Indian cyber law & acts
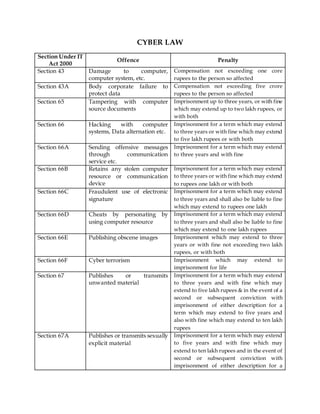
- 1. CYBER LAW Section Under IT Act 2000 Offence Penalty Section 43 Damage to computer, computer system, etc. Compensation not exceeding one core rupees to the person so affected Section 43A Body corporate failure to protect data Compensation not exceeding five crore rupees to the person so affected Section 65 Tampering with computer source documents Imprisonment up to three years, or with fine which may extend up to two lakh rupees, or with both Section 66 Hacking with computer systems, Data alternation etc. Imprisonment for a term which may extend to three years or with fine which may extend to five lakh rupees or with both Section 66A Sending offensive messages through communication service etc. Imprisonment for a term which may extend to three years and with fine Section 66B Retains any stolen computer resource or communication device Imprisonment for a term which may extend to three years or with fine which may extend to rupees one lakh or with both Section 66C Fraudulent use of electronic signature Imprisonment for a term which may extend to three years and shall also be liable to fine which may extend to rupees one lakh Section 66D Cheats by personating by using computer resource Imprisonment for a term which may extend to three years and shall also be liable to fine which may extend to one lakh rupees Section 66E Publishing obscene images Imprisonment which may extend to three years or with fine not exceeding two lakh rupees, or with both Section 66F Cyber terrorism Imprisonment which may extend to imprisonment for life Section 67 Publishes or transmits unwanted material Imprisonment for a term which may extend to three years and with fine which may extend to five lakh rupees & in the event of a second or subsequent conviction with imprisonment of either description for a term which may extend to five years and also with fine which may extend to ten lakh rupees Section 67A Publishes or transmits sexually explicit material Imprisonment for a term which may extend to five years and with fine which may extend to ten lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a
- 2. term which may extend to seven years and also with fine which may extend to ten lakh rupees Section 67B Abusing children online Imprisonment for a term which may extend to five years and with a fine which may extend to ten lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a term which may extend to seven years and also with fine which may extend to ten lakh rupees. Section 67C Preservation of information by intermediary Imprisonment for a term which may extend to three years and shall also be liable to fine Section 70 Un authorized access to protected system Imprisonment for a term which may extend to ten years and shall also be liable to fine Section 71 Misrepresentation to the controller or the certifying authority for obtaining license or electronic signature certificate Imprisonment for a term which may extend to two years, or with fine which may extend to one lakh rupees, or with both Section 72 Breach of Confidentiality and privacy Imprisonment for a term which may extend to two years, or with fine which may extend to one lakh rupees, or with both Section 72A Disclosure of information in breach of contract Imprisonment for a term which may extend to three years, or with a fine which may extend to five lakh rupees, or with both Section 73 & 74 Publishing false digital signature certificates Imprisonment for a term which may extend to two years, or with fine which may extend to one lakh rupees, or with both Section 383 IPC Web-Jacking Section 420 IPC Bogus websites, Cyber frauds Shall be punished with imprisonment of either description for a term which may extend to seven years, and shall also be liable to fine. Section 463 IPC E-mail spoofing Section 499 IPC Sending defamatory messages by email Section 503 IPC Sending threatening messages by email Shall be punished with simple imprisonment for a term which may extend to one year, or with fine, or with both.
- 3. CYBER CRIME LAWS IN INDIA Sec 43: Damage to computer, computer system, etc. (a) Whoever (1) willfully and maliciously engages in a knowing pattern of conduct or series of acts over a period of time directed at a specific person which seriously alarms or annoys that person and would cause a reasonable person to suffer substantial emotional distress, and (2) makes a threat with the intent to place the person in imminent fear of death or bodily injury, shall be guilty of the crime of stalking and shall be punished by imprisonment in the state prison for not more than 5 years or by a fine of not more than $1,000, or imprisonment in the house of correction for not more than 21/2 years or by both such fine and imprisonment. The conduct, acts or threats described in this subsection shall include, but not be limited to, conduct, acts or threats conducted by mail or by use of a telephonic or telecommunication device or electronic communication device including, but not limited to, any device that transfers signs, signals, writing, images, sounds, data, or intelligence of any nature transmitted in whole or in part by a wire, radio, electromagnetic, photo-electronic or photo-optical system, including, but not limited to, electronic mail, internet communications, instant messages or facsimile communications. A prosecution commenced hereunder shall not be placed on file or continued without a finding, and the sentence imposed upon a person convicted of violating any provision of this subsection shall not be reduced to less than the mandatory minimum term of imprisonment as established herein, nor shall said sentence of imprisonment imposed upon any person be suspended or reduced until such person shall have served said mandatory term of imprisonment. Whoever, after having been convicted of the crime of stalking, commits a second or subsequent such crime shall be punished by imprisonment in a jail or the state prison for not less than two years and not more than ten years. No sentence imposed under the provisions of this subsection shall be less than a mandatory minimum term of imprisonment of two years. Sec 43A: Body corporate failure to protect data (a) Whoever willfully and maliciously engages in a knowing pattern of conduct or series of acts over a period of time directed at a specific person, which seriously alarms that person and would cause a reasonable person to suffer substantial emotional distress, shall be guilty of the crime of criminal harassment and shall be punished by imprisonment in a house of correction for not more than 21/2 years or by a fine of not more than $1,000, or by both such fine and imprisonment. The conduct or acts described in this paragraph shall include, but not be limited to, conduct or acts conducted by mail or by use of a telephonic or telecommunication device or electronic communication device including, but not limited to, any device that transfers signs, signals, writing, images, sounds, data or intelligence of any nature transmitted in whole or in part by a wire, radio, electromagnetic, photo-electronic or photo-optical system, including, but not limited to, electronic mail, internet communications, instant messages or facsimile communications. (b) Whoever, after having been convicted of the crime of criminal harassment, commits a second or subsequent such crime, or whoever commits the crime of criminal harassment having previously been convicted of a violation of section 43, shall be punished by imprisonment in a house of correction for not more than two and one-half years or by imprisonment in the state prison for not more than ten years. Sec 65: Tampering with Computer Source Documents Whoever knowingly or intentionally conceals, destroys or alters or intentionally or knowingly causes another to conceal, destroy or alter any computer source code used for a computer, computer programme, computer system or computer network, when the computer source code
- 4. is required to be kept or maintained by law for the time being in force, shall be punishable with imprisonment up to three years, or with fine which may extend up to two lakh rupees, or with both. Explanation - For the purposes of this section, "Computer Source Code" means the listing of programmes, Computer Commands, Design and layout and programme analysis of computer resource in any form. Sec 66 Computer Related Offences If any person, dishonestly, or fraudulently, does any act referred to in section 43, he shall be punishable with imprisonment for a term which may extend to three years or with fine which may extend to five lakh rupees or with both. Explanation: For the purpose of this section,- a) the word "dishonestly" shall have the meaning assigned to it in section 24 of the Indian Penal Code;0. b) the word "fraudulently" shall have the meaning assigned to it in section 25 of the Indian Penal Code. Sec 66A Punishment for sending offensive messages through communication service, etc Any person who sends, by means of a computer resource or a communication device,- a) any information that is grossly offensive or has menacing character; or b) any information which he knows to be false, but for the purpose of causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred, or ill will, persistently by making use of such computer resource or a communication device, c) any electronic mail or electronic mail message for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages shall be punishable with imprisonment for a term which may extend to three years and with fine. Explanation: For the purposes of this section, terms "Electronic mail" and "Electronic Mail Message" means a message or information created or transmitted or received on a computer, computer system, computer resource or communication device including attachments in text, image, audio, video and any other electronic record, which may be transmitted with the message. Sec 66B Punishment for dishonestly receiving stolen computer resource or communication device Whoever dishonestly receives or retains any stolen computer resource or communication device knowing or having reason to believe the same to be stolen computer resource or communication device, shall be punished with imprisonment of either description for a term which may extend to three years or with fine which may extend to rupees one lakh or with both. Sec 66C Punishment for identity theft Whoever, fraudulently or dishonestly make use of the electronic signature, password or any other unique identification feature of any other person, shall be punished with imprisonment of either description for a term which may extend to three years and shall also be liable to fine which may extend to rupees one lakh. Sec 66D Punishment for cheating by personation by using computer resource Whoever, by means of any communication device or computer resource cheats by personation, shall be punished with imprisonment of either description for a term which may extend to three years and shall also be liable to fine which may extend to one lakh rupees. Sec 66E Punishment for violation of privacy
- 5. Whoever, intentionally or knowingly captures, publishes or transmits the image of a private area of any person without his or her consent, under circumstances violating the privacy of that person, shall be punished with imprisonment which may extend to three years or with fine not exceeding two lakh rupees, or with both Explanation.- For the purposes of this section-- (a) “transmit” means to electronically send a visual image with the intent that it be viewed by a person or persons; (b) “capture”, with respect to an image, means to videotape, photograph, film or record by any means; (c) “private area” means the naked or undergarment clad genitals, pubic area, buttocks or female breast; (d) “publishes” means reproduction in the printed or electronic form and making it available for public; (e) “under circumstances violating privacy” means circumstances in which a person can have a reasonable expectation that-- (i) he or she could disrobe in privacy, without being concerned that an image of his private area was being captured; or (ii) any part of his or her private area would not be visible to the public, regardless of whether that person is in a public or private place. Sec 66F Punishment for cyber terrorism (1) Whoever,- (A) with intent to threaten the unity, integrity, security or sovereignty of India or to strike terror in the people or any section of the people by- (i) denying or cause the denial of access to any person authorized to access computer resource; or (ii) attempting to penetrate or access a computer resource without authorisation or exceeding authorized access; or (iii) introducing or causing to introduce any Computer Contaminant. and by means of such conduct causes or is likely to cause death or injuries to persons or damage to or destruction of property or disrupts or knowing that it is likely to cause damage or disruption of supplies or services essential to the life of the community or adversely affect the critical information infrastructure specified under section 70, or (B) knowingly or intentionally penetrates or accesses a computer resource without authorisation or exceeding authorized access, and by means of such conduct obtains access to information, data or computer database that is restricted for reasons of the security of the State or foreign relations; or any restricted information, data or computer database, with reasons to believe that such information, data or computer database so obtained may be used to cause or likely to cause injury to the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, public order, decency or morality, or in relation to contempt of court, defamation or incitement to an offence, or to the advantage of any foreign nation, group of individuals or otherwise, commits the offence of cyber terrorism. (2) Whoever commits or conspires to commit cyber terrorism shall be punishable with imprisonment which may extend to imprisonment for life’. Sec 67 Punishment for publishing or transmitting obscene material in electronic form Whoever publishes or transmits or causes to be published in the electronic form, any material which is lascivious or appeals to the prurient interest or if its effect is such as to tend to deprave and corrupt persons who are likely, having regard to all relevant circumstances, to read, see or
