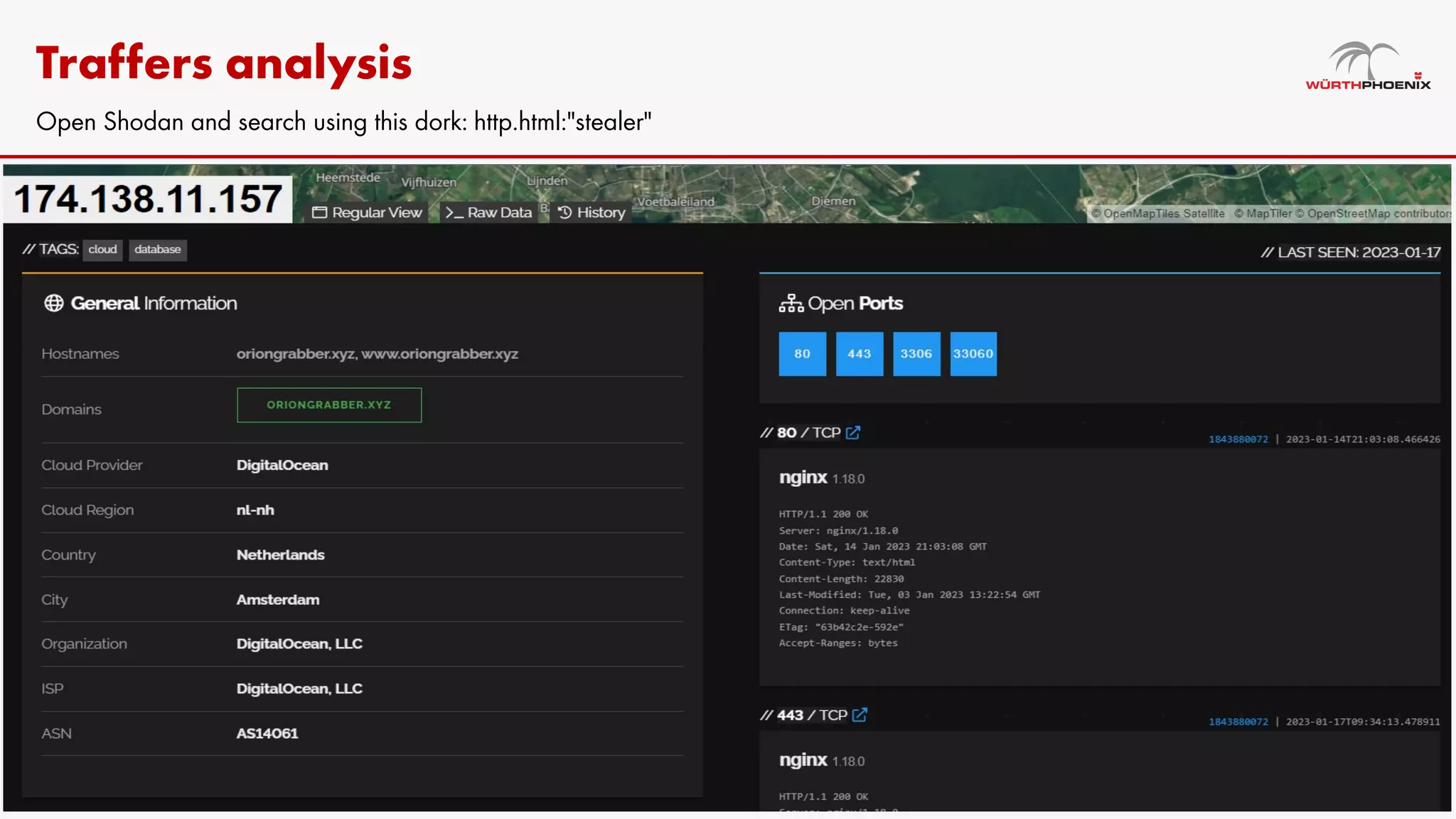
Log stealer malware is a trojan that collects sensitive data from infected systems, including login credentials and financial information. The document details various log stealer tools like Redline and Raccoon, including their origins, market presence, and operational methodologies. Additionally, it provides insights on marketplaces where stolen data is traded and discusses scraping techniques for monitoring these markets.