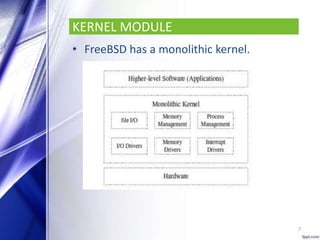
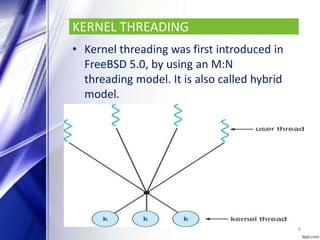
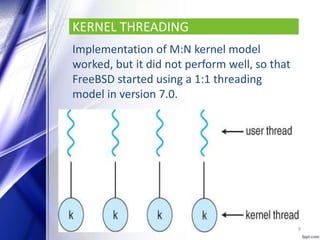
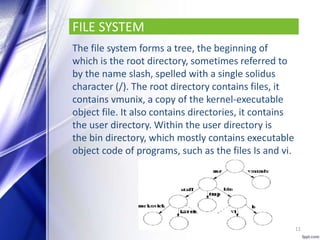
FreeBSD is an open source, Unix-like operating system that provides features such as multitasking, memory protection, and multi-user facilities. It is used by many companies including IBM, Nokia, Apple, and Netflix to build products and operating systems. FreeBSD has a monolithic kernel and uses a 1:1 threading model. It supports processes, files systems with directories and files, and memory management using paging and swapping. FreeBSD also supports network communication using multiple protocols and allows file sharing between clients and servers using NFS. Security features include SSL, TLS, access control lists, and mandatory access controls developed by the TrustedBSD project.