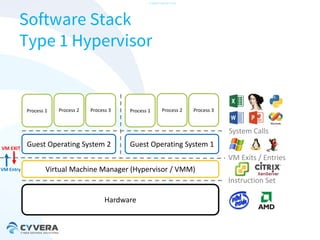
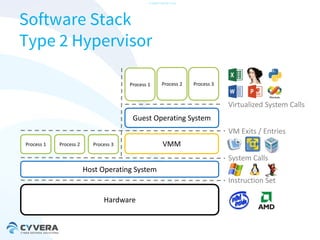
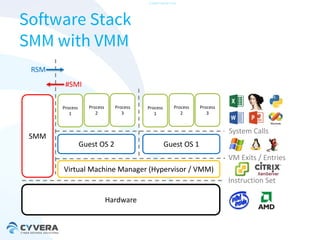
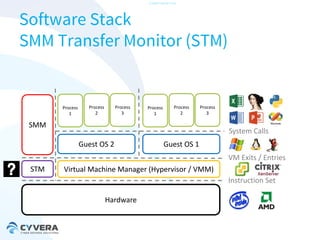
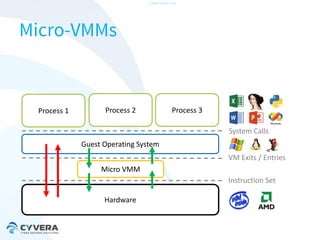
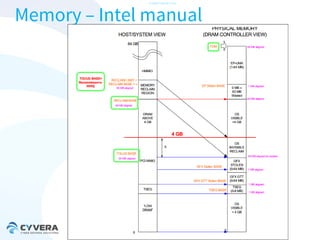
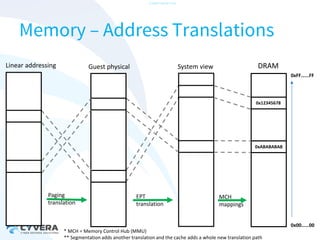
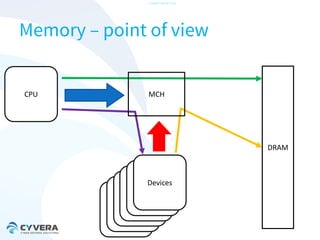
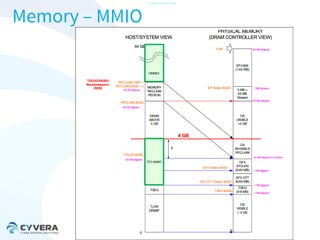
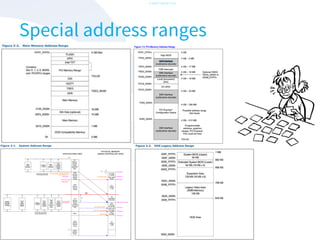
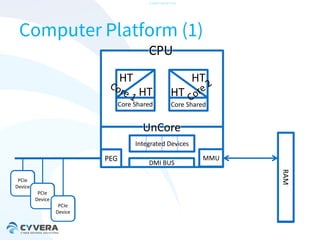
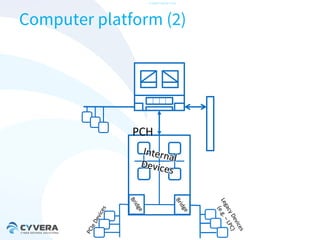
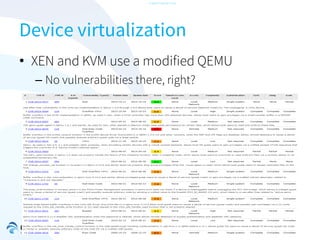
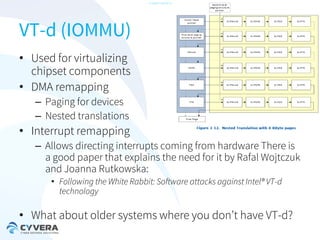
The document discusses the challenges of securing virtualization from a technical perspective. It covers weaknesses in hardware-assisted virtualization approaches, software stacks used for virtualization, complex memory management, computer platform internals, and potential attack vectors against virtualization. The presentation aims to demonstrate that achieving secure virtualization is virtually impossible due to the numerous opportunities for exploitation throughout the software and hardware stack.