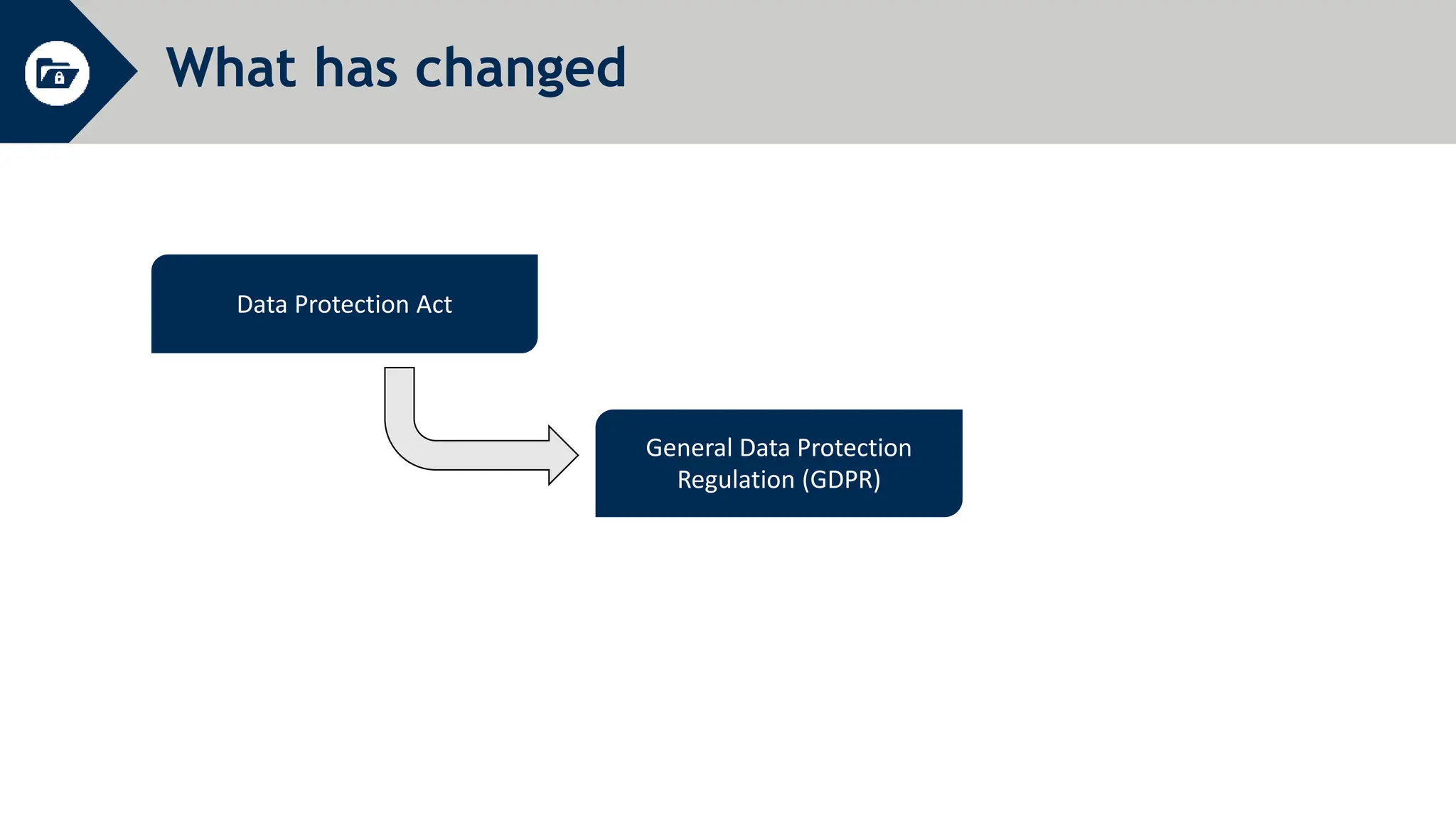
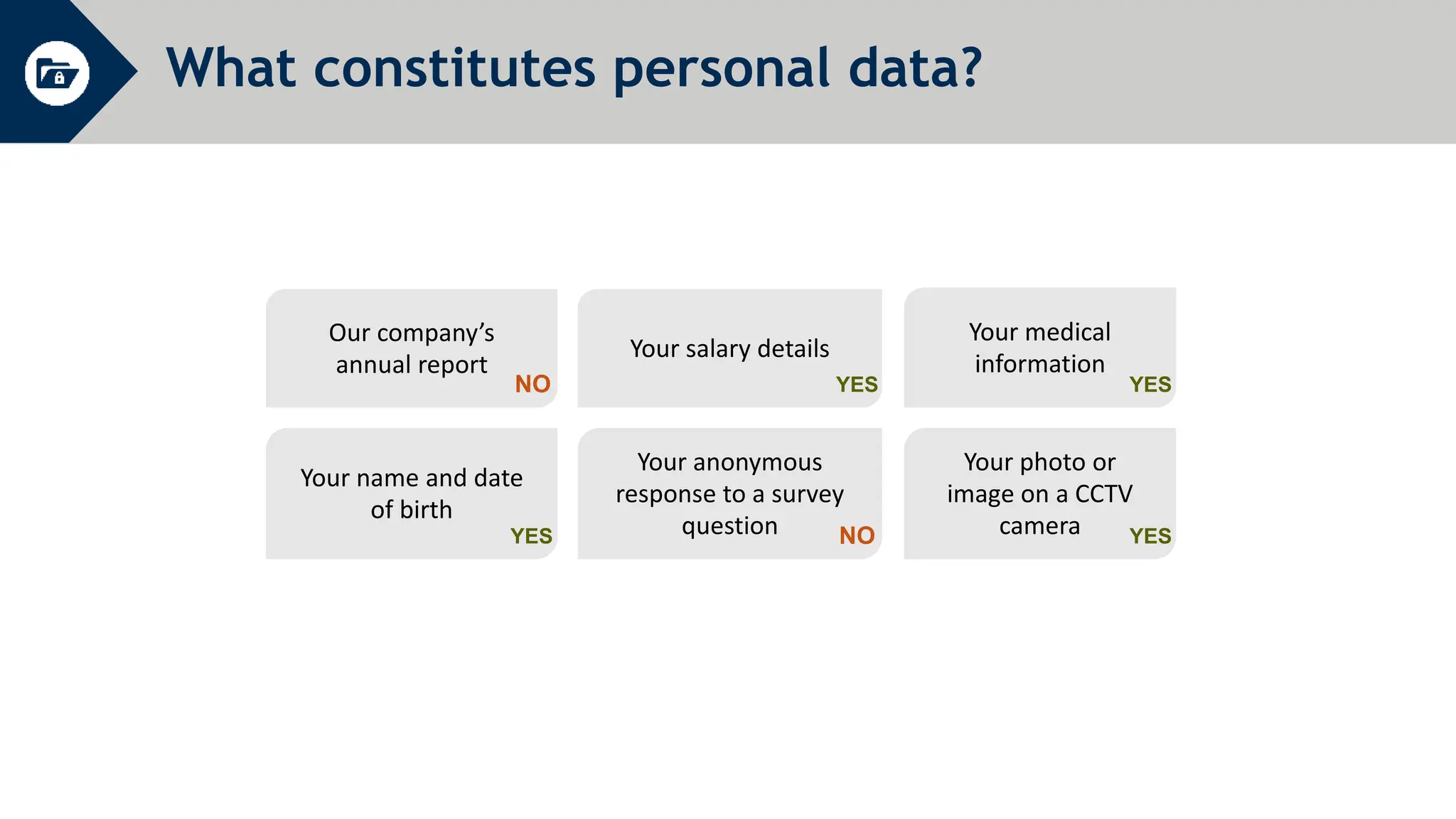
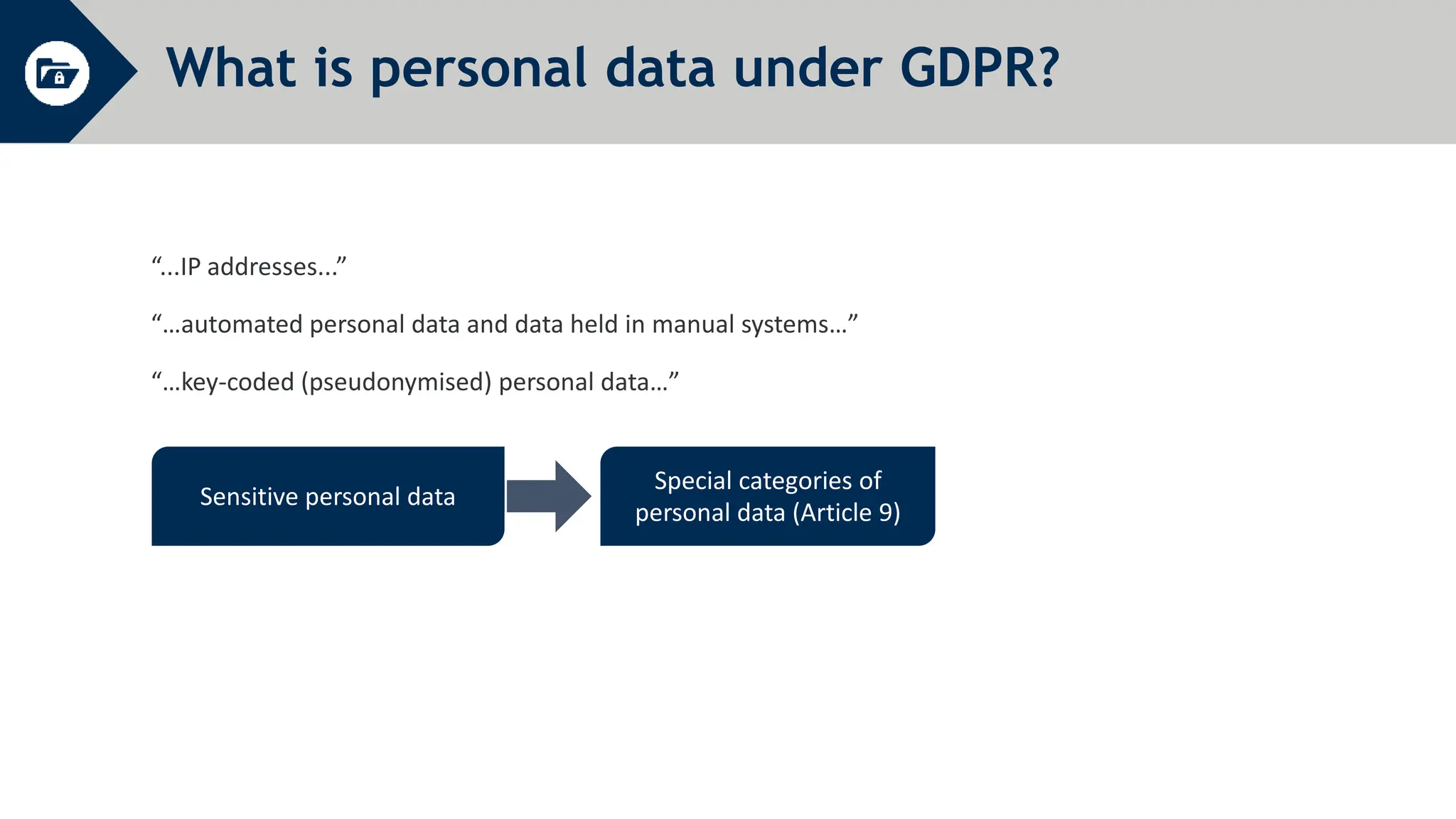
