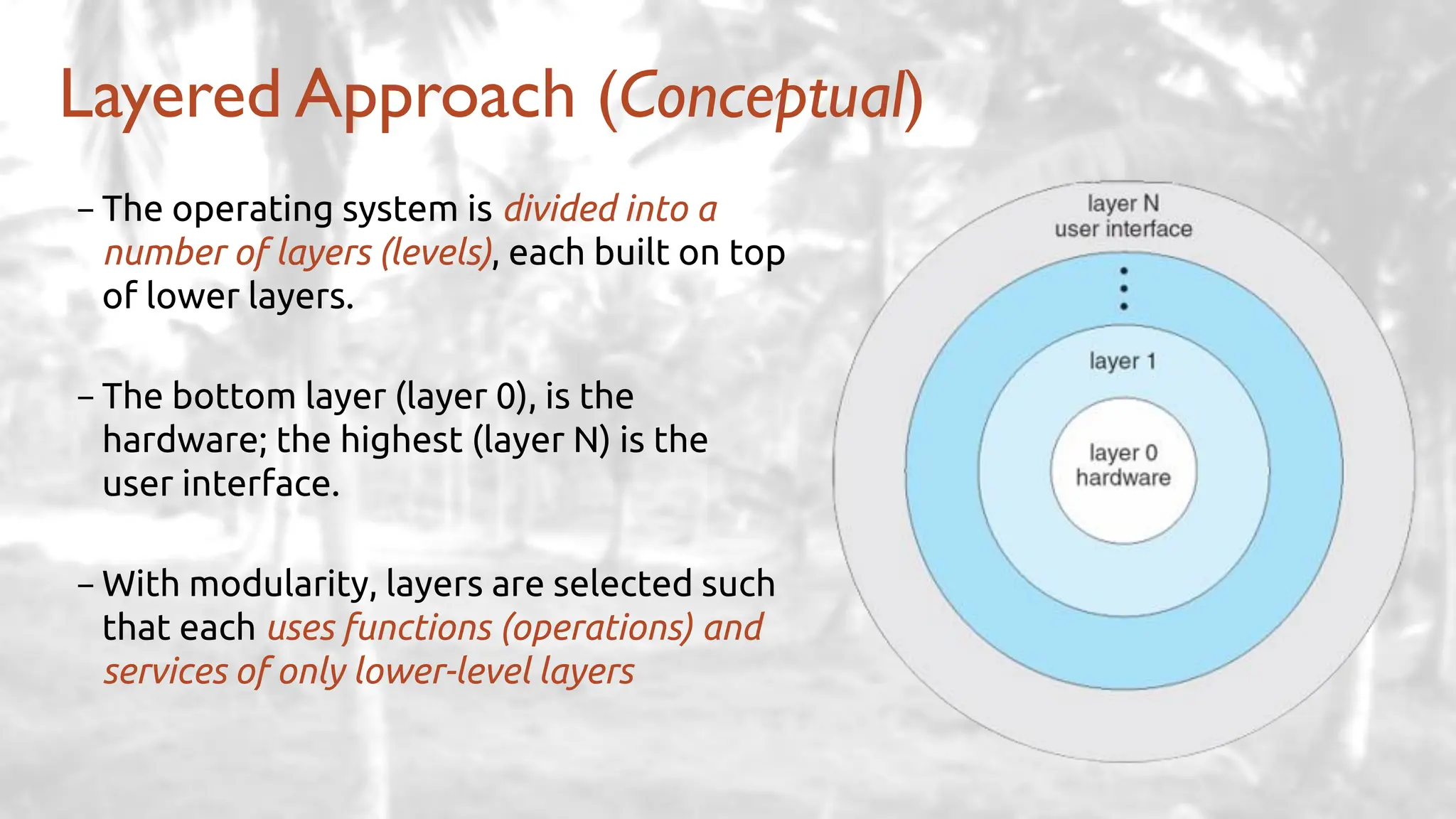
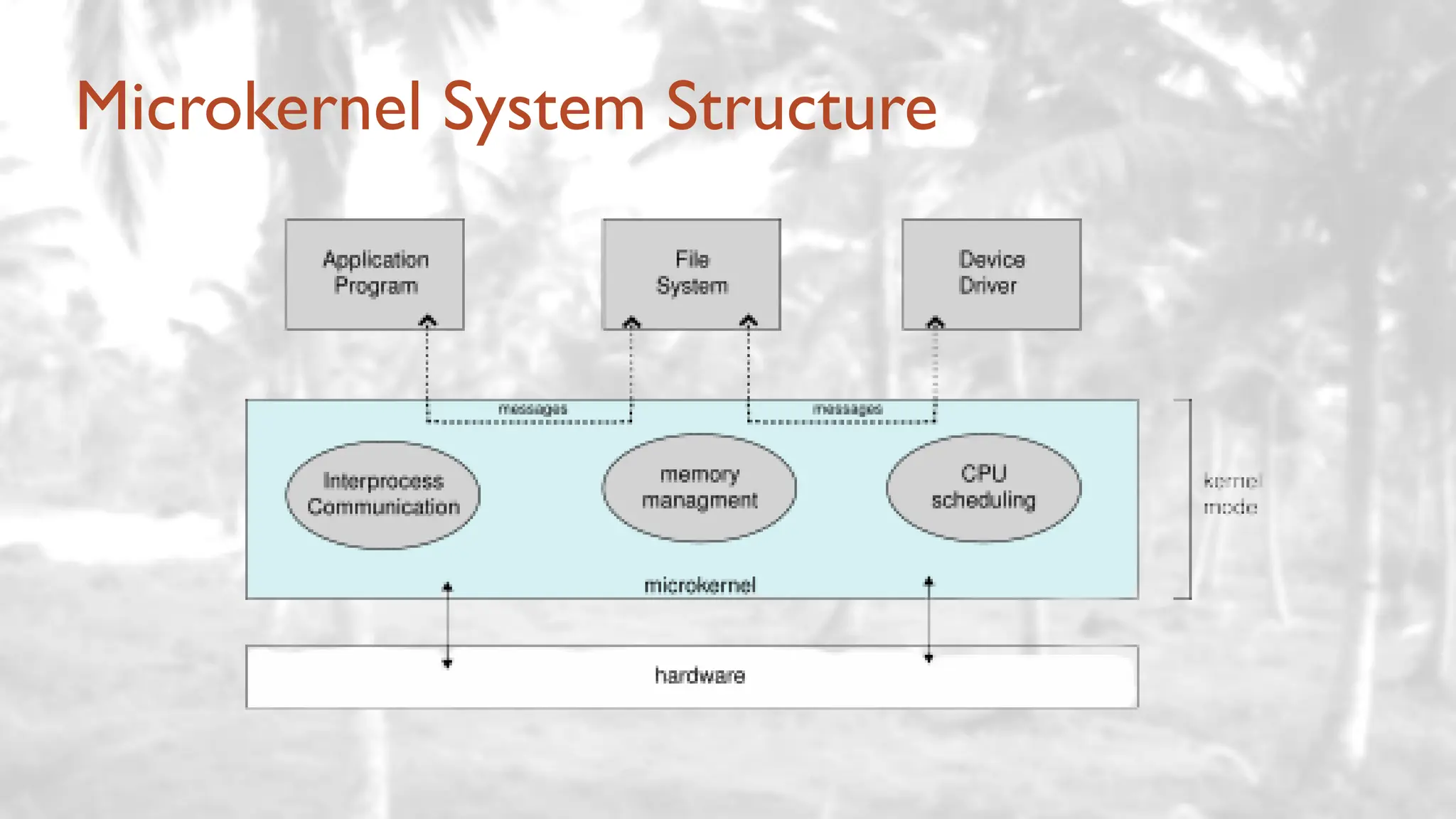
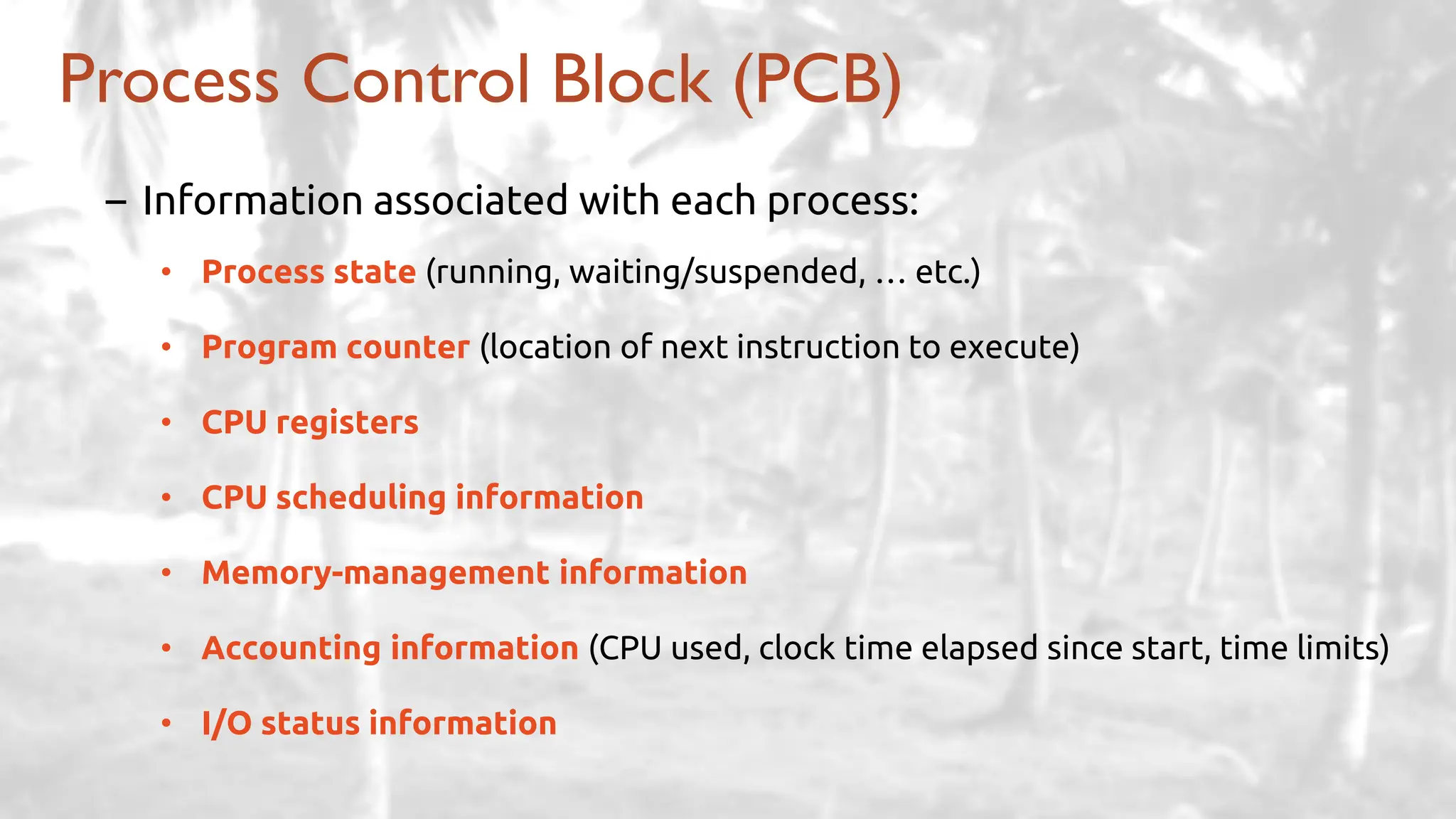
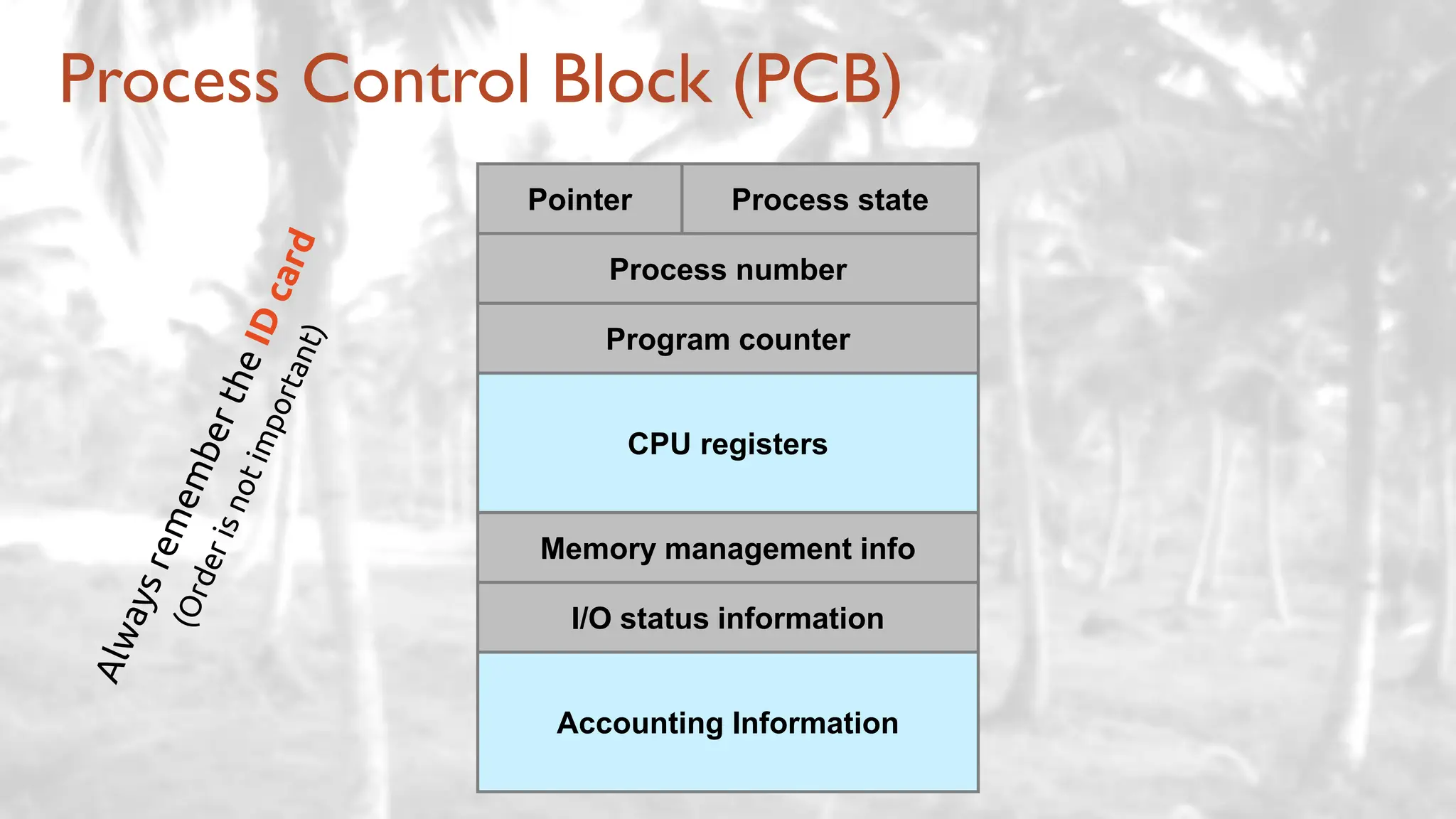
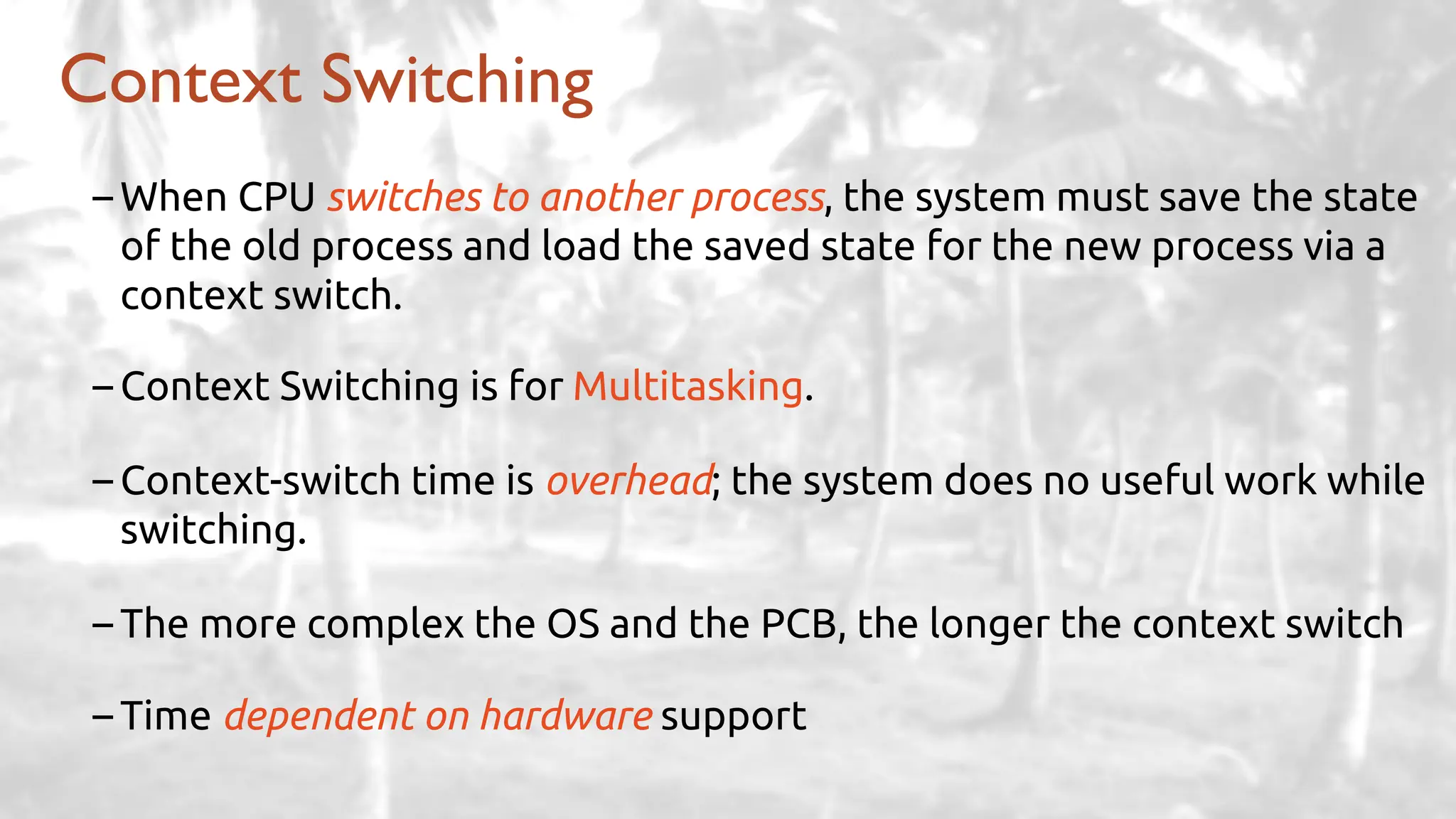
