ISO.IEC 27001 27002-2013
•
0 likes•155 views
This document outlines an information security management standard with 18 sections and 114 controls organized under 14 groups. The standard provides guidance on security policies, asset management, access control, cryptography, physical security, operations, systems development, supplier relationships, communications, incident management, business continuity, and compliance. It was authored by Jason P. Rusch and references ISO/IEC 27001 and 27002 for information security standards.
Report
Share
Report
Share
Download to read offline
Recommended
Developing a Security Policy That Will Survive

The beginning of a sound information system security program is the development of a security policy document that will help protect the organization�s assets and reputation. Often, the policy is written and placed on the shelf to be admired, but is not implemented, enforced or maintained. Not having a security policy today is a legal liability for any corporation, but what about policies that are written, and then never enforced? This presentation explores the life-cycle and methodology for successful security policy development, implementation, maintenance, and continued enforcement. Coordination with executive management, information system users, legal counsel, and security professionals are all part of the success model. Learn specific activities that have been used in the field to establish the security policy as part of the organization�s framework for operation and how to revive or rework existing policy that has not been implemented.
Jesper Frederikson - Key learnings from scaling saas successes and failures 

"As you set out to scale your business, the leadership team has address a range of critical topics such as: -
develop and formulate your culture – and maintain it as you grow
create and implement a clear planning & management framework that ensures all functions are aligned
hire, enable, develop and maintain a world-class team
build a predictable and effective revenue generating “machine”
make your customers successful and turn them into vocal fans
Learn from successes – and failures – accumulated at Postini/Google, Symantec (integrating MessageLabs), DocuSign, Okta, Siteimprove and Keepit and leave armed with the key things to be aware of as you begin to innovate & execute on multiple dimensions in order to scale quickly and profitably.
RESILIA positioning map

Here is a positioning model of RESILIA framework in the Cyber Resilience environment
Inspec, or how to translate compliance spreadsheets into code

InSpec allows you to examine any node with controls that can written in simple form and then executed in an automated fashion as part of your software development process. We'll talk about the basic concepts of InSpec, how to write controls and how to use the reported output to take your compliance spreadsheets into a automated development world.
What "good at software" looks like

Talk from the Pluralsight LIVE! conference that reviews key characteristics of quality software teams.
Recommended
Developing a Security Policy That Will Survive

The beginning of a sound information system security program is the development of a security policy document that will help protect the organization�s assets and reputation. Often, the policy is written and placed on the shelf to be admired, but is not implemented, enforced or maintained. Not having a security policy today is a legal liability for any corporation, but what about policies that are written, and then never enforced? This presentation explores the life-cycle and methodology for successful security policy development, implementation, maintenance, and continued enforcement. Coordination with executive management, information system users, legal counsel, and security professionals are all part of the success model. Learn specific activities that have been used in the field to establish the security policy as part of the organization�s framework for operation and how to revive or rework existing policy that has not been implemented.
Jesper Frederikson - Key learnings from scaling saas successes and failures 

"As you set out to scale your business, the leadership team has address a range of critical topics such as: -
develop and formulate your culture – and maintain it as you grow
create and implement a clear planning & management framework that ensures all functions are aligned
hire, enable, develop and maintain a world-class team
build a predictable and effective revenue generating “machine”
make your customers successful and turn them into vocal fans
Learn from successes – and failures – accumulated at Postini/Google, Symantec (integrating MessageLabs), DocuSign, Okta, Siteimprove and Keepit and leave armed with the key things to be aware of as you begin to innovate & execute on multiple dimensions in order to scale quickly and profitably.
RESILIA positioning map

Here is a positioning model of RESILIA framework in the Cyber Resilience environment
Inspec, or how to translate compliance spreadsheets into code

InSpec allows you to examine any node with controls that can written in simple form and then executed in an automated fashion as part of your software development process. We'll talk about the basic concepts of InSpec, how to write controls and how to use the reported output to take your compliance spreadsheets into a automated development world.
What "good at software" looks like

Talk from the Pluralsight LIVE! conference that reviews key characteristics of quality software teams.
Integrating Multiple IT Security Standards

Integrating Multiple IT Security StandardsMuhammad Faisal Naqvi, CISSP, CISA, AMBCI, ITIL, ISMS LA n Master
Presentation delivered on E-Crime Congress Middle East, DubaiHow does ISO 27001 Certification secure My organization?

