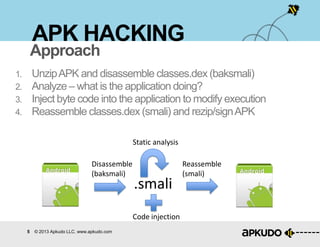
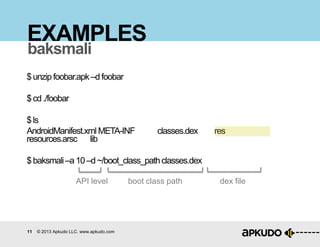
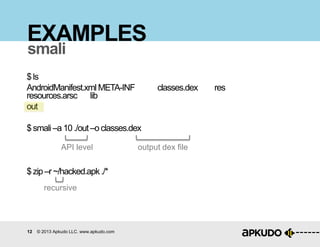
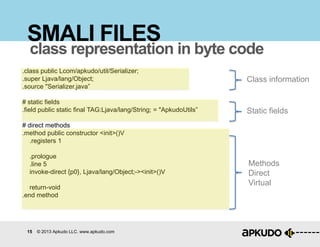
The document is a tutorial on hacking Android APKs, detailing the process of disassembling, modifying, and reassembling APK files using tools like smali, baksmali, and apktool. It includes a step-by-step guide on how to hack an application, specifically Snapchat, by injecting code to retrieve resources such as images. Additionally, it provides best practices for hardening apps against such modifications and discusses the tools and techniques employed in the process.











![18 © 2013 Apkudo LLC. www.apkudo.com
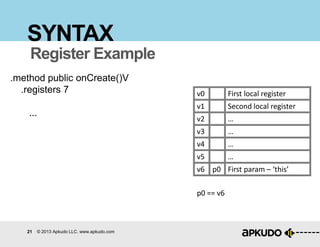
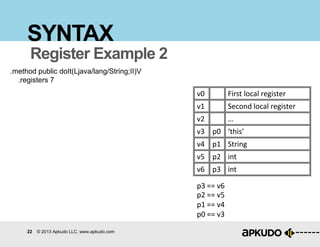
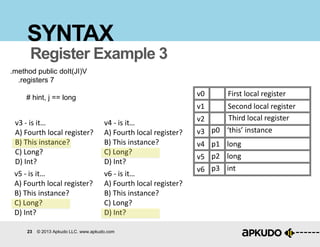
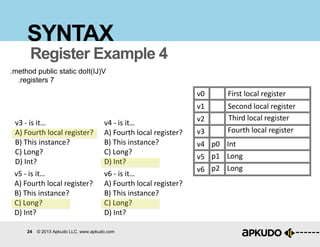
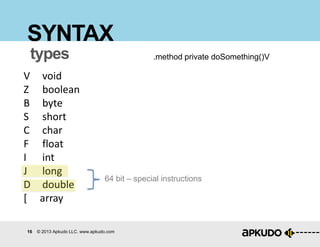
SYNTAX
Method definitions
.method <[keyword]> <name>(<[param]>)<return type>
Method invocations
invoke-static – any method that is static
invoke-virtual– any method that isn‟t private, static, or
final
invoke-direct – any non-static direct method
invoke-super – any superclass's virtual method
Invoke-interface– any interface method
Virtual methods require their class instance as a parameter!
.method private doSomething()Vmethods](https://image.slidesharecdn.com/hackingforfunandforprofit-130619123022-phpapp02/85/Hacking-for-Fun-and-Profit-Mostly-for-Fun-AnDevCon-Boston-18-320.jpg)