KISS API
•Download as PPTX, PDF•
0 likes•889 views
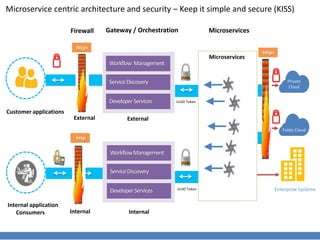
This document discusses microservice architecture and security. It outlines an architecture with external customer applications and internal applications communicating with microservices across private and public clouds through a gateway/orchestration layer. The architecture employs universal unique identifier tokens to help keep the design simple and secure.
Report
Share
Report
Share
Recommended
Cryptography in Blockchain

This document discusses cryptography in blockchain. It begins by introducing blockchain and cryptography separately. It then defines important cryptography terminology like encryption, decryption, cipher, and key. It describes the main types of cryptography as symmetric-key, asymmetric-key, and hash functions. It explains how blockchain uses asymmetric-key algorithms and hash functions. Hash functions are used to link blocks and maintain integrity. Cryptography provides benefits like the avalanche effect and uniqueness to blockchain. Finally, it discusses an application of cryptography in cryptocurrency, where public-private key pairs maintain user addresses and digital signatures approve transactions.
Future of hardware wallets bip 001

Nicolas Bacca discusses the future of hardware wallets and key improvements that can be made. Hardware wallets today focus on basic transaction confirmation but have limitations in more complex use cases like merchant purchases. Ledger proposes expanding functionality through an open LedgerOS that isolates secure elements and allows for customized confirmation UX and support of new assets. Lessons from smartcards on lifecycle management and isolation can be applied to build hardware wallets correctly from the ground up with key protection and integration of secure, pluggable applications.
12th International Conference on Communications Security & Information Assura...

12th International Conference on Communications Security & Information Assurance (CSIA 2021) focuses on all technical and practical aspects of communications security & information assurance for wired and wireless networks. The goal of this conference is to bring together researchers and practitioners from academia and industry to focus on understanding modern security threats and countermeasures, and establishing new collaborations in these areas
Authors are solicited to contribute to the conference by submitting articles that illustrate research results, projects, surveying works and industrial experiences that describe significant advances in the following areas, but are not limited to.
DN18 | Privacy by Design for Blockchain | Silvan Jongerius | TechGDPR 

About the Author:
Silvan Jongerius is the CEO and Founder of TechGDPR, a boutique consultancy for Data Protection and Privacy in tech-centric environments, such as Blockchain, AI and IoT. He has led Data Protection and security efforts since 2012, after spending 12 years in senior technology leadership, general management and innovation for large technology educators. In recent years, he has been particularly focused on Blockchain projects. He holds certifications from the Columbia Business School in Digital Strategies for Business, from the IAPP as Certified Information Privacy Professional (Europe/GDPR) and is TÜV certified Data Protection Officer (Datenschutzbeauftragter). He is the European Representative for DLT Labs, a Toronto-based blockchain development house. He is also a regular speaker, consultant and educator in GDPR, blockchain, innovation and technology, and is mentor and advisor for a number of innovative tech and blockchain projects.
12th International Conference on Communications Security & Information Assura...

12th International Conference on Communications Security & Information Assurance (CSIA 2021) focuses on all technical and practical aspects of communications security & information assurance for wired and wireless networks. The goal of this conference is to bring together researchers and practitioners from academia and industry to focus on understanding modern security threats and countermeasures, and establishing new collaborations in these areas
[Round table] zeroing in on zero trust architecture![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Idea of Zero Trust
Frameworks e.g. NIST framework
Building a Zero Trust Architecture
Building Tech stack for transition to Zero Trust Architecture
Building Tech stack for directly implementing Zero Trust Architecture
Bunker mail security

This document summarizes BunkerMail's encryption and authentication capabilities. It addresses PCI compliance requirements for encrypting data at rest and in motion. BunkerMail distributes cryptographic keys through steganography in digital pictures. User credentials contain encrypted keys for authentication using a photo as a virtual smartcard without transmitting passwords. Communications and stored data are encrypted end-to-end with unique AES keys protected by BunkerMail's public key infrastructure and redundant HTTPS. The system provides a secure and auditable solution for encryption at rest, in motion, and strong authentication.
Spring boot-vault

This document outlines a presentation on securing Spring Boot applications with Hashicorp Vault. It introduces Spring Boot and Vault, then describes several demos of integrating Vault to provide dynamic certificates, database credentials, and authentication tokens to a Spring Boot app. The presentation code is provided on GitHub for reference.
Recommended
Cryptography in Blockchain

This document discusses cryptography in blockchain. It begins by introducing blockchain and cryptography separately. It then defines important cryptography terminology like encryption, decryption, cipher, and key. It describes the main types of cryptography as symmetric-key, asymmetric-key, and hash functions. It explains how blockchain uses asymmetric-key algorithms and hash functions. Hash functions are used to link blocks and maintain integrity. Cryptography provides benefits like the avalanche effect and uniqueness to blockchain. Finally, it discusses an application of cryptography in cryptocurrency, where public-private key pairs maintain user addresses and digital signatures approve transactions.
Future of hardware wallets bip 001