- 6. hear the matter contained or embodied in it, shall be punished on first conviction with imprisonment of either description for a term which may extend to three years and with fine which may extend to five lakh rupees and in the event of a second or subsequent conviction with imprisonment of either description for a term which may extend to five years and also with fine which may extend to ten lakh rupees. Sec 67A Punishment for publishing or transmitting of material containing sexually explicit act, etc. in electronic form Whoever publishes or transmits or causes to be published or transmitted in the electronic form any material which contains sexually explicit act or conduct shall be punished on first conviction with imprisonment of either description for a term which may extend to five years and with fine which may extend to ten lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a term which may extend to seven years and also with fine which may extend to ten lakh rupees. Exception: This section and section 67 does not extend to any book, pamphlet, paper, writing, drawing, painting, representation or figure in electronic form- (i) the publication of which is proved to be justified as being for the public good on the ground that such book, pamphlet, paper, writing, drawing, painting, representation or figure is in the interest of science,literature,art,or learning or other objects of general concern; or (ii) which is kept or used bona fide for religious purposes. 67B Punishment for publishing or transmitting of material depicting children in sexually explicit act, etc. in electronic form Whoever- (a) publishes or transmits or causes to be published or transmitted material in any electronic form which depicts children engaged in sexually explicit act or conduct or (b) creates text or digital images, collects, seeks, browses, downloads, advertises, promotes, exchanges or distributes material in any electronic form depicting children in obscene or indecent or sexually explicit manner or (c) cultivates, entices or induces children to online relationship with one or more children for and on sexually explicit act or in a manner that may offend a reasonable adult on the computer resource or (d) facilitates abusing children online or (e) records in any electronic form own abuse or that of others pertaining to sexually explicit act with children, shall be punished on first conviction with imprisonment of either description for a term which may extend to five years and with a fine which may extend to ten lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a term which may extend to seven years and also with fine which may extend to ten lakh rupees: Provided that the provisions of section 67, section 67A and this section does not extend to any book, pamphlet, paper, writing, drawing, painting, representation or figure in electronic form- (i) The publication of which is proved to be justified as being for the public good on the ground that such book, pamphlet, paper writing, drawing, painting, representation or figure is in the interest of science, literature, art or learning or other objects of general concern; or (ii) which is kept or used for bonafide heritage or religious purposes Explanation: For the purposes of this section, "children" means a person who has not completed the age of 18 years. Sec 67C Preservation and Retention of information by intermediaries (1) Intermediary shall preserve and retain such information as may be specified for such duration and in such manner and format as the Central Government may prescribe.
- 7. (2) Any intermediary who intentionally or knowingly contravenes the provisions of sub section (1) shall be punished with an imprisonment for a term which may extend to three years and shall also be liable to fine. Sec 69 Powers to issue directions for interception or monitoring or decryption of any information through any computer resource (1) Where the central Government or a State Government or any of its officer specially authorized by the Central Government or the State Government, as the case may be, in this behalf may, if is satisfied that it is necessary or expedient to do in the interest of the sovereignty or integrity of India, defense of India, security of the State, friendly relations with foreign States or public order or for preventing incitement to the commission of any cognizable offence relating to above or for investigation of any offence, it may, subject to the provisions of sub-section (2), for reasons to be recorded in writing, by order, direct any agency of the appropriate Government to intercept, monitor or decrypt or cause to be intercepted or monitored or decrypted any information transmitted received or stored through any computer resource. (2) The Procedure and safeguards subject to which such interception or monitoring or decryption may be carried out, shall be such as may be prescribed (3) The subscriber or intermediary or any person in charge of the computer resource shall, when called upon by any agency which has been directed under sub section (1), extend all facilities and technical assistance to - (a) provide access to or secure access to the computer resource containing such informat ion; generating, transmitting, receiving or storing such information; or (b) intercept or monitor or decrypt the information, as the case may be; or (c) provide information stored in computer resource. (4) The subscriber or intermediary or any person who fails to assist the agency referred to in sub-section (3) shall be punished with an imprisonment for a term which may extend to seven years and shall also be liable to fine. Sec 69A Power to issue directions for blocking for public access of any information through any computer resource (1) Where the Central Government or any of its officer specially authorized by it in this behalf is satisfied that it is necessary or expedient so to do in the interest of sovereignty and integrity of India, defense of India, security of the State, friendly relations with foreign states or public order or for preventing incitement to the commission of any cognizable offence relating to above, it may subject to the provisions of sub-sections (2) for reasons to be recorded in writing, by order direct any agency of the Government or intermediary to block access by the public or cause to be blocked for access by public any information generated, transmitted, received, stored or hosted in any computer resource. (2) The procedure and safeguards subject to which such blocking for access by the public may be carried out shall be such as may be prescribed. (3) The intermediary who fails to comply with the direction issued under subsection (1) shall be punished with an imprisonment for a term which may extend to seven years and also be liable to fine. Sec 69B Power to authorize to monitor and collect traffic data or information through any computer resource for Cyber Security (1) The Central Government may, to enhance Cyber Security and for identification, analysis and prevention of any intrusion or spread of computer contaminant in the country, by notification in the official Gazette, authorize any agency of the Government to monitor and collect traffic data or information generated, transmitted, received or stored in any computer resource.
- 8. (2) The Intermediary or any person in-charge of the Computer resource shall when called upon by the agency which has been authorized under sub-section (1), provide technical assistance and extend all facilities to such agency to enable online access or to secure and provide online access to the computer resource generating , transmitting, receiving or storing such traffic data or information. (3) The procedure and safeguards for monitoring and collecting traffic data or information, shall be such as may be prescribed. (4) Any intermediary who intentionally or knowingly contravenes the provisions of sub-section( 2) shall be punished with an imprisonment for a term which may extend to three years and shall also be liable to fine. Explanation: For the purposes of this section, (i) "Computer Contaminant" shall have the meaning assigned to it in section 43 (ii) "traffic data" means any data identifying or purporting to identify any person, computer system or computer network or location to or from which the communication is or may be transmitted and includes communications origin, destination, route, time, date, size, duration or type of underlying service or any other information. Sec 70 Protected system (1) The appropriate Government may, by notification in the Official Gazette, declare any computer resource which directly or indirectly affects the facility of Critical Information Infrastructure, to be a protected system. Explanation: For the purposes of this section, "Critical Information Infrastructure" means the computer resource, the incapacitation or destruction of which , shall have debilitating impact on national security, economy, public health or safety. (2) The appropriate Government may, by order in writing, authorize the persons who are authorized to access protected systems notified under sub-section (1) (3) Any person who secures access or attempts to secure access to a protected system in contravention of the provisions of this section shall be punished with imprisonment of either description for a term which may extend to ten years and shall also be liable to fine. (4) The Central Government shall prescribe the information security practices and procedures for such protected system. Sec 71 Penalty for misrepresentation Whoever makes any misrepresentation to, or suppresses any material fact from, the Controller or the Certifying Authority for obtaining any license or Electronic Signature Certificate, as the case may be, shall be punished with imprisonment for a term which may extend to two years, or with fine which may extend to one lakh rupees, or with both. OFFENSES COVERED UNDER IPC AND SPECIAL LAWS Sec 503 IPC: Sending threatening messages by email Whoever threatens another with any injury to his person, reputation or property, or to the person or reputation of any one in whom that person is interested, with intent to cause alarm to that person, or to cause that person to do any act which he is not legally bound to do, or to omit to do any act which that person is legally entitled to do, as the means of avoiding the execution of such threat, commits criminal intimidation. Explanation-A threat to inure the reputation of any deceased person in whom the person threatened is interested, is within this section. Sec 499 IPC: Sending defamatory messages by e-mail
- 9. Whoever, by words either spoken or intended to be read, or by signs or by visible representations, makes or publishes any imputation concerning any person intending to harm, or knowing or having reason to believe that such imputation will harm, the reputation of such person, is said, except in the cases hereinafter expected, of defame that person. Explanation 1-It may amount to defamation to impute anything to a deceased person, if the imputation would harm the reputation of that person if living, and is intended to be hurtful to the feelings of his family or other near relatives. Explanation 2-It may amount to defamation to make an imputation concerning a company or an association or collection of persons as such. Explanation 3-An imputation in the form of an alternative or expressed ironically, may amount to defamation. Explanation 4-No imputation is said to harm a person's reputation, unless that imputation directly or indirectly, in the estimation of others, lowers the moral or intellectual character of that person, or lowers the character of that person in respect of his caste or of his calling, or lowers the credit of that person, or causes it to be believed that the body of that person is in a loathsome state, or in a state generally considered as disgraceful. Sec 463 IPC: E-mail spoofing Whoever makes any false documents or electronic record part of a document or electronic record with, intent to cause damage or injury], to the public or to any person, or to support any claim or title, or to cause any person to part with property, or to enter into any express or implied contract, or with intent to commit fraud or that fraud may be committed, commits forgery. Sec 420 IPC: Bogus websites, cyber frauds Whoever cheats and thereby dishonestly induces the person deceived any property to any person, or to make, alter or destroy the whole or any part of a valuable security, or anything which is signed or sealed, and which is capable of being converted into a valuable security, shall be punished with imprisonment of either description for a term which may extend to seven years, and shall also be liable to fine. Sec 383 IPC: Web-Jacking Whoever intentionally puts any person in fear of any injury to that person, or to any other, and thereby dishonestly induces the person so put in fear to deliver to any property or valuable security, or anything signed or sealed which may be converted into a valuable security, commits "extortion". Sec 509 IPC: Word, gesture or act intended to insult the modesty of a woman Whoever, intending to insult the modesty of any woman, utters any word, makes any sound or gesture, or exhibits any object, intending that such word or sound shall be heard, of that such gesture or object shall be seen, by such woman, or intrudes upon the privacy of such woman, shall be punished with simple imprisonment for a term which may extend to one year, or with fine, or with both.