Step by step read the given blog and learn how does ISO 27001 Certification secure My organization. Read More Link - https://bit.ly/3n6WKCN
Protected Workloads Security Shakedown

In this session we cover running PROTECTED workloads described by the Australian Cyber Security Centre, answer cloud security questions that we hear from customers, and impart best practices distilled from our experience working with organizations around the world. This session is for everyone who is curious about the cloud, cautious about the cloud, or excited about the cloud.
Iso 27001 certification

Certvalue is one of the leading ISO consulting & certification company with experts in every industry sector based out in your location. We focus more on improvement, best practices & profit rather than just documentation or certification. We help organisation to achieve certification at affordable cost.
What is ISO 27001 ISMS

ISO 27001 is a well-recognized international industry standard for benchmarking Information Security Management Systems (ISMS).
Information Security Management System ISO/IEC 27001:2005

Information Security Management System - ISO/IEC 27001:2005
Introduction and Requirements
Talk1 esc3 muscl-standards and regulation_v1_1

A quick introduction to ISO 27001, 27002, FFIEC, GDPR and Mauritius DPA 2017
UNINFO - BIG DATA & Information Security Standards - Guasconi

Fabio Guasconi ha presentato al 3rd ESA International Security Symposium relazioni fra BIG DATA e Information Security Standards.
ISO/IEC 27001, ISO/IEC 27002 and ISO/IEC 27032: How do they map?

ISO/IEC 27001, ISO/IEC 27002 and ISO/IEC 27032: How do they map?
Because of the ongoing increase in consumer data collection, breaches have also been increasing.
In this regards the information security, data privacy, and cybersecurity standards provide some guidelines and requirements on how to better manage and deal with such breaches.
Amongst others, the webinar covers:
• ISO 27032:2012 – A Framework for Cybersecurity Risks
• ISO/IEC 27000-series, Standards, 27001 vs 27002
• ISO 27002:2022 and 27001:2022 Updates
Presenters:
Danny Manimbo
Danny Manimbo is a Principal with Schellman, based in Denver, Colorado. As a member of Schellman’s West Coast/Mountain region management team, Danny is primarily responsible for co-leading Schellman's ISO practice and the development and oversight of Schellman's SOC practice line, as well as specialty practices such as HIPAA. Danny has been with Schellman for nine years and has over 11 years of experience in providing data security audit and compliance services.
Erik Tomasi
Erik Tomasi is the Managing Partner at EMTsec, a security consulting firm based in Miami and New York. He leads the firm’s consulting division and manages client relationships across several industry sectors. Mr. Tomasi is considered an expert in information security, risk management, and technology management.
Sawyer Miller
Sawyer is a Senior Manager who oversees the ISO practice for risk3sixty, an Atlanta-based Security, Privacy, and Compliance firm helping clients implement business-first information security and compliance programs.
Date: June 22, 2022
Tags: ISO, ISO/IEC 27001, ISO/IEC 27002, ISO/IEC 27032, Data protection, Data Privacy, Cybersecurity, Information Security
-------------------------------------------------------------------------------
Find out more about ISO training and certification services
Training: https://pecb.com/whitepaper/isoiec-270022022--information-security-cybersecurity-and-privacy-protection
https://pecb.com/whitepaper/no-iso-27001-certified-companies-among-largest-data-breaches-2014-2015
https://pecb.com/whitepaper/isoiec-270022013-information-technology---security-techniques-code-of-practice-for-information-security-controls
Webinars: https://pecb.com/webinars
Article: https://pecb.com/article
Whitepaper: https://pecb.com/whitepaper
-------------------------------------------------------------------------------
For more information about PECB:
Website: https://pecb.com/
LinkedIn: https://www.linkedin.com/company/pecb/
Facebook: https://www.facebook.com/PECBInternational/
Slideshare: http://www.slideshare.net/PECBCERTIFICATION
YouTube video: https://youtu.be/fE3DqISAfQY
2008: Web Application Security Tutorial

