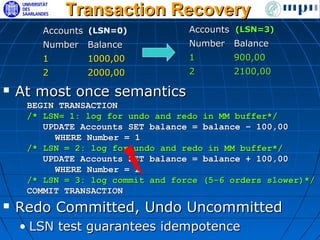
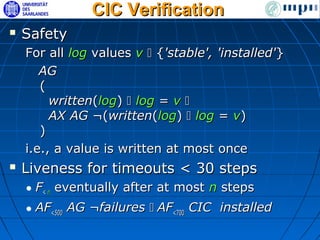
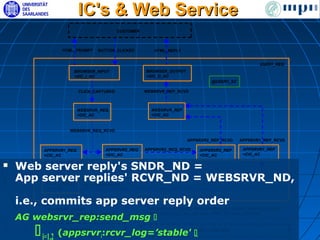
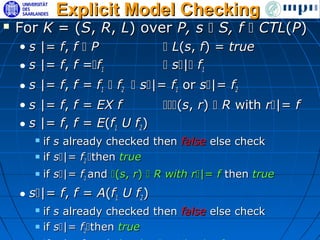
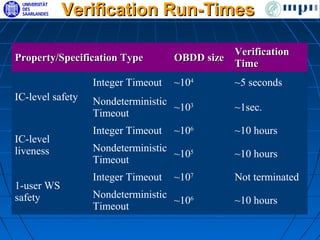
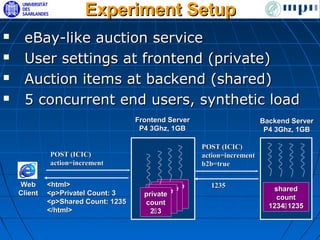
The document discusses ensuring exactly-once execution semantics for web services through the use of interaction contracts and failure masking techniques implemented in a PHP framework called EOS. It presents an interaction contracts framework that uses formal specifications, model checking, and persistent logging to guarantee exactly-once execution across failures. The document also evaluates the performance overhead of the EOS implementation through an experiment running a simulated e-commerce auction service.




![Committed IC Monitor
Statechart = Behavioral View
• Finite State Automaton (FSA) +
• Nesting + Orthogonal substates +
• E[C]/A transitions: on Event while Condition
Leave source, enter target, execute Action
E.g., A = E' means generate event E'
CIC_SC
SNDR_S
(not SNDR_CRASH)
•Configuration =active(CIC_SNDR_AC) ]/
SENDING [not set of entered
states
start!(CIC_SNDR_AC)
• Execution context = variable valuation
Stepi: confi ctxti confi+1 ctxti+1 RCVR_S
(not RCVR_CRASH)
RECEIVING
[not active(CIC_RCVR_AC)]/
start!(CIC_RCVR_AC)](https://image.slidesharecdn.com/doctoral-thesis-defense-shegalov-130204112530-phpapp01/85/Integrated-Data-Message-and-Process-Recovery-for-Failure-Masking-in-Web-Services-12-320.jpg)
![Committed IC Sender
CIC_SNDR_SC
MSG_LOOKUP
MSG_RECOVERED_TM/
SEND_MSG GET_MSG_OK
STABLE_S INSTALLED_OK/
SNDR_LAST_LOGGED:='INSTALLED'
SNDR_MSG_TM and
not (STABLE_OK or STABLE_OK SNDR_STABLE_TM and
INSTALLED_OK)/ not (INSTALLED_OK or GET_MSG_OK)/
SEND_MSG IS_INSTALLED
INSTALLED_OK/
SENDING SNDR_LAST_LOGGED:='INSTALLED' INSTALLED_S
SNDR_ND/
SEND_MSG SNDR_TRIGGER [SNDR_LAST_LOGGED=='INSTALLED']
[SNDR_LAST_LOGGED=='']/
SNDR_LAST_LOGGED
PREPARE_PERSISTENCE SNDR_ND RECOVERY
SNDR_CRASH
T
*
EVENT_OK = EVENT LINK_OUTAGE _TM means TIMEOUT](https://image.slidesharecdn.com/doctoral-thesis-defense-shegalov-130204112530-phpapp01/85/Integrated-Data-Message-and-Process-Recovery-for-Failure-Masking-in-Web-Services-13-320.jpg)
![Committed IC Receiver
CIC_RCVR_SC [RCVR_LAST_LOGGED=='STABLE']/
GET_MSG
MSG_RECOVERY
not SEND_MSG_OK
and SEND_MSG_OK
GET_MSG_TM/ SEND_MSG_OK
GET_MSG [RCVR_LAST_LOGGED=='']