- 10. CASES i) State of Tamil Nadu Vs Suhas Katti The Case of Suhas Katti is notable for the fact that the conviction was achieved successfully within a relatively quick time of 7 months from the filing of the FIR. Considering that similar cases have been pending in other states for a much longer time, the efficient handling of the case which happened to be the first case of the Chennai Cyber Crime Cell going to trial deserves a special mention. The case related to posting of obscene, defamatory and annoying message about a divorcee woman in the yahoo message group. E-Mails were also forwarded to the victim for information by the accused through a false e-mail account opened by him in the name of the victim. The posting of the message resulted in annoying phone calls to the lady in the belief that she was soliciting. Based on a complaint made by the victim in February 2004, the Police traced the accused to Mumbai and arrested him within the next few days. The accused was a known family friend of the victim and was reportedly interested in marrying her. She however married another person. This marriage later ended in divorce and the accused started contacting her once again. On her reluctance to marry him, the accused took up the harassment through the Internet. On 24-3-2004 Charge Sheet was filed u/s 67 of IT Act 2000, 469 and 509 IPC before The Hon’ble Addl. CMM Egmore by citing 18 witnesses and 34 documents and material objects. The same was taken on file in C.C.NO.4680/2004. On the prosecution side 12 witnesses were examined and entire documents were marked as Exhibits. The Defence argued that the offending mails would have been given either by ex-husband of the complainant or the complainant herself to implicate the 104 accused as accused alleged to have turned down the request of the complainant to marry her. Further the Defence counsel argued that some of the documentary evidence was not sustainable under Section 65B of the Indian Evidence Act. However, the court relied upon the expert witnesses and other evidence produced before it, including the witnesses of the Cyber Cafe owners and came to the conclusion that the crime was conclusively proved. Ld. Additional Chief Metropolitan Magistrate, Egmore, delivered the judgement on 5-11-04 as follows: " The accused is found guilty of offences under section 469, 509 IPC and 67 of IT Ac t 2000 and the accused is convicted and is sentenced for the offence to undergo RI for 2 years under 469 IPC and to pay fine of Rs.500/-and for the offence u/s 509 IPC sentenced to undergo 1 year Simple imprisonment and to pay fine of Rs.500/- and for the offence u/s 67 of IT Act 2000 to undergo RI for 2 years and to pay fine of Rs.4000/- All sentences to run concurrently." This is considered as the first case convicted under Section 67 of Information Technology Act 2000 in India. ii) Syed Asifuddin and Ors. V. The State of AP. & Anr., 2005CriLJ4314 Tata Indicom employees were arrested for manipulation of the electronic 32-bit number (ESN) programmed into cell phones that were exclusively franchised to Reliance Infocomm. The court held that such manipulation amounted to tampering with computer source code as envisaged by section 65 of the Information Technology Act, 2000. Reliance Infocomm launched a scheme under which a cell phone subscriber was given a digital handset worth Rs. 10,500/- as well as service bundle for 3 years with an initial payment of Rs. 3350/- and monthly outflow of Rs. 600/-. The subscriber was also provided a 1 year warranty and 3 year insurance on the handset. The condition was that the handset was technologically locked so that it would only work with the Reliance Infocomm services. If the customer 105 wanted to leave Reliance services, he would
- 11. have to pay some charges including the true price of the handset. Since the handset was of a high quality, the market response to the scheme was phenomenal. Unidentified persons contacted Reliance customers with an offer to change to a lower priced Tata Indicom scheme. As part of the deal, their phone would be technologically "unlocked" so that the exclusive Reliance handsets could be used for the Tata Indicom service. Reliance officials came to know about this "unlocking" by Tata employees and lodged a First Information Report (FIR) under various provisions of the Indian Penal Code, Information Technology Act and the Copyright Act. The police then raided some offices of Tata Indicom in Andhra Pradesh and arrested a few Tata Tele Services Limited officials for reprogramming the Reliance handsets. These arrested persons approached the High Court requesting the court to quash the FIR on the grounds that their acts did not violate the said legal provisions. Some of the issues raised by the defence in the case were - It is always open for the subscriber to change from one service provider to the other service provider; The subscriber who wants to change from Tata Indicom always takes his handset, to other service providers to get service connected and to give up Tata services; The handsets brought to Tata by Reliance subscribers are capable of accommodating two separate lines and can be activated on principal assignment mobile ( NAM 1 or NAM 2). The mere activation of NAM 1 or NAM 2 by Tata in relation to a handset brought to it by a Reliance subscriber does not amount to any crime; A telephone handset is neither a computer nor a computer system containing a computer programmed; there is no law in force which requires the maintenance of "computer source code". Hence section 65 of the Information Technology Act does not apply. Following were the observations of the Court – As per section 2 of the Information Technology Act, any electronic, magnetic or optical device used for storage of information received through satellite, microwave or other communication media and the 106 devices which are programmable and capable of retrieving any information by manipulations of electronic, magnetic or optical impulses is a computer which can be used as computer system in a computer network. The instructions or programmed given to computer in a language known to the computer are not seen by the users of the computer/consumers of computer functions. This is known as source code in computer parlance. ESN and SID come within the definition of "computer source code" under section 65 of the Information Technology Act. When ESN is altered, the offence under Section 65 of Information Technology Act is attracted because every service provider has to maintain its own SID code and also give a customer specific number to each instrument used to avail the services provided. iii) P.R. Transport Agency Vs. Union of India (UOI) Bharat Coking Coal Ltd (BCC) held an e-auction for coal in different lots. P.R. Transport Agency's (PRTA) bid was accepted for 4000 metric tons of coal from Dobari Colliery. The acceptance letter was issued on 19th July 2005 by e-mail to PRTA's e-mail address. Acting upon this acceptance, PRTA deposited the full amount of Rs. 81.12 lakh through a cheque in favour of BCC. This cheque was accepted and encashed by BCC. BCC did not deliver the coal to PRTA. Instead it e-mailed PRTA saying that the sale as well as the e-auction in favour of PRTA stood cancelled "due to some technical and unavoidable reasons". The only reason for this cancellation was that there was some other person whose bid for the same coal was slightly higher than that of PRTA. Due to some flaw in the computer or it’s programmed or feeding of data the higher bid had not been considered earlier. This communication was challenged by PRTA in the High Court of Allahabad.
- 12. BCC objected to the "territorial jurisdiction" of the Court on the grounds that no part of the cause of action had arisen within U.P. The communication of the 107 acceptance of the tender was received by the petitioner by e-mail at Chandauli (U.P.). Hence the contract (from which the dispute arose) was completed at Chandauli (U.P). The completion of the contract is a part of the "cause of action'. The place where the contract was completed by receipt of communication of acceptance is a place where 'part of cause of action' arises. The Court observed – In reference to contracts made by telephone, telex or fax, the contract is complete when and where the acceptance is received. However, this principle can apply only where the transmitting terminal and the receiving terminal are at fixed points. In case of e-mail, the data (in this case acceptance) can be transmitted from anywhere by the e-mail account holder. It goes to the memory of a 'server' which may be located anywhere and can be retrieved by the addressee account holder from anywhere in the world. Therefore, there is no fixed point either of transmission or of receipt. Section 13(3) of the Information Technology Act has covered this difficulty of "no fixed point either of transmission or of receipt". According to this section "...an electronic record is deemed to be received at the place where the addressee has his place of business." The acceptance of the tender will be deemed to be received by PRTA at the places where it has place of business. In this case it is Varanasi and Chandauli (both in U.P.) The acceptance was received by PRTA at Chandauli / Varanasi. The contract became complete by receipt of such acceptance. Both these places are within the territorial jurisdiction of the High Court of Allahabad. Therefore, a part of the cause of action has arisen in U.P. and the court has territorial jurisdiction. iv) SMC Pneumatics (India) Private Limited v. Jogesh Kwatra A company’s employee started sending derogatory, defamatory and obscene emails about company’s Managing Director. The emails were anonymous and frequent and were sent to many company’s business associates to tarnish the image and goodwill of the company. The accused was identified by the company by the private computer expert. Delhi High Court granted an injunction and restrained the employee from sending, publishing and transmitting emails which are defamatory or derogatory to the plaintiffs. v) Ritu Kohli case One Mrs. Ritu Kohli complained to the police against the a person who was using her identity to chat over the Internet at the website www.mirc.com, mostly in the Delhi channel for four consecutive days. Mrs. Kohli further complained that the person was chatting on the Net, using her name and giving her address and was talking obscene language. The same person was also deliberately giving her telephone number to other chatters encouraging them to call Ritu Kohli at odd hours. Consequently, Mrs Kohli received almost 40 calls in three days mostly at odd hours from as far away as Kuwait, Cochin, Bombay and Ahmedabad. The said calls created havoc in the personal life and mental peace of Ritu Kohli who decided to report the matter. The IP addresses were traced and the police investigated the entire matter and ultimately arrested Manish Kathuria on the said complaint. Manish apparently pleaded guilty and was arrested. A case was registered under section 509, of the Indian Penal Code (IPC). vi) Avnish Bajaj Vs. State (N.C.T.) of Delhi Avnish Bajaj – CEO of Baazee.com, a customer-to-customer website, which facilitates the online sale of property. Baazee.com receives commission from such sales and also generates revenue from advertisements carried on its web pages. An obscene MMS clipping was listed for sale on Baazee.com on 27th November, 2004 in the name
- 13. of “DPS Girl having fun”. Some copies of the clipping were sold through Baazee.com and the seller received the money for the sale. Avnish Bajaj was arrested under section 67 of the Information Technology Act, 2000. The arguments of the defendant were that - Section 67 of the Information Technology Act relates to publication of obscene material. It does not relate to transmission of such material. On coming to learn of the illegal character of the sale, remedial steps were taken within 38 hours, since the intervening period was a weekend. The findings of the Court – It has not been established from the evidence that any publication took place by the accused, directly or indirectly. The actual obscene recording/clip could not be viewed on the portal of Baazee.com. The sale consideration was not routed through the accused. Prima facie Baazee.com had endeavored to plug the loophole. The accused had actively participated in the investigations. The nature of the alleged offence is such that the evidence has already crystallized and may even be tamper proof. Even though the accused is a foreign citizen, he is of Indian origin with family roots in India. The evidence that has been collected indicates only that the obscene material may have been unwittingly offered for sale on the website. The evidence that has been collected indicates that the heinous nature of the alleged crime may be attributable to some other person. The court granted bail to Mr. Bajaj subject to furnishing two sureties of Rs. 1 lakh each. The court ordered Mr. Bajaj to surrender his passport and not to leave India without the permission of the Court. The court also ordered Mr. Bajaj to participate and assist in the investigation.