Nicolas Bacca discusses the future of hardware wallets and key improvements that can be made. Hardware wallets today focus on basic transaction confirmation but have limitations in more complex use cases like merchant purchases. Ledger proposes expanding functionality through an open LedgerOS that isolates secure elements and allows for customized confirmation UX and support of new assets. Lessons from smartcards on lifecycle management and isolation can be applied to build hardware wallets correctly from the ground up with key protection and integration of secure, pluggable applications.
12th International Conference on Communications Security & Information Assura...

12th International Conference on Communications Security & Information Assurance (CSIA 2021) focuses on all technical and practical aspects of communications security & information assurance for wired and wireless networks. The goal of this conference is to bring together researchers and practitioners from academia and industry to focus on understanding modern security threats and countermeasures, and establishing new collaborations in these areas
Authors are solicited to contribute to the conference by submitting articles that illustrate research results, projects, surveying works and industrial experiences that describe significant advances in the following areas, but are not limited to.
DN18 | Privacy by Design for Blockchain | Silvan Jongerius | TechGDPR 

About the Author:
Silvan Jongerius is the CEO and Founder of TechGDPR, a boutique consultancy for Data Protection and Privacy in tech-centric environments, such as Blockchain, AI and IoT. He has led Data Protection and security efforts since 2012, after spending 12 years in senior technology leadership, general management and innovation for large technology educators. In recent years, he has been particularly focused on Blockchain projects. He holds certifications from the Columbia Business School in Digital Strategies for Business, from the IAPP as Certified Information Privacy Professional (Europe/GDPR) and is TÜV certified Data Protection Officer (Datenschutzbeauftragter). He is the European Representative for DLT Labs, a Toronto-based blockchain development house. He is also a regular speaker, consultant and educator in GDPR, blockchain, innovation and technology, and is mentor and advisor for a number of innovative tech and blockchain projects.
12th International Conference on Communications Security & Information Assura...

12th International Conference on Communications Security & Information Assurance (CSIA 2021) focuses on all technical and practical aspects of communications security & information assurance for wired and wireless networks. The goal of this conference is to bring together researchers and practitioners from academia and industry to focus on understanding modern security threats and countermeasures, and establishing new collaborations in these areas
[Round table] zeroing in on zero trust architecture![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Idea of Zero Trust
Frameworks e.g. NIST framework
Building a Zero Trust Architecture
Building Tech stack for transition to Zero Trust Architecture
Building Tech stack for directly implementing Zero Trust Architecture
Bunker mail security

This document summarizes BunkerMail's encryption and authentication capabilities. It addresses PCI compliance requirements for encrypting data at rest and in motion. BunkerMail distributes cryptographic keys through steganography in digital pictures. User credentials contain encrypted keys for authentication using a photo as a virtual smartcard without transmitting passwords. Communications and stored data are encrypted end-to-end with unique AES keys protected by BunkerMail's public key infrastructure and redundant HTTPS. The system provides a secure and auditable solution for encryption at rest, in motion, and strong authentication.
Spring boot-vault

This document outlines a presentation on securing Spring Boot applications with Hashicorp Vault. It introduces Spring Boot and Vault, then describes several demos of integrating Vault to provide dynamic certificates, database credentials, and authentication tokens to a Spring Boot app. The presentation code is provided on GitHub for reference.
12th International Conference on Communications Security & Information Assura...

12th International Conference on Communications Security & Information Assurance (CSIA 2021) focuses on all technical and practical aspects of communications security & information assurance for wired and wireless networks. The goal of this conference is to bring together researchers and practitioners from academia and industry to focus on understanding modern security threats and countermeasures, and establishing new collaborations in these areas
Identity Days 2020 - Quelles sont les méthodes et le niveau de sécurisation/r...

Retrouvez le support de la conférence donnée par Hakim Taoussi & Xuan Ahehehinnou lors de la seconde édition des Identity Days.
Burt Kaliski RSA conference 2007

This document discusses the re-emergence of symmetric key infrastructures (SKI) for managing encryption keys. It notes that as data protection grows in importance, SKIs that manage symmetric encryption keys across different applications and locations have advantages over standalone key management solutions. The document reviews lessons learned from previous SKI implementations as well as public key infrastructure (PKI) in designing modern SKIs. It suggests SKIs could fulfill many roles currently relying on public-key cryptography if public-key encryption was not available, and discusses potential technologies beyond PKI for security services like authentication, encryption, and key establishment in the future.
identity based encryption transformation for flexible sharing of encrypted da...