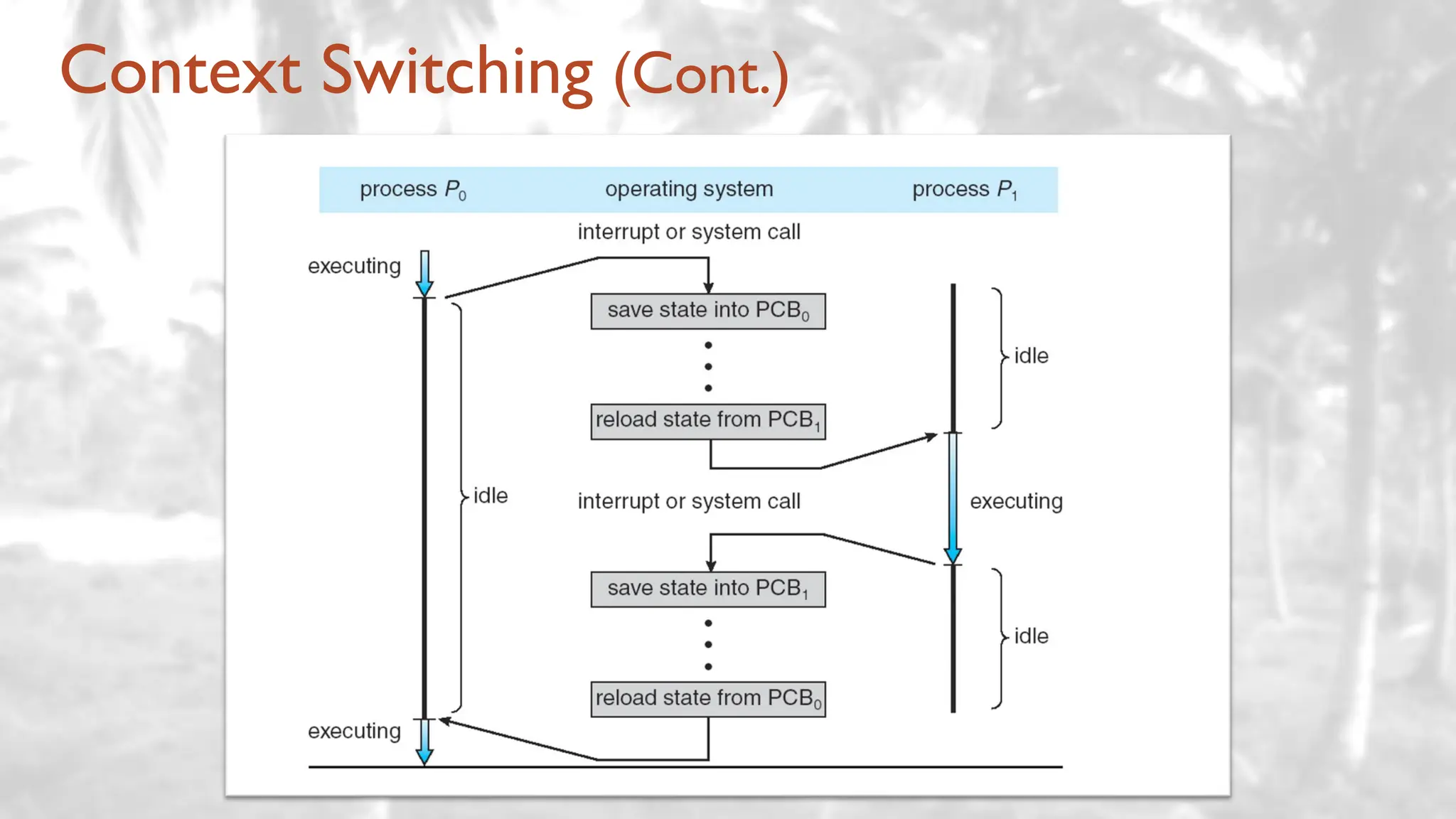
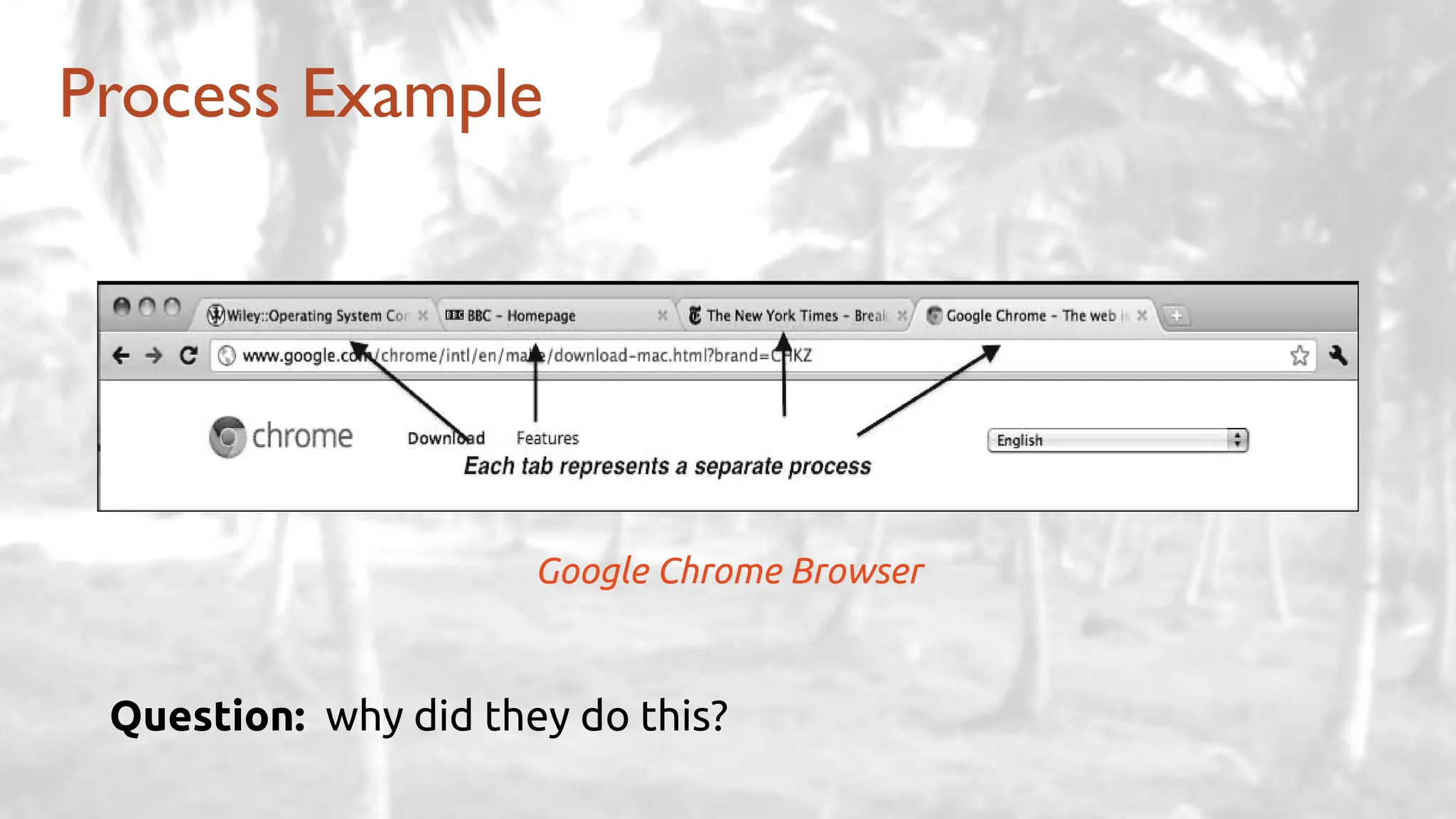
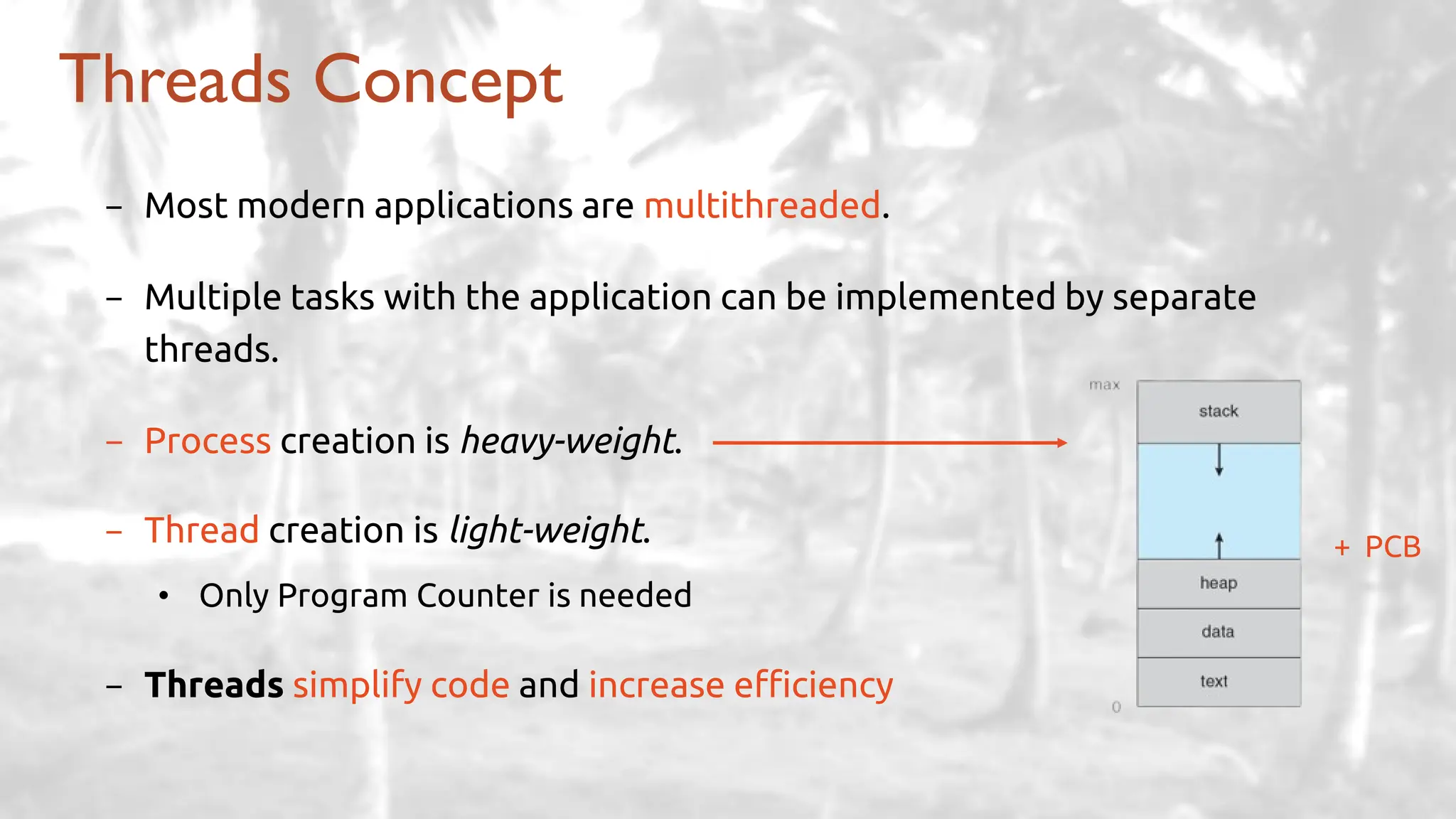
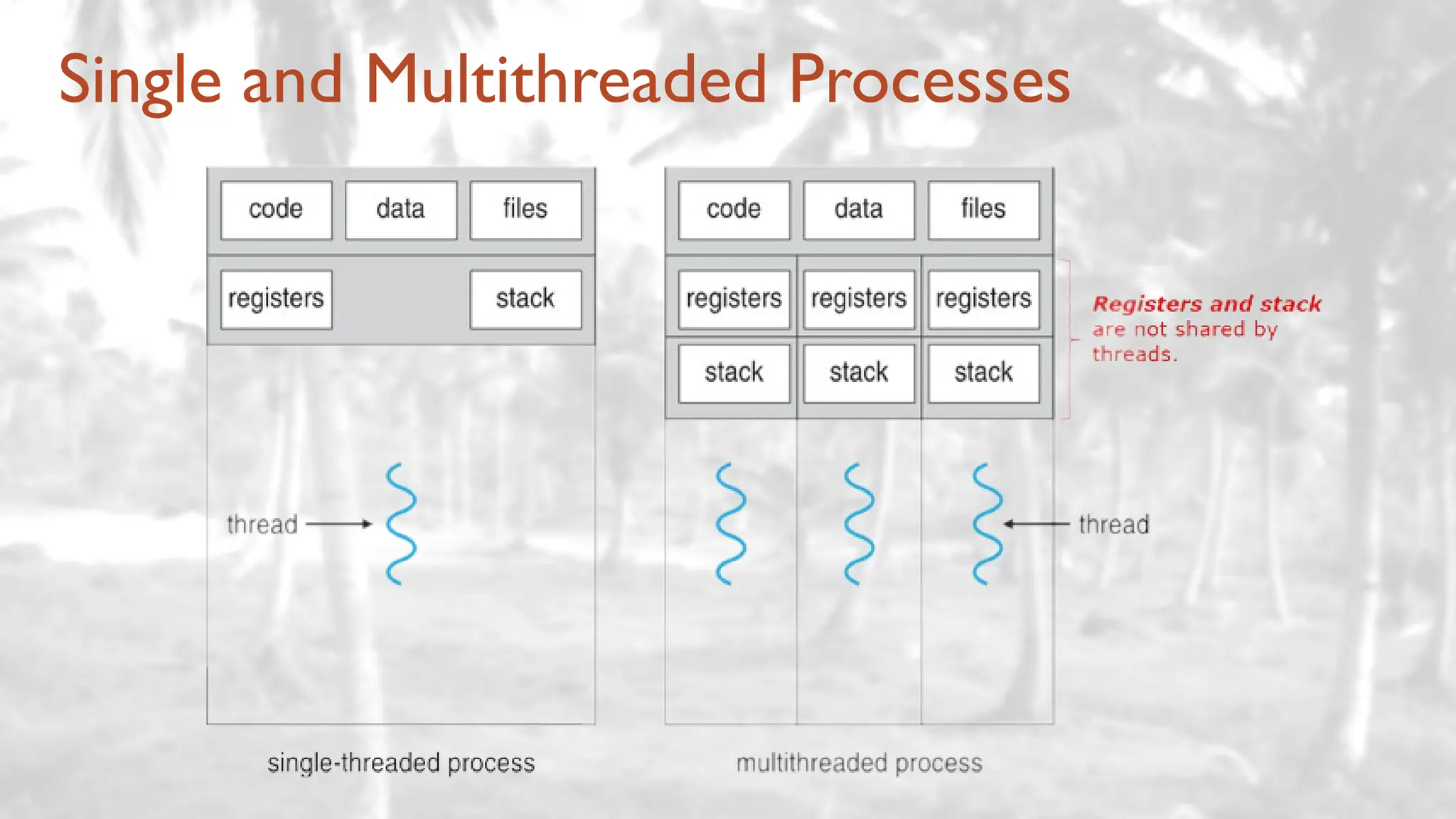
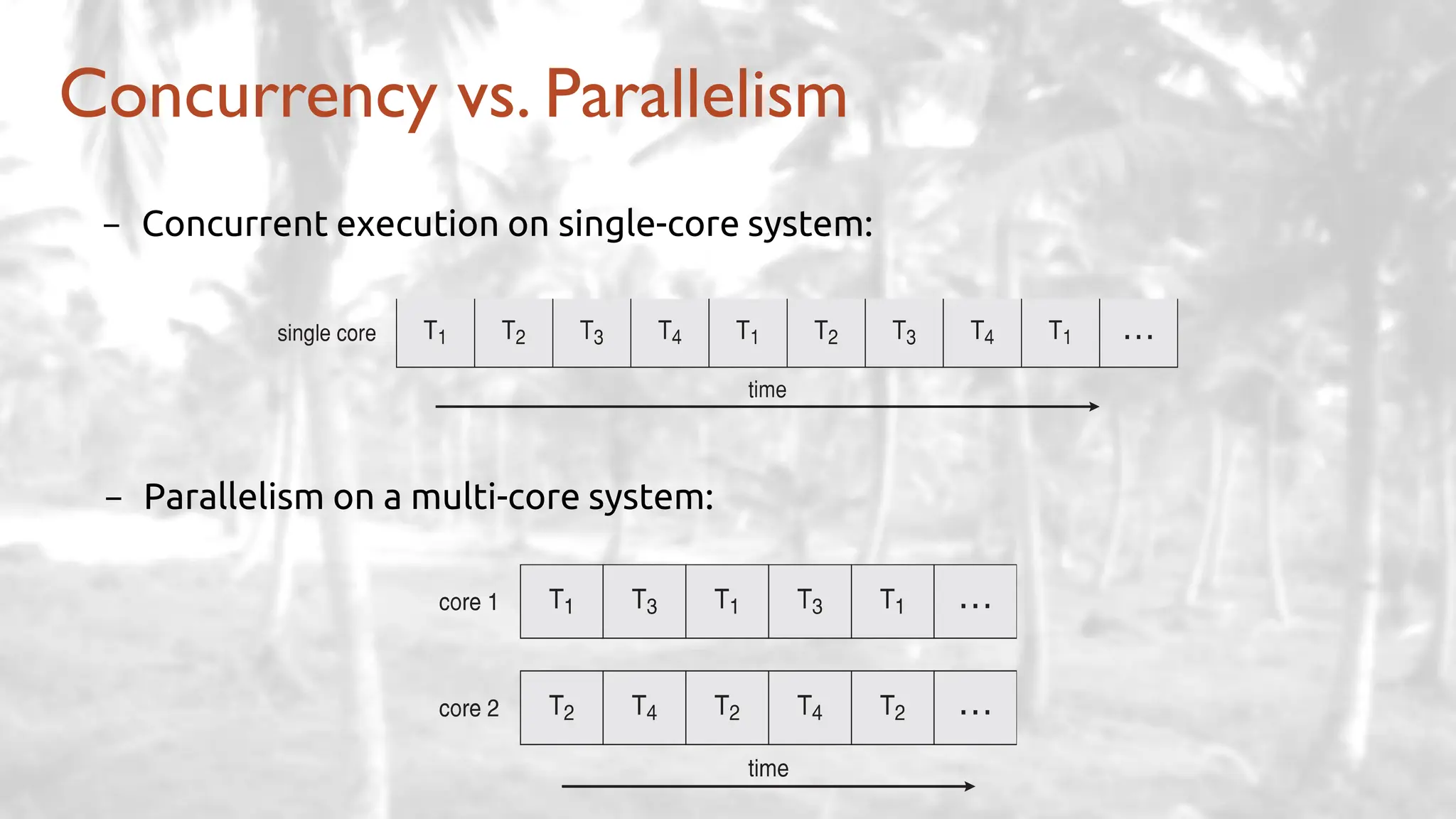
