This document provides an in-depth examination of bootkits, detailing how they achieve persistence below the operating system kernel level and offering detection and prevention advice. It covers various boot processes across different operating systems, low-level technologies such as BIOS, UEFI, and Secure Boot, and discusses multiple case studies and countermeasures against exploitation techniques. The conclusion emphasizes the ongoing potential for vulnerabilities and the importance of adopting common security practices.
![IBM Security Systems | © 2014 IBM Corporation
BOOTKITS STEP-BY-STEP
AN IN-DEPTH LOOK AT PERSISTENCE MECHANISMS USED BY BOOTKITS
Eric Koeppen
IBM X-Force Advanced Research
erkoeppe[at]us[dot]ibm[dot]com
@PorkChop
(v1)](https://image.slidesharecdn.com/bootkitsstep-by-step-slides-final-v1-release-140721150417-phpapp01/75/Bootkits-step-by-step-slides-final-v1-release-1-2048.jpg)





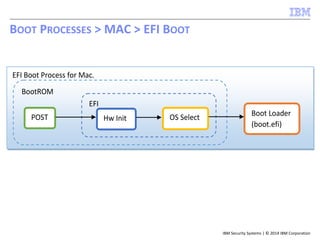
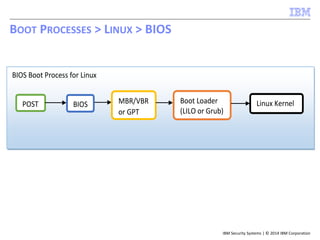
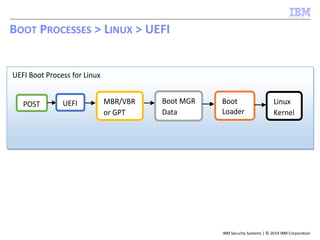
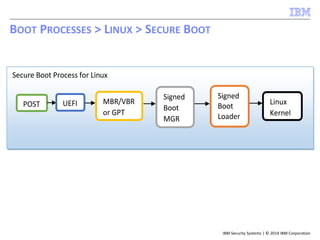

































![IBM Security Systems | © 2014 IBM Corporation
BOOTKITS STEP-BY-STEP:
AN IN-DEPTH LOOK AT PERSISTENCE MECHANISMS USED BY BOOTKITS
Thank You!
Eric Koeppen
IBM X-Force Advanced Research
erkoeppe[at]us[dot]ibm[dot]com
@PorkChop](https://image.slidesharecdn.com/bootkitsstep-by-step-slides-final-v1-release-140721150417-phpapp01/85/Bootkits-step-by-step-slides-final-v1-release-53-320.jpg)