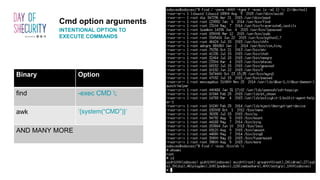
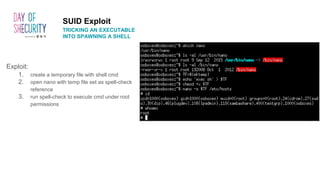
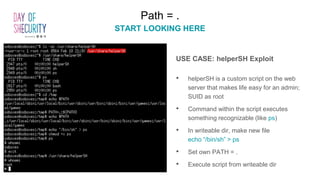
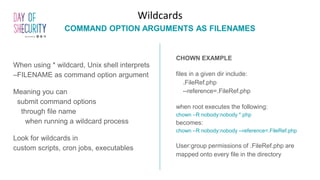
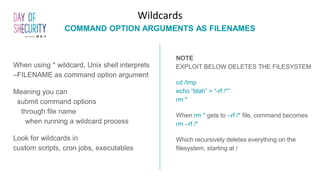
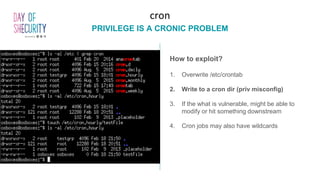
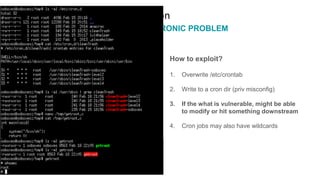
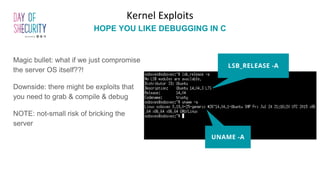
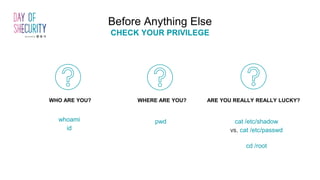
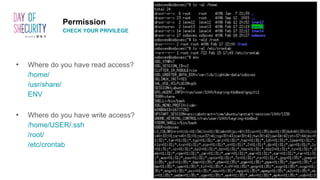
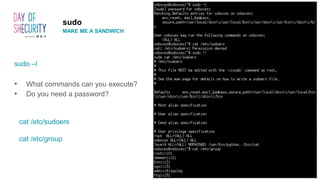
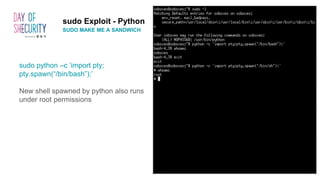
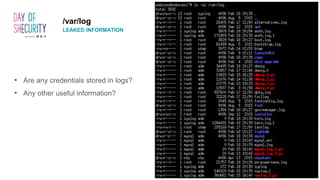
The document provides an in-depth overview of Linux privilege escalation methods, detailing definitions, strategies, and types of exploits including easy, sneaky, and boss modes. It outlines the importance of understanding user permissions, SUID/SGID bits, wildcard exploitation, and cron jobs in gaining unauthorized access. Additionally, it includes practical resources for further learning and contact information for the author.










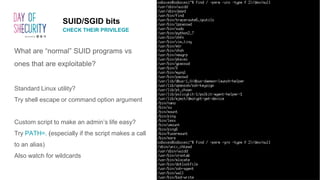
![SUID/SGID bits
CHECK THEIR PRIVILEGE
• What is the SUID/SGID bit?
• How to find a SUID/SGID binary?
• What runs as the root user?
find / -perm -u=s [-type f] 2>/dev/null
find / -perm -4000 [-type f] 2>/dev/null
• What runs in the root group?
find / -perm -g=s [-type f] 2>/dev/null
find / -perm -2000 [-type f] 2>/dev/null](https://image.slidesharecdn.com/doshw0012019-kbroussard-privescworkshop-forpdf-190227224216/85/Introduction-to-Linux-Privilege-Escalation-Methods-16-320.jpg)