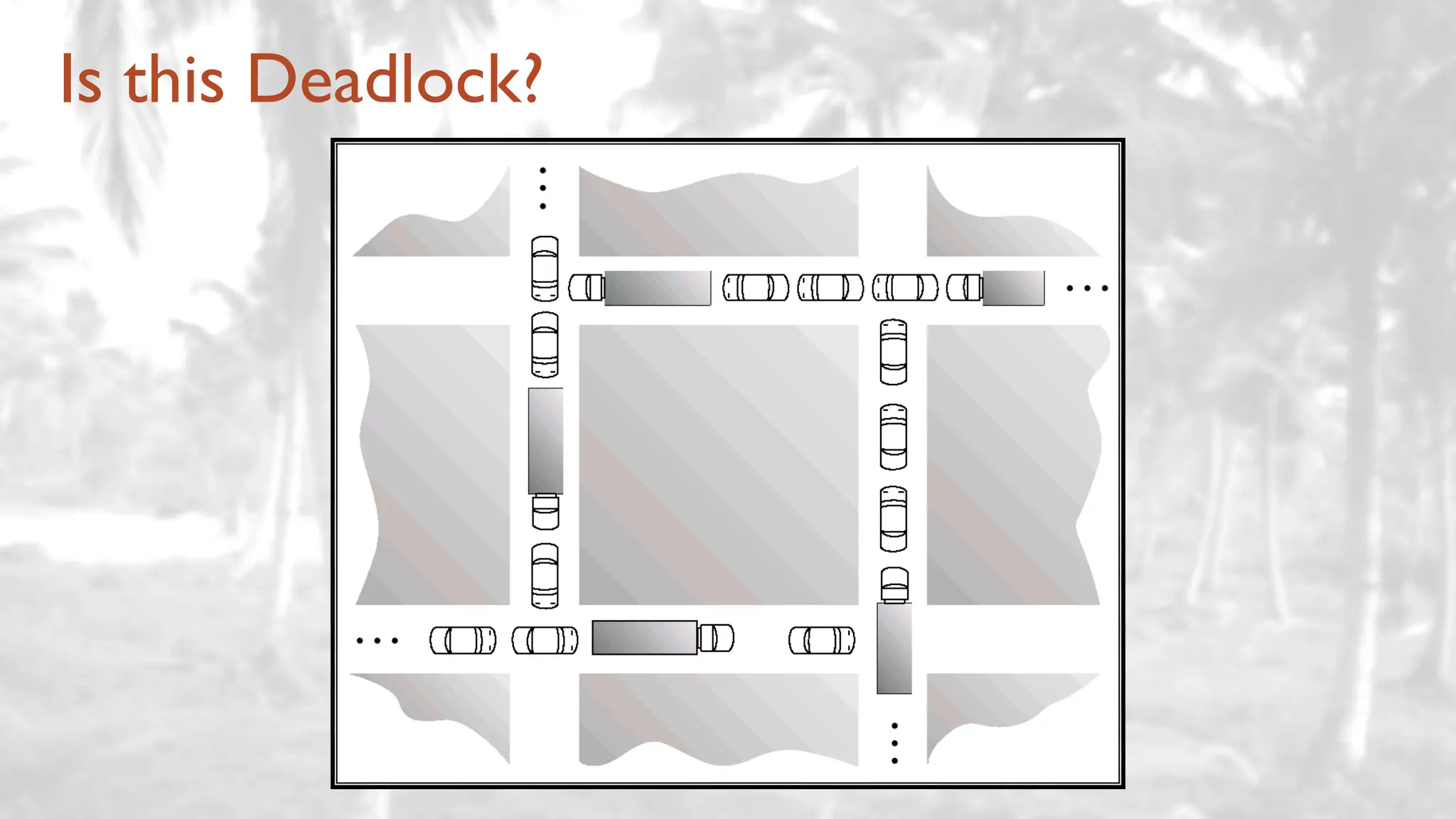
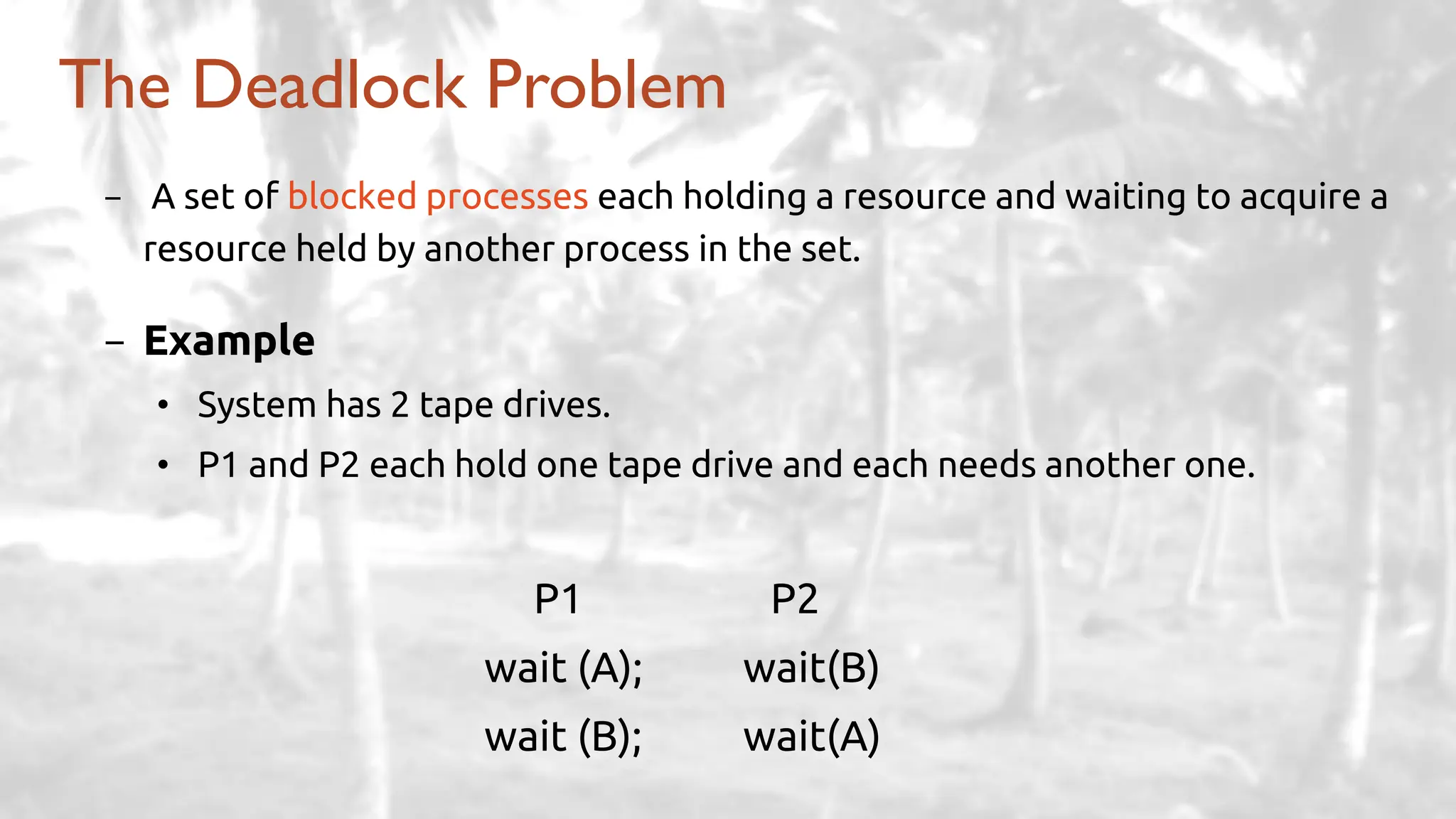
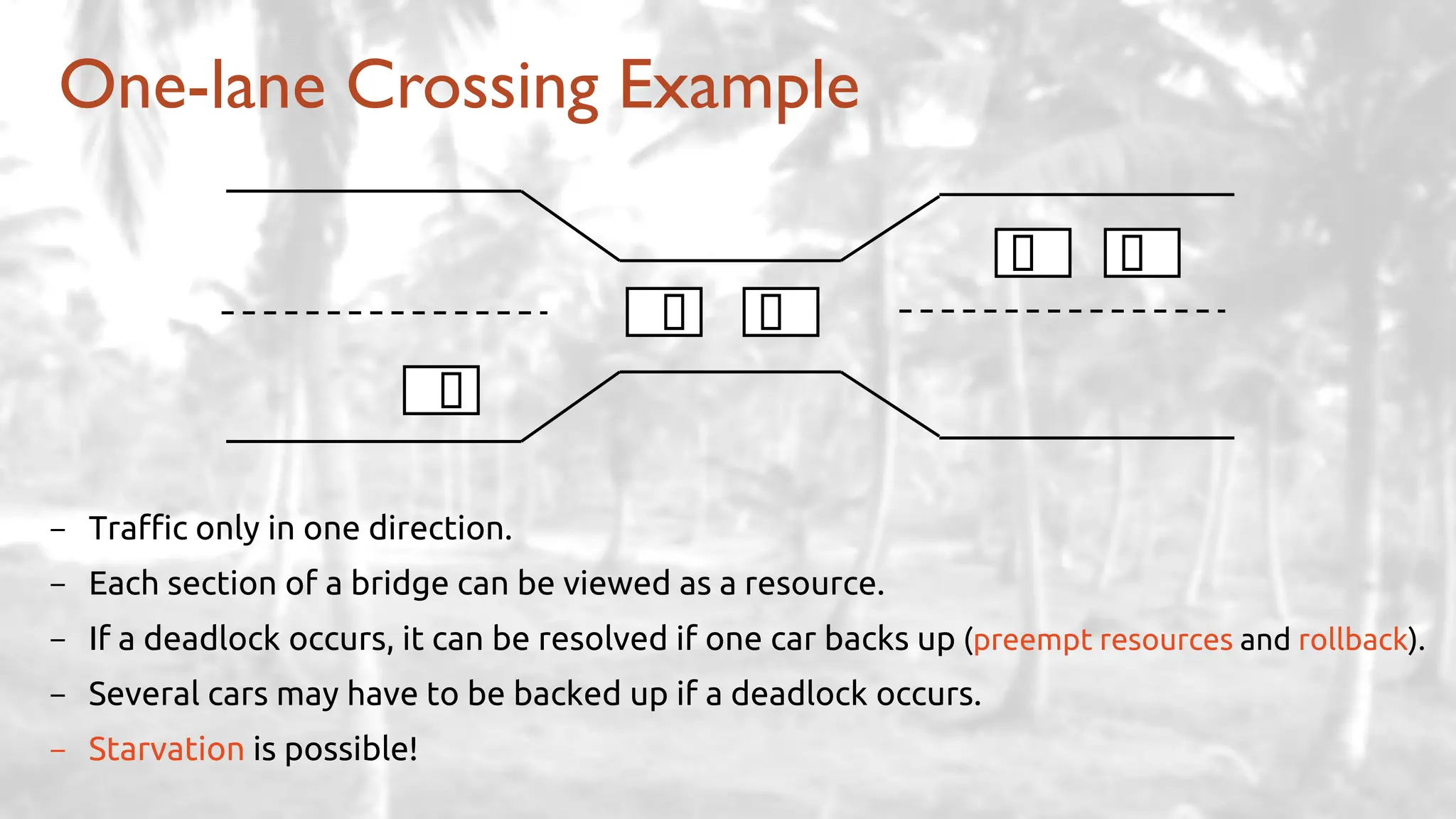
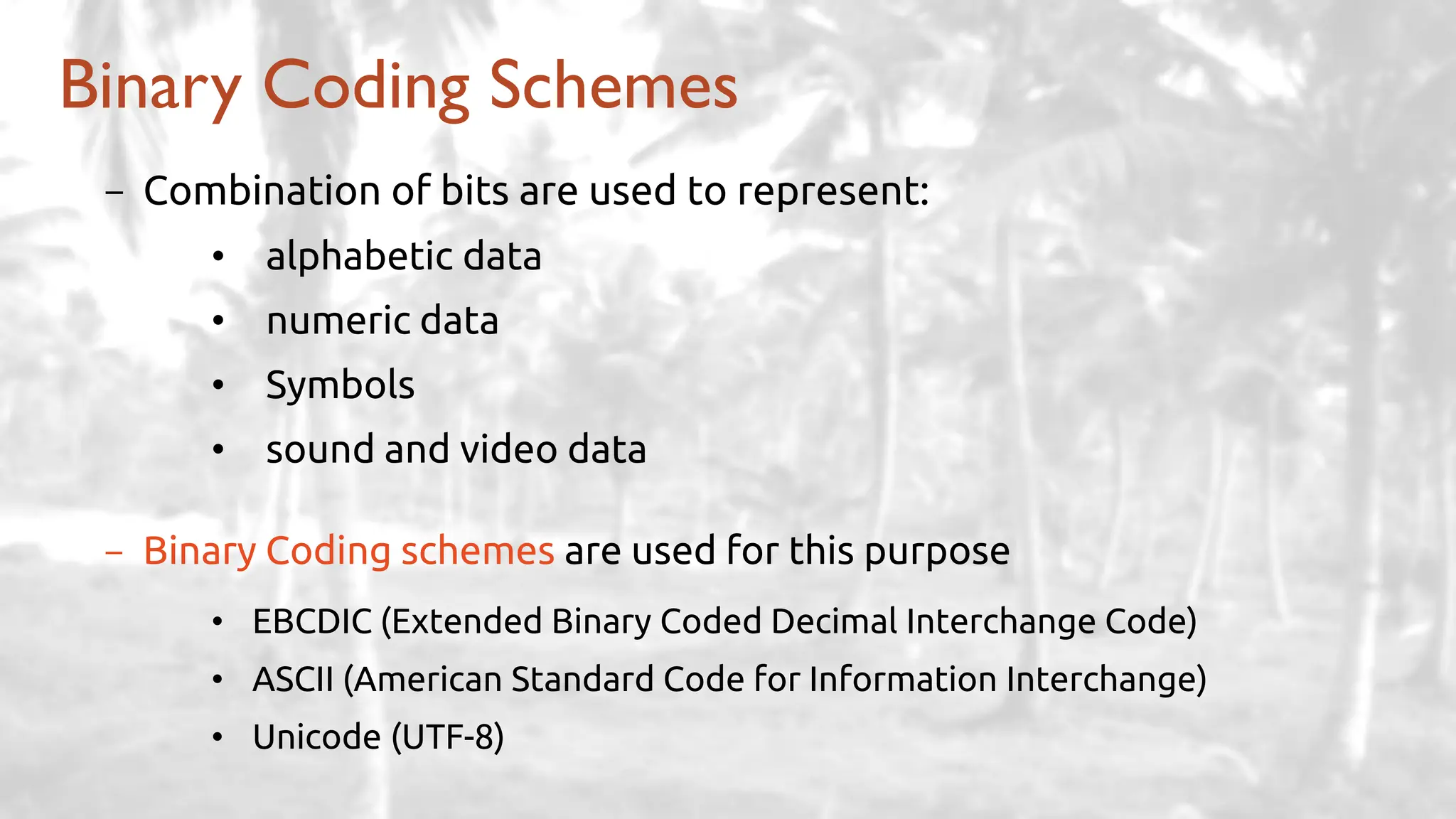
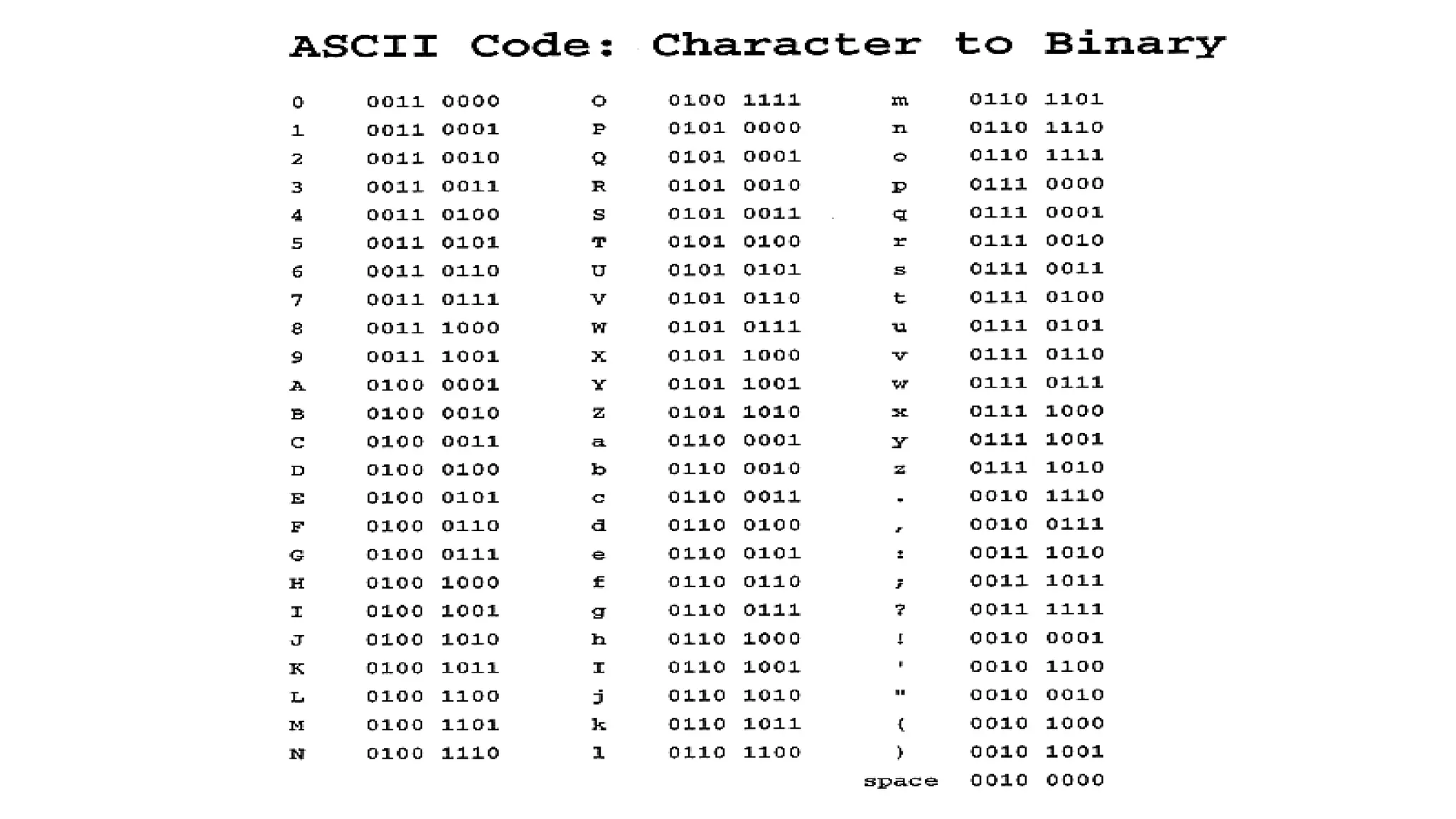
