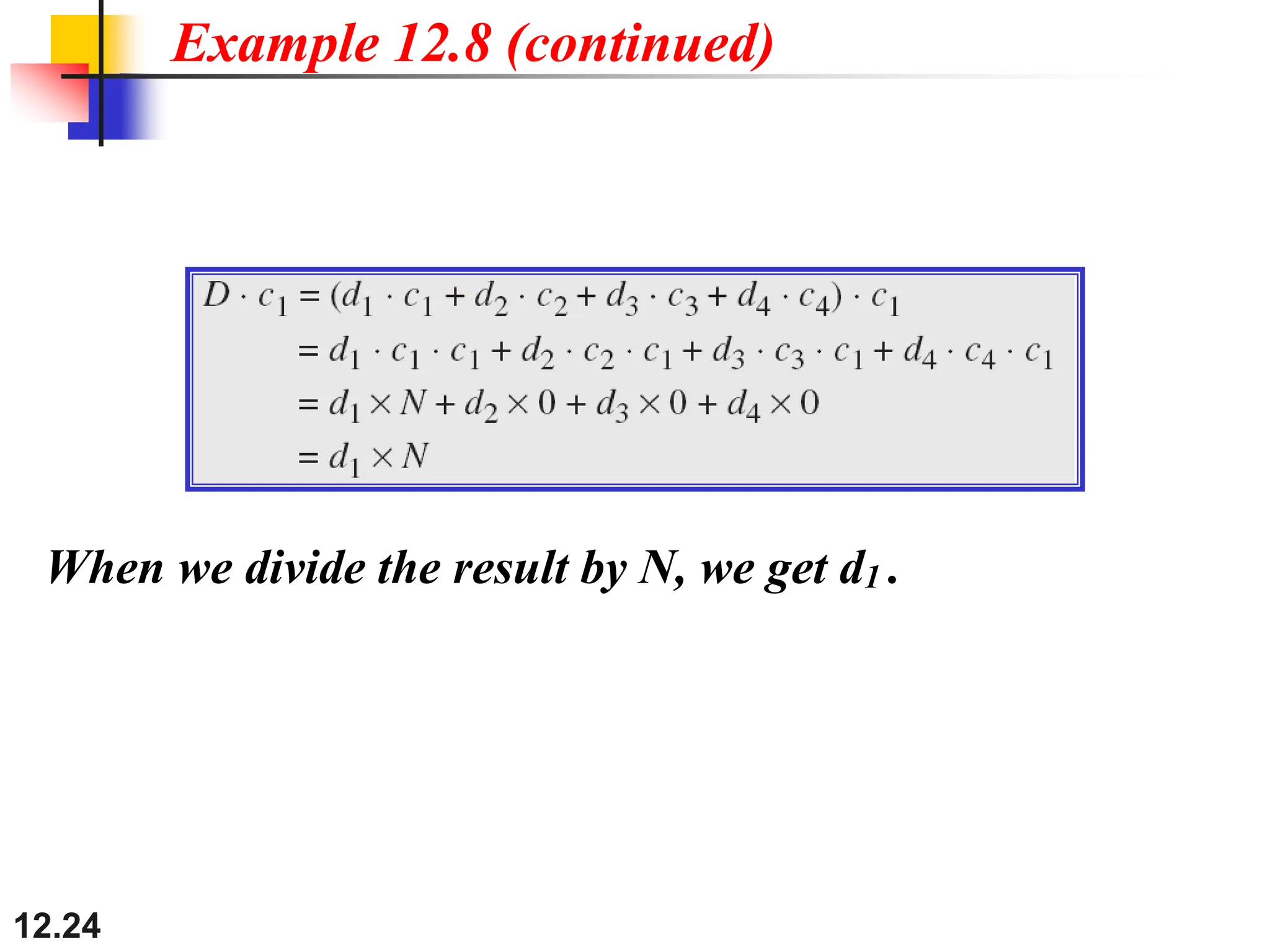
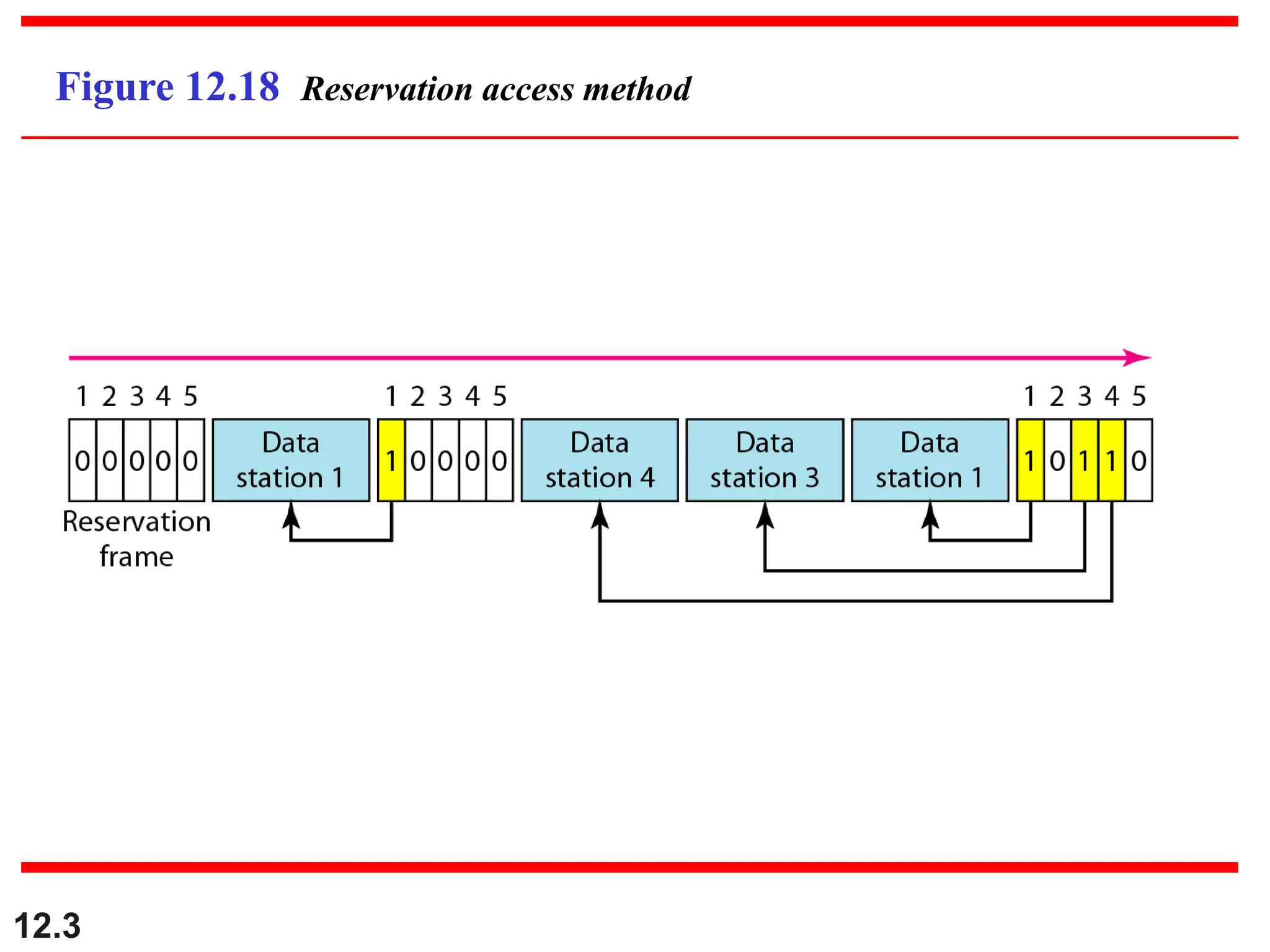
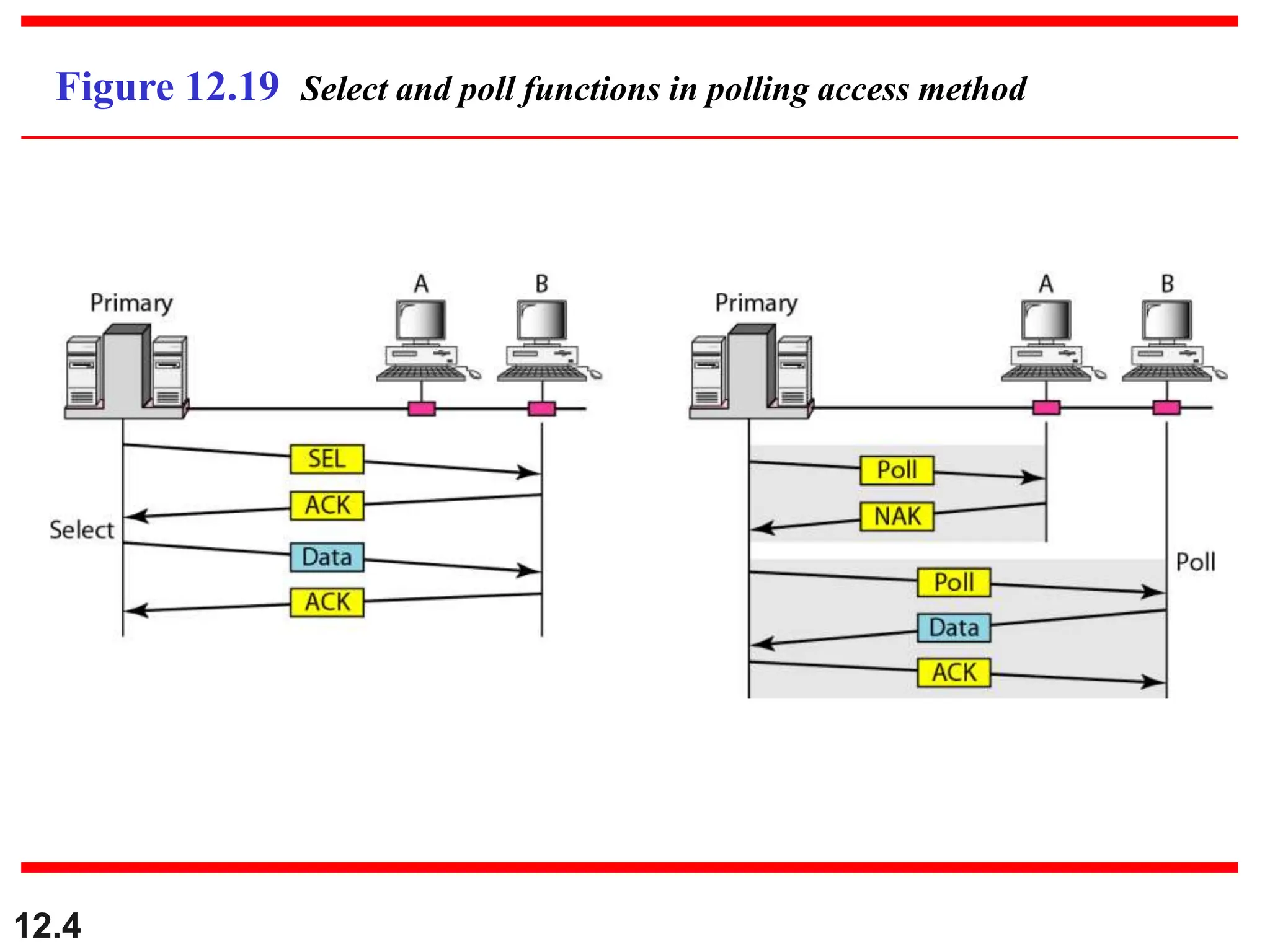
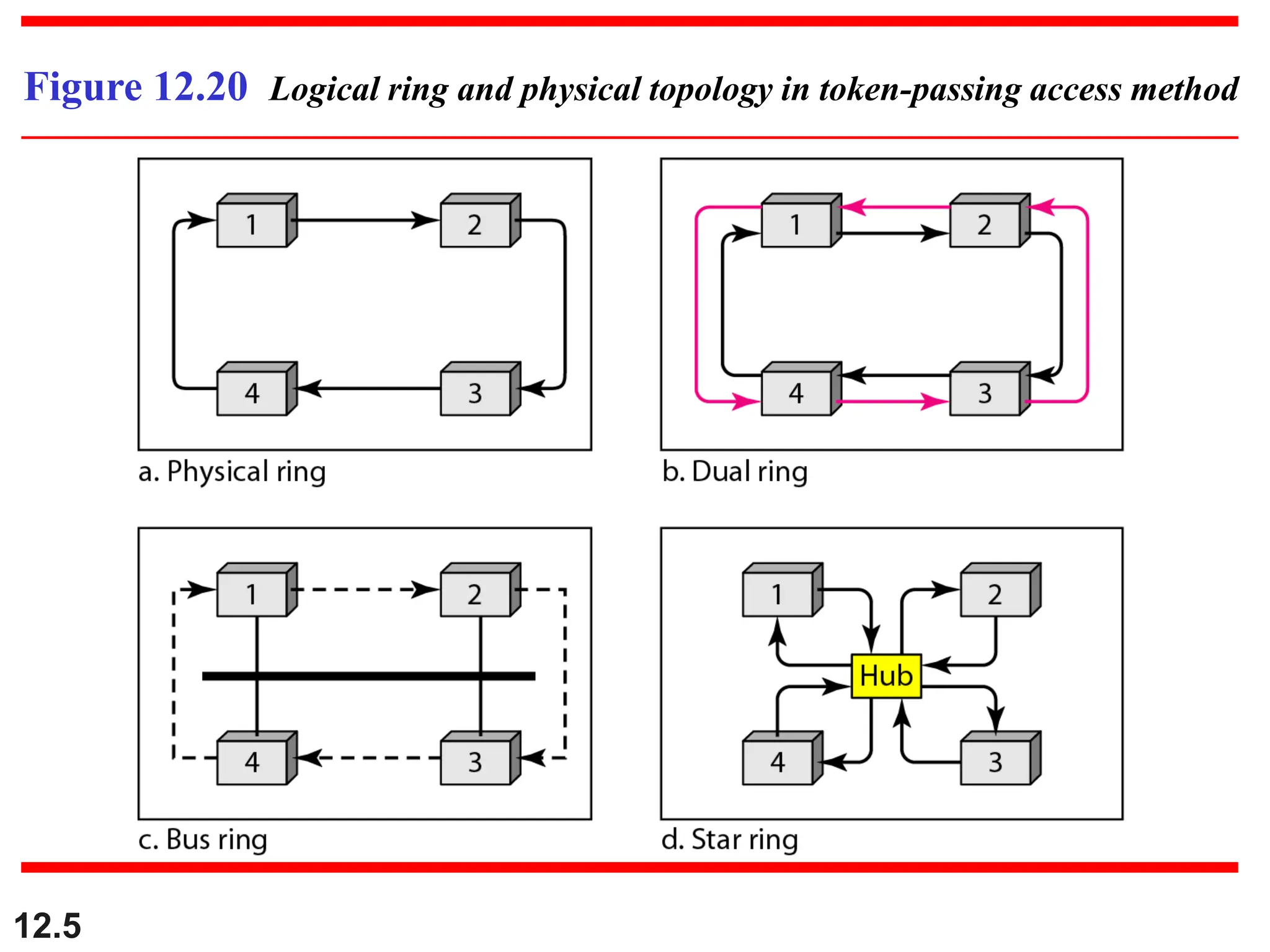
