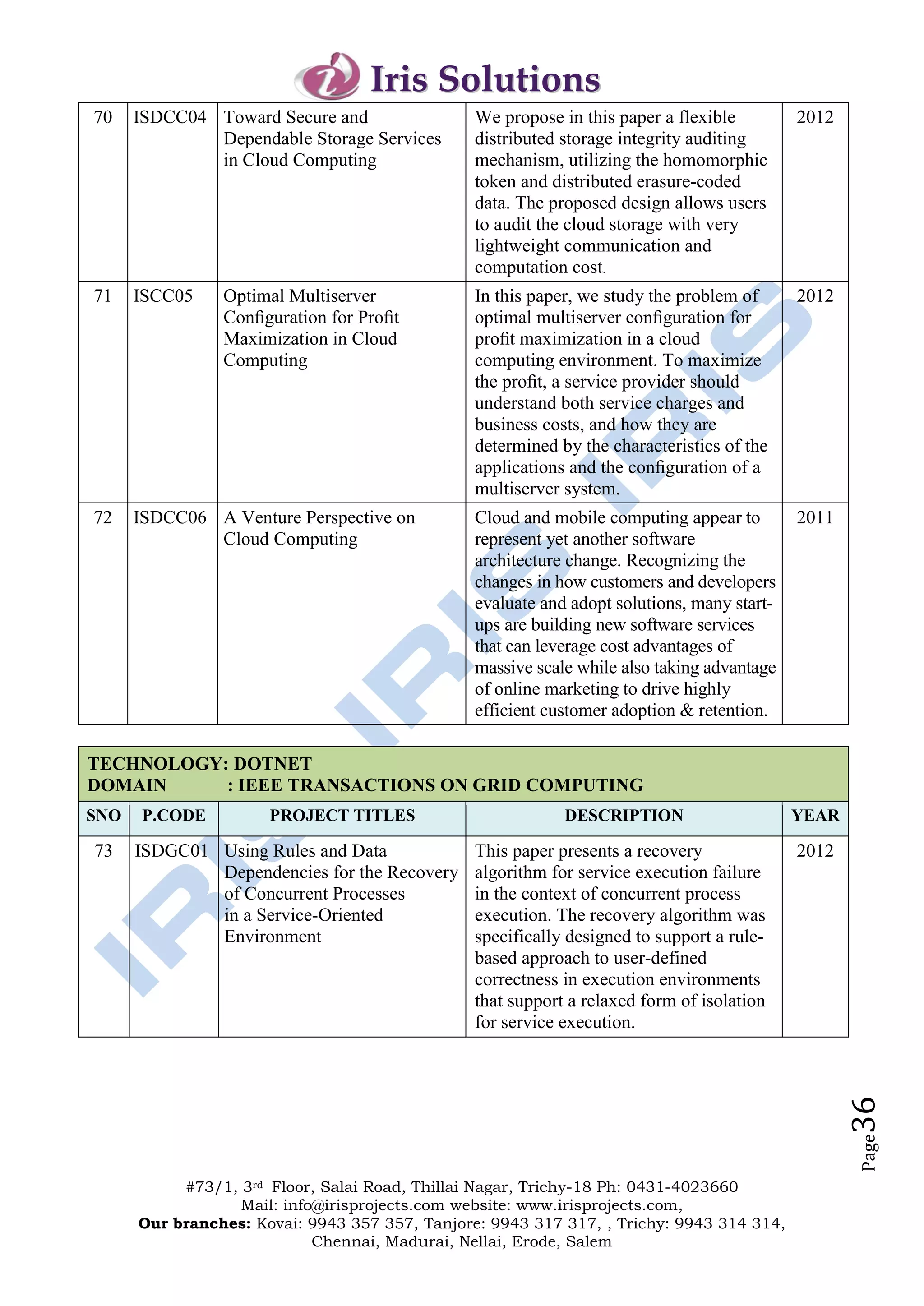
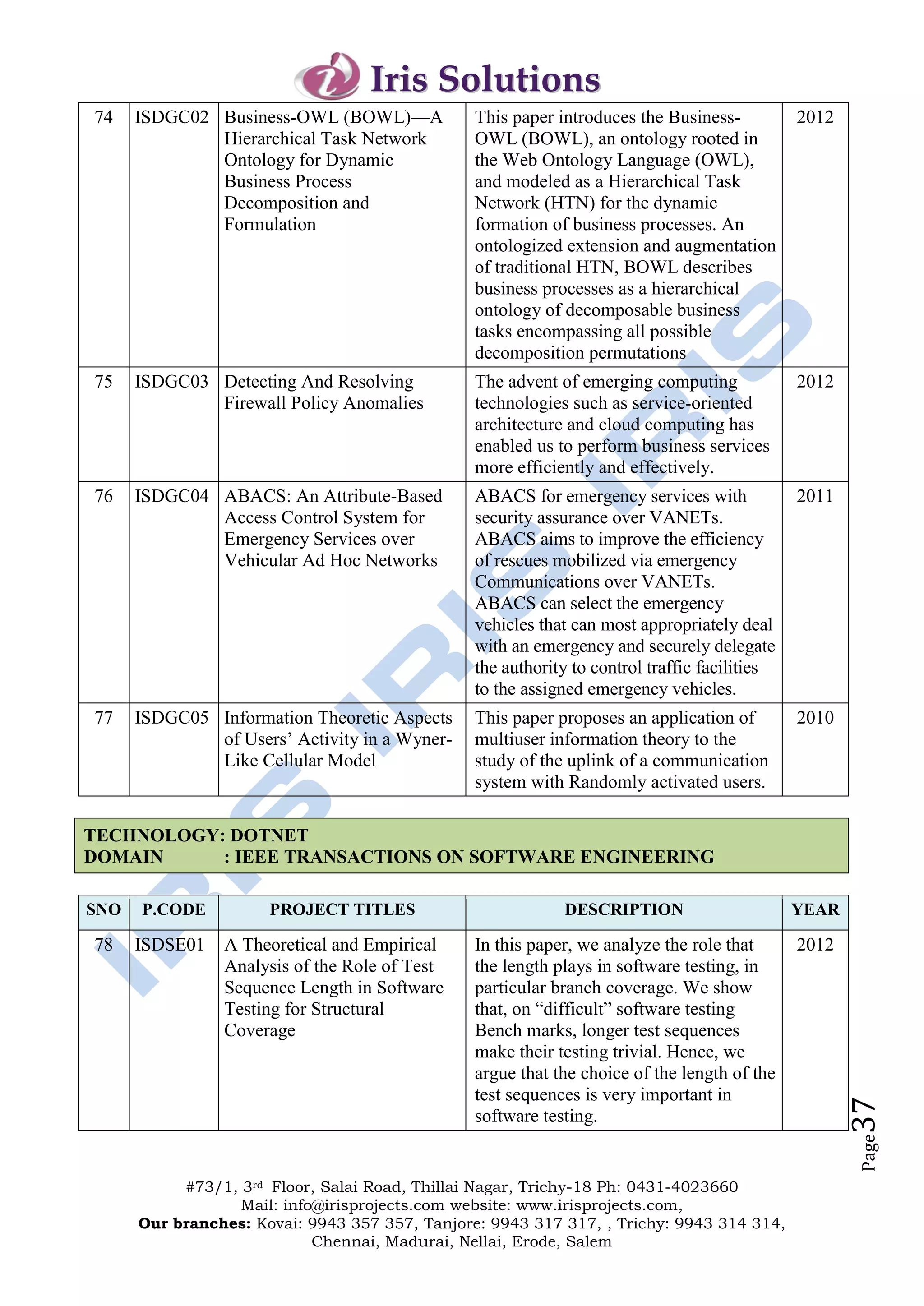
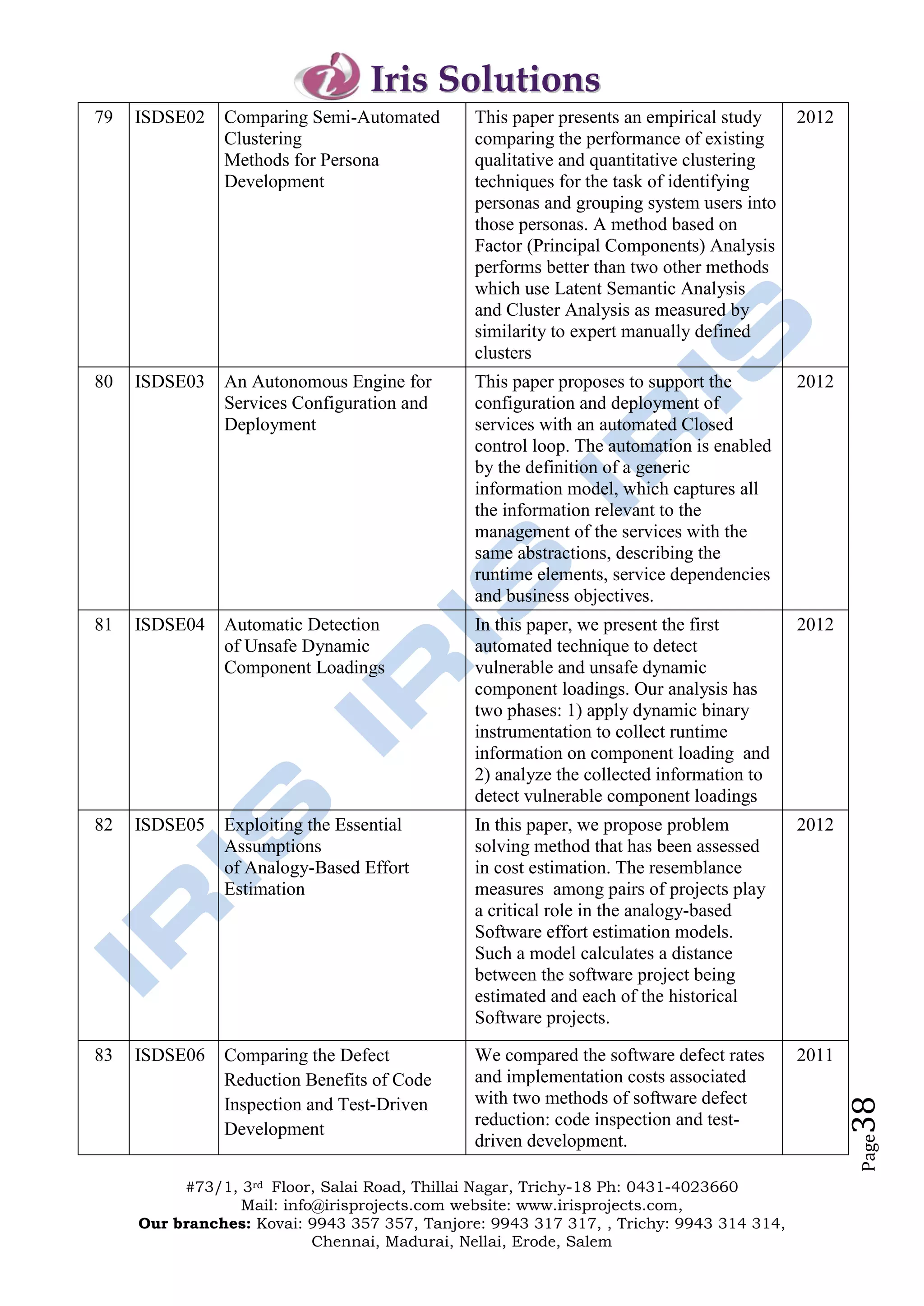
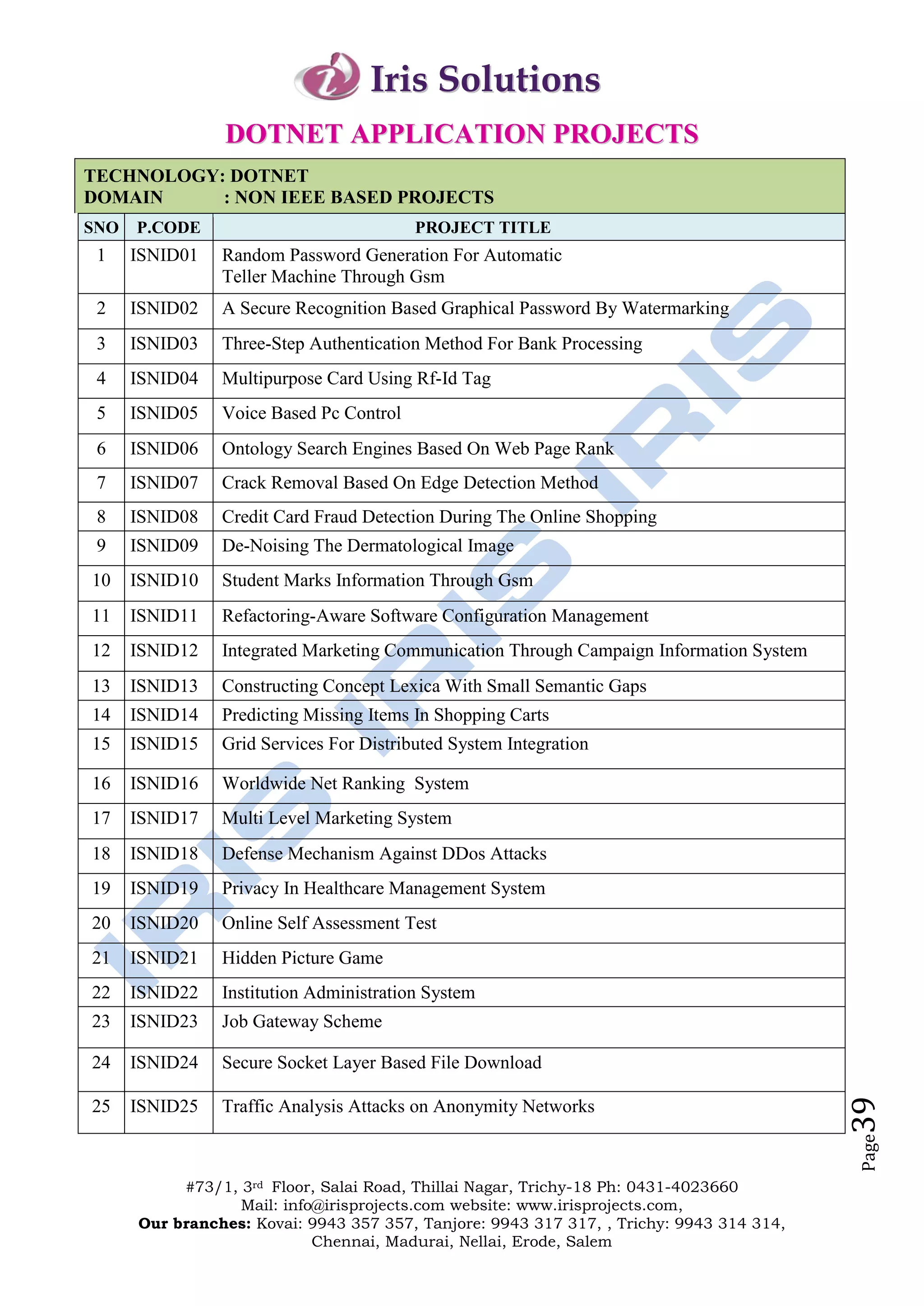
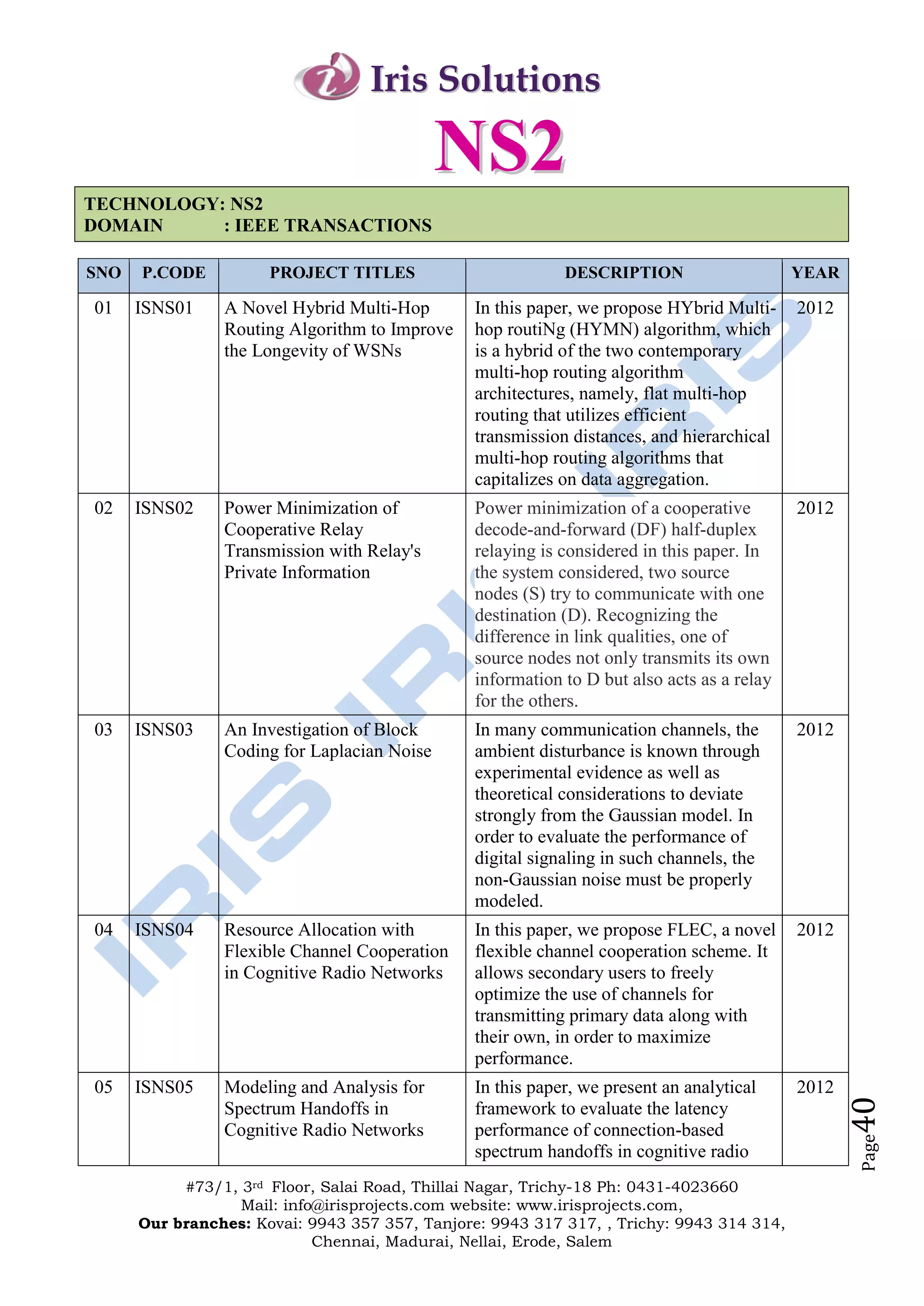
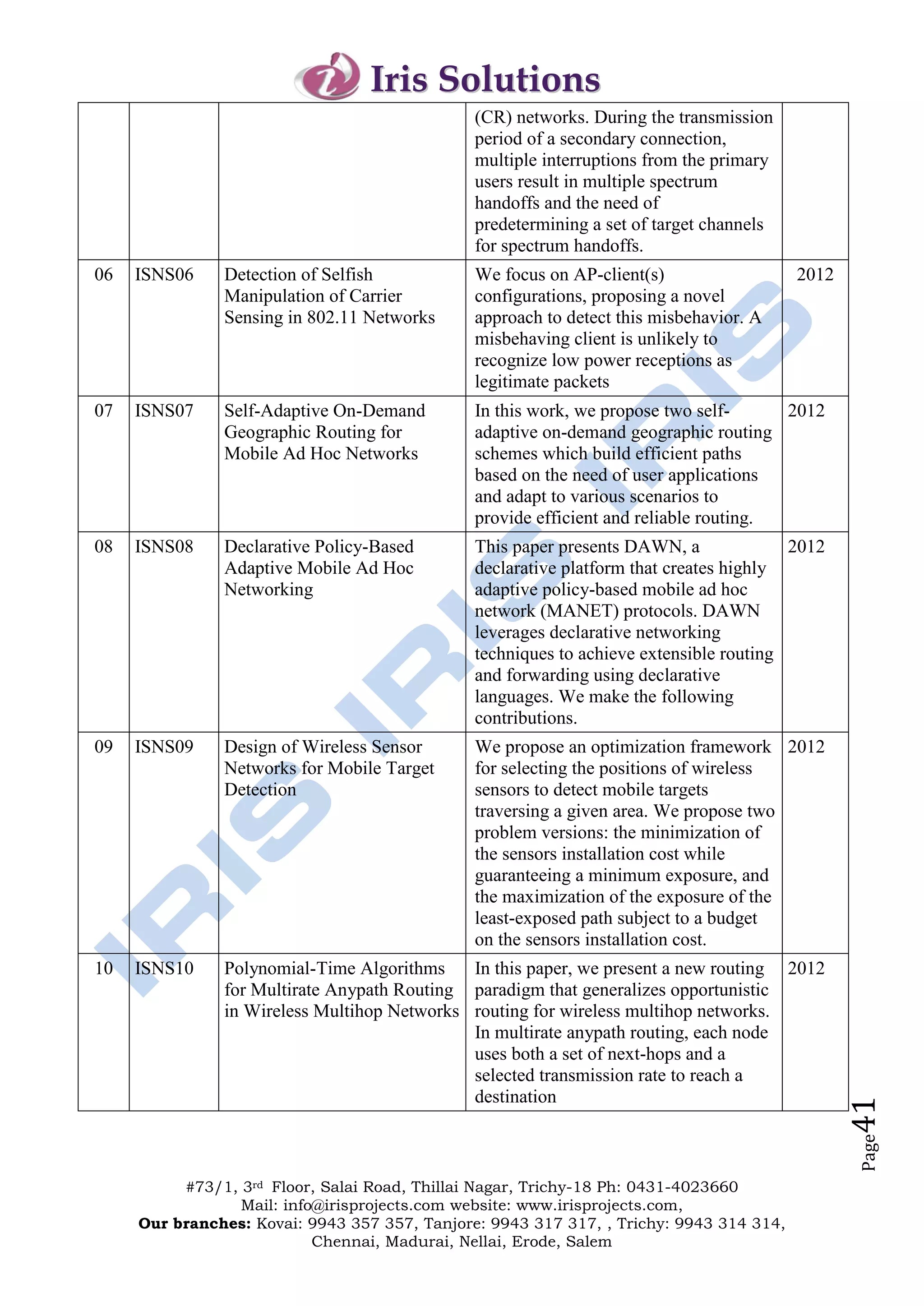