Presented at a four hour pre-conference at the 2008 Annual Educause National Conference.
Integrated Management Systems

Management systems are merging. Is quality at the center or part of the mix?
Cybersecurity Frameworks for DMZCON23 230905.pdf

Cybersecurity Frameworks: Lists, Links, How to Choose, Key Considerations, and Mappings
Understanding the NIST Risk Management Framework: 800-37 Rev. 2

Denise Tawwab's presentation on "Understanding the NIST Risk Management Framework" given at the Techno Security & Digital Forensics Conference on June 3, 2019 in Myrtle Beach, SC.
More Related Content
What's hot
Integrating Multiple IT Security Standards

Integrating Multiple IT Security StandardsMuhammad Faisal Naqvi, CISSP, CISA, AMBCI, ITIL, ISMS LA n Master
Presentation delivered on E-Crime Congress Middle East, DubaiHow does ISO 27001 Certification secure My organization?

Step by step read the given blog and learn how does ISO 27001 Certification secure My organization. Read More Link - https://bit.ly/3n6WKCN
Protected Workloads Security Shakedown

In this session we cover running PROTECTED workloads described by the Australian Cyber Security Centre, answer cloud security questions that we hear from customers, and impart best practices distilled from our experience working with organizations around the world. This session is for everyone who is curious about the cloud, cautious about the cloud, or excited about the cloud.
What's hot (6)
How does ISO 27001 Certification secure My organization?

How does ISO 27001 Certification secure My organization?
Similar to ISO.IEC 27001 27002-2013
Iso 27001 certification

Certvalue is one of the leading ISO consulting & certification company with experts in every industry sector based out in your location. We focus more on improvement, best practices & profit rather than just documentation or certification. We help organisation to achieve certification at affordable cost.
What is ISO 27001 ISMS

ISO 27001 is a well-recognized international industry standard for benchmarking Information Security Management Systems (ISMS).
Information Security Management System ISO/IEC 27001:2005

Information Security Management System - ISO/IEC 27001:2005
Introduction and Requirements
Talk1 esc3 muscl-standards and regulation_v1_1

A quick introduction to ISO 27001, 27002, FFIEC, GDPR and Mauritius DPA 2017
UNINFO - BIG DATA & Information Security Standards - Guasconi

Fabio Guasconi ha presentato al 3rd ESA International Security Symposium relazioni fra BIG DATA e Information Security Standards.
ISO/IEC 27001, ISO/IEC 27002 and ISO/IEC 27032: How do they map?

ISO/IEC 27001, ISO/IEC 27002 and ISO/IEC 27032: How do they map?
Because of the ongoing increase in consumer data collection, breaches have also been increasing.
In this regards the information security, data privacy, and cybersecurity standards provide some guidelines and requirements on how to better manage and deal with such breaches.
Amongst others, the webinar covers:
• ISO 27032:2012 – A Framework for Cybersecurity Risks
• ISO/IEC 27000-series, Standards, 27001 vs 27002
• ISO 27002:2022 and 27001:2022 Updates
Presenters:
Danny Manimbo
Danny Manimbo is a Principal with Schellman, based in Denver, Colorado. As a member of Schellman’s West Coast/Mountain region management team, Danny is primarily responsible for co-leading Schellman's ISO practice and the development and oversight of Schellman's SOC practice line, as well as specialty practices such as HIPAA. Danny has been with Schellman for nine years and has over 11 years of experience in providing data security audit and compliance services.
Erik Tomasi
Erik Tomasi is the Managing Partner at EMTsec, a security consulting firm based in Miami and New York. He leads the firm’s consulting division and manages client relationships across several industry sectors. Mr. Tomasi is considered an expert in information security, risk management, and technology management.
Sawyer Miller
Sawyer is a Senior Manager who oversees the ISO practice for risk3sixty, an Atlanta-based Security, Privacy, and Compliance firm helping clients implement business-first information security and compliance programs.
Date: June 22, 2022
Tags: ISO, ISO/IEC 27001, ISO/IEC 27002, ISO/IEC 27032, Data protection, Data Privacy, Cybersecurity, Information Security
-------------------------------------------------------------------------------
Find out more about ISO training and certification services
Training: https://pecb.com/whitepaper/isoiec-270022022--information-security-cybersecurity-and-privacy-protection
https://pecb.com/whitepaper/no-iso-27001-certified-companies-among-largest-data-breaches-2014-2015
https://pecb.com/whitepaper/isoiec-270022013-information-technology---security-techniques-code-of-practice-for-information-security-controls
Webinars: https://pecb.com/webinars
Article: https://pecb.com/article
Whitepaper: https://pecb.com/whitepaper
-------------------------------------------------------------------------------
For more information about PECB:
Website: https://pecb.com/
LinkedIn: https://www.linkedin.com/company/pecb/
Facebook: https://www.facebook.com/PECBInternational/
Slideshare: http://www.slideshare.net/PECBCERTIFICATION
YouTube video: https://youtu.be/fE3DqISAfQY
2008: Web Application Security Tutorial