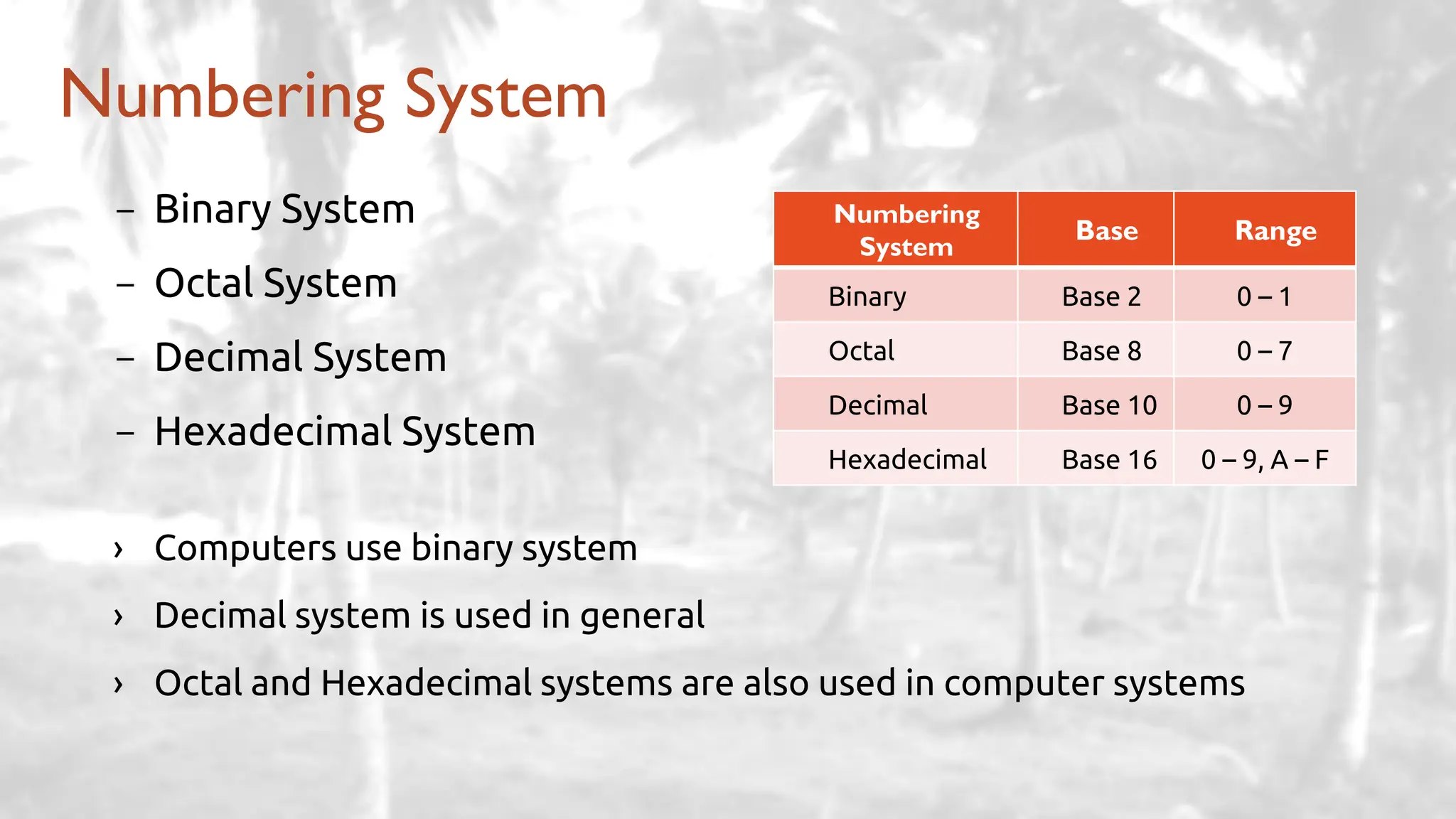
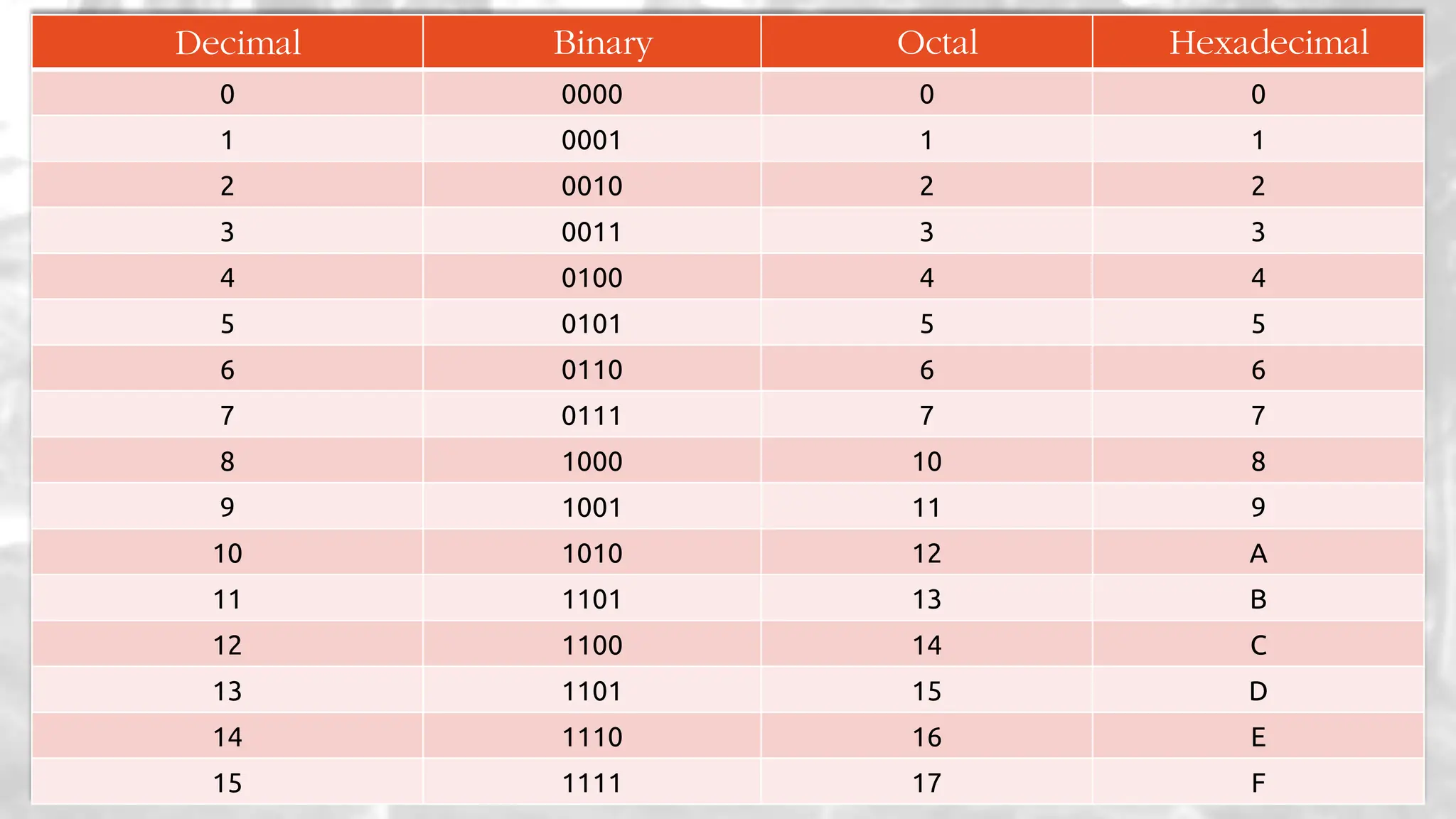
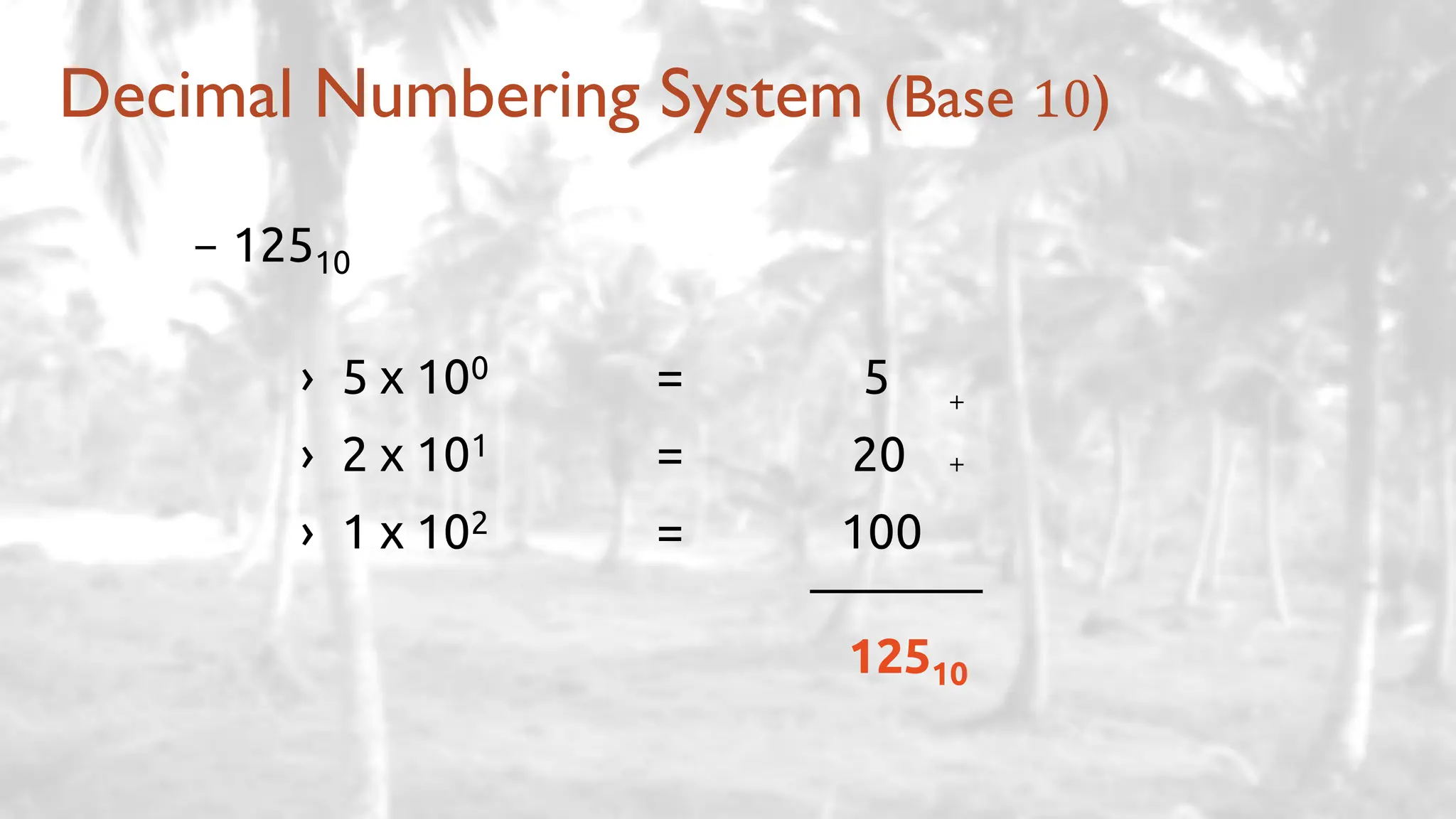
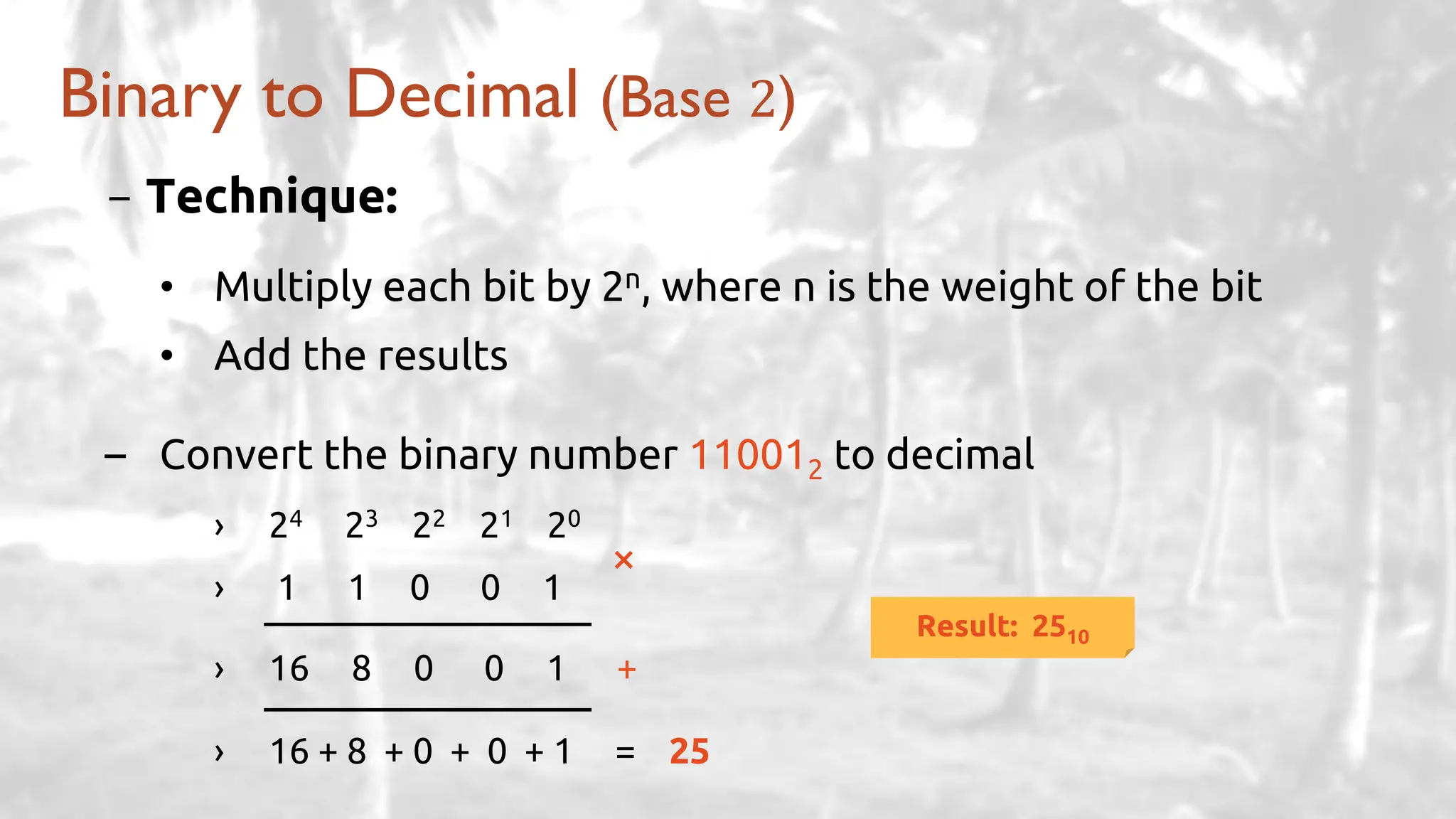
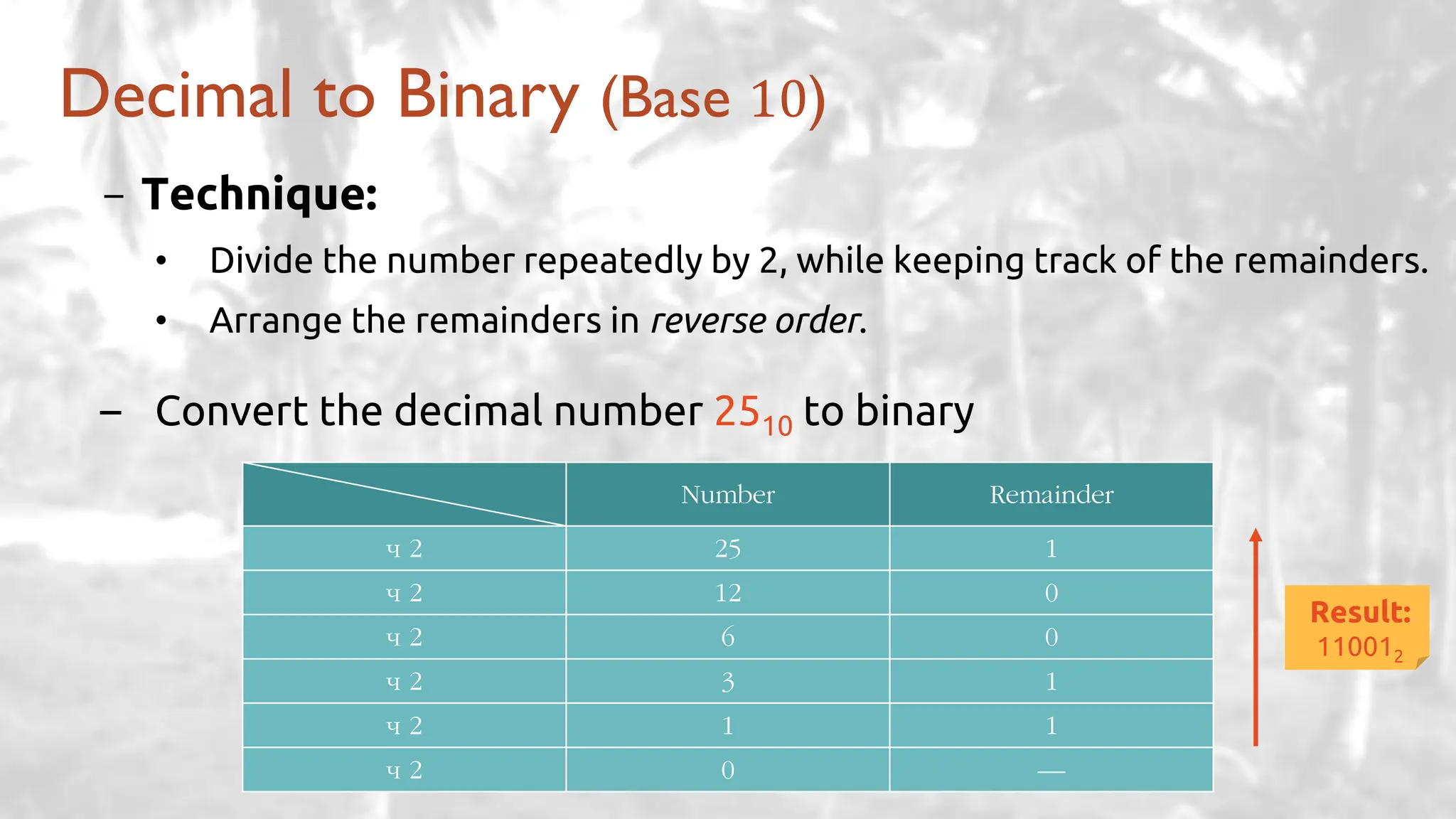