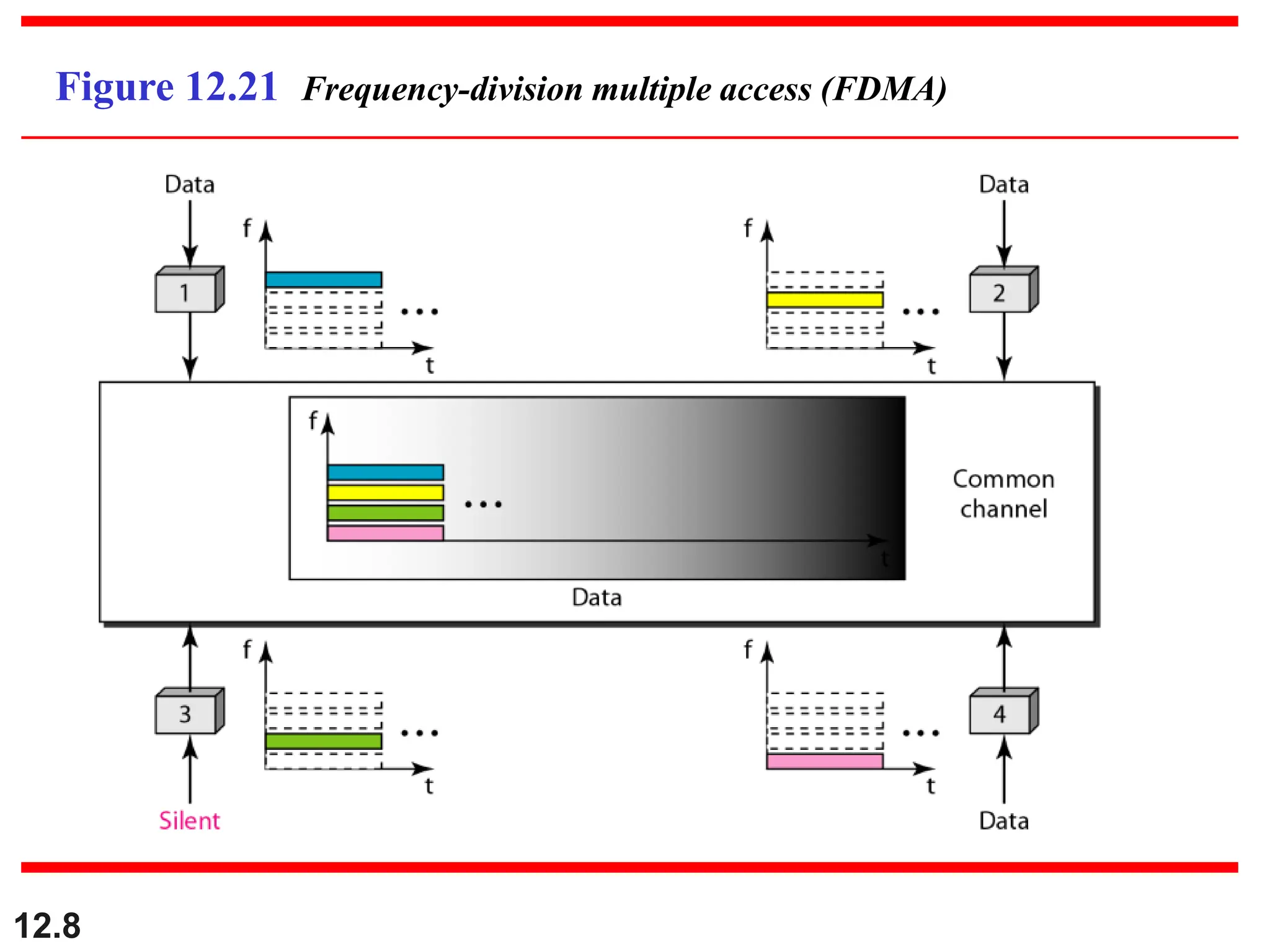
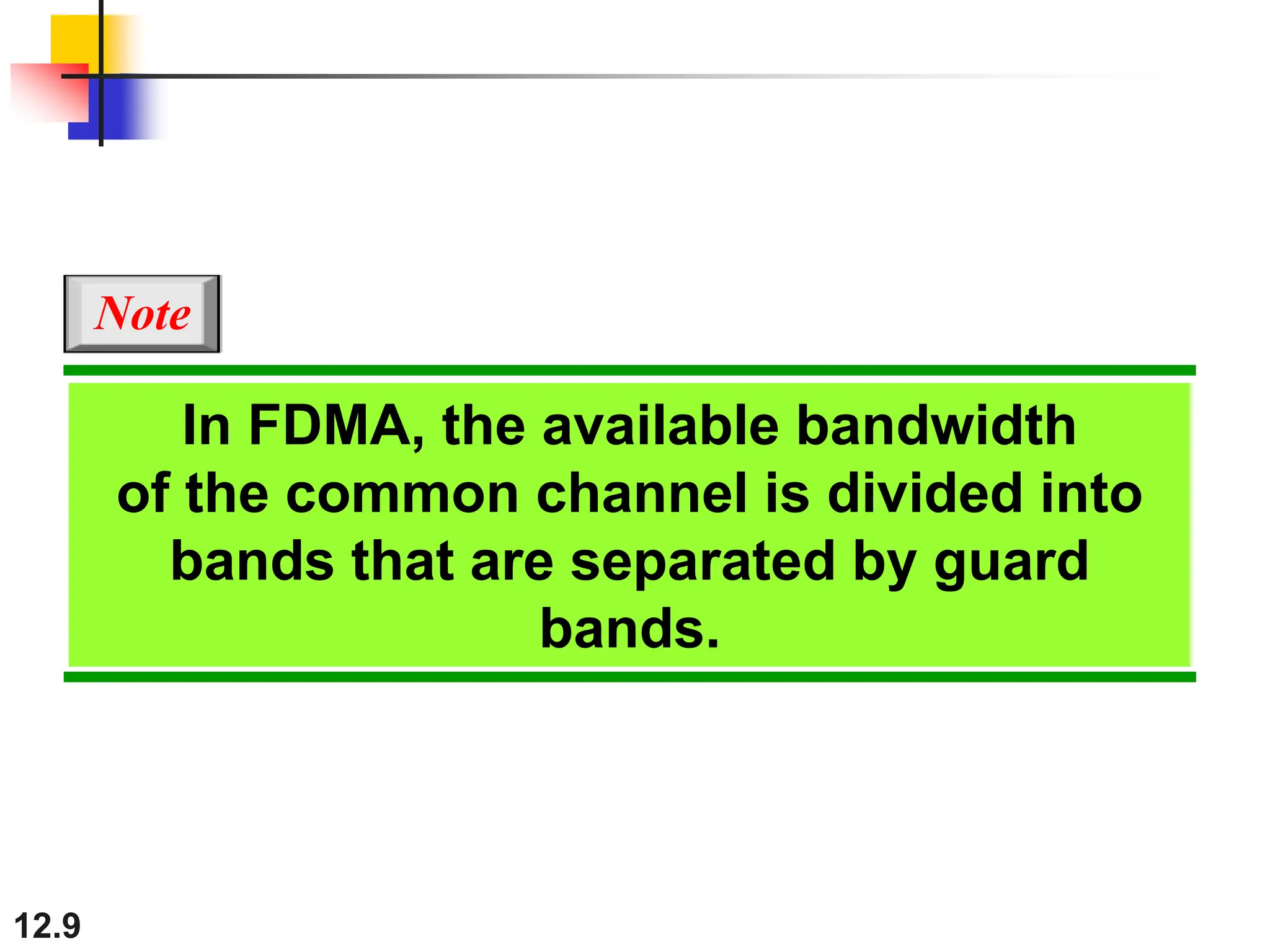
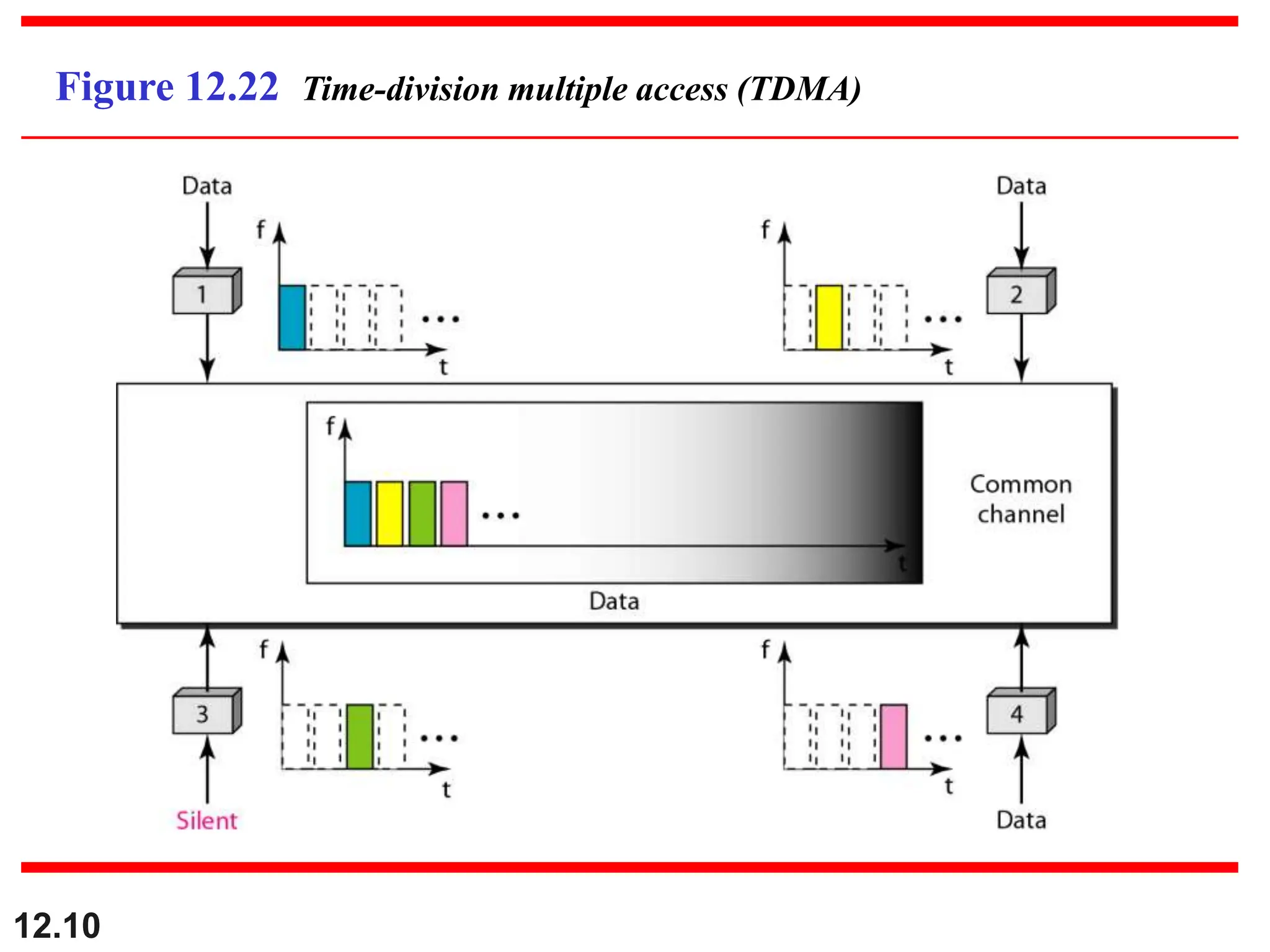
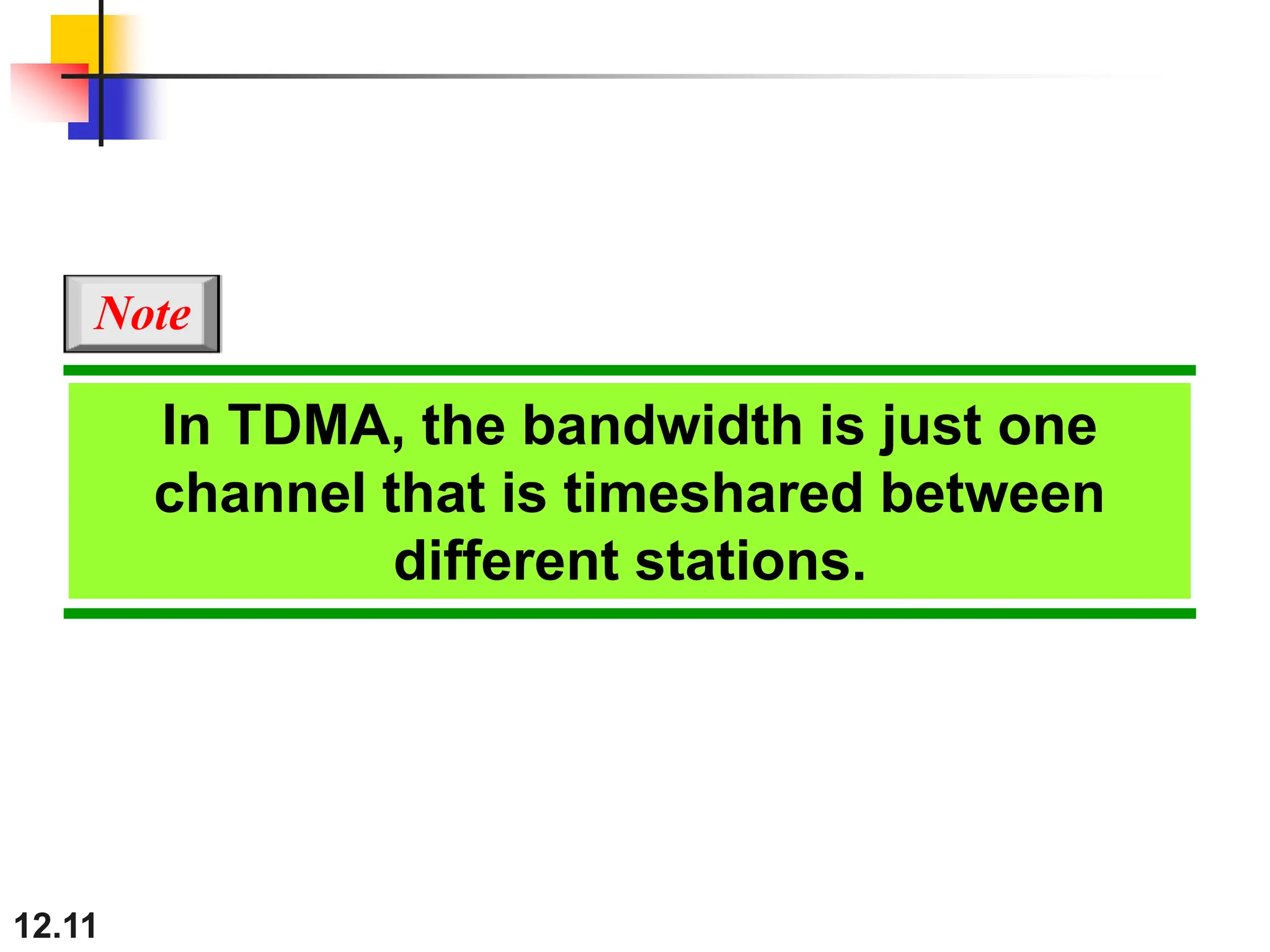