Presented at a four hour pre-conference at the 2008 Annual Educause National Conference.
Integrated Management Systems

Management systems are merging. Is quality at the center or part of the mix?
Cybersecurity Frameworks for DMZCON23 230905.pdf

Cybersecurity Frameworks: Lists, Links, How to Choose, Key Considerations, and Mappings
Understanding the NIST Risk Management Framework: 800-37 Rev. 2

Denise Tawwab's presentation on "Understanding the NIST Risk Management Framework" given at the Techno Security & Digital Forensics Conference on June 3, 2019 in Myrtle Beach, SC.
Sarwono sutikno forum tik utk standardisasi keamanan kartu cerdas - 4 nov 2...

Sarwono sutikno forum tik utk standardisasi keamanan kartu cerdas - 4 nov 2...Sarwono Sutikno, Dr.Eng.,CISA,CISSP,CISM,CSX-F
Design Control atau Risk Treatment untuk Kartu Cerdas untuk Pembayaran. Control dari Tata kelola, manajemen sampai tingkat perangkat.ISO 27001 INFORMATION TECHNOLOGY MANAGEMENT SYSTEM

The new ISO 45001:2018 standard for Occupational health and safety is now an ISO standard unlike previous version OHSAS 18001 standard. Its core text remains similar to ISO 9001:2015 standard and other ISO standards having 10 clauses.
RSA: CSA GRC Stack Update for the CSA Atlanta Chapter

RSA CSA GRC Stack Update for the Atlanta CSA Chapter by Phil Agcaoili
Similar to ISO.IEC 27001 27002-2013 (20)
Information Security Management System ISO/IEC 27001:2005

Information Security Management System ISO/IEC 27001:2005
UNINFO - BIG DATA & Information Security Standards - Guasconi

UNINFO - BIG DATA & Information Security Standards - Guasconi
ISO/IEC 27001, ISO/IEC 27002 and ISO/IEC 27032: How do they map?

ISO/IEC 27001, ISO/IEC 27002 and ISO/IEC 27032: How do they map?
Understanding the NIST Risk Management Framework: 800-37 Rev. 2

Understanding the NIST Risk Management Framework: 800-37 Rev. 2
Sarwono sutikno forum tik utk standardisasi keamanan kartu cerdas - 4 nov 2...

Sarwono sutikno forum tik utk standardisasi keamanan kartu cerdas - 4 nov 2...
ISO 27001 INFORMATION TECHNOLOGY MANAGEMENT SYSTEM

ISO 27001 INFORMATION TECHNOLOGY MANAGEMENT SYSTEM
RSA: CSA GRC Stack Update for the CSA Atlanta Chapter

RSA: CSA GRC Stack Update for the CSA Atlanta Chapter
More from Jason Rusch - CISSP CGEIT CISM CISA GNSA
DATA PROTECTION LAWS OF THE WORLD

International Information Data Security Laws & Regulations
Great document authored by DLA Piper
Common Security Framework Summary

Authored my own "Common Security Framework Summary" because I wasn't satisfied with anything I found online.
More from Jason Rusch - CISSP CGEIT CISM CISA GNSA (20)
Information_Governance_Risk_Compliance_Frameworks (v5)

Information_Governance_Risk_Compliance_Frameworks (v5)
Recently uploaded
-- June 2024 is National Volunteer Month --

Check out our June display of books on voluntary organisations
Discover the innovative and creative projects that highlight my journey throu...