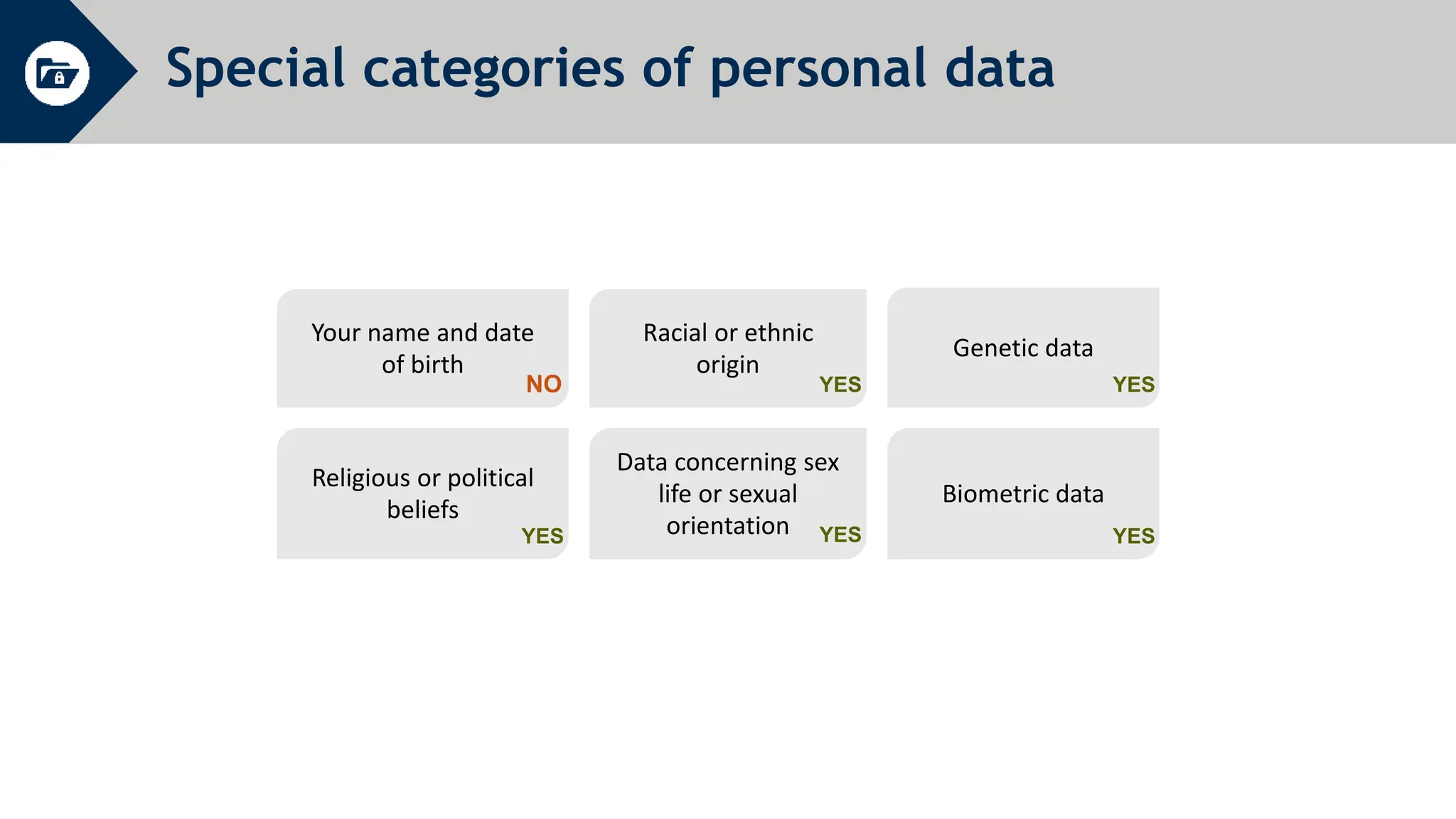
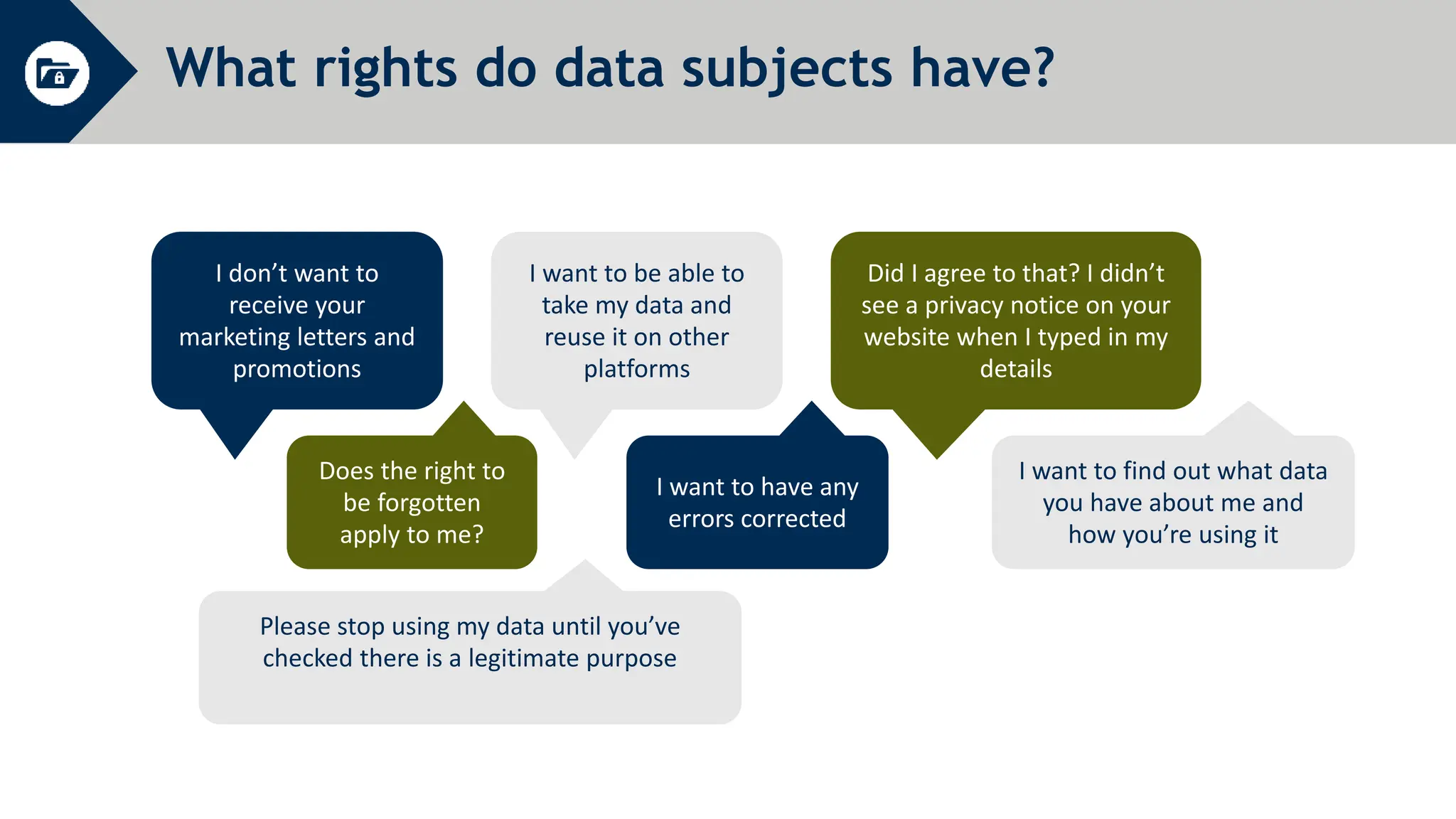
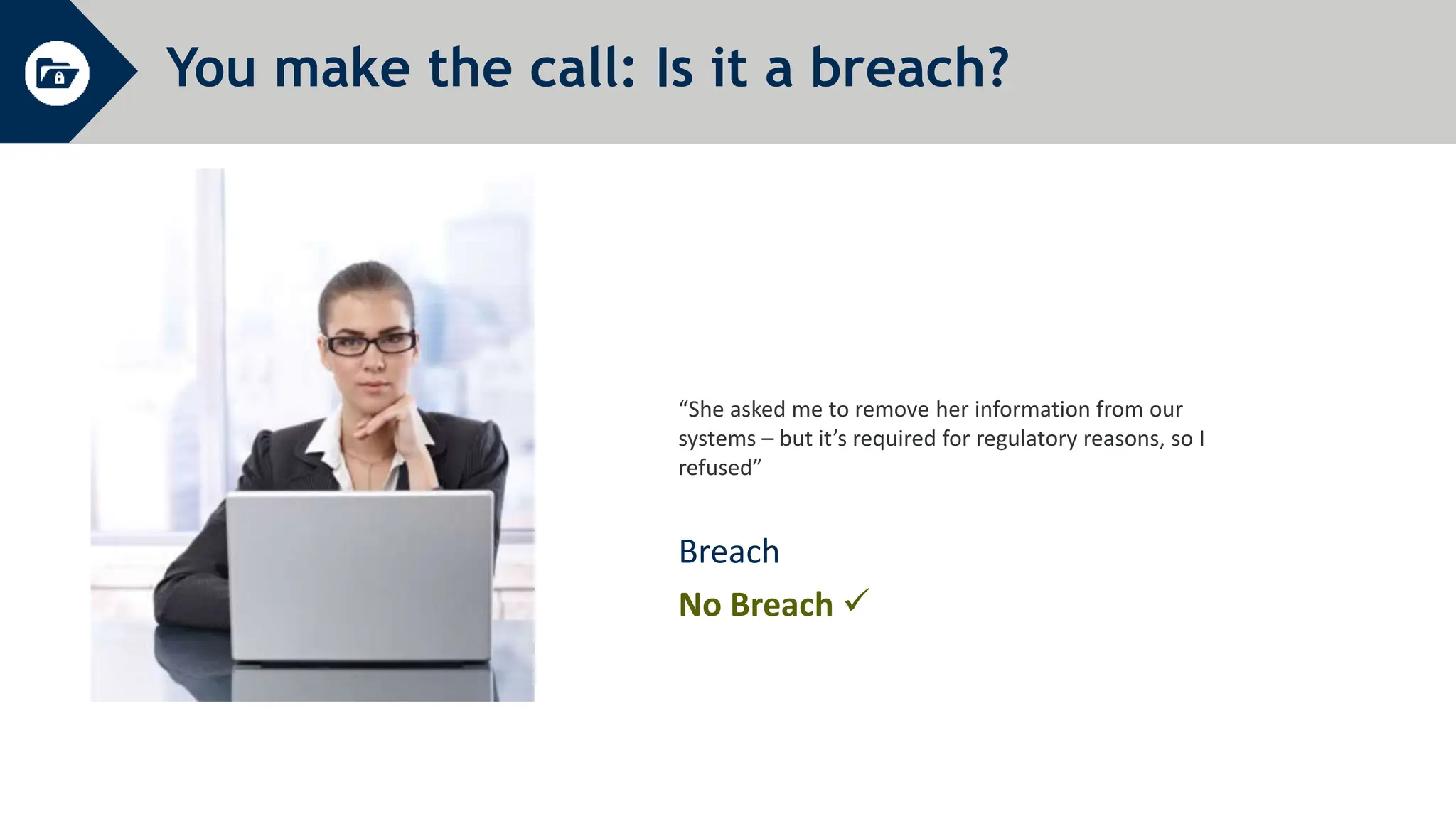
