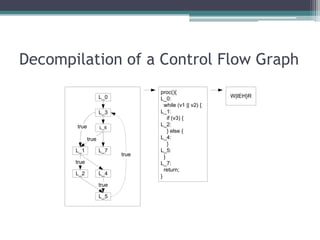
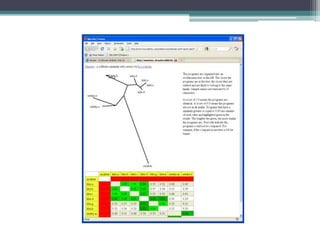
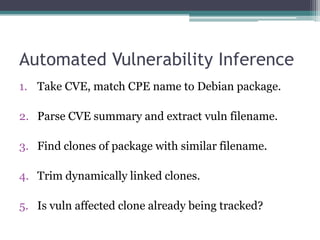
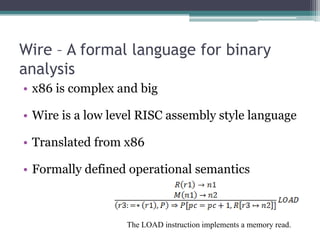
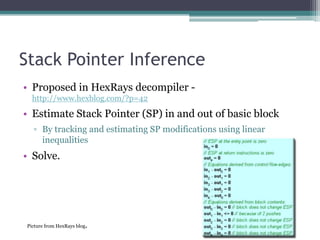
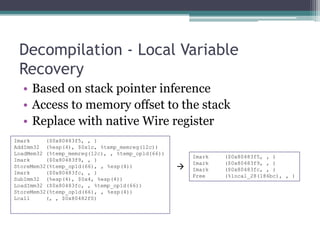
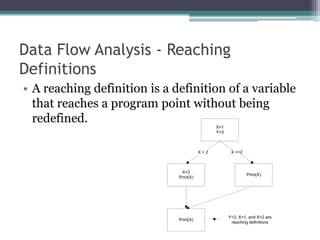
Bugwise is a tool that detects bugs in binaries using decompilation and data flow analysis. It detects issues like use-after-free bugs, double free bugs, and unsafe calls to getenv(). It has scanned over 123,000 Debian binaries and reported 85 getenv() related bugs across 47 packages. The probability of a binary having a vulnerability is 0.00067, and the probability of a package having at least one vulnerable binary is 0.00255. Bugwise is based on strong theoretical underpinnings like data flow analysis and is extensible to detect more bug classes. The presenter aims to make more of their research public and get more people using their tools via their website.





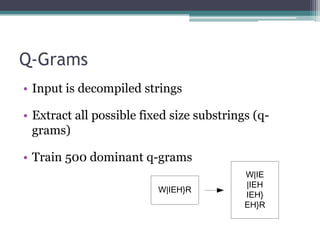






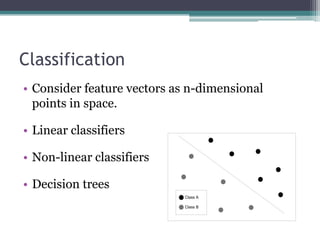










![Use-after-free Detection
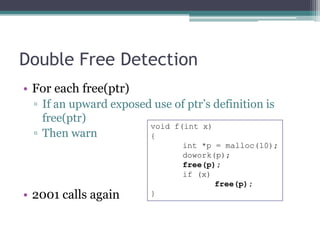
• For each free(ptr)
▫ If ptr live
void f(int x)
▫ Then warn {
int *p = malloc(10);
dowork(p);
free(p);
if (x)
p[0] = 1;
}](https://image.slidesharecdn.com/ruxconttalk-121022055037-phpapp01/85/FooCodeChu-Services-for-Software-Analysis-Malware-Detection-and-Vulnerability-Research-42-320.jpg)



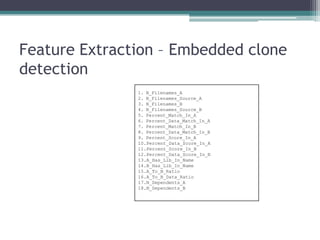
![Double free in SGID games “xonix”
memset(score_rec[i].login, 0, 11);
strncpy(score_rec[i].login, pw->pw_name, 10);
memset(score_rec[i].full, 0, 65);
strncpy(score_rec[i].full, fullname, 64);
score_rec[i].tstamp = time(NULL);
free(fullname);
if((high = freopen(PATH_HIGHSCORE, "w",high)) == NULL) {
fprintf(stderr, "xonix: cannot reopen high score filen");
free(fullname);
gameover_pending = 0;
return;
}](https://image.slidesharecdn.com/ruxconttalk-121022055037-phpapp01/85/FooCodeChu-Services-for-Software-Analysis-Malware-Detection-and-Vulnerability-Research-48-320.jpg)