Discover the innovative and creative projects that highlight my journey through Full Sail University. Below, you’ll find a collection of my work showcasing my skills and expertise in digital marketing, event planning, and media production.
3.0 Project 2_ Developing My Brand Identity Kit.pptx

A personal brand exploration presentation summarizes an individual's unique qualities and goals, covering strengths, values, passions, and target audience. It helps individuals understand what makes them stand out, their desired image, and how they aim to achieve it.
buy old yahoo accounts buy yahoo accounts

As a business owner, I understand the importance of having a strong online presence and leveraging various digital platforms to reach and engage with your target audience. One often overlooked yet highly valuable asset in this regard is the humble Yahoo account. While many may perceive Yahoo as a relic of the past, the truth is that these accounts still hold immense potential for businesses of all sizes.
In the Adani-Hindenburg case, what is SEBI investigating.pptx

Adani SEBI investigation revealed that the latter had sought information from five foreign jurisdictions concerning the holdings of the firm’s foreign portfolio investors (FPIs) in relation to the alleged violations of the MPS Regulations. Nevertheless, the economic interest of the twelve FPIs based in tax haven jurisdictions still needs to be determined. The Adani Group firms classed these FPIs as public shareholders. According to Hindenburg, FPIs were used to get around regulatory standards.
Evgen Osmak: Methods of key project parameters estimation: from the shaman-in...

Evgen Osmak: Methods of key project parameters estimation: from the shaman-inspired to the data-driven praxis (UA)
Kyiv PMDay 2024 Summer
Website – www.pmday.org
Youtube – https://www.youtube.com/startuplviv
FB – https://www.facebook.com/pmdayconference
Building Your Employer Brand with Social Media

Presented at The Global HR Summit, 6th June 2024
In this keynote, Luan Wise will provide invaluable insights to elevate your employer brand on social media platforms including LinkedIn, Facebook, Instagram, X (formerly Twitter) and TikTok. You'll learn how compelling content can authentically showcase your company culture, values, and employee experiences to support your talent acquisition and retention objectives. Additionally, you'll understand the power of employee advocacy to amplify reach and engagement – helping to position your organization as an employer of choice in today's competitive talent landscape.
Tata Group Dials Taiwan for Its Chipmaking Ambition in Gujarat’s Dholera

The Tata Group, a titan of Indian industry, is making waves with its advanced talks with Taiwanese chipmakers Powerchip Semiconductor Manufacturing Corporation (PSMC) and UMC Group. The goal? Establishing a cutting-edge semiconductor fabrication unit (fab) in Dholera, Gujarat. This isn’t just any project; it’s a potential game changer for India’s chipmaking aspirations and a boon for investors seeking promising residential projects in dholera sir.
Visit : https://www.avirahi.com/blog/tata-group-dials-taiwan-for-its-chipmaking-ambition-in-gujarats-dholera/
Premium MEAN Stack Development Solutions for Modern Businesses

Stay ahead of the curve with our premium MEAN Stack Development Solutions. Our expert developers utilize MongoDB, Express.js, AngularJS, and Node.js to create modern and responsive web applications. Trust us for cutting-edge solutions that drive your business growth and success.
Know more: https://www.synapseindia.com/technology/mean-stack-development-company.html
Top mailing list providers in the USA.pptx

Discover the top mailing list providers in the USA, offering targeted lists, segmentation, and analytics to optimize your marketing campaigns and drive engagement.
Anny Serafina Love - Letter of Recommendation by Kellen Harkins, MS.