- 14. IN THE HIGH COURT OF ANDHRA PRADESH Cri. Petn. Nos. 2601 and 2602 of 2003 Decided On: 29.07.2005 Appellants: Syed Asifuddin and Ors. Vs. Respondent: The State of Andhra Pradesh and Anr. Summary of the case Tata Indicom employees were arrested for manipulation of the electronic 32-bit number (ESN) programmed into cell phones that were exclusively franchised to Reliance Information. The court held that such manipulation amounted to tampering with computer source code as envisaged by section 65 of the Information Technology Act, 2000. Background of the case Reliance Info comm launched a scheme under which a cell phone subscriber was given a digital handset worth Rs. 10,500 as well as service bundle for 3 years with an initial payment of Rs. 3350 and monthly outflow of Rs. 600. The subscriber was also provided a 1 year warranty and 3 year insurance on the handset. The condition was that the handset was technologically locked so that it would only work with the Reliance Info comm services. If the customer wanted to leave Reliance services, he would have to pay some charges including the true price of the handset. Since the handset was of a high quality, the market response to the scheme was phenomenal. Unidentified persons contacted Reliance customers with an offer to change to a lower priced Tata Indicom scheme. As part of the deal, their phone would be technologically “unlocked” so that the exclusive Reliance handsets could be used for the Tata Indicom service. Reliance officials came to know about this “unlocking” by Tata employees and lodged a First Information Report (FIR) under various provisions of the Indian Penal Code, Information Technology Act and the Copyright Act. The police then raided some offices of Tata Indicom in Andhra Pradesh and arrested a few Tata Tele Services Limited officials for reprogramming the Reliance handsets. These arrested persons approached the High Court requesting the court to quash the FIR on the grounds that their acts did not violate the said legal provisions. Issues raised by the Defence 1. It is always open for the subscriber to change from one service provider to the other service provider. 2. The subscriber who wants to change from Tata Indicom always takes his handset, to other service providers to get service connected and to give up Tata services. 3. The handsets brought to Tata by Reliance subscribers are capable of accommodating two separate lines and can be activated on principal assignment mobile (NAM 1 or NAM 2). The mere activation of NAM 1 or NAM 2 by Tata in relation to a handset brought to it by a Reliance subscriber does not amount to any crime. 4. A telephone handset is neither a computer nor a computer system containing a computer programme. 5. There is no law in force which requires the maintenance of "computer source code". Hence section 65 of the Information Technology Act does not apply. Findings of the court 1. As per section 2 of the Information Technology Act, any electronic, magnetic or optical device used for storage of information received through satellite, microwave or other communication media and the devices which are programmable and capable of retrieving any information by
- 15. manipulations of electronic, magnetic or optical impulses is a computer which can be used as computer system in a computer network. 2. The instructions or programme given to computer in a language known to the computer are not seen by the users of the computer/consumers of computer functions. This is known as source code in computer parlance. 3. A city can be divided into several cells. A person using a phone in one cell will be plugged to the central transmitter of the telecom provider. This central transmitter will receive the signals and then divert them to the relevant phones. 4. When the person moves from one cell to another cell in the same city, the system i.e., Mobile Telephone Switching Office (MTSO) automatically transfers signals from tower to tower. 5. All cell phone service providers have special codes dedicated to them and these are intended to identify the phone, the phone's owner and the service provider. 6. System Identification Code (SID) is a unique 5-digit number that is assigned to each carrier by the licensor. Every cell phone operator is required to obtain SID from the Government of India. SID is programmed into a phone when one purchases a service plan and has the phone activated. 7. Electronic Serial Number (ESN) is a unique 32-bit number programmed into the phone when it is manufactured by the instrument manufacturer. ESN is a permanent part of the phone. 8. Mobile Identification Number (MIN) is a 10-digit number derived from cell phone number given to a subscriber. MIN is programmed into a phone when one purchases a service plan. 9. When the cell phone is switched on, it listens for a SID on the control channel, which is a special frequency used by the phone and base station to talk to one another about things like call set-up and channel changing. 10. If the phone cannot find any control channels to listen to, the cell phone displays "no service" message as it is out of range. 11. When cell phone receives SID, it compares it to the SID programmed into the phone and if these code numbers match, cell knows that it is communicating with its home system. Along with the SID, the phone also transmits registration request and MTSO which keeps track of the phone's location in a database, knows which cell phone you are using and gives a ring. 12. So as to match with the system of the cell phone provider, every cell phone contains a circuit board, which is the brain of the phone. It is a combination of several computer chips programmed to convert analog to digital and digital to analog conversion and translation of the outgoing audio signals and incoming signals. 13. This is a micro processor similar to the one generally used in the compact disk of a desktop computer. Without the circuit board, cell phone instrument cannot function. 14. When a Reliance customer opts for its services, the MIN and SID are programmed into the handset. If someone manipulates and alters ESN, handsets which are exclusively used by them become usable by other service providers like TATA Indicom. Conclusions of the court 1. A cell phone is a computer as envisaged under the Information Technology Act. 2. ESN and SID come within the definition of “computer source code” under section 65 of the Information Technology Act. 3. When ESN is altered, the offence under Section 65 of Information Technology Act is attracted because every service provider has to maintain its own SID code and also give a customer specific number to each instrument used to avail the services provided. 4. Whether a cell phone operator is maintaining computer source code, is a matter of evidence.
- 16. 5. In Section 65 of Information Technology Act the disjunctive word "or" is used in between the two phrases – a. "when the computer source code is required to be kept" b. "maintained by law for the time being in force" 1. Punjab-Haryana High Court (Section 65 and Section 66 of The IT Act,2000) Sanjay Kumar vs State Of Haryana on 10th Jan, 2013 CRR No.66 of 2013 (O&M) 1 Present criminal revision has been preferred by the petitioner against judgment dated 21.08.2012 passed by the learned Sessions Judge, Faridabad, whereby an appeal preferred by the petitioner has been dismissed and judgment of conviction dated 01.09.2011 and order of sentence dated 03.09.2011 passed by learned Judicial Magistrate First CRR No.66 of 2013 (O&M) 2 Class, Faridabad, has been upheld, vide which the petitioner has been convicted for offences punishable under Sections 420, 467, 468, 471 of the Indian Penal Code and Sections 65 and 66 of the Information & Technology Act, 2000 and sentenced to undergo rigorous imprisonment as follows:- Under Section Period Fine 420 IPC Two years Rs.1,000/- 467 IPC Three years Rs.2,000/- 468 IPC Two years Rs.1,000/- 471 IPC Two years Rs.1,000/- 65 I.T. Act Two years Rs.1,000/- 66 I.T. Act Two years Rs.1000/- In default of payment of fine, the petitioner shall further undergo simple imprisonment for a period of two months. All the sentences were ordered to run concurrently. Brief facts of the prosecution case are that the Senior Branch Manager, Vijay Bank, NIT, Faridabad moved a complaint dated 11.02.2003 before the Police stating that the petitioner was deputed by M/s Virmati Software and Telecommunication Ltd. to maintain the Software System supplied by them to the bank. He was also looking Software System of certain other banks. In connection with rendering such services, the petitioner was having access to their accounting system which was computerized and was also in a position to enter into ledgers and various other accounts. While reconciling the accounts, certain discrepancies were pointed out by the officials of the bank and in that process, it was revealed that the accused-petitioner, who was having SB Account No. 21499 in his CRR No.66 of 2013 (O&M) 3 personal name in their bank, manipulated the entries by forging and fabricating certain entries from one account to another, from the computer system by handling the software and got the entries pertaining to the amount of the the bank and withdrew the amounts from the bank on various dates by issuing cheques in his own favour and withdrew the amount from the cash counter of the bank as well as through transfer/clearing transactions. As per enquiry, it has been revealed that the accused by carrying out forgery, fabricating the entries in the computer system of the bank, illegally and wrongfully, withdrew Rs.17,67,409/- from the bank and thus, caused wrongful gain to himself and wrongful loss to the bank. The said Bank came to know regarding the fraud committed by the accused on 07.02.2003. thereafter, the accused was called to the bank and he was confronted with the details of the fraud but he gave evasive replies as only admitted having embezzled a sum of Rs. 17 lacs without giving further information or revealing the exact amount of fraud or the modus operandi of the same and also assured to pay back the amount to the bank. On receipt of the complaint, a case bearing FIR No. 165 dated 11.02.2003, under Sections 406, 420, 467, 468, 469, 471 of the Indian Penal Code and Sections 65, 66 and 72 of the Information and Technology Act, 2000 was registered against the petitioner. After completion of investigation, challan against the accused-petitioner was presented in the Court. Thereafter, charge was framed against the accused petitioner to which he pleaded not guilty and claimed trial.