The document proposes an identity-based encryption transformation (IBET) model to address the problem of flexibly sharing encrypted data with more users in public clouds. IBET seamlessly integrates identity-based encryption and identity-based broadcast encryption, allowing data access based on user identities without certificate management. It provides a mechanism to transform an IBE ciphertext into an IBBE ciphertext, enabling access by a new group of users not specified during IBE encryption. The document outlines existing challenges with sharing encrypted data, describes the proposed IBET system and its advantages like security and controllable transformations, and lists system requirements.
Identity-centric interoperability with the Ceramic Protocol

https://ssimeetup.org/identity-centric-interoperability-ceramic-protocol-joel-thorstensson-webinar-57/
Ceramic is a new permissionless protocol for creating and accessing unstoppable documents that serve as the foundation for a connected, interoperable web without silos. Joel Thorstensson is the founder and CTO of 3Box and the primary author of the ceramic protocol as well as several Ethereum standards for identity and will provide a conceptual and technical intro to Ceramic.
At the root of many of the internet’s problems is that apps and services today are built primarily in silos. This includes identity registries and credentials, user data and access permissions, infrastructure, and services. It not only puts control over data and identities in the wrong hands, but it’s a fundamentally outdated and inefficient model for building digital products.
Ceramic unlocks information interoperability between all platforms and services across the web, allowing participants to create and resolve documents for any type of information without any centralized service. Ceramic uses DIDs (Decentralized Identifiers), IPLD (InterPlanetary Linked Data), signed messages, and blockchain anchoring to create a trusted and shared graph of verifiable documents. While flexible, these documents are especially well-suited for self-sovereign identity systems, user-centric data ecosystems, and open web services.
Call for Papers - 15th International Conference on Network Security & Applica...

15th International Conference on Network Security & Applications (CNSA 2022) focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this conference is to bring together researchers and practitioners from academia and industry to focus on understanding modern security threats and counter measures and establishing new collaborations in these areas.
Authors are solicited to contribute to the conference by submitting articles that illustrate research results, projects, surveying works and industrial experiences that describe significant advances in the areas of Security & its applications.
Blockchains and the IoT

This document discusses blockchains and their applications to the Internet of Things (IoT). It provides background on Bitcoin and the key characteristics of blockchain technology, including decentralization, immutability, and trusted transfer of assets. The document then outlines how blockchains could enable faster, safer, and cheaper transactions compared to traditional centralized systems. It proposes using MongoDB as the database layer for enterprise blockchain implementations due to its scalability, availability, data model flexibility, and other features. Finally, the document presents an enterprise blockchain maturity model ranging from centralized to decentralized approaches.
Samsung. Blockchain Keystore SDK and Use Cases

The document discusses Samsung's blockchain keystore, SDK, and use cases. The keystore stores private keys for blockchain services in a secure hardware wallet. It puts consumers in control of their data and credentials. The SDK allows developers to integrate blockchain functionality and provides functions for apps. Example use cases include payments, credentials, secure data storage, and digital rights management.
Build 2017 - B8024 - Connected intelligent things with Windows IoT Core and A...

This document provides an overview of Microsoft's Azure IoT platform and services for connecting, managing and analyzing IoT device data in the cloud. It summarizes Azure IoT Hub for device connectivity and management, Azure IoT Edge for processing data at the edge, and Azure IoT Central for a fully managed IoT SaaS solution. It also outlines capabilities for device security, provisioning and management, and analytics and visualization of IoT data in the Azure cloud.
What to look for in a hosted supplier

Mark Holland, Managing Partner, Baker Tilly Revas Limited
Understanding the security, credibility and flexibility of hosted suppliers and how to make sure the one you choose meets your needs.
Executive Alliance Dallas - Accellion Presentation

In the executive briefing, "How to Avoid BYO Disaster", Paula Skokowski, VP of Products and Marketing at Accellion, Gold Sponsor, provided insight into some of the more important trends and issues related to supporting and securing mobile access to confidential information in the BYOD post-PC era, their drivers, and expected impacts as organizations look to control and secure enterprise content.
От прорывной концепции до комплексного решения для компаний

This document discusses blockchain technology and its applications. It begins by describing the four types of people who are familiar with blockchain to different degrees. It then discusses blockchain fundamentals like distributed ledgers and smart contracts. Several use cases for blockchain are outlined across multiple industries like finance, healthcare, government and more. The strategy and roadmap for an open blockchain platform is presented, focusing on delivering capabilities for identity, privacy, operations and tools. Execution involves proving blockchain concepts, developing horizontal solutions, and creating industry-specific offerings.
DSI Tracker

DSI Tracker is an entry-level media management system from Dynamic Solutions International designed for their Virtual Library. It allows users to track media usage and expiration dates, move media between scratch and retain pools, and perform simple restores directly from virtual media. DSI Tracker was designed to work with DSI VTL Conductor to boost functionality like managing both virtual and physical media.
Rationalization and Defense in Depth - Two Steps Closer to the Cloud

