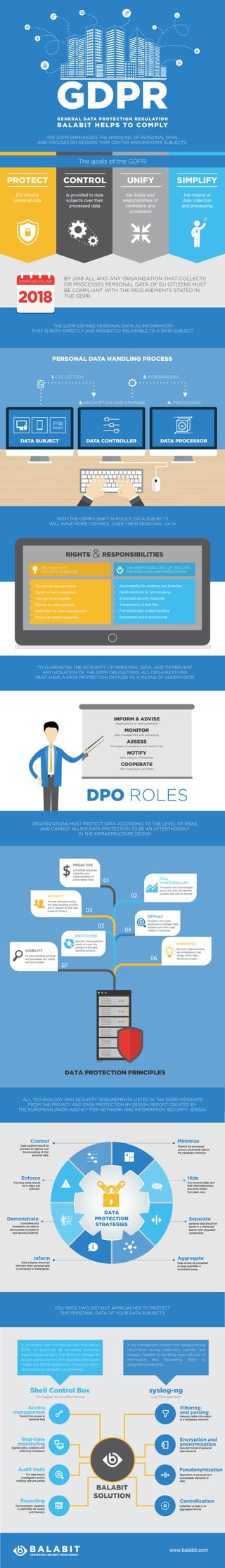
GDPR infographic
- 1. DPO ROLES INFORM & ADVISE organizations on data protection MONITOR data management and processing ASSESS the impact of protection and level of risk NOTIFY data subjects of breaches COOPERATE with supervisory authority DATA PROTECTION PRINCIPLES FULL FUNCTIONALITY Processes and technologies serve only their pre-defined purpose and will not deviate EMBEDDED Security measurements are embedded in the design of the data handling process VISIBILITY All data handling activities and processes are visible and accountable RESPECT All acts executed during the data handling process are in respect for the data subjects’ privacy PROACTIVE Immediate response capability and implementation of preventative tools END-TO-END Security measurements needs to cover the entirety of the data handling process DEFAULT Deviation from prior agreements between data subjects and other data entities is forbidden 01 02 03 04 05 06 07 GENERAL DATA PROTECTION REGULATION BALABIT HELPS TO COMPLY PROTECT CONTROL UNIFY SIMPLIFY The goals of the GDPR the duties and responsibilities of controllers and processors the means of data collection and processing EU citizens’ personal data is provided to data subjects over their processed data PERSONAL DATA HANDLING PROCESS 1. COLLECTION 2. ENCRYPTION AND STORAGE 3. FORWARDING 4. PROCESSING DATA SUBJECT DATA CONTROLLER DATA PROCESSOR WITH THE GDPR'S SHIFT IN POLICY, DATA SUBJECTS WILL HAVE MORE CONTROL OVER THEIR PERSONAL DATA THE GDPR DEFINES PERSONAL DATA AS INFORMATION THAT IS BOTH DIRECTLY AND INDIRECTLY RELATABLE TO A DATA SUBJECT THE GDPR EMPHASIZES THE HANDLING OF PERSONAL DATA, AND FOCUSES ON DESIGNS THAT CENTER AROUND DATA SUBJECTS The right to data correction Tighter consent requisitions The right to be forgotten Chance for data portability Notification on data endangerment Privacy by default measures THE RIGHTS OF THE DATA SUBJECTS Accountability for violations and breaches Harsh sanctions for not complying Embedded security measures Transparency of data flow Full functionality of data handling Guaranteed end-to-end security THE RESPONSIBILITIES OF THE DATA CONTROLLERS AND PROCESSORS RIGHTS & RESPONSIBILITIES ALL TECHNOLOGY AND SECURITY REQUIREMENTS LISTED IN THE GDPR ORIGINATE FROM THE PRIVACY AND DATA PROTECTION BY DESIGN REPORT CREATED BY THE EUROPEAN UNION AGENCY FOR NETWORK AND INFORMATION SECURITY (ENISA) Hide Separate Minimize Aggregate Enforce Demonstrate Control Inform DATA PROTECTION STRATEGIES Restrict the processed amount of personal data to the necessary minimum. Data subjects should be provided an agency over the processing of their personal data. Any personal data, and their interrelationships, should be hidden from plain view. personal data should be stored in a distributed fashion with separated components. Data should be processed at large quantities in centralized areas. A privacy policy should be in place and enforced. Controllers and processors are able to demonstrate compliance and security incidents. Data subjects should be informed when personal data is processed or endangered. YOU NEED TWO DISTINCT APPROACHES TO PROTECT THE PERSONAL DATA OF YOUR DATA SUBJECTS Shell Control Box A log management system that safeguards log information during collection, transfer and storage. Capable to handling mass volumes of information and forwarding them to designated endpoints. syslog-ng www.balabit.com ORGANIZATIONS MUST PROTECT DATA ACCORDING TO THE LEVEL OF RISKS, AND CANNOT ALLOW DATA PROTECTION TO BE AN AFTERTHOUGHT IN THE INFRASTRUCTURE DESIGN TO GUARANTEE THE INTEGRITY OF PERSONAL DATA, AND TO PREVENT ANY VIOLATION OF THE GDPR OBLIGATIONS, ALL ORGANIZATIONS MUST HAVE A DATA PROTECTION OFFICER AS A MEANS OF SUPERVISION A privileged user monitoring tool that allows DPOs to supervise all processes executed against personal data. The ability to manage all access points and monitor activities that could violate the GDPR obligations. Providing review and reporting capability on all events. BALABIT SOLUTION Access management Restrict the access to personal data Real-time monitoring Against policy violations and enforcing compliance Audit trails For data breach investigation and for notifying relevant parties Reporting Demonstration capability to authorities for review and forensics Filtering and parsing Keeping visible information at a necessary minimum Encryption and anonymization Secured format of personal data elements Pseudonymization Separation of personal and processable elements of data Centralization Collection of data in an aggregated format Privileged Access Monitoring Log Management BY 2018 ALL AND ANY ORGANIZATION THAT COLLECTS OR PROCESSES PERSONAL DATA OF EU CITIZENS MUST BE COMPLIANT WITH THE REQUIREMENTS STATED IN THE GDPR. GDPR DEADLINE 2018