MSG_RECEIVED RECOVERY
MSG_EXEC_TM/
RECEIVED;
[RCVR_LAST_LOGGED=='INSTALLED']
[RCVR_LAST_LOGGED=='STABLE'] [ICIC]/
MSG_PROCESSED RCVR_LAST_LOGGED:='INSTALLED';
INSTALLED
( RCVR_STABLE_TM or
RCVR_ND [MSG_ORDER_MATTERS] )
[not ICIC and RCVR_LAST_LOGGED=='']/
RCVR_LAST_LOGGED:='STABLE';
STABLE
RCVR_INSTALL_TM/ RCVR_LAST_LOGGED:='INSTALLED'; INSTALLED
RCVR_LAST_LOGGED:='INSTALLED' INSTALLED_R
STABLE_R
SEND_MSG or IS_INSTALLED/ SEND_MSG or IS_INSTALLED/
STABLE INSTALLED
RCVR_CRASH
T
*
EVENT_OK = EVENT LINK_OUTAGE, _TM means TIMEOUT](https://image.slidesharecdn.com/doctoral-thesis-defense-shegalov-130204112530-phpapp01/85/Integrated-Data-Message-and-Process-Recovery-for-Failure-Masking-in-Web-Services-14-320.jpg)
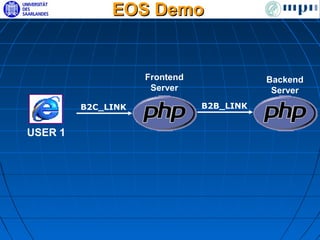
![PHP and Zend Engine
<html>
Web Web
Script called 5 times Web Web
Client Client Client Client
1. <html> server reports: Script called 1000 times
Other
</html>
2. <?php
3. session_start();
4. $HTTP_SESSION_VARS["count"]++;
5. printf("Script called %i times",
6. $HTTP_SESSION_VARS["count"]);
Zend Engine
7. $ch = curl_init("http://eos-php.net/b2b.php");
8. $b2b_reply = Session CURL
curl_exec($ch);
9. printf("Other server reports: %s", $b2b_reply);
10. curl_close($ch);
11.?>
12.</html>
Zend Engine Zend Engine
Session CURL Session CURL](https://image.slidesharecdn.com/doctoral-thesis-defense-shegalov-130204112530-phpapp01/85/Integrated-Data-Message-and-Process-Recovery-for-Failure-Masking-in-Web-Services-22-320.jpg)

![Run-Time Overhead
Frontend
Session Server1 step 5 steps Backend
10 steps
Server
PHP elapsed time [sec] 0.1560 0.7900 1.6100
POST (ICIC)
POST (ICIC) action=increment
EOS-PHPaction=increment [sec]
elapsed time 0.3140
b2b=true 1.6850 3.1000
Overhead (elapsed time) [%]
Web <html>
101% 113%
1235 93%
private
private shared
PHP frontend CPU Count: 3
Client <p>Privatel time [sec] private
private
count
count 0.0390
<p>Shared Count: 1235 count 0.2708 0.5727
count
count 23
23 12341235
EOS-PHP frontend CPU time [sec]
</html> 21
23
0.0815 0.6000 1.1545
Overhead (frontend CPU) [%] 109% 122% 102%
PHP backend CPU time [sec] 0.0090 0.0550 0.1200
EOS-PHP backend CPU time [sec] 0.0130 0.0750 0.1600
Overhead (backend CPU) [%] 44% 36% 33%](https://image.slidesharecdn.com/doctoral-thesis-defense-shegalov-130204112530-phpapp01/85/Integrated-Data-Message-and-Process-Recovery-for-Failure-Masking-in-Web-Services-25-320.jpg)