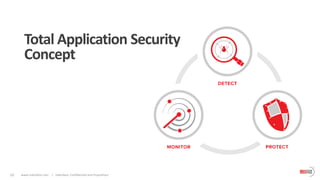
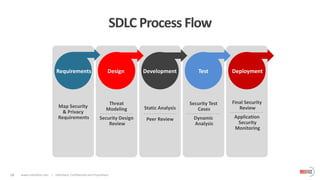
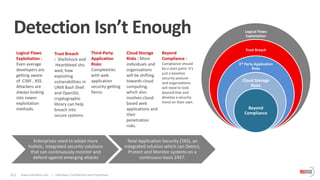
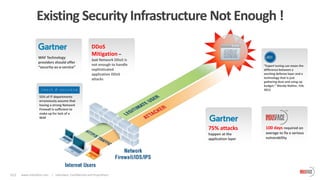
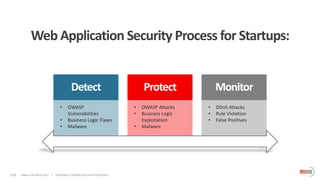
The document outlines the critical importance of application layer security for startups, emphasizing that most security breaches occur at this level due to vulnerabilities in web applications. It advocates for a comprehensive application security strategy that includes continuous testing, proactive monitoring, and integration of security throughout the software development life cycle. Additionally, it highlights the need for specialized security solutions, such as web application firewalls, to protect against evolving threats and ensures compliance with industry standards.