Security represents one of the biggest concerns about cloud computing. In this session we’ll get past the FUD with a real-world look at some key issues. We’ll discuss the infrastructure necessary to support rationalization and security services, explore architecture for defense –in-depth, and deal frankly with the good, the bad, and the ugly in Cloud security. (As presented by Dave Chappelle at OTN Architect Day in Chicago, October 24, 2011.)
IoT on Blockchain Solution Overview

How to track the location of an Internet of Things (IoT) device on the blockchain and view it in a Google Maps reader application.
This solution features: (Hardware) Particle.io Electron device using C++ programming; (Platform) Provide Platform running on the Ethereum Network using Solidity smart contracts; (Application) Google Maps leveraging the Provide Platform APIs and running on a node.js platform.
Resources:
http://provide.services
http://particle.io
https://cloud.google.com/maps-platform/
For a video overview of the detailed solution:
https://youtu.be/TTroWlQCwZc
Public Key Infrastructure (PKI) Market 2021 - Regional Outlook and Competitiv...

Public Key Infrastructure (PKI) Market 2021 - Regional Outlook and Competitive Strategies Analysis to 2027
WSO2Con US 2013 - Identity Management Best Practices with WSO2 Identity Server

This document discusses identity management best practices using WSO2 Identity Server. It covers key topics like versatile authentication, context-based access control, identity provisioning, delegation and federation. Identity management is important for securing access in today's connected business environment where mobile, social and cloud computing are disrupting traditional approaches. The document also provides deployment patterns and discusses customizing user interfaces.
GDPR Part 4: Better Together Quest & SonicWall

Challenges with privileged accounts are: they are many of them an provide access everywhere; they get shared and lack the needed individual accountability of who, what and when use access.
See how ou can address these challenges with top solutions for application-level security and privileged account management from SonicWall and Quest
Wso2con identity patterns

This document discusses enterprise identity management patterns and practices. It covers topics like email, JIRA, SVN, Forrester's Identity Management Maturity Model, Identity as a Service, Single Sign-On, provisioning, delegation, federation, access control, auditing and principles of identity data. The principles of identity data state that identities should not be replicated, business requirements should drive identity replication, replicated identities should be read-only and identity data should be location transparent. It also discusses enforcing consistency and integrity of identity data with policies. The document also briefly outlines features of the WSO2 Identity Server.
Azure IoT from groundup

This document provides an overview of Microsoft's approach to simplifying IoT solutions using Azure services. It discusses how Azure makes it easier to build secure and scalable IoT solutions from device to cloud, provision and manage large numbers of devices at scale, gain insights from IoT data, and infuse devices with intelligence. It also describes key Azure IoT services like IoT Hub, IoT Suite, IoT Central, as well as security measures and a demonstration of data flow using an IoT development kit.
Apps Break Data

How information systems are built or acquired puts information, which is what they should be about, in a secondary place. Our language adapted accordingly, and we no longer talk about information systems but applications. Applications evolved in a way to break data into diverse fragments, tightly coupled with applications and expensive to integrate. The result is technical debt, which is re-paid by taking even bigger "loans", resulting in an ever-increasing technical debt. Software engineering and procurement practices work in sync with market forces to maintain this trend. This talk demonstrates how natural this situation is. The question is: can something be done to reverse the trend?
Mutation Testing for Task-Oriented Chatbots

Conversational agents, or chatbots, are increasingly used to access all sorts of services using natural language. While open-domain chatbots - like ChatGPT - can converse on any topic, task-oriented chatbots - the focus of this paper - are designed for specific tasks, like booking a flight, obtaining customer support, or setting an appointment. Like any other software, task-oriented chatbots need to be properly tested, usually by defining and executing test scenarios (i.e., sequences of user-chatbot interactions). However, there is currently a lack of methods to quantify the completeness and strength of such test scenarios, which can lead to low-quality tests, and hence to buggy chatbots.
To fill this gap, we propose adapting mutation testing (MuT) for task-oriented chatbots. To this end, we introduce a set of mutation operators that emulate faults in chatbot designs, an architecture that enables MuT on chatbots built using heterogeneous technologies, and a practical realisation as an Eclipse plugin. Moreover, we evaluate the applicability, effectiveness and efficiency of our approach on open-source chatbots, with promising results.
More Related Content
What's hot
12th International Conference on Communications Security & Information Assura...

12th International Conference on Communications Security & Information Assurance (CSIA 2021) focuses on all technical and practical aspects of communications security & information assurance for wired and wireless networks. The goal of this conference is to bring together researchers and practitioners from academia and industry to focus on understanding modern security threats and countermeasures, and establishing new collaborations in these areas
Identity Days 2020 - Quelles sont les méthodes et le niveau de sécurisation/r...