- 17. The prosecution, in order to prove its case, examined PW1 A. CRR No.66 of 2013 (O&M) 4 Siridhar, PW2 Girish Kumar Verma, PW3 Maheshwar Rath, PW4 Ramesh Kumar Malik and PW5 Dalip Singh, DSP. Thereafter, statement of the accused was recorded under Section 313 Cr.P.C. All the incriminating circumstances were put to the accused. He denied the same and pleaded innocence. The learned trial Court, after appreciation of the evidence,convicted and sentenced the petitioner as aforesaid vide judgment and order dated 01.09.2011 and 03.09.2011 respectively. Thereafter, the petitioner preferred an appeal, which was dismissed by the learned Sessions Judge, Faridabad vide judgment dated 21.08.2012. Hence, this criminal revision. I have heard learned counsel for the petitioner and perused the record. Learned counsel for the petitioner contends that the petitioner has been falsely implicated in this case as the complainant and eye witness were inimical to the petitioner as they were having a dispute about 15/16 years prior to the occurrence. Learned counsel further contends that there is no direct evidence to connect the petitioner with the alleged offence in question, therefore, no prima facie case has been made out against the petitioner I have considered the contentions of the learned counsel for the petitioner. From perusal of the judgments of both the Courts below, it transpires that the allegations against the petitioner are that the petitioner CRR No.66 of 2013 (O&M) 5 has manipulated the computerized Bank account i.e. the interest entries and thereby cheated the complainant bank by forging electronic record in order to cause wrongful loss to the bank and wrongful gain to himself to the tune of Rs.17,67,409/-. It has come in the documentary evidence on record that the petitioner has forged the entries in the bank record and had thereby withdrawn a sum of Rs.17,67,409/-. The learned Trial Court, after appreciating the evidence on record, observed as under:- "9. All the prosecution witnesses have supported the prosecution case. The complainant PW-1 A. Siridhar and PW-2 Girraj Parshad Sharma have stated that the accused Sanjay Kumar Bhatia was the employee of M/s Virmati Software and Telecommunication Ltd. and have been appointed in their branch for the purpose of maintenance of Software System supplied by them to the bank. This fact stand corroborated by document Ex.P36 wherein in Team No. 7 the name of Sanjay has been mentioned along with his residence number and Pager number. Sanjay Kumar Bhatia has also opened an A/c No. 21499 in their bank as evident from the account opening form of the accused Sanjay Bhatia placed on record as Ex.P37 along with specimen signature Card Ex.P38 and the cheque book issued register Ex.P39. Further, from the bank statement of account no. 21499, Ex.P8, on 1.8.2001, Rs.2,00,000/- was deposited by clearing and Rs.1/- as interest. However, nothing is mentioned as to what is the basis of clearing. In this regard, PW-3 Maheshwar Rath stated that during his inquiry he could not find any supporting document or CRR No.66 of 2013 (O&M) 6 voucher. The accused has also not produced any evidence in this regard. Rather, Ex.PW1/D shows that even the amount of Rs.2,00,000/- has been transferred from interest account on 1.8.2001. This fact stand corroborated by the report Ex.P34 wherein it is mentioned that the accused has increased interest portion in his own account through first time creation to the extent of Rs.2,00,000/- and then applied interest along with other SB accounts and to mislead the Branch employees, the accused has splitted the transaction into 2 parts,one entry is shown as "by interest credit" as Rs.1.00 and the other by clearing as Rs.2,00,000/- and, therefore, the amount of Rs.2,00,000/- is reflected in account statement as `by clearing'. 10. Similarly, using the same modus operandi, accused forged the interest entries on 1.8.2002 and 2.8.2000 and got deposited Rs.3,00,000/- and Rs.4,20,000/- respectively in his account.
- 18. 11. Further, the accused used the fixed deposit account of Sardar Jeet Singh. The account of Jeet Singh was opened on 8.3.2002 in which Rs.1,05,00,000/- was deposited on that day as evidence from Ex.P3. The statement of account of Sardar Jeet Singh Ex.P3 shows that an interest of Rs.8,46,489/- was deposited on 29.4.2002. However, the said interest calculated was an inflated one, calculated by forging entries to the effect as it the account of Jeet Singh was opened on a prior date. Thereafter, on 30.4.2002, accused transferred the amount of Rs.8,46,489/- to the account of Anil Kumar Sharma having A/c No. 22618 which had already been closed on 1.9.2001,as evident from Ex.P5, by forging the CRR No.66 of 2013 (O&M) 7 entries to the effect that it was changed in bank records form closed to o pen and on 8.5.2002, 13.5.2002 and 18.5.2002, accused transferred the amount of Rs.2,50,000/-, Rs. 2,50,000/- and Rs.3,47,409/- respectively from the account of Sh. Anil Kumar to his account as evident from Ex.P5 and Ex.P8 to Ex.P12. Further, PW-3 Sh. Maheshwar Rath has stated as also evident from his report Ex.P34 that the transaction rooted through theaccount of Jeet Singh and Anil Kumar has been deleted by accused using SRF files which were laterrecovered during Audit. 12. Moreover, Ex.P15 to Ex.P24 show that accused has withdrawn the said amount through cheques. 13. In this manner, the accused was dishonestly forged the bank records to cause wrongful loss to the bank and thereby cheated the concerned bank by depositing Rs.17,67,409/- in his account and thereafter withdrawing the same. Further, the accused has admitted his guilt vide letter Ex.P44. The signature of accused on the letter Ex.P44 are similar to the specimen signatures of accused on bank opening account card Ex.P38 as well as on the bank opening Account form Ex.P37. Furthermore, form the bare perusal of the confessional statement Ex.P44, it clearly emanates that the manner in which the word `Sanjay' has been written is similar to the manner word `Sanjay' has been written by accused below his signatures by accused as he even returned in his statement under Section 313 Cr.P.C. Moreover, Ex.P47 and Ex.P48 show that accused has tendered Rs.3,50,000/- to the bank in respect of the amount fraudulently withdrawn by him which shows the CRR No.66 of 2013 (O&M) 8 admission of guilt as evident from Ex.P47 and Ex.P48. 14. On the other hand, the learned counsel for the accused during the course of arguments has argued that no specific password was allotted to Sanjay. However, no doubt password is given to an employee but it has surfaced in the testimonies of the prosecution witnesses that for the purpose of maintaining the software and in this manner had assess to all those files to which only the employee of the bank could have. Moreover, as the amount was deposited in the account of accused and he has withdrawn it, there is no force in said argument. 15. In this manner, the accused had cheated the bank and forged the electronic record to cause wrongful loss to bank and wrongful gain to himself. The prosecution has been able to prove beyond reasonable doubts, the ingredients of Sections 420, 467, 468 and 471 IPC. 16. Furthermore, clearly the accused has tampered with the computer source document and he has also altered in the information which resided in the computer resource and by doing so he committed the offences under Sections 65 and 66 of the Information & Technology Act, 2000. At the same time, it is pertinent to mention that although accused was having secured assess to electrical record of the bank and he forged the entries and cheated to cause wrongful gain to himself but there is no such breach of confidentiality by disclosing the information to any other person and as such he is acquitted of offence under Section 72 of the Information & Technology Act, 2000." The learned Trial Court was wholly justified in convicting the accused-petitioner and the learned Appellate court, as can be clearly seen, CRR No.66 of 2013 (O&M) 9 had not committed
- 19. any error in upholding the conviction of the accused petitioner. Learned counsel for the petitioner failed to point out any misreading or non-reading of any evidence and could not point out any infirmity in the judgments of the Courts below. The findings of guilt, reached against the accused-petitioner does not, thus, suffer from any infirmity, legal or factual and does not therefore, warrant interference by this Court in exercise of this Court's revisional jurisdiction. In view of the above, there is no merit in the contentions raised by the learned counsel for the petitioner.Dismissed in limine. 2. IN THE HIGH COURT OF MADRAS Fatima Riswana v. State Rep. by ACP., Chennai & Ors AIR 2005 712. The appellant is a prosecution witness in S.C. No. 9 of 2004 wherein respondents 2 to 6 are the accused facing trail for offences punishable under Section 67 of Information Technology Act, 2000 r/w Section 6 of Indecent Representation of Women (prohibition) Act, 1986, Under Section 5 & 6 of Immoral Traffic (Prevention) Act, 1956, Under Section 27 of Arms Act, 1959 And Sections 120(B), 506(ii), 366, 306 & 376 I.P.C. The said trial relates to exploitation of certain men and women by one of the accused Dr. L. Prakash for the purpose of making pornographic photos and videos in various acts of sexual intercourse and thereafter selling them to foreign websites. The said session's trail came to be allotted to the foreign websites. The said Session's trail came to be allotted to the V Fast Track Court, Chennai which is presided over by a lay Judge. When the said trail before the V Fast Track Court was pending certain criminal revision petitions came to be filed by the accused against the orders made by the said court rejecting their applications for supply of copies of 74 Compact Discs (CDs) containing pornographic material on which the prosecution was relying. The said revision petitions were rejected by the Madras High Court by its order dated 13th February, 2004 holding that giving all the copies of the concerned CDs might give room for copying such illegal material and illegal circulation of the same, however the court pemitted the accused persons to peruse the CDs of their choice in the Chamber of the Judge in the presence of the accused, their advocates, the