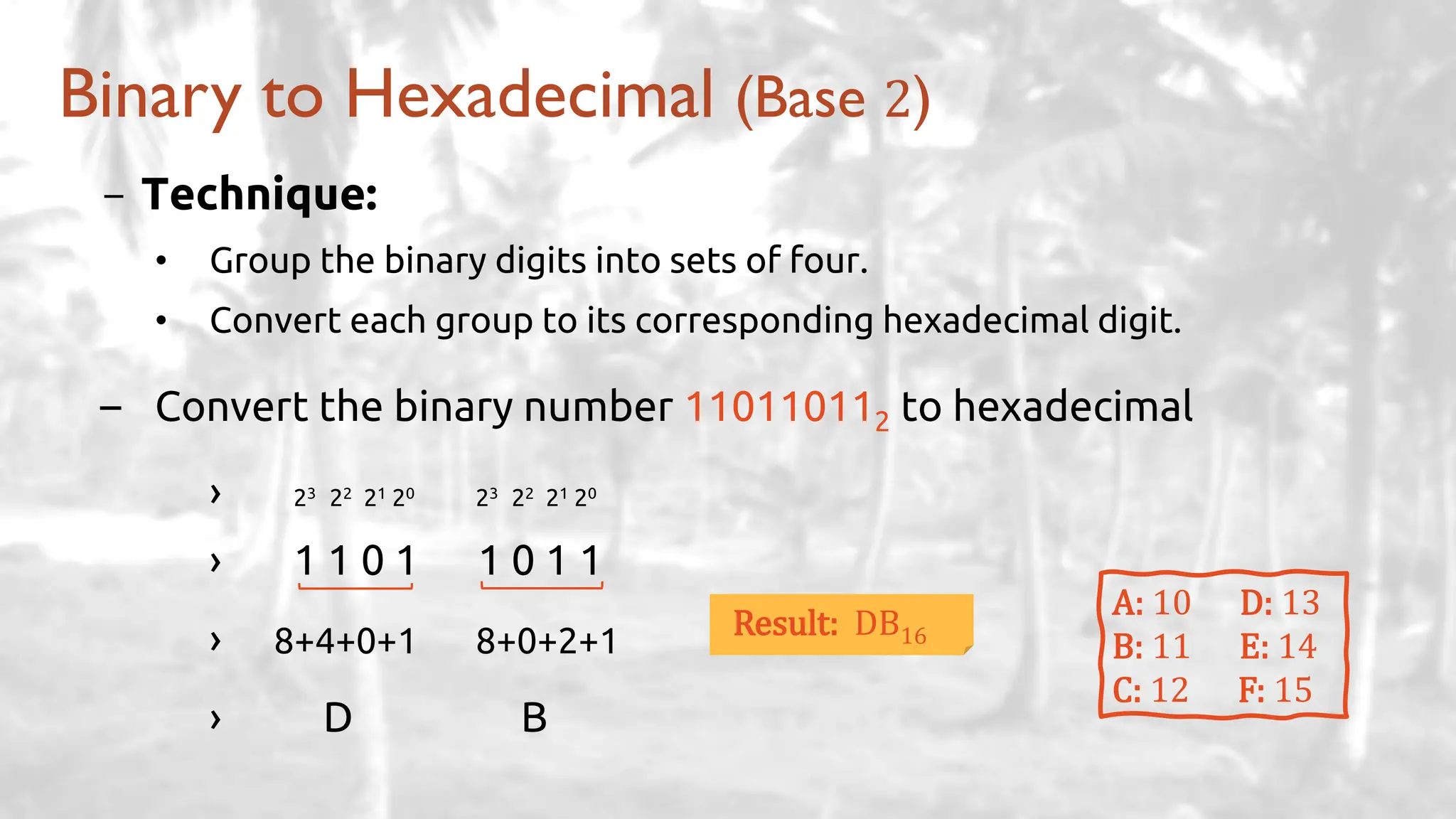
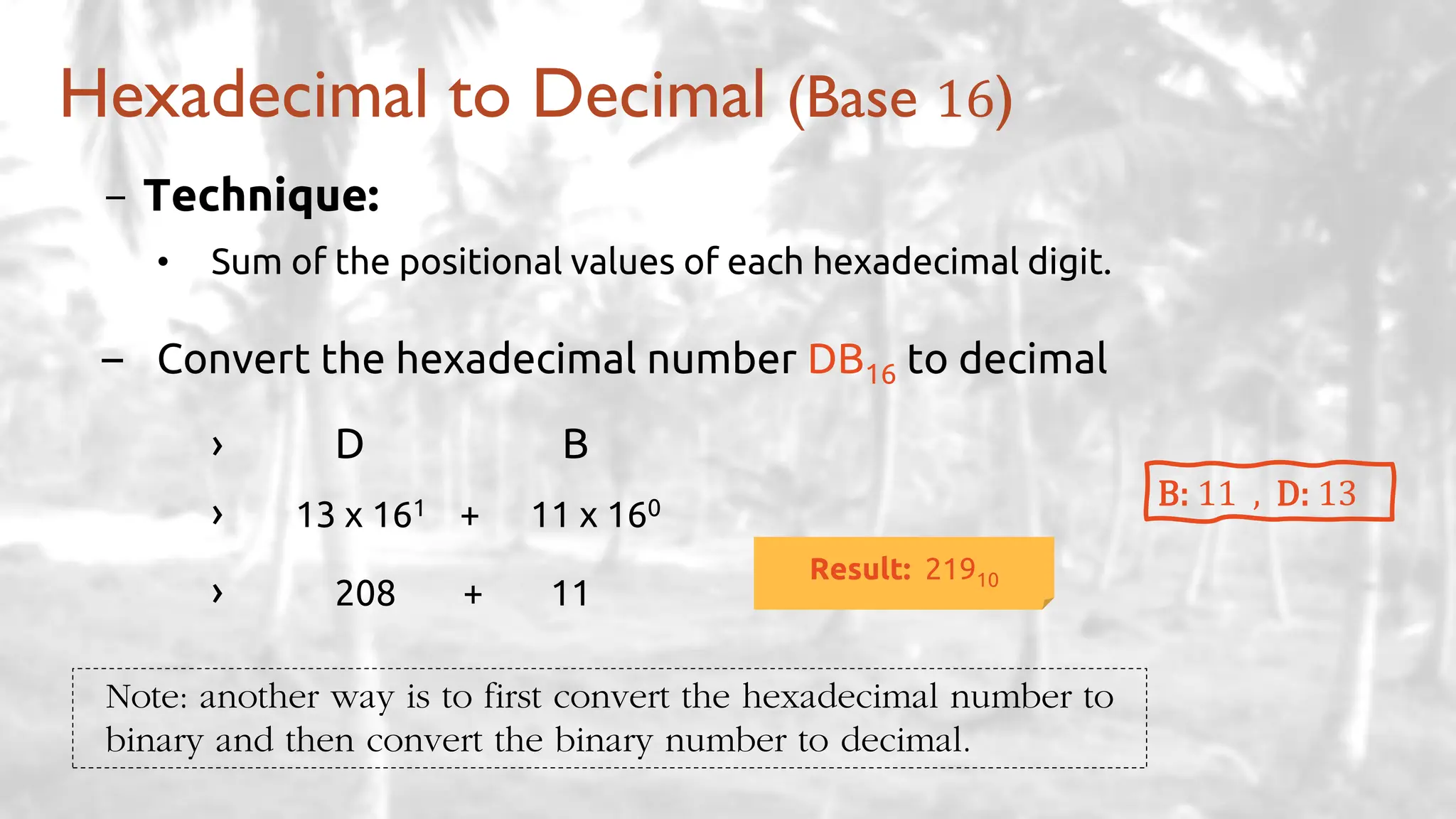
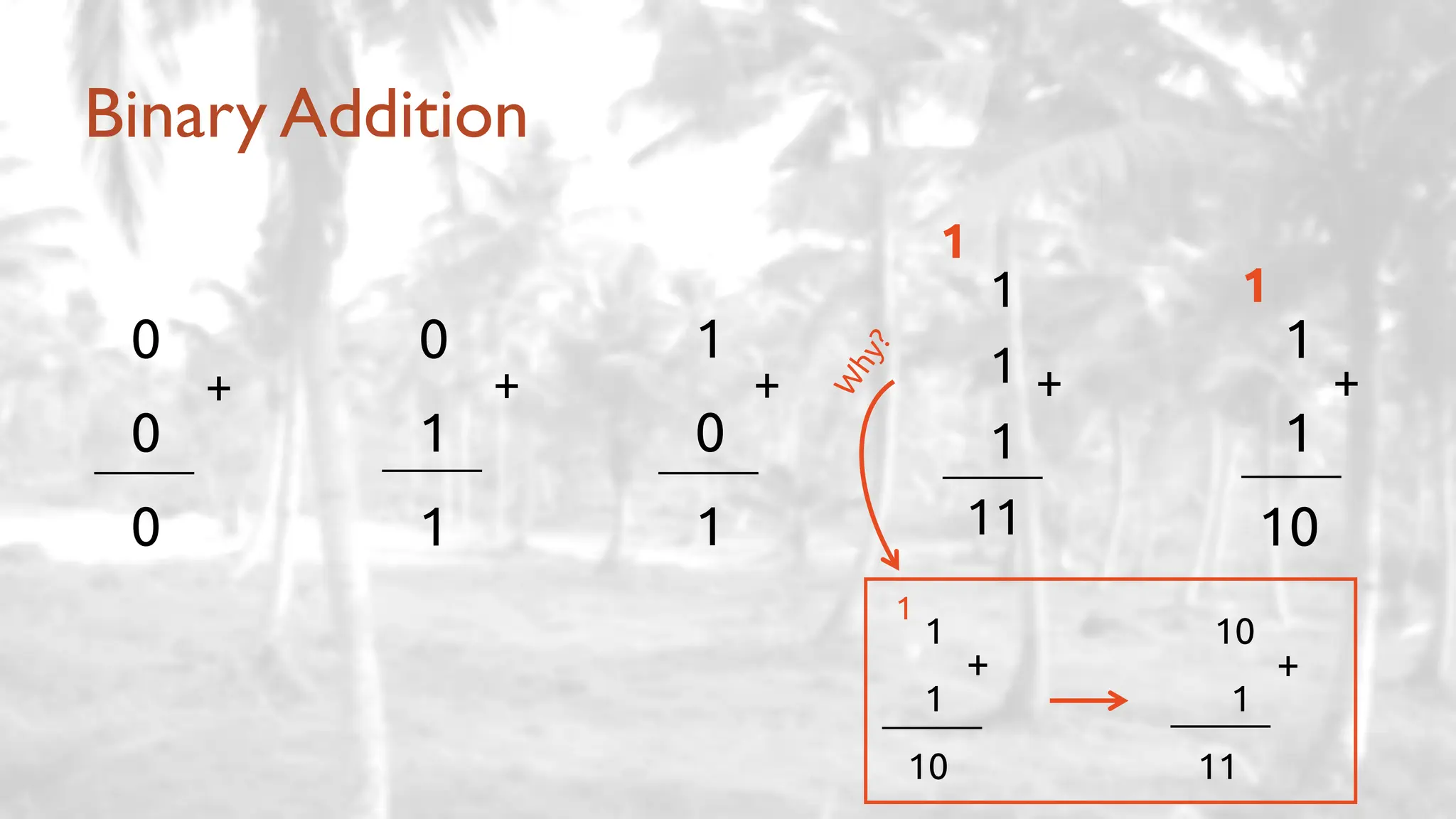
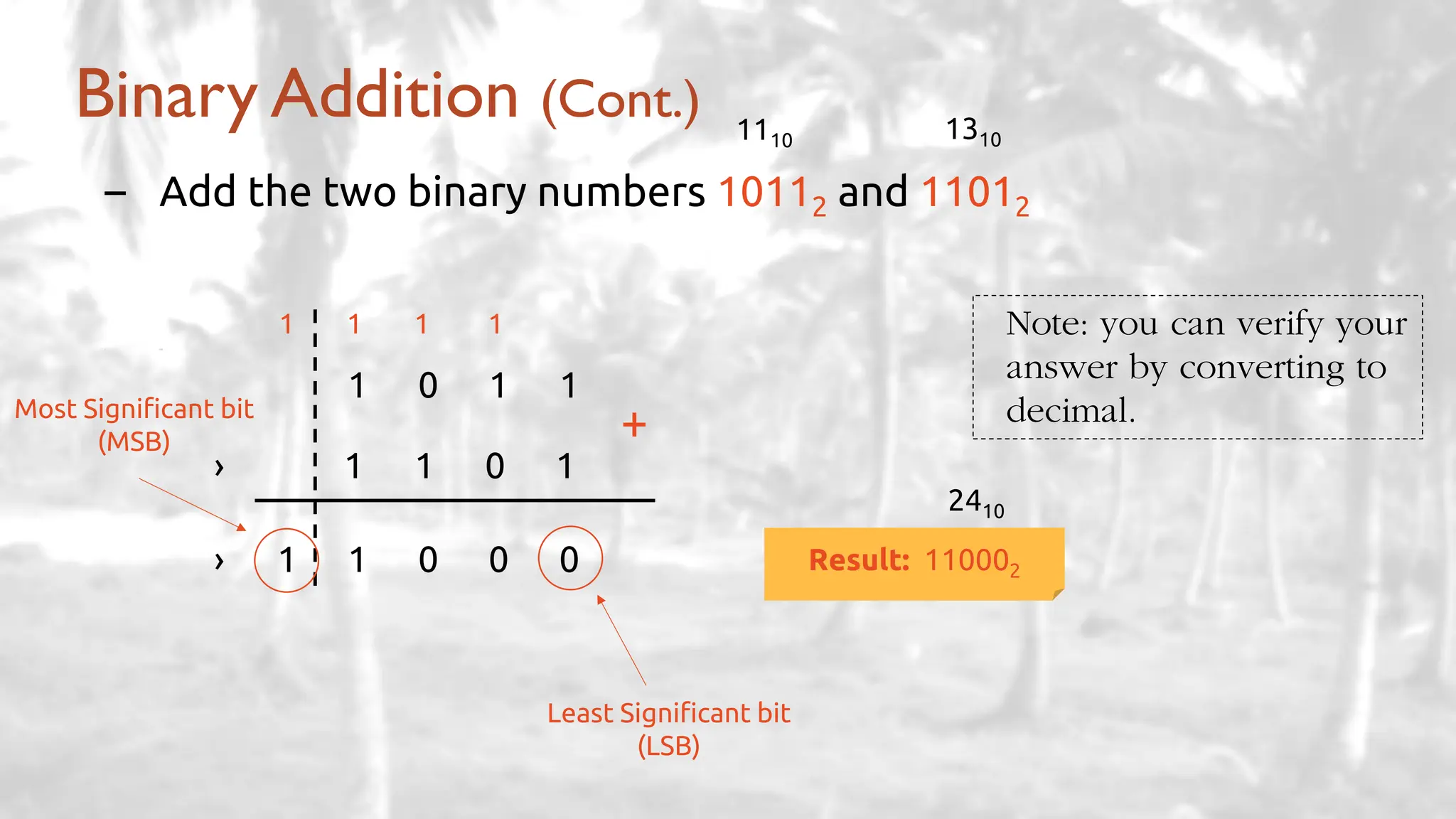
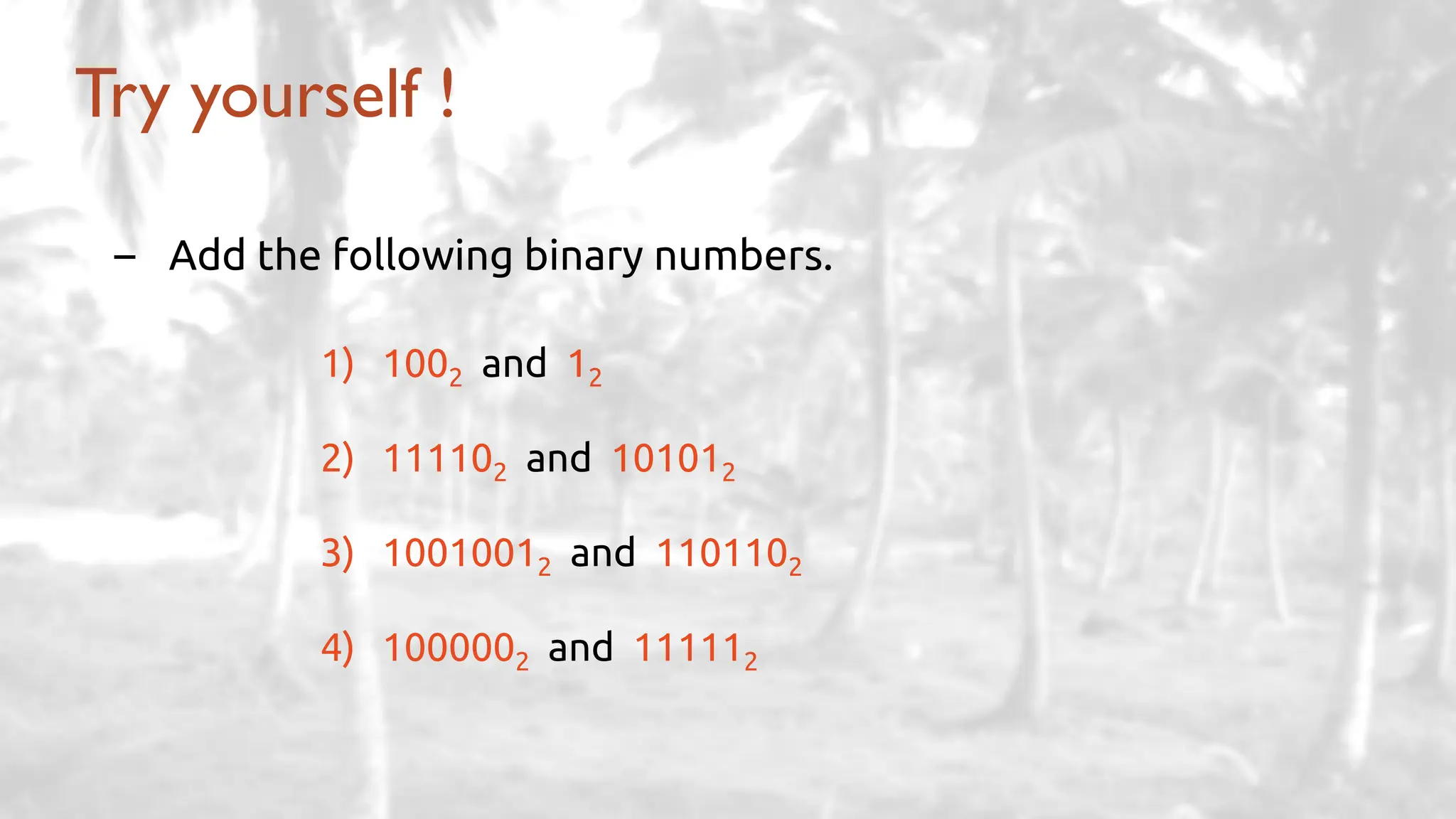
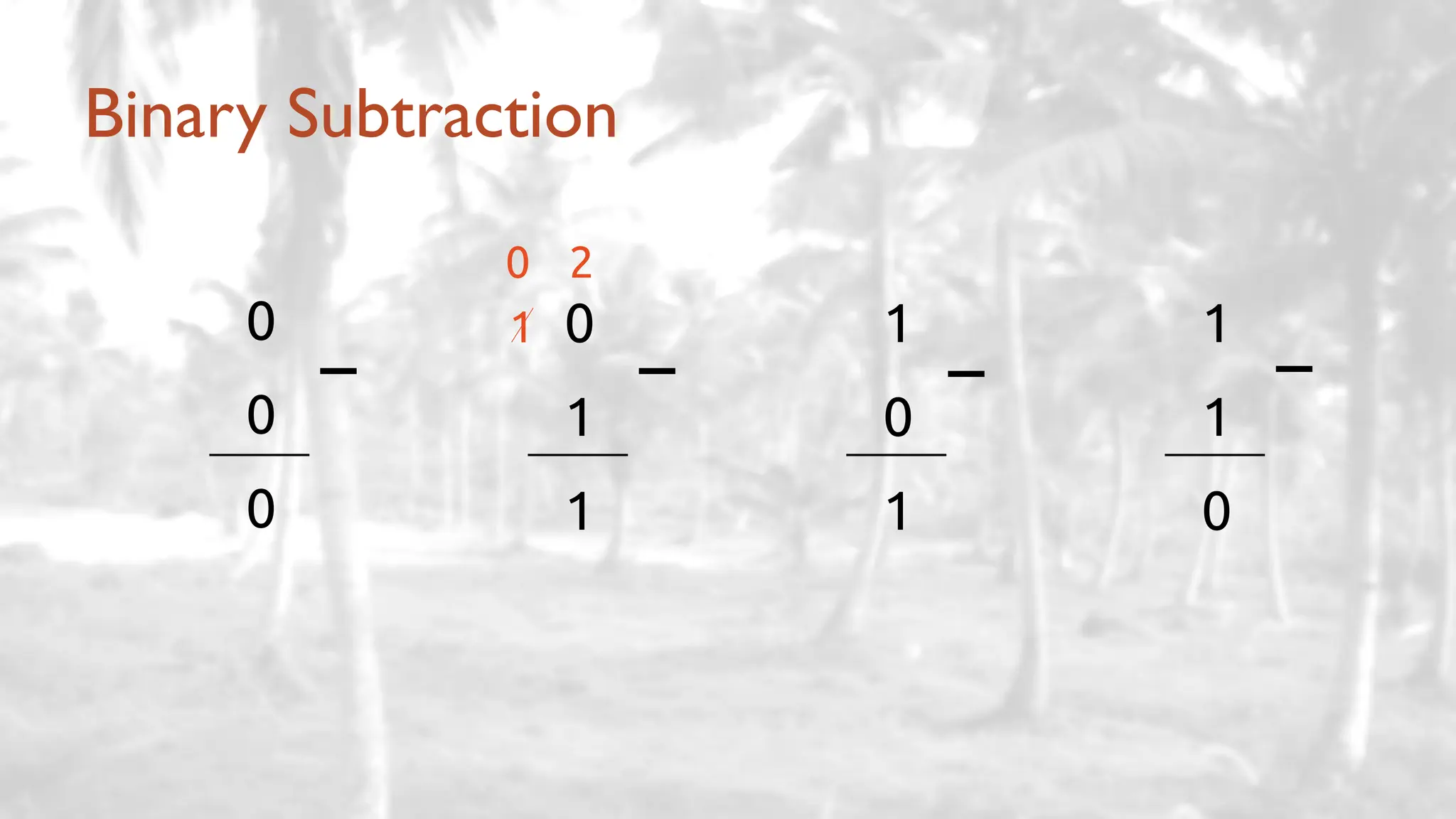
