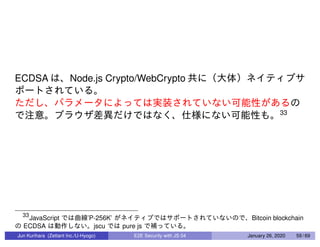
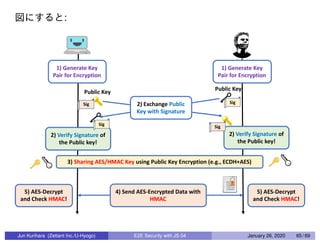
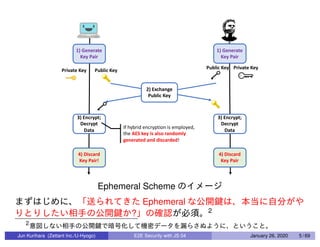
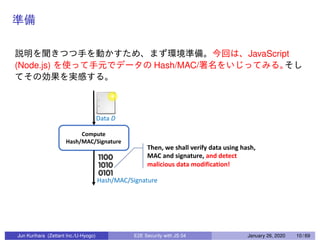
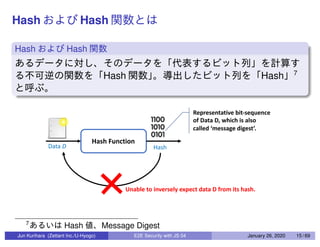
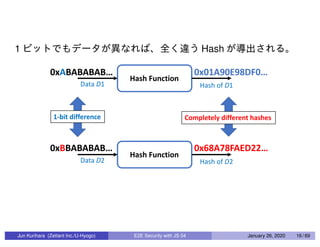
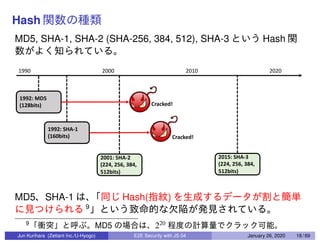
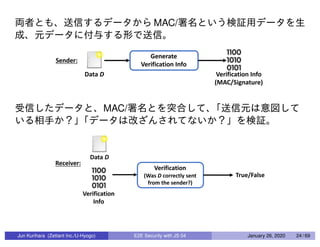
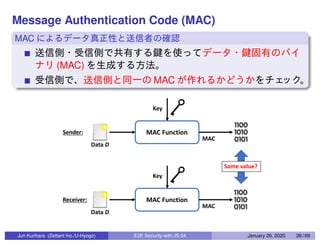
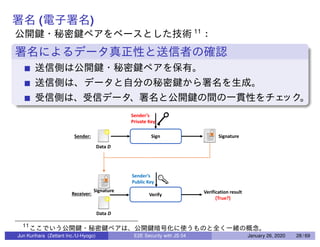
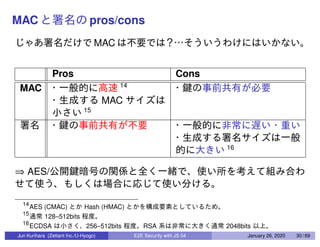
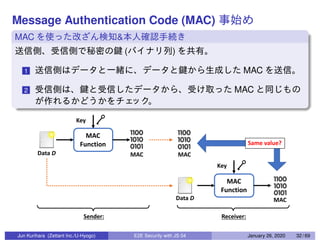
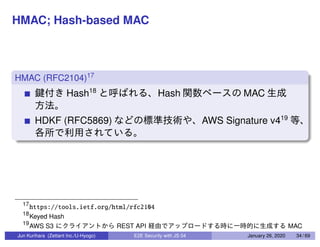
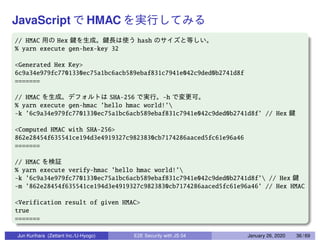
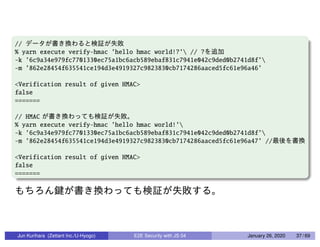
This document discusses end-to-end (E2E) security in JavaScript, detailing various cryptographic methods including AES, RSA, and HMAC. It covers concepts of ephemeral schemes, message authentication codes (MAC), hashing techniques, and practical implementations using Node.js and relevant libraries. The presentation appears to be from a technical session led by Jun Kurihara at Zettant Inc. on January 26, 2020.
























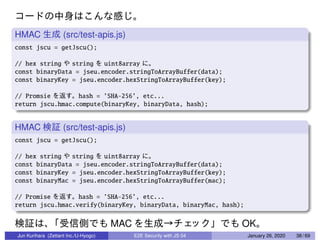
![MAC (JS )
CMAC; Cipher-based MAC (NIST SP800-38B20
)
(e.g., AES) CBC Hash
MAC
GMAC; Galois MAC (NIST SP800-38D21
)
(e.g., AES) Galois Counter Mode (GCM)
MAC 22
Hash
MAC GMAC
CMAC/GMAC
20
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-38b.pdf
21
https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-38d.pdf
22
F[x]/(x128 +x7 +x2 +x+1) = F2128
Jun Kurihara (Zettant Inc./U-Hyogo) E2E Security with JS 04 January 26, 2020 39 / 69](https://image.slidesharecdn.com/04-200126114119/85/JavaScript-End-to-End-4-39-320.jpg)