Retrouvez le support de la conférence donnée par Hakim Taoussi & Xuan Ahehehinnou lors de la seconde édition des Identity Days.
Burt Kaliski RSA conference 2007

This document discusses the re-emergence of symmetric key infrastructures (SKI) for managing encryption keys. It notes that as data protection grows in importance, SKIs that manage symmetric encryption keys across different applications and locations have advantages over standalone key management solutions. The document reviews lessons learned from previous SKI implementations as well as public key infrastructure (PKI) in designing modern SKIs. It suggests SKIs could fulfill many roles currently relying on public-key cryptography if public-key encryption was not available, and discusses potential technologies beyond PKI for security services like authentication, encryption, and key establishment in the future.
identity based encryption transformation for flexible sharing of encrypted da...

The document proposes an identity-based encryption transformation (IBET) model to address the problem of flexibly sharing encrypted data with more users in public clouds. IBET seamlessly integrates identity-based encryption and identity-based broadcast encryption, allowing data access based on user identities without certificate management. It provides a mechanism to transform an IBE ciphertext into an IBBE ciphertext, enabling access by a new group of users not specified during IBE encryption. The document outlines existing challenges with sharing encrypted data, describes the proposed IBET system and its advantages like security and controllable transformations, and lists system requirements.
Identity-centric interoperability with the Ceramic Protocol

https://ssimeetup.org/identity-centric-interoperability-ceramic-protocol-joel-thorstensson-webinar-57/
Ceramic is a new permissionless protocol for creating and accessing unstoppable documents that serve as the foundation for a connected, interoperable web without silos. Joel Thorstensson is the founder and CTO of 3Box and the primary author of the ceramic protocol as well as several Ethereum standards for identity and will provide a conceptual and technical intro to Ceramic.
At the root of many of the internet’s problems is that apps and services today are built primarily in silos. This includes identity registries and credentials, user data and access permissions, infrastructure, and services. It not only puts control over data and identities in the wrong hands, but it’s a fundamentally outdated and inefficient model for building digital products.
Ceramic unlocks information interoperability between all platforms and services across the web, allowing participants to create and resolve documents for any type of information without any centralized service. Ceramic uses DIDs (Decentralized Identifiers), IPLD (InterPlanetary Linked Data), signed messages, and blockchain anchoring to create a trusted and shared graph of verifiable documents. While flexible, these documents are especially well-suited for self-sovereign identity systems, user-centric data ecosystems, and open web services.
Call for Papers - 15th International Conference on Network Security & Applica...

15th International Conference on Network Security & Applications (CNSA 2022) focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this conference is to bring together researchers and practitioners from academia and industry to focus on understanding modern security threats and counter measures and establishing new collaborations in these areas.
Authors are solicited to contribute to the conference by submitting articles that illustrate research results, projects, surveying works and industrial experiences that describe significant advances in the areas of Security & its applications.
Blockchains and the IoT

This document discusses blockchains and their applications to the Internet of Things (IoT). It provides background on Bitcoin and the key characteristics of blockchain technology, including decentralization, immutability, and trusted transfer of assets. The document then outlines how blockchains could enable faster, safer, and cheaper transactions compared to traditional centralized systems. It proposes using MongoDB as the database layer for enterprise blockchain implementations due to its scalability, availability, data model flexibility, and other features. Finally, the document presents an enterprise blockchain maturity model ranging from centralized to decentralized approaches.
Samsung. Blockchain Keystore SDK and Use Cases

The document discusses Samsung's blockchain keystore, SDK, and use cases. The keystore stores private keys for blockchain services in a secure hardware wallet. It puts consumers in control of their data and credentials. The SDK allows developers to integrate blockchain functionality and provides functions for apps. Example use cases include payments, credentials, secure data storage, and digital rights management.
Build 2017 - B8024 - Connected intelligent things with Windows IoT Core and A...

This document provides an overview of Microsoft's Azure IoT platform and services for connecting, managing and analyzing IoT device data in the cloud. It summarizes Azure IoT Hub for device connectivity and management, Azure IoT Edge for processing data at the edge, and Azure IoT Central for a fully managed IoT SaaS solution. It also outlines capabilities for device security, provisioning and management, and analytics and visualization of IoT data in the Azure cloud.
What to look for in a hosted supplier

Mark Holland, Managing Partner, Baker Tilly Revas Limited
Understanding the security, credibility and flexibility of hosted suppliers and how to make sure the one you choose meets your needs.
Executive Alliance Dallas - Accellion Presentation

In the executive briefing, "How to Avoid BYO Disaster", Paula Skokowski, VP of Products and Marketing at Accellion, Gold Sponsor, provided insight into some of the more important trends and issues related to supporting and securing mobile access to confidential information in the BYOD post-PC era, their drivers, and expected impacts as organizations look to control and secure enterprise content.
От прорывной концепции до комплексного решения для компаний

This document discusses blockchain technology and its applications. It begins by describing the four types of people who are familiar with blockchain to different degrees. It then discusses blockchain fundamentals like distributed ledgers and smart contracts. Several use cases for blockchain are outlined across multiple industries like finance, healthcare, government and more. The strategy and roadmap for an open blockchain platform is presented, focusing on delivering capabilities for identity, privacy, operations and tools. Execution involves proving blockchain concepts, developing horizontal solutions, and creating industry-specific offerings.
DSI Tracker

