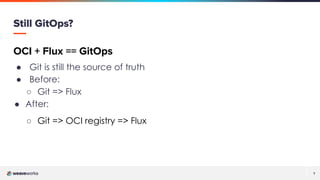
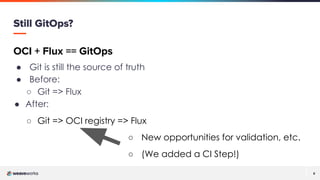
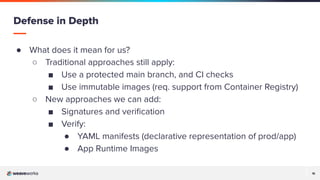
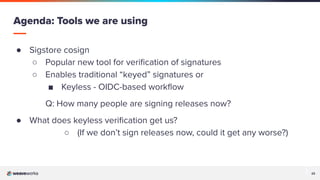
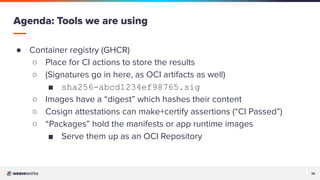
The document discusses a presentation on improving Flux's security and scalability using OCI and Helm, focusing on GitOps principles and features such as image verification with cosign. It covers the transition from using Git repositories to OCI registries for managing application deployments and highlights tools like Sigstore cosign for validation and security. Additionally, the presentation emphasizes community engagement and the use of GitOps tools to enhance Kubernetes development and operations.