expert, the public prosecutor and the Investigating Office and also observed that the case be transferred to another court with competent jurisdiction presided by a male officer at the option of the sessions judge and taking the same the accused filed a revision petition for transferred to Fast track 4 court presided by the male officer and the Appellant alleged that she would be embarrassed if the trail is conducted by the male presiding officer and that the lady sessions judge didn't object or the trail of the case and the Appellant alleged that she would be embarrassed if the trail is conducted by the male presiding officer and that the Lady sessions judge didn't object to the trail of the case in the fast track 5 and the high court has erred in transferring the case and the Appellant was not given any opportunity of being heard before the alleged transfer. The learned counsel for the respondents contended that the Appellant learned though arrayed as witness is for all purpose an accused herself and law officer appearing in the case had expressed their embarrassment in conducting the trial before a lady Presiding Officer and even though the Presiding Officer did not expressly record her embarrassment, it was apparent that she too wanted the case to be transferred to another court, therefore, this Court should not interfere with the order of transfer. It was held that this appeal has to be allowed in the sessions case No. 9 of 2004 now transferred to the IV Fast Track Court Chennai be Transferred back to the V Fast Track Court, Chennai. 3. IN THE HIGH COURT OF DELHI Avnish Bajaj v State (N.C.T.) of Delhi (2005) 3 Comp LJ 364 (Del) The accused is the CEO of Baaze.com, which Company facilitates the sale of any property, for which it receives commission and also generates revenue from advertisement carried on its web
- 20. page. In the present case, Counsel for the State has argued that the accused was remiss, at the pain of culpability, in not stopping payment through Banking channels after learning of the illegal nature of the transaction. It has been strenuously contended that if bail is not granted it will adversely impact e-commerce, for which India may be the eventual loser. These are not considerations which India may be the eventual loser. These are not considerations which would prevail or tamper the Courts decision whether to grant or reject bail. Mr. Jaitely, counsel for the petitioner has underscored that in Section 67 of the Information Technology Act, 2000 an offence is committed by a person who publishes or transmits any material which is lascivious or appeals to the prurient or transmits any material which is lascivious or appeals to the prurient interest. Sections 292 and 294 of the Indian Penal Code have also been mentioned which contemplate the selling, letting on hire, distribution pr public exhibition of the absence matter. He has emphasized that the provision does not bring within its sweep the causing of the transmission in contradistinction to the publication of obscene material. Prima facie it has not been established from the evidence that has been gathered till date that any publication took place by the accused, directly or indirectly. The actual obscene recording/clip cannot be viewed on the portal of Bazze.com. It was held that the accused has actively participated in the investigations, and nothing was even argued before it in contrary by Counsel for the State. The nature of the alleged offence is such that the evidence has already crystallised and may even be tamper proof. Even though the accused is no longer an Indian National, he is of Indian origin with family roots in our country. It cannot possibly be argued that a foreign national is disentitled to the grant of bail The accused is enlarged on bail subject to furnishing two sureties in the sum of Rs. 1,00,000/- each to the satisfaction of the concerned Court/ Metropolitan Magistrate/Duty Magistrate. The Accused shall also not leave the territories of India without the leave of the Court and far for this purpose shall surrender his passport to the Magistrate. It is implicit in the grant of bail that he shall participate and assist in the investigation. The Bail Application stands disposed of. 3A. IN THE HIGH COURT OF DELHI Over three and a half years ago, an internet website carried a listing which offered for sale a video clip, shot on a mobile phone, of two children of a school in Delhi indulging in an explicitly sexual act. The petitioner, who was the Managing Director (MD) of the company that owned the website at the relevant point in time, asks this Court to annul his criminal prosecution for the offences of making available for sale and causing to be published an obscene product within the meaning of Section 292 Indian Penal Code (IPC) and Section 67 of the Information Technology Act 2000 (IT Act). This petition under Section 482 of the Code of Criminal Procedure 1973 ('CrPC') also raise questions concerning the criminal liability of directors for the offences attributable to a company, both under the IPC as well as the IT Act, particularly when such company is not arraigned as an accused. The website baaze.com provided an online platform or market where a seller and a buyer could interact. The Court held that as the IPC is concerned there is no automatic criminal liability of a director where the company is arraigned as an accused. The absence of such a provision in the IPC could be viewed as a lacuna but is not to be lightly presumed as there have been numerous statutes enacted by Parliament thereafter which have incorporated such provisions. For instances, Section 85 It Act is similarly worded as Section 141 NI Act and incorporates a deemed criminal liability of the director. The IT Act amends certain provisions of the IPC as well. But Parliament has chosen not to make any amendment to incorporate such a provision in the IPC. The Court has therefore to proceed with the law as it exists, particularly since it is a penal statute which admits of strict construction. The Court held that the case against the petitioner of the offence under Sections 292 and 294 IPC is quashed and the read with Section 85 IT Act will continue.
- 21. 4. IN THE HIGH COURT OF MADRAS S. Sekar v The Principal General Manager (Telecom) (B.S.N.L.) The petitioner is an employee of the second respondent, B.S.N.L, working as a Telecom Technical Assistant (Switch). It so happened that while he was working in SIPCOT MBM Main Exchange, Keeranur, the B.S.N.L. higher officials suspected him and others for having committed offences in manipulating the computer system and thereby causing loss to B.S.N.L. The FIR in Crime No. 1 of 2004 was came to be registered on 06.01.2004 by the Police, Pudukottai, for the offences under Section 406, 420 and 468 I.P.C. and 43(g) of the Information Technology Act, 2000. The main thrust of the grievance of the petitioner in this case is that when there is a special enactment namely, the Information Technology Act, 2000, which is in operation relating to the alleged misconduct attributed as against the petitioner, there is no question of invoking the penal sections under the Indian Penal Code, It is also his specific plausible argument that section 43(g) of the Information Technology Act, 2000, has been invoked without any basis. The Second respondent filed the computer which was adopted by the first respondent filed the computer which was adopted by the first respondent also, denying and refuting the allegations and the averments highlights that the FIR registered was proper and the Police is investigating into the matter properly. The point for consideration is as to whether the FIR referred to supra, has to be declared null and void as prayed by the Writ petitioner? It was held that the Police to investigate thoroughly into the matter and add or delete the penal Sections under the Information Technology Act, 2000, as well as IPC and ultimately, it is for the criminal court which would be seized of the matter to decide on that. The Section 43(g) of the Information Technology Act, 2000, invoked by the police and specified in the FIR is declared void. Accordingly, the Writ petition is ordered. No costs, connected M.P. is closed. 5. IN THE HIGH COURT OF ANDHRA PRADESH Syed Asifuddin and Ors. v The State of Andhra Pradesh And Anr. 2005 Cri LJ 4314 These two petitions are filed by different persons under section 482 of Code of Criminal Procedure, 1973 (Cr. P.C.) seeking similar relief. Both the matters were admitted on the same day and since then both the matters are being disposed of as such, this common order covers both the matters. The petitioners in both the matters seek the relief of quashing FIR No. 20 of 2003 of Criminal Investigation Department (CID) Police, Hyderabad, registered under section 409, 420 and 120B of Indian Penal Code, 1860 (for short, IPC), Section 65 of the Information Technology Act, 2000 (for short IT Act) and section 63 of the copyright Act, 1957 (for short, Copyright Act). While admitting the petition, this Court passed orders in criminal miscellaneous petition No. 3951 of 2003 staying all further proceeding including investigation of the crime pending disposal of the main petition. The Public Prosecutor filed criminal miscellaneous petition No. 232 of 2005 for vacating the said order. The matter were "Finally hared at that stage itself and are being, disposed of finally. The main allegation against the petitioners is that the MIN of Reliance phone is irreversibly integrated with ESN and the petitioners hacked ESN so as to wean away RIM customer to TATA Indicom service. The question is whether the manipulation of this electronic 32-bit number (ESN) programmed into Samsung N191 and LG-2030 cell phone instrument exclusively franchised to second respondent amounts to altering source code used by these computer handsets i.e., cell phone instruments. In the background facts, a question would also arise whether such alteration amounts to hacking with computer system? If the query answered in the affirmative, it is always open to the police to alter the FIR or it is always open to the criminal Court to frame a charge specifically with regard to hacking with computer system, which is an offence under Section 66 of the It Act. At this stage, we may read Sections 65 and 66 of the IT Act.