DSI Tracker is an entry-level media management system from Dynamic Solutions International designed for their Virtual Library. It allows users to track media usage and expiration dates, move media between scratch and retain pools, and perform simple restores directly from virtual media. DSI Tracker was designed to work with DSI VTL Conductor to boost functionality like managing both virtual and physical media.
Rationalization and Defense in Depth - Two Steps Closer to the Cloud

Security represents one of the biggest concerns about cloud computing. In this session we’ll get past the FUD with a real-world look at some key issues. We’ll discuss the infrastructure necessary to support rationalization and security services, explore architecture for defense –in-depth, and deal frankly with the good, the bad, and the ugly in Cloud security. (As presented by Dave Chappelle at OTN Architect Day in Chicago, October 24, 2011.)
IoT on Blockchain Solution Overview

How to track the location of an Internet of Things (IoT) device on the blockchain and view it in a Google Maps reader application.
This solution features: (Hardware) Particle.io Electron device using C++ programming; (Platform) Provide Platform running on the Ethereum Network using Solidity smart contracts; (Application) Google Maps leveraging the Provide Platform APIs and running on a node.js platform.
Resources:
http://provide.services
http://particle.io
https://cloud.google.com/maps-platform/
For a video overview of the detailed solution:
https://youtu.be/TTroWlQCwZc
Public Key Infrastructure (PKI) Market 2021 - Regional Outlook and Competitiv...

Public Key Infrastructure (PKI) Market 2021 - Regional Outlook and Competitive Strategies Analysis to 2027
WSO2Con US 2013 - Identity Management Best Practices with WSO2 Identity Server

This document discusses identity management best practices using WSO2 Identity Server. It covers key topics like versatile authentication, context-based access control, identity provisioning, delegation and federation. Identity management is important for securing access in today's connected business environment where mobile, social and cloud computing are disrupting traditional approaches. The document also provides deployment patterns and discusses customizing user interfaces.
GDPR Part 4: Better Together Quest & SonicWall

Challenges with privileged accounts are: they are many of them an provide access everywhere; they get shared and lack the needed individual accountability of who, what and when use access.
See how ou can address these challenges with top solutions for application-level security and privileged account management from SonicWall and Quest
Wso2con identity patterns

This document discusses enterprise identity management patterns and practices. It covers topics like email, JIRA, SVN, Forrester's Identity Management Maturity Model, Identity as a Service, Single Sign-On, provisioning, delegation, federation, access control, auditing and principles of identity data. The principles of identity data state that identities should not be replicated, business requirements should drive identity replication, replicated identities should be read-only and identity data should be location transparent. It also discusses enforcing consistency and integrity of identity data with policies. The document also briefly outlines features of the WSO2 Identity Server.
Azure IoT from groundup

This document provides an overview of Microsoft's approach to simplifying IoT solutions using Azure services. It discusses how Azure makes it easier to build secure and scalable IoT solutions from device to cloud, provision and manage large numbers of devices at scale, gain insights from IoT data, and infuse devices with intelligence. It also describes key Azure IoT services like IoT Hub, IoT Suite, IoT Central, as well as security measures and a demonstration of data flow using an IoT development kit.
What's hot (20)
12th International Conference on Communications Security & Information Assura...

12th International Conference on Communications Security & Information Assura...
Identity Days 2020 - Quelles sont les méthodes et le niveau de sécurisation/r...

Identity Days 2020 - Quelles sont les méthodes et le niveau de sécurisation/r...
identity based encryption transformation for flexible sharing of encrypted da...

identity based encryption transformation for flexible sharing of encrypted da...
Identity-centric interoperability with the Ceramic Protocol

Identity-centric interoperability with the Ceramic Protocol
Call for Papers - 15th International Conference on Network Security & Applica...

Call for Papers - 15th International Conference on Network Security & Applica...
Build 2017 - B8024 - Connected intelligent things with Windows IoT Core and A...

Build 2017 - B8024 - Connected intelligent things with Windows IoT Core and A...
Executive Alliance Dallas - Accellion Presentation

Executive Alliance Dallas - Accellion Presentation
От прорывной концепции до комплексного решения для компаний

От прорывной концепции до комплексного решения для компаний
Rationalization and Defense in Depth - Two Steps Closer to the Cloud

Rationalization and Defense in Depth - Two Steps Closer to the Cloud
Public Key Infrastructure (PKI) Market 2021 - Regional Outlook and Competitiv...

