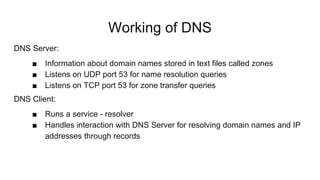
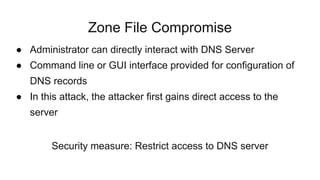
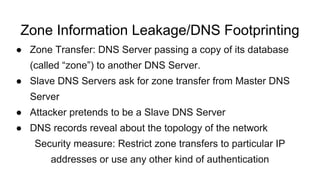
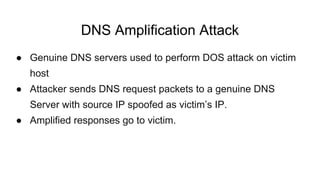
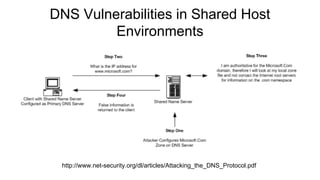
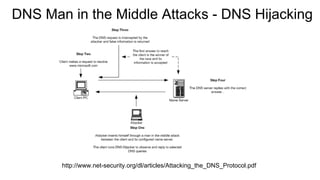
Dhaval Kapil presented on DNS security. He discussed how DNS works and its flaws due to a lack of security in its original design. This allowed various threats to emerge like zone file compromise, DNS amplification attacks, and cache poisoning. To mitigate these threats, extensions like DNSSEC were developed to authenticate DNS responses and ensure integrity, though adoption remains limited.