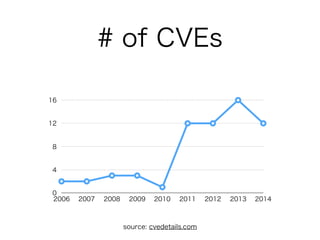
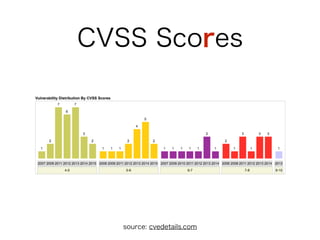
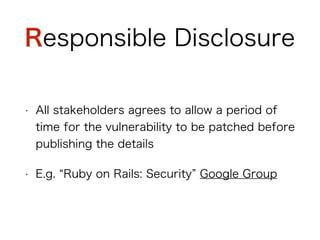
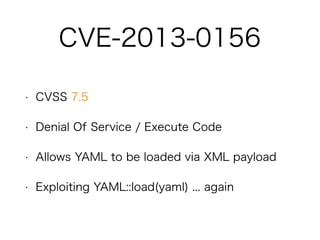
This document discusses hacking vulnerabilities in Ruby on Rails. It notes that as Ruby on Rails usage increases, it becomes a bigger target for hackers. Statistics are presented showing an increase in Common Vulnerabilities and Exposures (CVEs) reported for Ruby on Rails from 2006 to 2014. Several specific CVEs from 2013 are examined in detail, including code responsible, demonstrations of exploits, and links to patches. The document advocates for responsible disclosure of vulnerabilities and learning from past exploits to improve security.