Public Key Infrastructure (PKI) Market 2021 - Regional Outlook and Competitiv...
WSO2Con US 2013 - Identity Management Best Practices with WSO2 Identity Server

WSO2Con US 2013 - Identity Management Best Practices with WSO2 Identity Server
Recently uploaded
Apps Break Data

How information systems are built or acquired puts information, which is what they should be about, in a secondary place. Our language adapted accordingly, and we no longer talk about information systems but applications. Applications evolved in a way to break data into diverse fragments, tightly coupled with applications and expensive to integrate. The result is technical debt, which is re-paid by taking even bigger "loans", resulting in an ever-increasing technical debt. Software engineering and procurement practices work in sync with market forces to maintain this trend. This talk demonstrates how natural this situation is. The question is: can something be done to reverse the trend?
Mutation Testing for Task-Oriented Chatbots

Conversational agents, or chatbots, are increasingly used to access all sorts of services using natural language. While open-domain chatbots - like ChatGPT - can converse on any topic, task-oriented chatbots - the focus of this paper - are designed for specific tasks, like booking a flight, obtaining customer support, or setting an appointment. Like any other software, task-oriented chatbots need to be properly tested, usually by defining and executing test scenarios (i.e., sequences of user-chatbot interactions). However, there is currently a lack of methods to quantify the completeness and strength of such test scenarios, which can lead to low-quality tests, and hence to buggy chatbots.
To fill this gap, we propose adapting mutation testing (MuT) for task-oriented chatbots. To this end, we introduce a set of mutation operators that emulate faults in chatbot designs, an architecture that enables MuT on chatbots built using heterogeneous technologies, and a practical realisation as an Eclipse plugin. Moreover, we evaluate the applicability, effectiveness and efficiency of our approach on open-source chatbots, with promising results.
What is an RPA CoE? Session 1 – CoE Vision

In the first session, we will review the organization's vision and how this has an impact on the COE Structure.
Topics covered:
• The role of a steering committee
• How do the organization’s priorities determine CoE Structure?
Speaker:
Chris Bolin, Senior Intelligent Automation Architect Anika Systems
Harnessing the Power of NLP and Knowledge Graphs for Opioid Research

Gursev Pirge, PhD
Senior Data Scientist - JohnSnowLabs
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The typical problem in product engineering is not bad strategy, so much as “no strategy”. This leads to confusion, lack of motivation, and incoherent action. The next time you look for a strategy and find an empty space, instead of waiting for it to be filled, I will show you how to fill it in yourself. If you’re wrong, it forces a correction. If you’re right, it helps create focus. I’ll share how I’ve approached this in the past, both what works and lessons for what didn’t work so well.
June Patch Tuesday

Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
“Temporal Event Neural Networks: A More Efficient Alternative to the Transfor...

“Temporal Event Neural Networks: A More Efficient Alternative to the Transfor...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/temporal-event-neural-networks-a-more-efficient-alternative-to-the-transformer-a-presentation-from-brainchip/
Chris Jones, Director of Product Management at BrainChip , presents the “Temporal Event Neural Networks: A More Efficient Alternative to the Transformer” tutorial at the May 2024 Embedded Vision Summit.
The expansion of AI services necessitates enhanced computational capabilities on edge devices. Temporal Event Neural Networks (TENNs), developed by BrainChip, represent a novel and highly efficient state-space network. TENNs demonstrate exceptional proficiency in handling multi-dimensional streaming data, facilitating advancements in object detection, action recognition, speech enhancement and language model/sequence generation. Through the utilization of polynomial-based continuous convolutions, TENNs streamline models, expedite training processes and significantly diminish memory requirements, achieving notable reductions of up to 50x in parameters and 5,000x in energy consumption compared to prevailing methodologies like transformers.
Integration with BrainChip’s Akida neuromorphic hardware IP further enhances TENNs’ capabilities, enabling the realization of highly capable, portable and passively cooled edge devices. This presentation delves into the technical innovations underlying TENNs, presents real-world benchmarks, and elucidates how this cutting-edge approach is positioned to revolutionize edge AI across diverse applications.Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians

Dmitrii Kamaev, PhD
Senior Product Owner - QIAGEN
Northern Engraving | Nameplate Manufacturing Process - 2024

Manufacturing custom quality metal nameplates and badges involves several standard operations. Processes include sheet prep, lithography, screening, coating, punch press and inspection. All decoration is completed in the flat sheet with adhesive and tooling operations following. The possibilities for creating unique durable nameplates are endless. How will you create your brand identity? We can help!
Introduction of Cybersecurity with OSS at Code Europe 2024

I develop the Ruby programming language, RubyGems, and Bundler, which are package managers for Ruby. Today, I will introduce how to enhance the security of your application using open-source software (OSS) examples from Ruby and RubyGems.
The first topic is CVE (Common Vulnerabilities and Exposures). I have published CVEs many times. But what exactly is a CVE? I'll provide a basic understanding of CVEs and explain how to detect and handle vulnerabilities in OSS.
Next, let's discuss package managers. Package managers play a critical role in the OSS ecosystem. I'll explain how to manage library dependencies in your application.
I'll share insights into how the Ruby and RubyGems core team works to keep our ecosystem safe. By the end of this talk, you'll have a better understanding of how to safeguard your code.
How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf

A Mix Chart displays historical data of numbers in a graphical or tabular form. The Kalyan Rajdhani Mix Chart specifically shows the results of a sequence of numbers over different periods.
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
GNSS spoofing via SDR (Criptored Talks 2024)

In the realm of cybersecurity, offensive security practices act as a critical shield. By simulating real-world attacks in a controlled environment, these techniques expose vulnerabilities before malicious actors can exploit them. This proactive approach allows manufacturers to identify and fix weaknesses, significantly enhancing system security.
This presentation delves into the development of a system designed to mimic Galileo's Open Service signal using software-defined radio (SDR) technology. We'll begin with a foundational overview of both Global Navigation Satellite Systems (GNSS) and the intricacies of digital signal processing.
The presentation culminates in a live demonstration. We'll showcase the manipulation of Galileo's Open Service pilot signal, simulating an attack on various software and hardware systems. This practical demonstration serves to highlight the potential consequences of unaddressed vulnerabilities, emphasizing the importance of offensive security practices in safeguarding critical infrastructure.
Principle of conventional tomography-Bibash Shahi ppt..pptx

before the computed tomography, it had been widely used.
GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph

Tomaz Bratanic
Graph ML and GenAI Expert - Neo4j
Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency

Freshworks creates AI-boosted business software that helps employees work more efficiently and effectively. Managing data across multiple RDBMS and NoSQL databases was already a challenge at their current scale. To prepare for 10X growth, they knew it was time to rethink their database strategy. Learn how they architected a solution that would simplify scaling while keeping costs under control.
JavaLand 2024: Application Development Green Masterplan

My presentation slides I used at JavaLand 2024
HCL Notes and Domino License Cost Reduction in the World of DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-and-domino-license-cost-reduction-in-the-world-of-dlau/
The introduction of DLAU and the CCB & CCX licensing model caused quite a stir in the HCL community. As a Notes and Domino customer, you may have faced challenges with unexpected user counts and license costs. You probably have questions on how this new licensing approach works and how to benefit from it. Most importantly, you likely have budget constraints and want to save money where possible. Don’t worry, we can help with all of this!
We’ll show you how to fix common misconfigurations that cause higher-than-expected user counts, and how to identify accounts which you can deactivate to save money. There are also frequent patterns that can cause unnecessary cost, like using a person document instead of a mail-in for shared mailboxes. We’ll provide examples and solutions for those as well. And naturally we’ll explain the new licensing model.
Join HCL Ambassador Marc Thomas in this webinar with a special guest appearance from Franz Walder. It will give you the tools and know-how to stay on top of what is going on with Domino licensing. You will be able lower your cost through an optimized configuration and keep it low going forward.
These topics will be covered
- Reducing license cost by finding and fixing misconfigurations and superfluous accounts
- How do CCB and CCX licenses really work?
- Understanding the DLAU tool and how to best utilize it
- Tips for common problem areas, like team mailboxes, functional/test users, etc
- Practical examples and best practices to implement right away
Recently uploaded (20)
9 CEO's who hit $100m ARR Share Their Top Growth Tactics Nathan Latka, Founde...

9 CEO's who hit $100m ARR Share Their Top Growth Tactics Nathan Latka, Founde...
Harnessing the Power of NLP and Knowledge Graphs for Opioid Research

Harnessing the Power of NLP and Knowledge Graphs for Opioid Research
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...
“Temporal Event Neural Networks: A More Efficient Alternative to the Transfor...

“Temporal Event Neural Networks: A More Efficient Alternative to the Transfor...
Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians

Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians
Northern Engraving | Nameplate Manufacturing Process - 2024

Northern Engraving | Nameplate Manufacturing Process - 2024
Introduction of Cybersecurity with OSS at Code Europe 2024

Introduction of Cybersecurity with OSS at Code Europe 2024
How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf

How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Nordic Marketo Engage User Group_June 13_ 2024.pptx

Nordic Marketo Engage User Group_June 13_ 2024.pptx
Principle of conventional tomography-Bibash Shahi ppt..pptx

Principle of conventional tomography-Bibash Shahi ppt..pptx
GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph

GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph
Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency

Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency
JavaLand 2024: Application Development Green Masterplan

JavaLand 2024: Application Development Green Masterplan
HCL Notes and Domino License Cost Reduction in the World of DLAU

HCL Notes and Domino License Cost Reduction in the World of DLAU
KISS API
- 1. Microservice centric architecture and security – Keep it simple and secure (KISS) External Internal Workflow Management ServiceDiscovery DeveloperServices WorkflowManagement ServiceDiscovery DeveloperServices Customer applications Internal application Consumers Private Cloud Public Cloud External Firewall Enterprise Systems Microservices Gateway / Orchestration Internal Microservices UUID Token UUID Token