- 22. Crime No. 20 of 2003 in so far as it is under section 409, 420 and 120B of Indian Penal Code, 1860 is quashed and insofar as the crimes under Section 63 of the Copyright Act, 1957, the criminal petitions are dismissed. The CID Police, which registered Crime No. 20 of 2003, is directed to complete investigation and file a final report before the Metropolitan Magistrate competent to take cognizance of the case within a period of Three months from the date of receipt of this order. The criminal petitions are accordingly dismissed. 6. IN THE HIGH COURT OF MADRAS D'zine Garage Pvt. Ltd. rep. by its Director Mr. Hari Sethuraman v D'zine Café FZE & D'zine Café FZE v D'zine Garage Pvt. Ltd. rep. by its Director Mr. Hari Sethuraman Plaintiff registered proprietor of the service mark 'D'zine filed suit for permanent injection against Applicant-Defendant who was using the mark 'D'zine' café as a service mark and as part of their corporate name and domain name 'www.Dzinecafe.com'- Respondent/Plaintiff contended that the Applicant- Defendant has deliberately adopted a similar service mark/trade name D'zine café in a calculated attempt to cash in on the reputation and goodwill enjoyed by the Respondent/Plaintiff and to get illicit and quick gains without putting any substantial efforts – Interim injunction granted – Hence, application by Defendant to vacate interim injunction and to strike the pleadings and reject the plaint – Applicant-Defendant contended that the Respondent- Plaintiff has no office in India and hence present Court has no jurisdiction to try the matter and therefore, the plaint was liable to be rejected – Held, to justify an Order of rejection of plaint, the Defendant would be required to show a very strong case in his favour and the power would be exercised sparingly and only in exception cases, since it would interface with the right of the party to proceed with the trial to get to it legitimate and according to the substantive merit of his case – Such a case has not been made out by he Defendant – it was held that application for rejection of plaint not maintainable. Defendant sought vacation of interim injunction on the ground that the registration is for a logo only and that 'D'zine' was not a coined word, it is a corrupt from of design and is commonly used – Further contented that, D'zine' café were sufficiently different and not likely to mislead and many others are using it – Held, for granting interim injunction phonetic similarly cannot be ignored and prior user must be proved and dishonest intention must be there – In the instant case, there is phonetic similarly – Further, 'D'zine not a generic word, it cannot be said to carry distinctive reference to a particular trade, becoming publici jiris – As business of parties are almost same and the fact that one is 'Dzine' café and other is 'Dzine' garage, clientele is likely to be confused and to t are the same – prior user established by Plaintiff – No specific denial of the charge that the Defendant is taking advantages of the plaintiff mark- Usage of the same word by others and others and that is a common word is no defence in an action for interim injunction – Interim injunction granted. 7. IN THE HIGH COURT OF GUJRAT Nirav Navinbhai Shah & 4 ors. v State of Gujarat and Anr. The applicants, original accused in crime I.C.R. No. 54 of 2004 dated 26.02.2004 registered with sector 7 police station Gandhinagar for offences punishable under sections 381, 408, 415, 418, 420 read with sections 34 and 120B of the Indian Penal Code and section 66 and 72 of the Information Technology Act, 2000 (herein after referred to as 'the IT Act for short) have preferred this application under section 482 of the Code of Criminal Procedure 1973 (herein after referred to as ' the code' for short) for quashing of FIR I.C.R. No. 54 of 2004 dated 26.02.2004 registered with Sector No. 7 Police Station Gandhinagar and the resultant Criminal Case No. 54 of 2004 dated 26.02.2004 registered with sector No. 7 Police station Gandhinagar and the resultant Criminal case No.3528 of 2004
- 23. pending before the judicial Magistrate First Class Gandhinagar, mainly on the grounds that the facts and allegation leading to lodging FIR show that the real dispute was a civil dispute and as the same has been amicably settled between the parties, no useful purpose would be served in continuing the criminal proceedings, rather continuation of same would be counter productive to the interest of justice. The compliant also does not contain any essential ingredient for maintaining criminal proceeding for the alleged offences. As it’s stated in the arguments of the learned counsels that the parties have filed civil suits also in respect of the same dispute. The entire dispute between the parties is resolved by amicable settlement. The alleged hacking is perpetrated on the Complainants computer system only which said to have data pertaining to its client. The Counsels have submitted that on same of the web sites these data are already available. The dispute appears to be private in nature. The offence alleged is not strictly affecting or infringing any other individual or citizen. Thus looking to the nature of the disputes, it can well be said that continuation of the same is not in interest of justice. It was held that the FIR 54 of 2004 registered at sector 7 Police Station Gandhinagar and resultant Criminal Case No. 3528 of 2004 pending before the JMFC Gandhinagar deserve to be quashed in the interest of just and hereby they are quashed. Rule is made absolute. 8. CYBER DEFAMATION SMC Pneumatics (India) Pvt. Ltd. v. Jogesh Kwatra, Suit No. 1279/2001 Delhi HC In India's first case of cyber defamation, a Court of Delhi assumed jurisdiction over a matter where a corporate’s reputation was being defamed through emails and passed an important ex -parte injunction. In this case, the defendant Jogesh Kwatra being an employ of the plaintiff company started sending derogatory, defamatory, obscene, vulgar, filthy and abusive emails to his employers as also to different subsidiaries of the said company all over the world with the aim to defame the company and its Managing Director Mr. R K Malhotra. The plaintiff filed a suit for permanent injunction restraining the defendant from doing his illegal acts of sending derogatory emails to the plaintiff. On behalf of the plaintiffs it was contended that the emails sent by the defendant were distinctly obscene, vulgar, abusive, intimidating, humiliating and defamatory in nature. Counsel further argued that the aim of sending the said emails was to malign the high reputation of the plaintiffs all over India and the world. He further contended that the acts of the defendant in sending the emails had resulted in invasion of legal rights of the plaintiffs. Further the defendant is under a duty not to send the aforesaid emails. It is pertinent to note that after the plaintiff company discovered the said employ could be indulging in the matter of sending abusive emails, the plaintiff terminated the services of the defendant. After hearing detailed arguments of Counsel for Plaintiff, Hon'ble Judge of the Delhi High Court passed an ex-parte ad interim injunction observing that a prima facie case had been made out by the plaintiff. Consequently, the Delhi High Court restrained the defendant from sending derogatory, defamatory, obscene, vulgar, humiliating and abusive emails either to the plaintiffs or to its sister subsidiaries all over the world including their Managing Directors and their Sales and Marketing departments. Further, Hon'ble Judge also restrained the defendant from publishing, transmitting or causing to be published any information in the actual world as also in cyberspace which is derogatory or defamatory or abusive of the plaintiffs. This order of Delhi High Court assumes tremendous significance as this is for the first time that an Indian Court assumes jurisdiction in a matter concerning cyber defamation and grants an ex-parte injunction restraining the defendant from defaming the plaintiffs by sending derogatory, defamatory, abusive and obscene emails either to the plaintiffs or their subsidiaries.
- 24. 9. PHISHING Nasscom vs. Ajay Sood & Others In a landmark judgment in the case of National Association of Software and Service Companies vs Ajay Sood & Others, delivered in March, ‘05, the Delhi High Court declared `phishing’ on the internet to be an illegal act, entailing an injunction and recovery of damages. Elaborating on the concept of ‘phishing’, in order to lay down a precedent in India, the court stated that it is a form of internet fraud where a person pretends to be a legitimate association, such as a bank or an insurance company in order to extract personal data from a customer such as access codes, passwords, etc. Personal data so collected by misrepresenting the identity of the legitimate party is commonly used for the collecting party’s advantage. court also stated, by way of an example, that typical phishing scams involve persons who pretend to represent online banks and siphon cash from e-banking accounts after conning consumers into handing over confidential banking details. The Delhi HC stated that even though there is no specific legislation in India to penalise phishing, it held phishing to be an illegal act by defining it under Indian law as “a misrepresentation made in the course of trade leading to confusion as to the source and origin of the e-mail causing immense harm not only to the consumer but even to the person whose name, identity or password is misused". The court held the act of phishing as passing off and tarnishing the plaintiff’s image. The plaintiff in this case was the National Association of Software and Service Companies (Nasscom), India’s premier software association. The defendants were operating a placement agency involved in head-hunting and recruitment. In order to obtain personal data, which they could use for purposes of head-hunting, the defendants composed and sent e-mails to third parties in the name of Nasscom. The high court recognised the trademark rights of the plaintiff and passed an ex-parte ad-interim injunction restraining the defendants from using the trade name or any other name deceptively similar to Nasscom. The court further restrained the defendants from holding themselves out as being associates or a part of Nasscom. The court appointed a commission to conduct a search at the defendants’ premises. Two hard disks of the computers from which the fraudulent e-mails were sent by the defendants to various parties were taken into custody by the local commissioner appointed by the court. The offending e-mails were then downloaded from the hard disks and presented as evidence in court. During the progress of the case, it became clear that the defendants in whose names the offending e-mails were sent were fictitious identities created by an employee on defendants’ instructions, to avoid recognition and legal action. On discovery of this fraudulent act, the fictitious names were deleted from the array of parties as defendants in the case. Subsequently, the defendants admitted their illegal acts and the parties settled the matter through the recording of a compromise in the suit proceedings. According to the terms of compromise, the defendants agreed to pay a sum of Rs1.6 million to the plaintiff as damages for violation of the plaintiff’s trademark rights. The court also ordered the hard disks seized from the defendants’ premises to be handed over to the plaintiff who would be the owner of the hard disks. This case achieves clear milestones: It brings the act of “phishing” into the ambit of Indian laws even in the absence of specific legislation; It clears the misconception that there is no “damages culture” in India for violation of IP rights; This case reaffirms IP owners’ faith in the Indian judicial