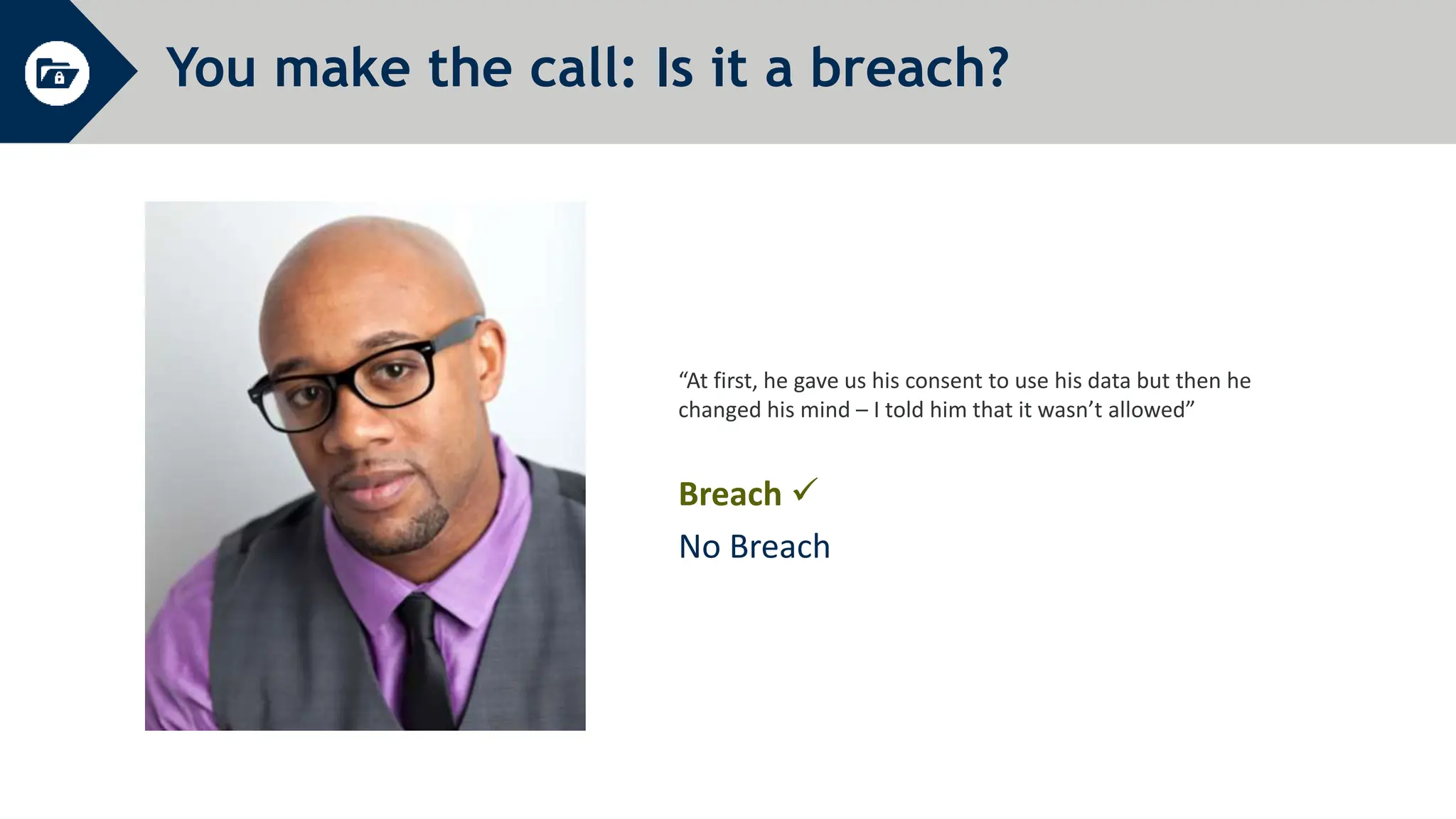
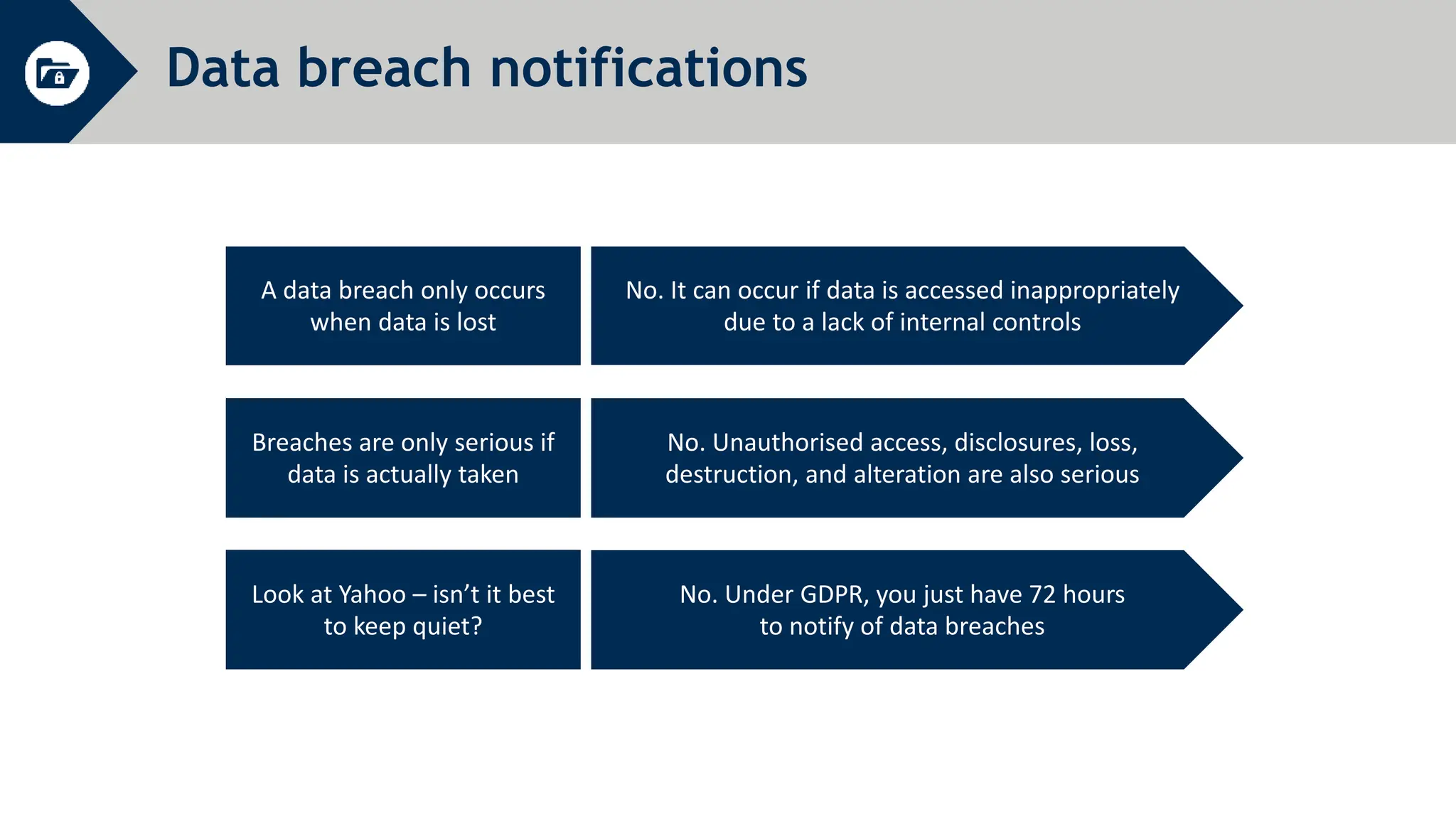
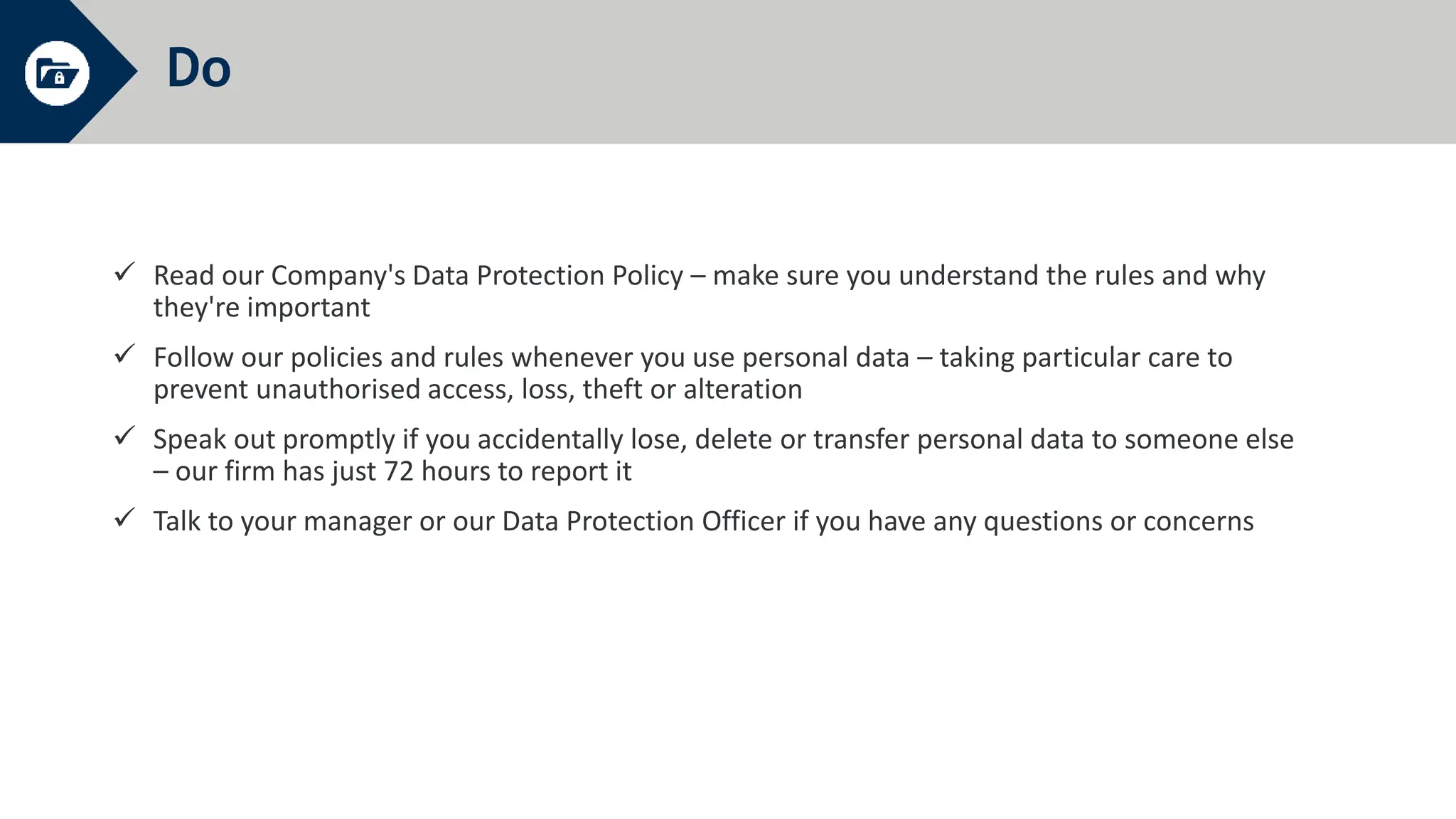
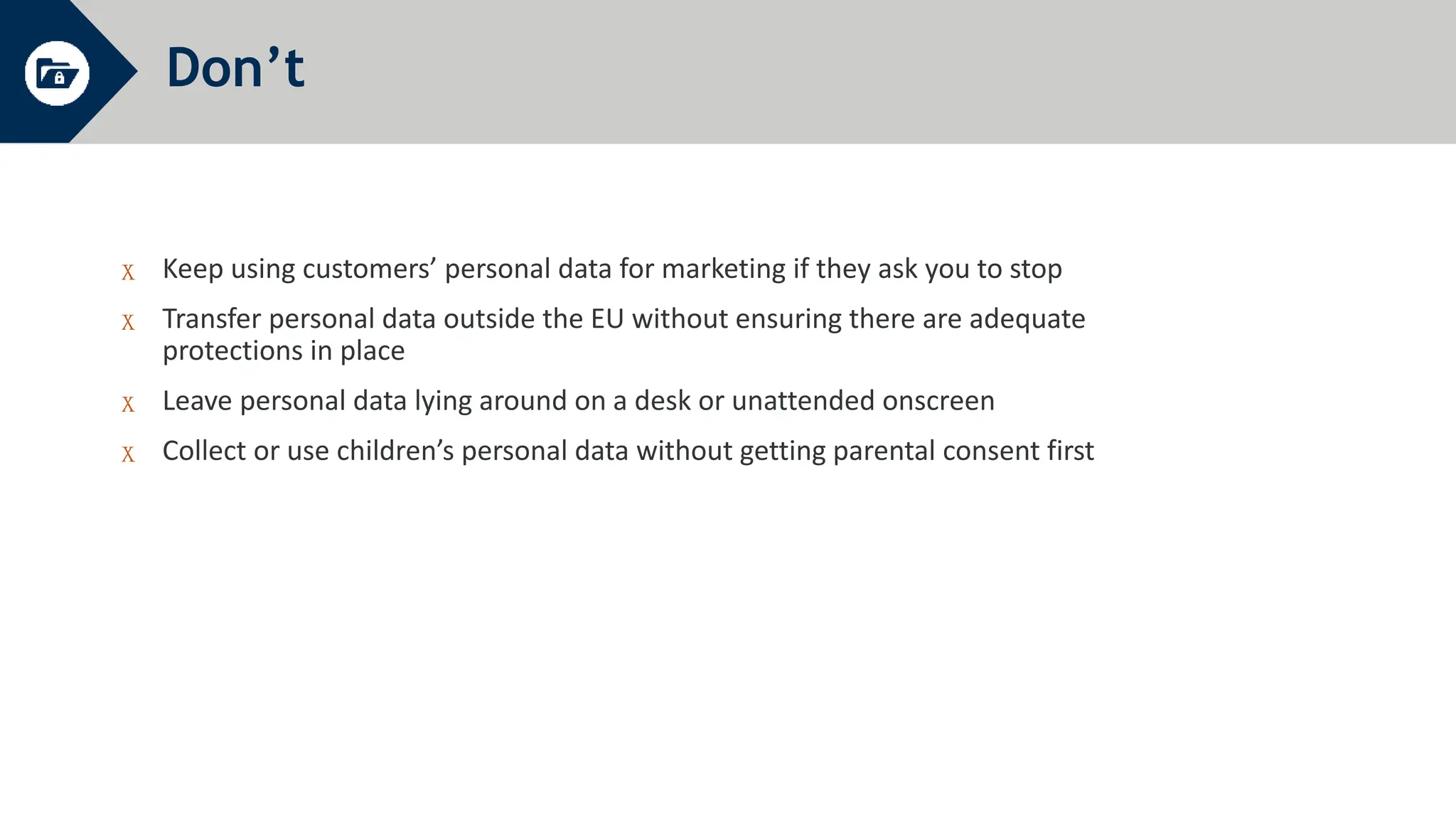
General Data Protection Regulation (GDPR) establishes rules around personal data and privacy. It defines personal data broadly as any information related to an identifiable individual. GDPR gives individuals rights over their personal data, including rights to access, correct, and delete personal data. It also requires organizations to only process personal data for specific legitimate purposes, notify authorities of data breaches within 72 hours, and can issue fines of up to 4% of global annual turnover for violations. The document provides an overview of key GDPR concepts and requirements for an organization to comply with the regulation.