This letter, written by Kellen Harkins, Course Director at Full Sail University, commends Anny Love's exemplary performance in the Video Sharing Platforms class. It highlights her dedication, willingness to challenge herself, and exceptional skills in production, editing, and marketing across various video platforms like YouTube, TikTok, and Instagram.
Recruiting in the Digital Age: A Social Media Masterclass

In this masterclass, presented at the Global HR Summit on 5th June 2024, Luan Wise explored the essential features of social media platforms that support talent acquisition, including LinkedIn, Facebook, Instagram, X (formerly Twitter) and TikTok.
Company Valuation webinar series - Tuesday, 4 June 2024

This session provided an update as to the latest valuation data in the UK and then delved into a discussion on the upcoming election and the impacts on valuation. We finished, as always with a Q&A
Recently uploaded (20)
Auditing study material for b.com final year students

Auditing study material for b.com final year students
Discover the innovative and creative projects that highlight my journey throu...

Discover the innovative and creative projects that highlight my journey throu...
3.0 Project 2_ Developing My Brand Identity Kit.pptx

3.0 Project 2_ Developing My Brand Identity Kit.pptx
In the Adani-Hindenburg case, what is SEBI investigating.pptx

In the Adani-Hindenburg case, what is SEBI investigating.pptx
Evgen Osmak: Methods of key project parameters estimation: from the shaman-in...

Evgen Osmak: Methods of key project parameters estimation: from the shaman-in...
The Influence of Marketing Strategy and Market Competition on Business Perfor...

The Influence of Marketing Strategy and Market Competition on Business Perfor...
Tata Group Dials Taiwan for Its Chipmaking Ambition in Gujarat’s Dholera

Tata Group Dials Taiwan for Its Chipmaking Ambition in Gujarat’s Dholera
Premium MEAN Stack Development Solutions for Modern Businesses

Premium MEAN Stack Development Solutions for Modern Businesses
Anny Serafina Love - Letter of Recommendation by Kellen Harkins, MS.

Anny Serafina Love - Letter of Recommendation by Kellen Harkins, MS.
The Influence of Marketing Strategy and Market Competition on Business Perfor...

The Influence of Marketing Strategy and Market Competition on Business Perfor...
Recruiting in the Digital Age: A Social Media Masterclass

Recruiting in the Digital Age: A Social Media Masterclass
Company Valuation webinar series - Tuesday, 4 June 2024

Company Valuation webinar series - Tuesday, 4 June 2024
ISO.IEC 27001 27002-2013
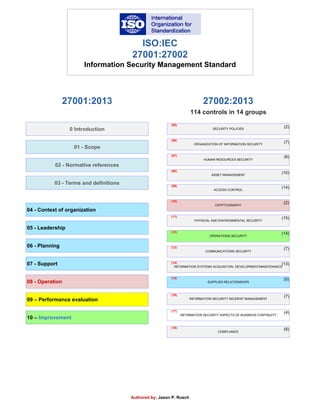
- 1. ISO:IEC 27001:27002 Information Security Management Standard 0 Introduction 01 - Scope 02 - Normative references 03 - Terms and definitions Authored by; Jason P. Rusch 04 - Context of organization 05 - Leadership 06 - Planning 07 - Support 08 - Operation 10 – Improvement 09 – Performance evaluation SECURITY POLICIES ORGANIZATION OF INFORMATION SECURITY HUMAN RESOURCES SECURITY ASSET MANAGEMENT ACCESS CONTROL CRYPTOGRAPHY PHYSICAL AND ENVIRONMENTAL SECURITY OPERATIONS SECURITY INFORMATION SYSTEMS ACQUISITION, DEVELOPMENT/MAINTENANCE SUPPLIER RELATIONSHIPS COMMUNICATIONS SECURITY (11) (10) (12) (13) (14) (15) (09) (08) (07) (06) (05) INFORMATION SECURITY INCIDENT MANAGEMENT (16) INFORMATION SECURITY ASPECTS OF BUSINESS CONTINUITY (17) COMPLIANCE (18) (2) (7) (6) (10) (14) (2) (15) (14) (7) (13) (5) (7) (4) (8) 114 controls in 14 groups 27002:201327001:2013