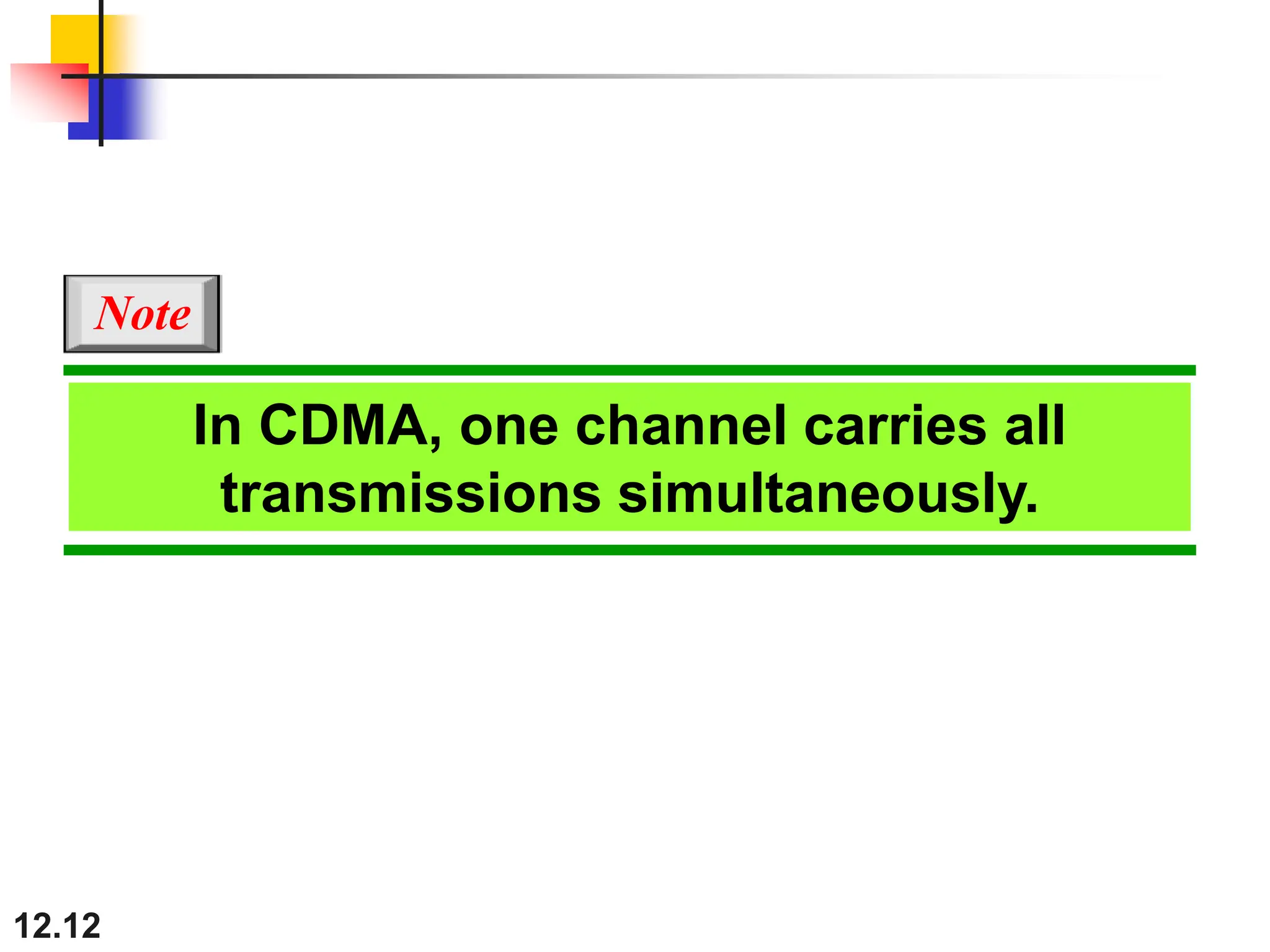
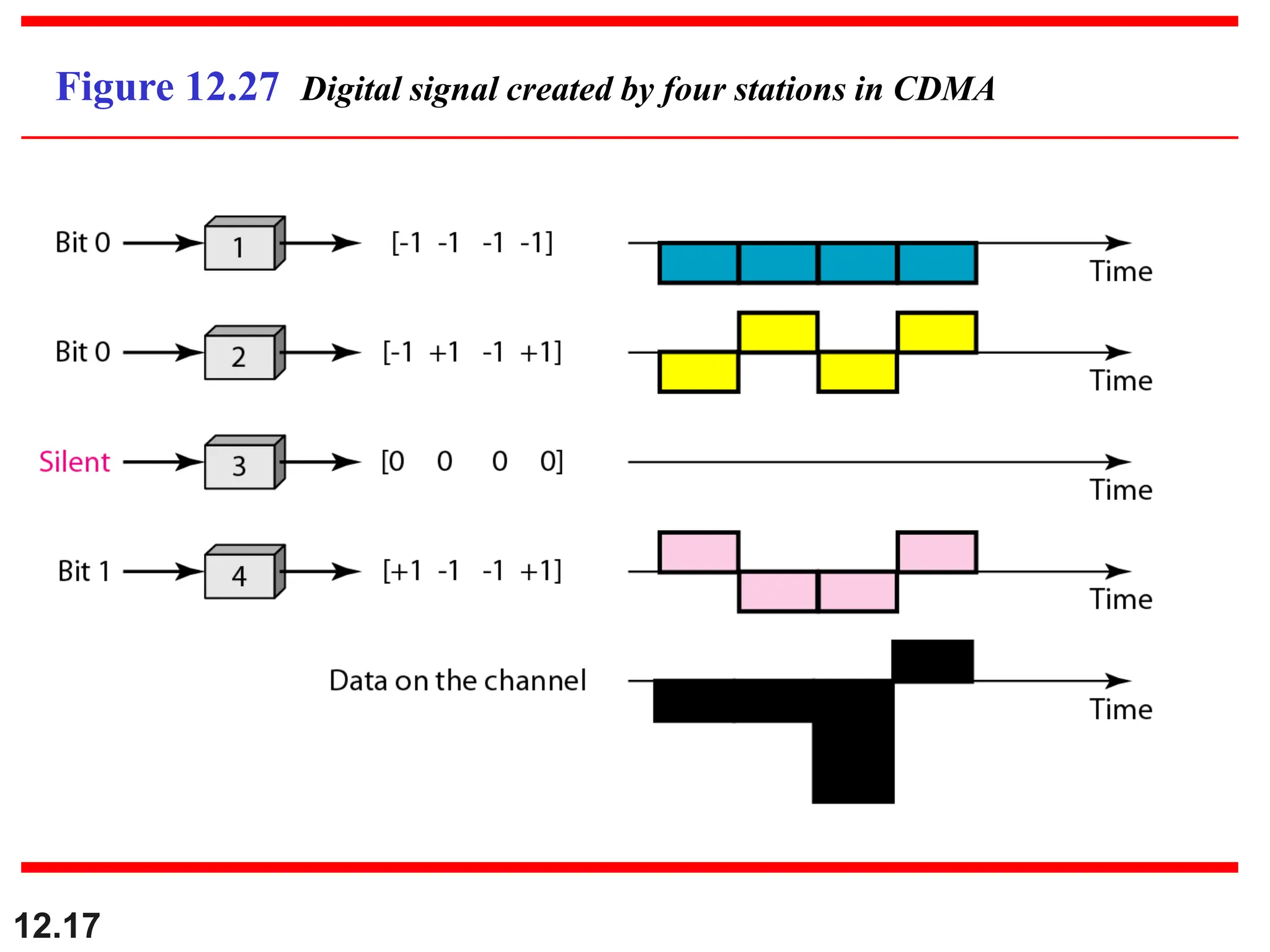
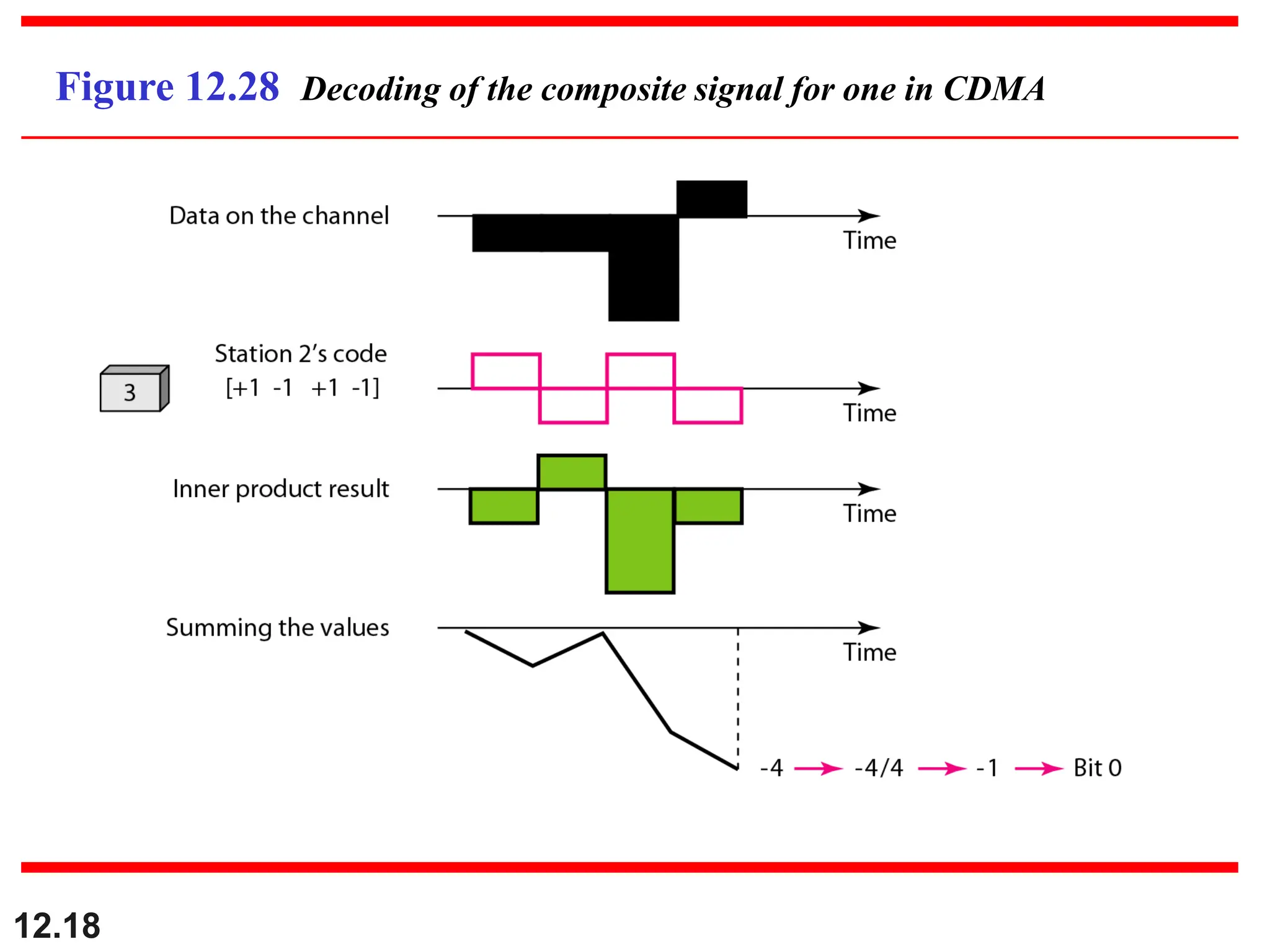
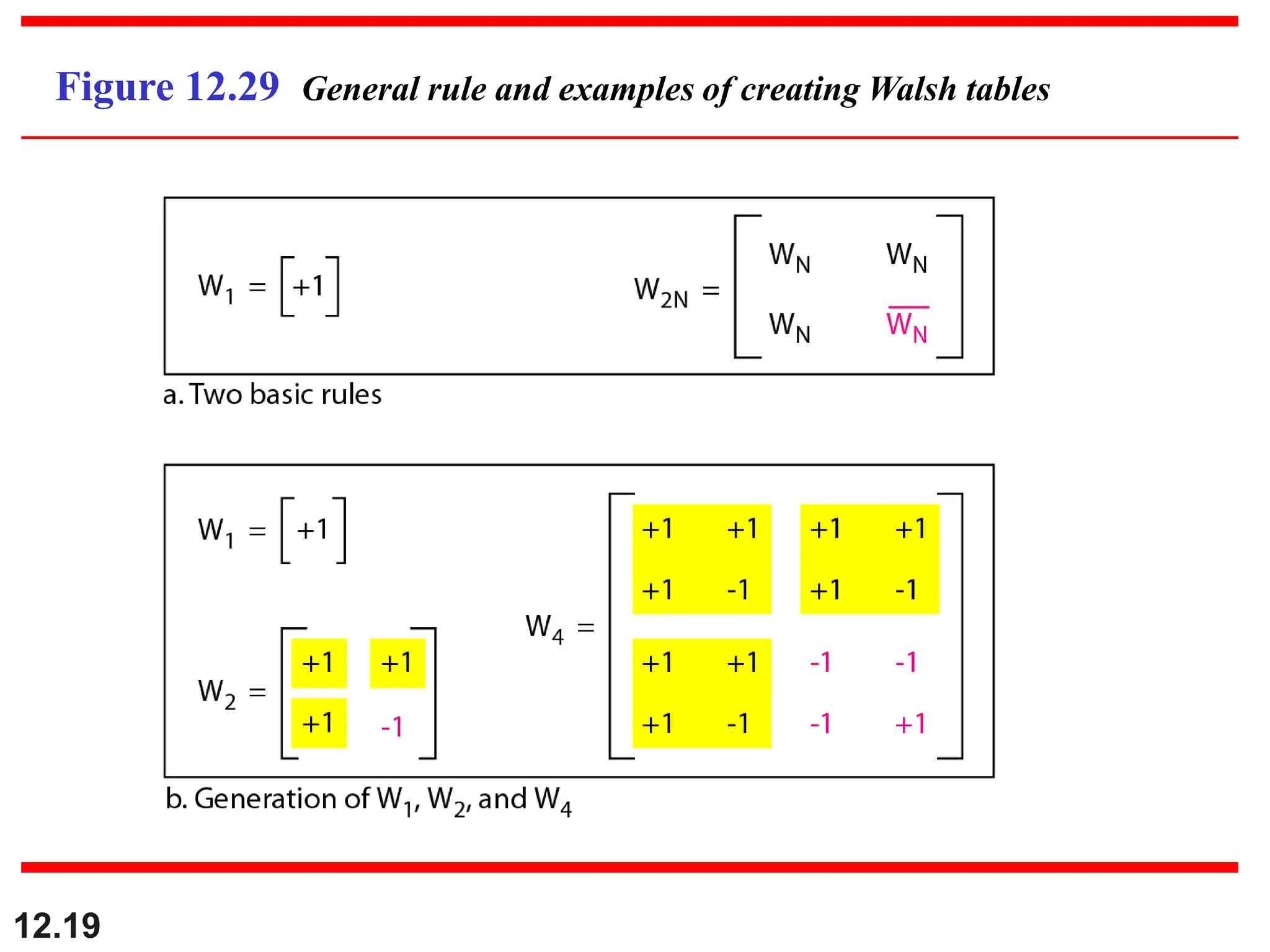
The document discusses controlled access methods for network communication, including reservation polling and token passing, where stations must be authorized to send data. Additionally, it introduces channelization techniques, specifically frequency-division (FDMA), time-division (TDMA), and code-division multiple access (CDMA), explaining how bandwidth is shared among stations. Practical applications of these methods, such as cellular phone systems, are highlighted alongside examples and figures that clarify the concepts presented.