- 25. system’s ability and willingness to protect intangible property rights and send a strong message to IP owners that they can do business in India without sacrificing their IP rights. 10. State of Tamil Nadu v/s. Suhas Kutti, 2004 Assistant Commissioner of Police, Cyber Crime Cell, C.C.B.Egmore, Chennai.8 has filed Final Report against the accused, that on 7.2.04, evening at Cyber Café Hello World Centre, Sion, Mumbai having an I.P.61.11.10.99, the accused with intention of harming the reputation of the Complainant Ms. R, created user id in the name of her and composed an obscene message intending that such document shall be used for posting in different obscene Yahoo Group, with the intention to make others to believe that the document was made by her, so that the persons seeing the obscene message would send offending calls to her,in harming her reputation and by insulting her modesty by the words exhibited in the email and in the course of same transaction, on 7.2.04, evening at Cyber Café Hello World Centre, Sion, Mumbai, having an IP 61.11.10.99 the Accused posted obscene message which are lascivious and also have the effect to corrupt persons who are likely to read and see such obscene messages and caused to the published in different obscene Yahoo goups and in the course of same transaction, that on 9.2.04, morning, at Cyber Café Heighten Advertising, Mahim, Mumbai, having an IP 202.88.165.53 the accused with intention of harming the reputation of the complainant Ms. R entered user id. which was created by him in the name of the complainant and composed an obscene message intending that such document shall be used for posting in different obscene Yahoo groups, with the intention to make others to believe that the document was made by her, so that the persons seeing the obscene message would send offending calls to her, in harming her reputation and by insulting her modesty by the words exhibited in the email and that in the course of same transaction, that on 9.2.04, morning at cyber café Heighten Advertising, Mahim, Mumbai, having an IP 202.88.165.53, the accused posted obscene messages which are lascivious and also have the effect to corrupt person who are likely to read and see such obscene messages and caused to be published in different obscene Yahoo goups and thereby the accused have committed offences u/s 469 IPC, 67 I.T Act. 469 &509 IPC, and 67 of I.T. Act. P.W. 1 is the only daughter of P.W.2 and P.W.3.P.W.2 is the father, P.W.3 is the mother. Presently, P.W.1 is working as a senior Executive (H.R.) in a multinational Company at Chennai. She studied her MBA Course in Mumbai in the year 1997, the accused studied with P.W.1 and she was his classmate is Mumbai. Accused belongs to Mumbai. On 9.2.04, She opened her Rediff e-mail and noticed the receipt of two obscene messages which were posted on 7.2.04 and 9.2.04. She took computer output of the obscene message posted on 7.2.04, Ex P.1 is the obscene message. The obscene message carried her Office phone numbers and her e-mail I.D. The house Phone number was wrongly given. The said obscene messages have been sent through Yahoo website to 5 sex groups. The computer printout obscene message posted in @ Radha lovers group is EX.P.2. On seeing the said messages, several persons sent the responsive message and many persons tried to contact her over phone. Ex P3 series is the responsive messages. Several Phone calls came to her office. P.W.1 informed the said matter to her parents. The messages were likely to harm the reputation and morale of P.W.1. P.W. 1 had married Jaichand Prajapathi of Uttar Pradesh in the year 2001. The family life was not happy and she obtained divorce through court in the year 2003. The Accused was citied as witness in the divorce petition. P.W.1 recollected one incident and suspected in the involvement of the Accused. During college days in the year 1997, the accused used to travel with P.W.1 in train at Mumbai. On one such occasion, Accused pointed out an obscene scribbling with phone number in the train and told P.W.1 that on seeing the phone number, many persons would try to contact the phone number and this is the best way to spoil the reputation of a woman. The Accused even
- 26. expressed his desire to marry P.W.1, after the engagement of P.W.1 with Jaichand Prajapati was over. P.W.1 turned down his proposal. In the year 2003, the Accused stayed in the house of the P.W.1 for about 10 days stating that he has to attend an interview at Banglalore. At that time also, Accused offered to marry P.W.1 for which P.W.1 and her parents refused the alliance. Thereafter, P.W.1 after his return to Mumbai was in the habit of making Phone calls, sending S.M.S. Messages and sending E-mail to P.W.1 frequently. Hence P.W.1 blocked the e-mail I.D. of the Accused. Ex.P5 is the Computer output for blocking the e-mail I.D. of the Accused. On seeing the obscene message, P.W.1 discussed the matter with P.W.2 and P.W.3 and sought the help of the Accused over phone. P.W.1 and her parents issued a warning message in the name of PW 2 and PW 3 by creating an email ID viz, parant2003@yahoo.co.in and transmitted same to the yahoo groups. She sent warning messages to the persons, who sent responsive message in ExP.6 series. A copy of warning message was also sent to the Accused. P.W.1 lodged a complaint on 14/2/2004 along with Ex.P1 at Cyber Crime Police. The complaint is Ex. P.4 P.W.12 who received the complaint directed P.W.4 to obtain header details and other particulars to find out the origination of the messages. P.W.4 went to Cyber Café at Kennath Lane, Egmore along with P.W. 1 she down loaded the message took print out by using the e-mail I.D. Parant2003@Yahoo.Co.in Ex.P.9-Ex.P.12. She extracted and stored the messages in Mo.2 floppies. Thereafter P.W.12 gave a requisition to the Hathway Cable and Data Com. Pvt. Ltd; under Ex.P.13, for which it gave a reply in Ex. P.14. P.W.12 also gave a requisition to Dishnet D.S.L. in Ex.P.13 and the reply given by Dishnet D.S.L is Ex.P.15. P.W.5 speaks about Ex.P.13 and Ex.P.14. P.W.6 speaks about Ex.P.15.P.W.12 also examined P.W.11 and obtained particulars in Ex. P.29 series and confirmed that the messages were originated from Mumbai. P.W.12- Investigation Officer registered F.I.R. Ex.P.34 on 20.2.04. Thereafter, P.W.12 proceeded to Mumbai on 24.2.04, and arrested the Accused at Mumbai on 25.2.04. He seized Mo.1 Cell Phone from the Accused under Mahazar Ex.P.8 P.W.8 and P.W.9 who are running browsing Centre at Mumbai, identified the Accused in the presence of P.W.12. He seized Ex.P.23, 24 registers from them. P.W.8 speaks about the Accused and the seizure of Ex.P.22 and the remarks made by P.W.12 in Ex.P.23, P.W. 9 speaks about the Accused that he came to the browsing centre and signed in the Register Ex.P24 as R. Ex.P.25 is the word written by the Accused. P. W. 12, brought the Accused to Chennai on 28.2.04, after producing the Accused before a Mumbai Court. The Accused gave a confession statement in the presence of P.W. 10 and he gave the password “an rose”. The said word is Ex.P.27. The particulars stored in the SIM Card were taken print out in Ex.P. 28 series through S.M.S. Reader. P.W.12 went to the office of P.W.7 and took computer print out by using the password “an rose”. He issued the certificate in Ex.P.21. The computer print outs are Ex. P 16 -P.20. P.W.12 completed investigation and laid charge sheet against the Accused of offences u/s 67 of I T Act and u/s 469,509 of IPC. Final Order …this court is not inclined to accept the theory projected by the Accused that the obscene messages would have been created by P.W.1, P.W.2 and P.W.3 or by Jaichand Prajapathi. It is clear that the Accused himself has composed and posted the obscene messages from the browsing centre of P.W.8 and P.W.9. This Court holds that the prosecution has proved its charges against the accused beyond all reasonable doubt and hence the Accused is liable to be punished. The Accused was heard regarding the question of sentence u/s 248 (2) Cr.P.C. The Accused pleaded for admonition. The Accused is not a lay man. He is educated and studied upto M.B.A. P.W.1 is holding a responsible post in a multinational Company at Chennai. The Accused has chosen to post the obscene message for the simple reason that she refused to marry him. He did not
- 27. behave like an educated man. Only a family woman can realise the mental sufferings and pain if unknown persons contacted her through phone and e-mail and invited her to bed. The mental sufferings and humiliation undergone by the P.W.1 cannot be compensated in terms of money or by solacial words. It cannot be stated that the Accused had acted in a heat of passion. Two days repeatedly he had sent the obscene message—Computer system and browsing centre are meant for learning things and updating knowledge in various fields. The Accused has misused the same to take revenge on a sophisticated lady. Therefore, the Accused does not deserve leniency and is liable to be punished. In the result, the Accused is found guilty of offences u/s 469,509 IPC, and u/s 67 of I.T. Act. and the Accused is convicted and is sentenced to undergo Rigorous imprisonment for 2 years u/s 469 IPC, and to pay a fine Rs.500/- i/d, to undergo simple imprisonment for 1 month and for the offence u/s 509 IPC, sentenced to undergo 1 year simple Imprisonment and to pay a fine of Rs.500/- i/d to undergo simple imprisonment for 1 month and for the offence u/s 67 of Information Technology Act 2000 to undergo Rigorous Imprisonment for 2 years and to pay a fine of Rs.4,000/- i/d to undergo S.I. for 6 months. All sentences to run concurrently. The period undergone by the Accused will be set off u/s 428 Cr.P.C. 11. AP High Court dismisses Google's Petition contending being intermediary it cannot be held liable for defamation THE HONOURABLE SRI JUSTICE SAMUDRALA GOVINDARAJULU, AP High Court Crl.P.No.7207 OF 2009 19-04-2011 Google India Pvt. Ltd., M/s.Visaka Industries Limited and another ORDER: 1.The petitioner/A-2 is accused of offences punishable under Sections 120-B, 500, 501/34 I.P.C in C.C. No.679 of 2009 on the file of XI Additional Chief Metropolitan Magistrate, Secunderabad along with another. The petitioner/A-2 is Google India Private Limited represented by its Managing Director (Sales and Operations). The 1st respondent/complainant is Visaka Industries Limited, Secunderabad represented by its authorised signatory who is its Deputy Manager- Legal. The complainant is engaged in business of manufacturing and selling of Asbestos cement sheets and allied products. It is alleged that A-1 viz., Gopala Krishna is a Co-ordinator "Ban Asbestos India" a group which is hosted by A-2 and publishes regular articles in the said group and that on 21.11.2008 an article was published in the said group and it was captioned as "poisoning the system; Hindustan Times" aiming at a single manufacturer of Asbestos cement products viz., the complainant and names of renowned politicians of the country G.Venkata Swamy and Sonia Gandhi who have nothing to do with the ownership or management of the complainant-company were named in that article. It is further alleged that on 31.07.2008 another article captioned as "Visaka Asbestos Industries making gains" and that both the above articles contained defamatory statements against the complainant and they are available in Cyber space in the form of articles for world wide audience. In the complaint, details of defamatory remarks made in several other articles published by A-1 in A-2 group are given in detail, which details may not be necessary for the purpose of disposal of this criminal petition. 2) It is contended by the senior counsel appearing for the petitioner/A-2 that actions of intermediaries such as Google Inc., which is a service provider providing platform for end users to upload content, does not amount to publication in law and consequently the question of holding such intermediaries liable for defamation does not arise. Senior Counsel appearing for