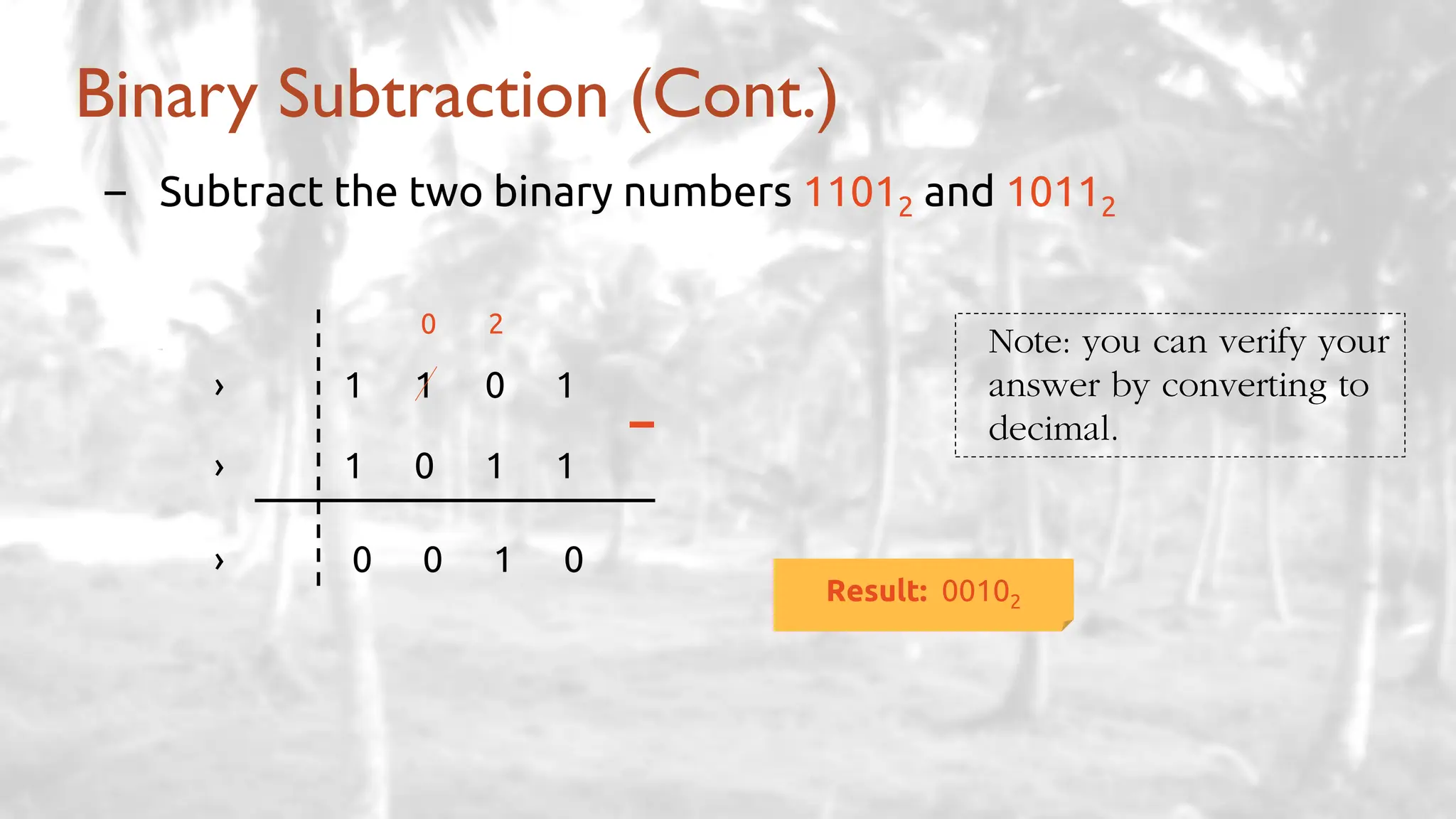
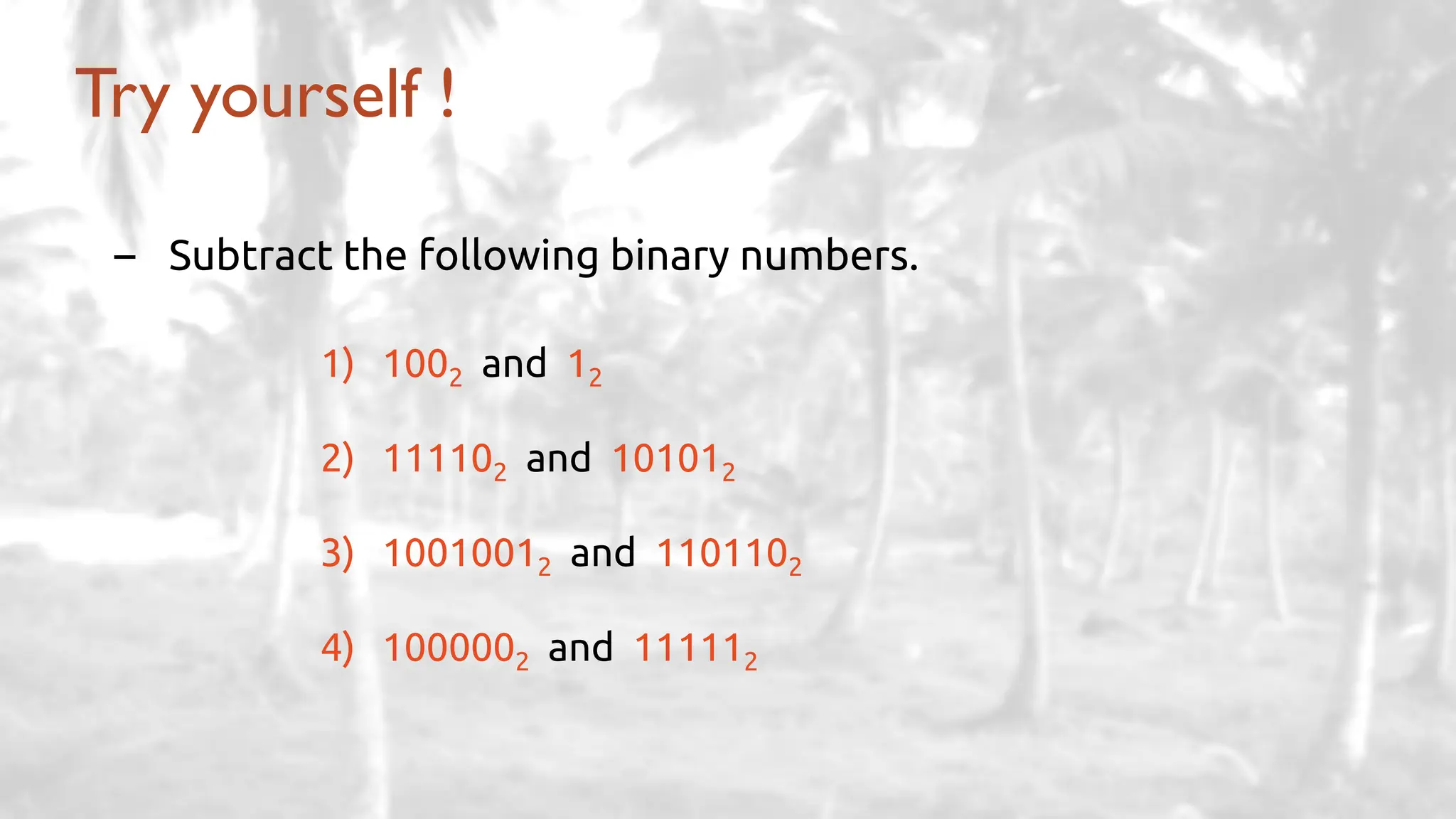
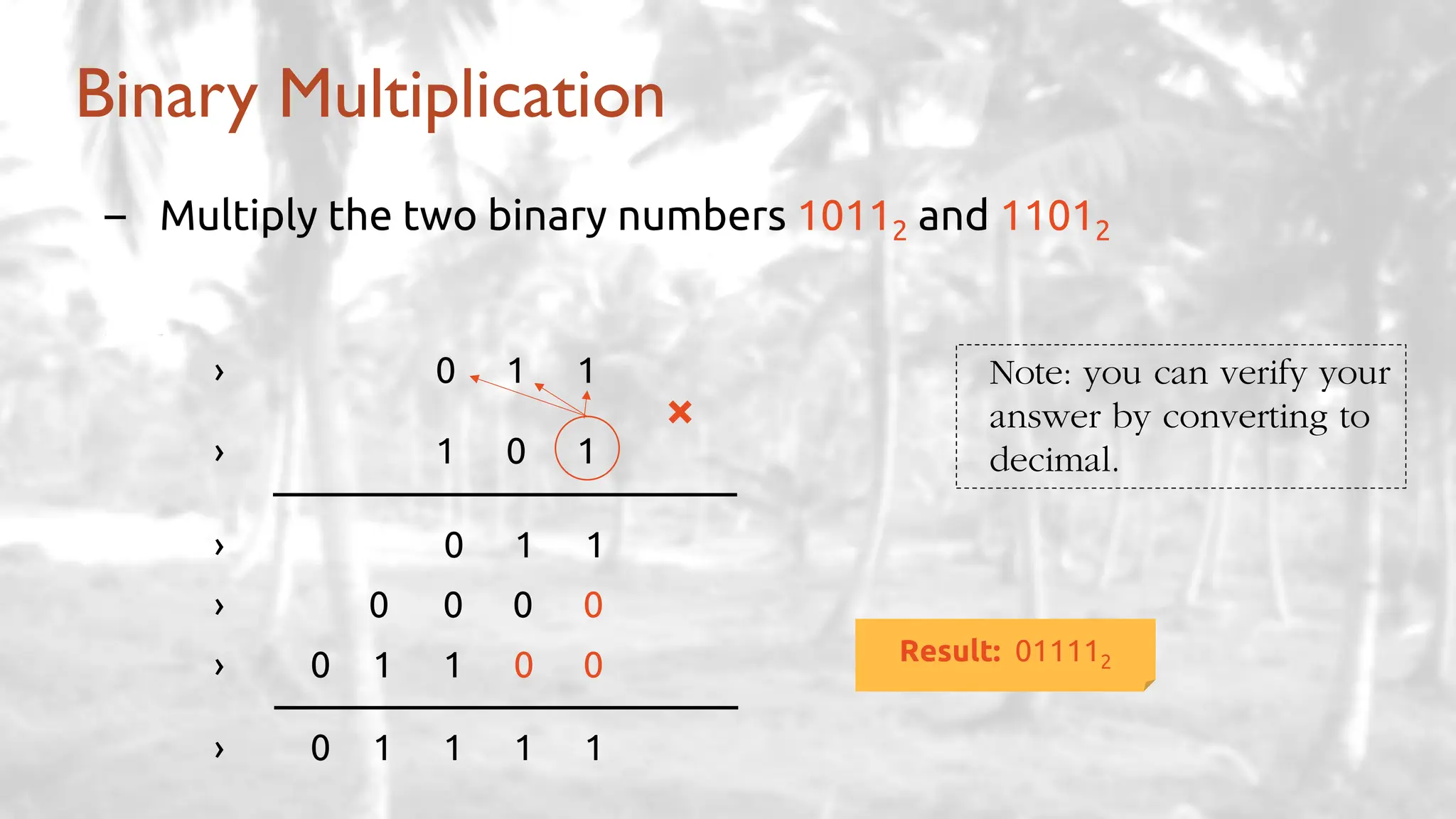
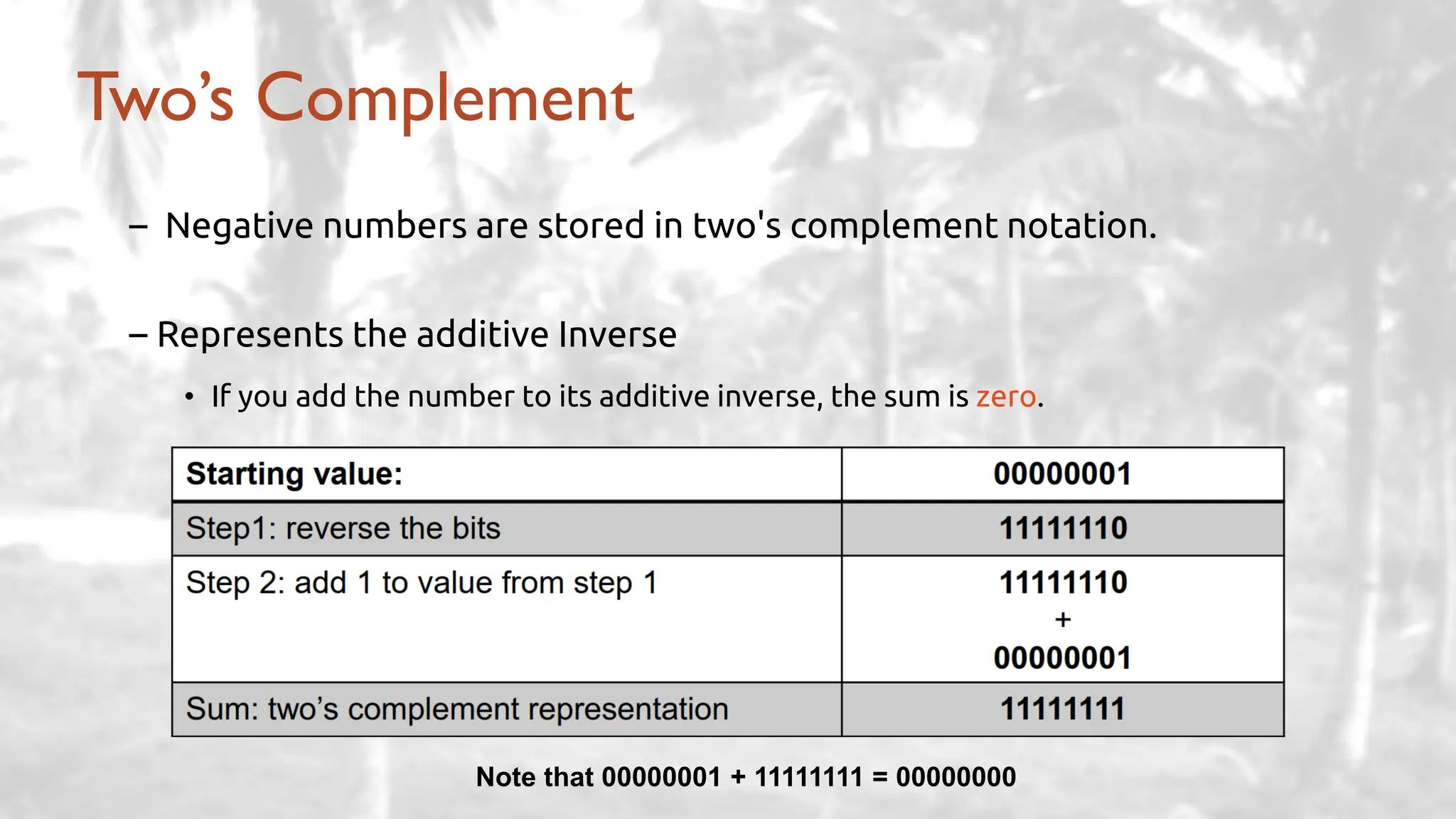
The lecture delves into operating system architectures, including Direct Memory Access (DMA), various storage structures, and distinctions between files and directories. It explores operating system designs such as MS-DOS, Unix, and modular systems, highlighting their advantages and disadvantages. The discussion also covers process management, threading, concurrency, deadlocks, binary coding schemes, and basic arithmetic in binary notation.