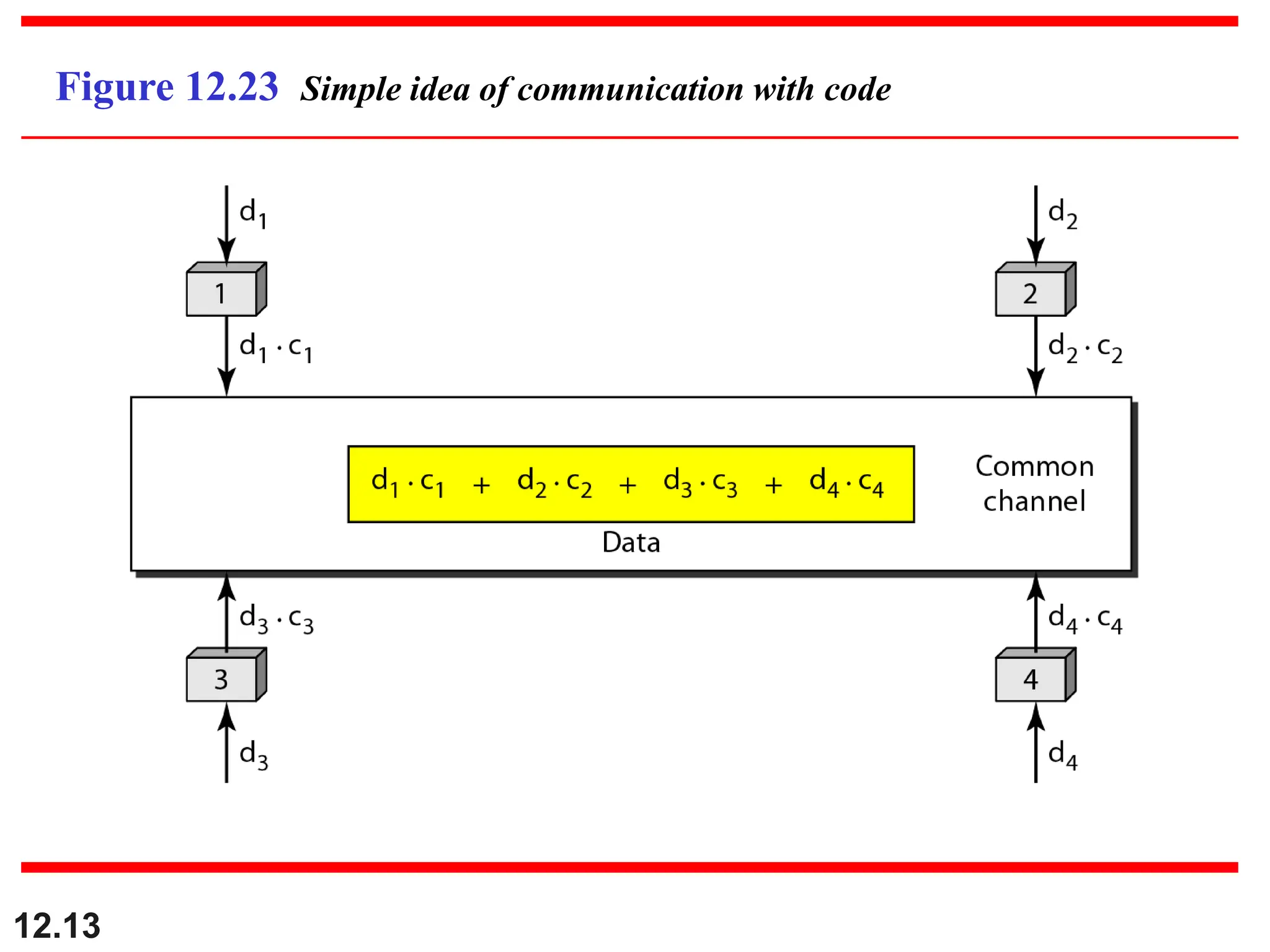
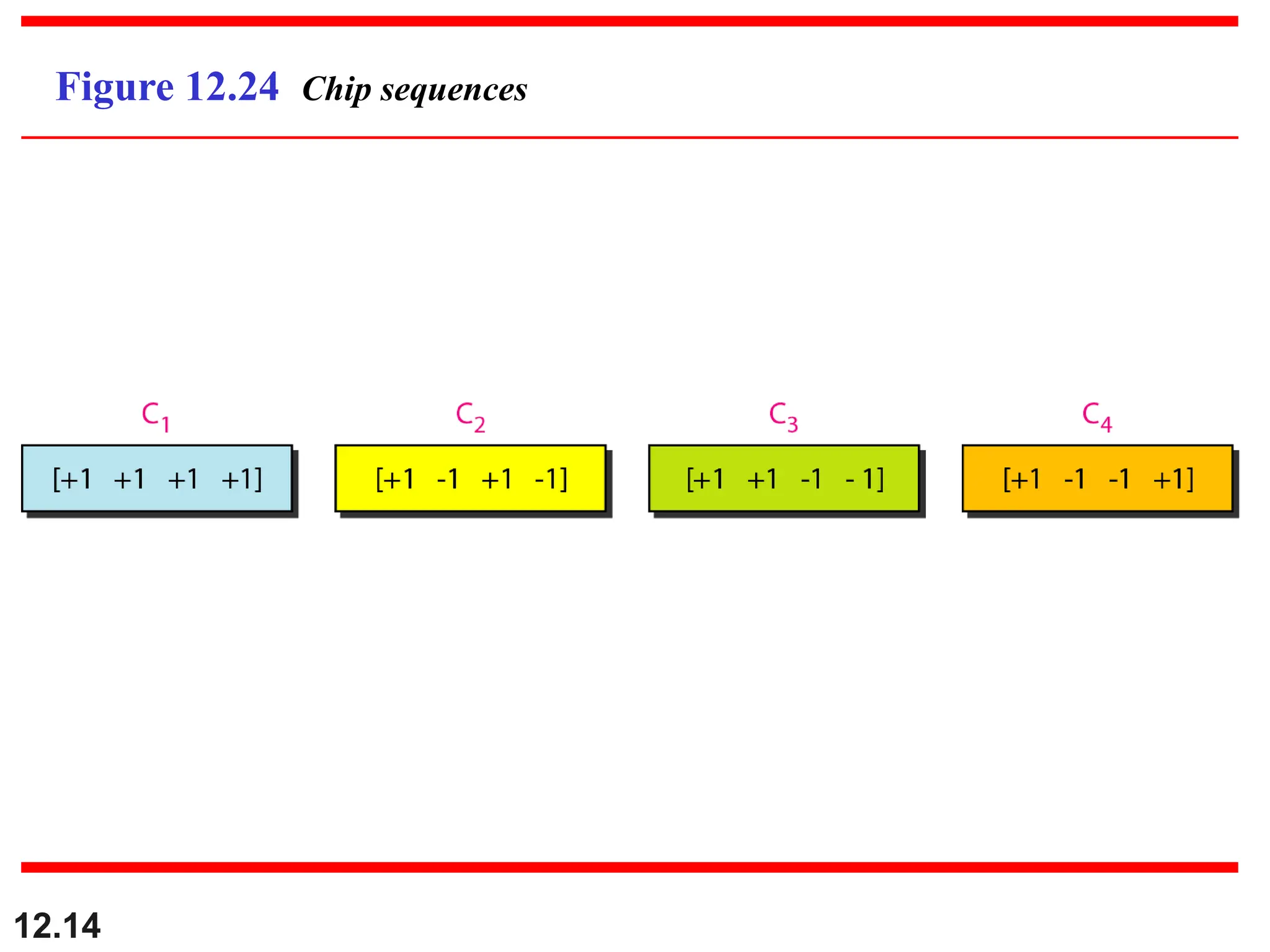
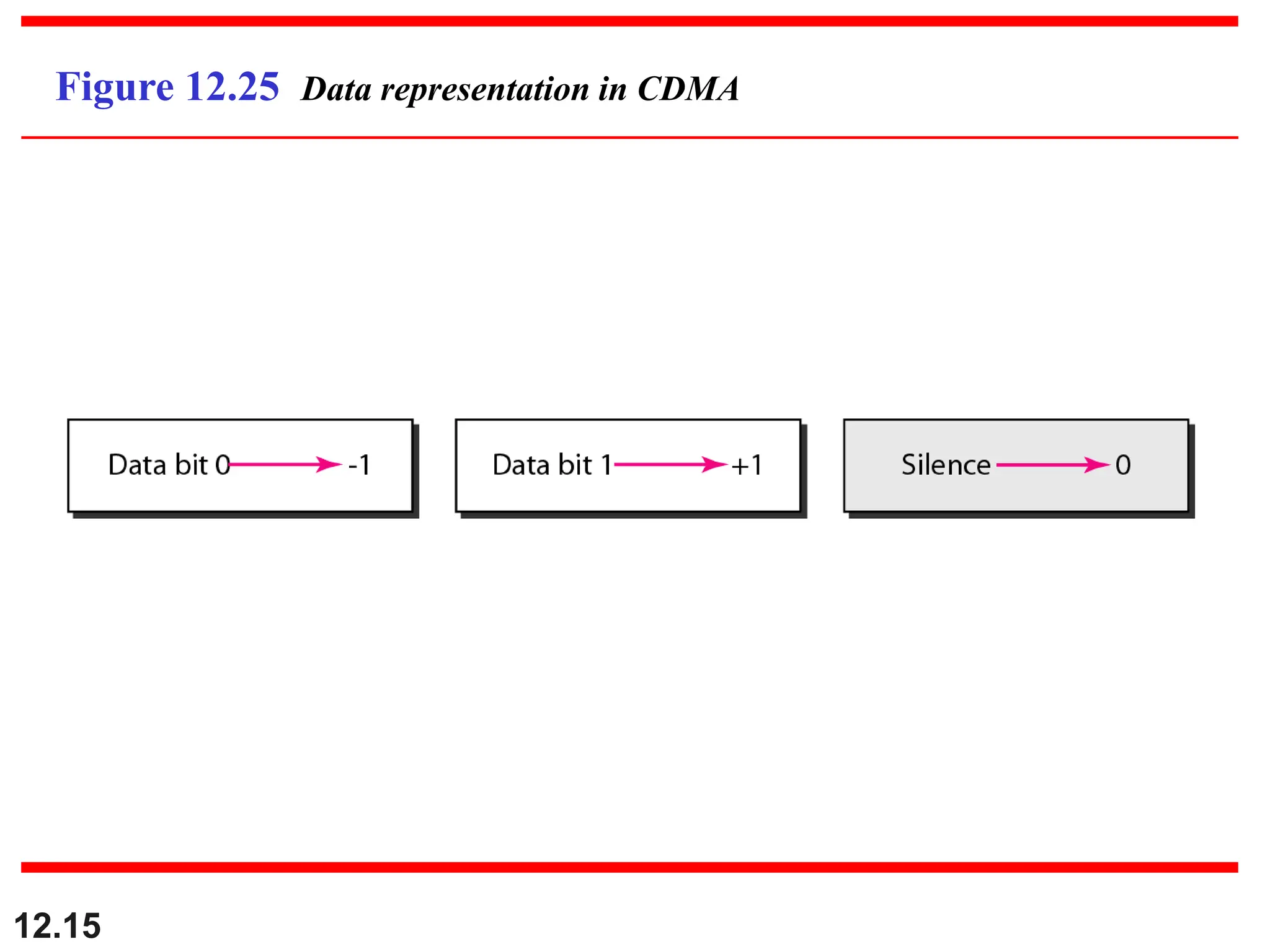
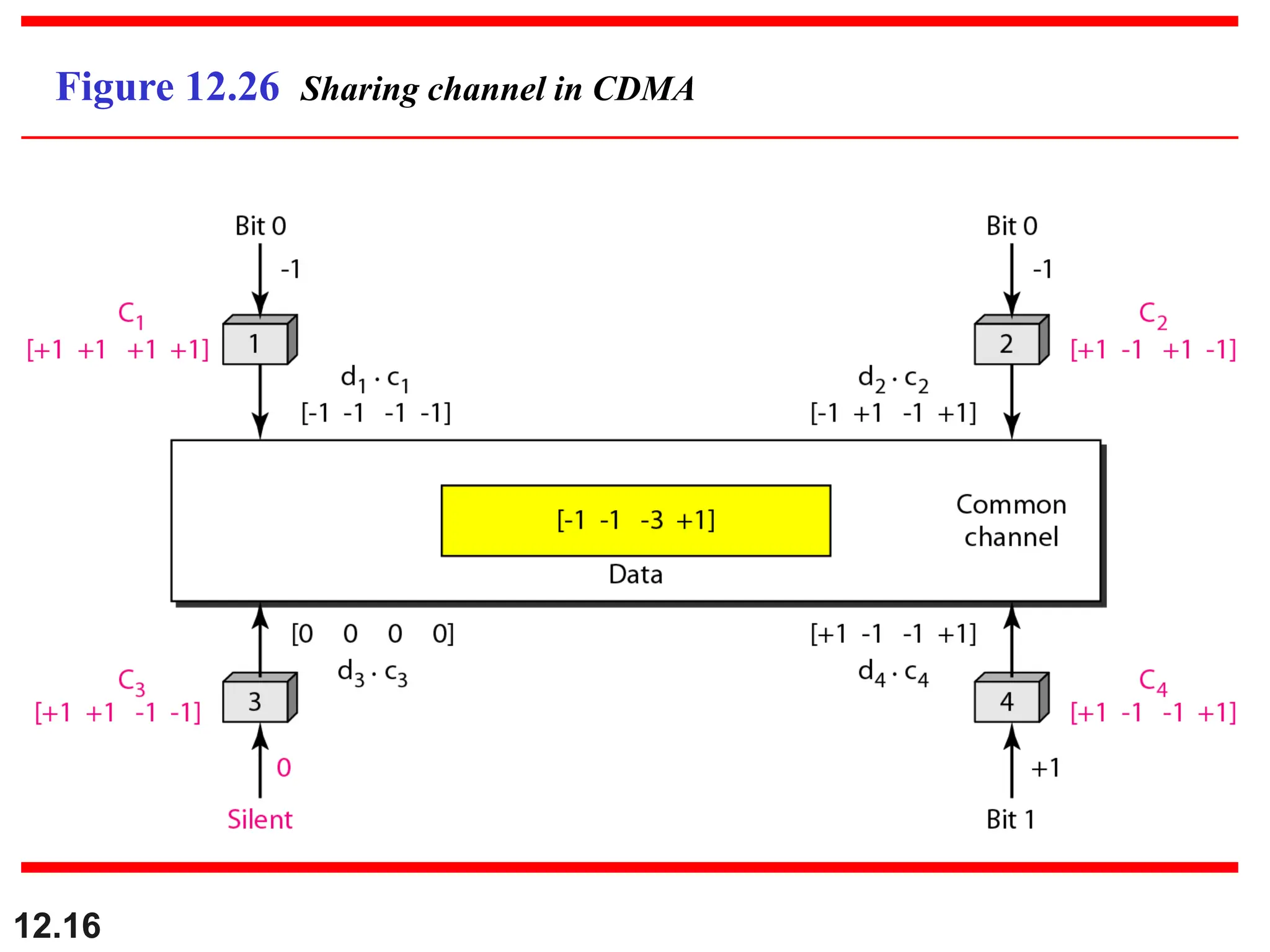
![12.21
Find the chips for a network with
a. Two stations b. Four stations
Example 12.6
Solution
We can use the rows of W2 and W4 in Figure 12.29:
a. For a two-station network, we have
[+1 +1] and [+1 −1].
b. For a four-station network we have
[+1 +1 +1 +1], [+1 −1 +1 −1],
[+1 +1 −1 −1], and [+1 −1 −1 +1].](https://image.slidesharecdn.com/y4eces7ln2425pptps-240615170212-b2baeb87/75/In-controlled-access-the-stations-consult-one-another-to-find-which-station-has-the-right-to-send-A-station-cannot-send-unless-it-has-been-authorized-by-other-stations-We-discuss-three-popular-controlled-access-methods-21-2048.jpg)