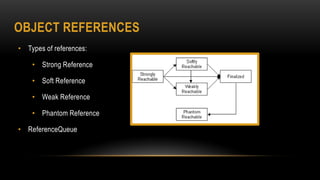
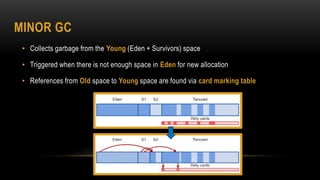
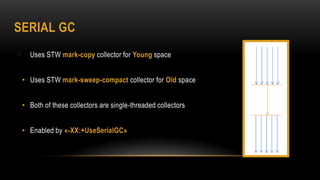
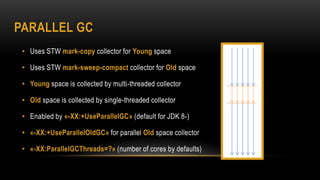
This document provides an overview of key concepts in the Java Virtual Machine (JVM) including memory management, garbage collection techniques, class loading, execution engines, multi-threading, and the Java Native Interface (JNI). It discusses topics such as heap vs non-heap memory, minor vs major garbage collection, just-in-time compilation, safe points, and how to call native methods from Java using JNI.






![OBJECT SCHEMA
• Objects
• Mark word [4/8 bytes]
• Class pointer [4/8 bytes]
• Fields ...
• Arrays
• Mark word [4/8 bytes]
• Class pointer [4/8 bytes]
• Array length [4 bytes]
• Elements …](https://image.slidesharecdn.com/jvmunderthehood-170105195425/85/JVM-Under-the-Hood-11-320.jpg)