The document outlines the offerings and details of Iris Solutions, which provides project assistance for various technology disciplines including engineering and computer science. It highlights the importance of research and development, simulation training, and industry-oriented guidance to support student projects and skills enhancement. Additionally, the document includes contact information for various branches and a list of specific IEEE transaction titles related to networking and network security.

![Iris Solutions
CONTACT DETAILS
Trichy:
Iris Solutions,
#73/1, 3rd Floor, Salai Road,
Thillai Nagar, [Near Hotel Kannappa]
Trichy-18.
Ph: 0431- 4023660,
Mob: 9943 314 314
Kovai:
Iris Solutions,
#165, 5th Street, [Near Hotel LALA]
Gandhipuram,
Coimbatore-12.
Ph: 0422- 4372816
Mob: 9943 357 357
Tanjore:
Iris Solutions,
#1520,South Rampart,
[ Near Siva Siva Chidambaram Jewellery]
Tanjore -1.
Ph : 04362-300609
Mob : 9943 317 317
3
Page
#73/1, 3rd Floor, Salai Road, Thillai Nagar, Trichy-18 Ph: 0431-4023660
Mail: info@irisprojects.com website: www.irisprojects.com,
Our branches: Kovai: 9943 357 357, Tanjore: 9943 317 317, , Trichy: 9943 314 314,
Chennai, Madurai, Nellai, Erode, Salem](https://image.slidesharecdn.com/ieee2012softwaretitles2012-13-120817141004-phpapp01/75/IRIS-SOLUTIONS-IEEE-2012-ENGINEERING-PROJECT-TITLES-FOR-CSE-IT-3-2048.jpg)