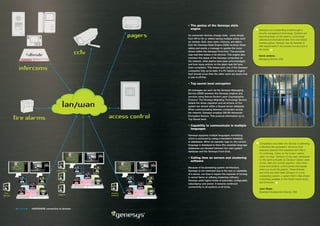
This document describes the Genesys integrated security management system from ISM. It discusses Genesys' system architecture which includes driver separation, a state engine, messaging service, and migrating technology to provide redundancy. Genesys provides a graphical user interface to monitor and control multiple security systems from different manufacturers on a single platform. It emphasizes ease of use, flexibility, and reliability.