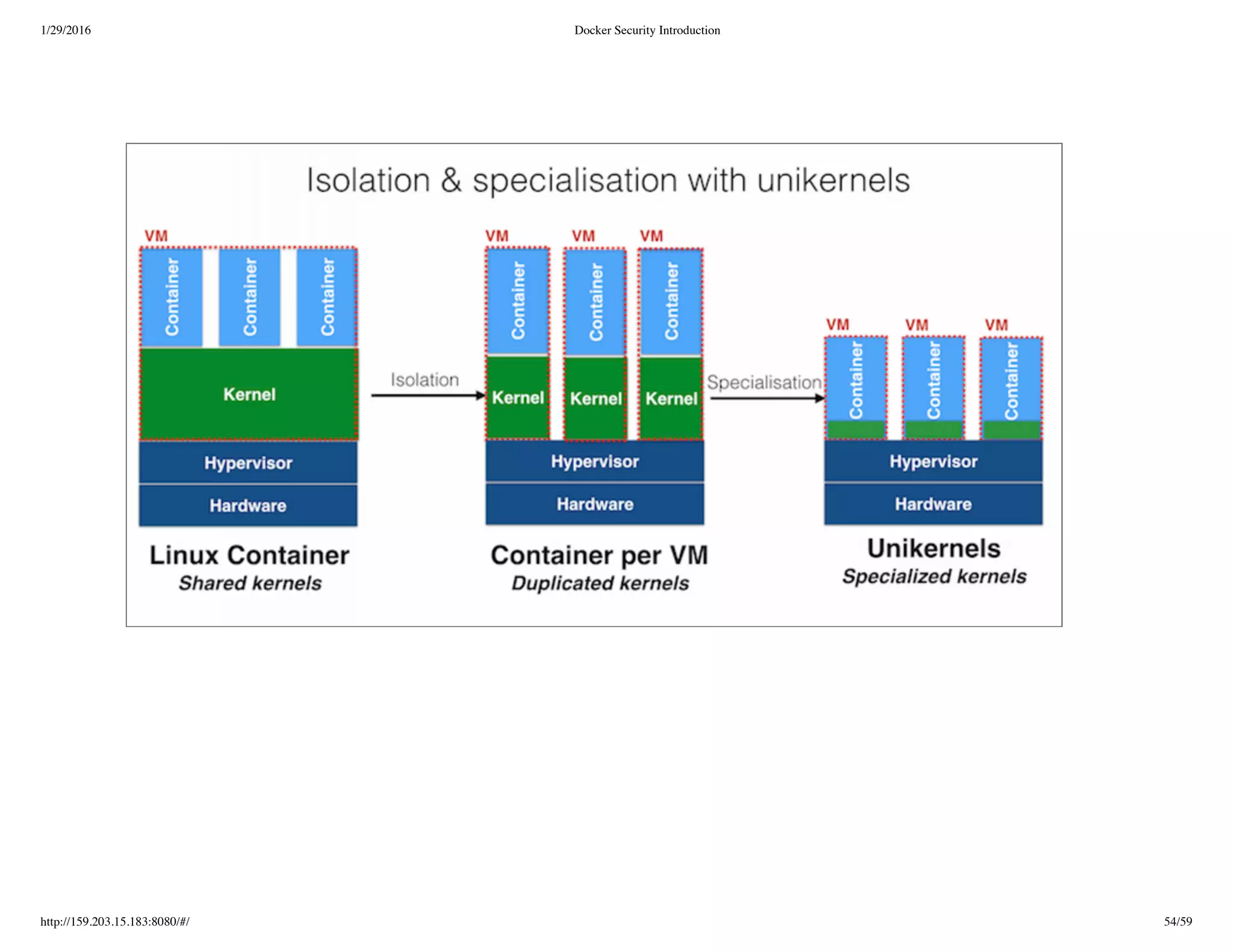
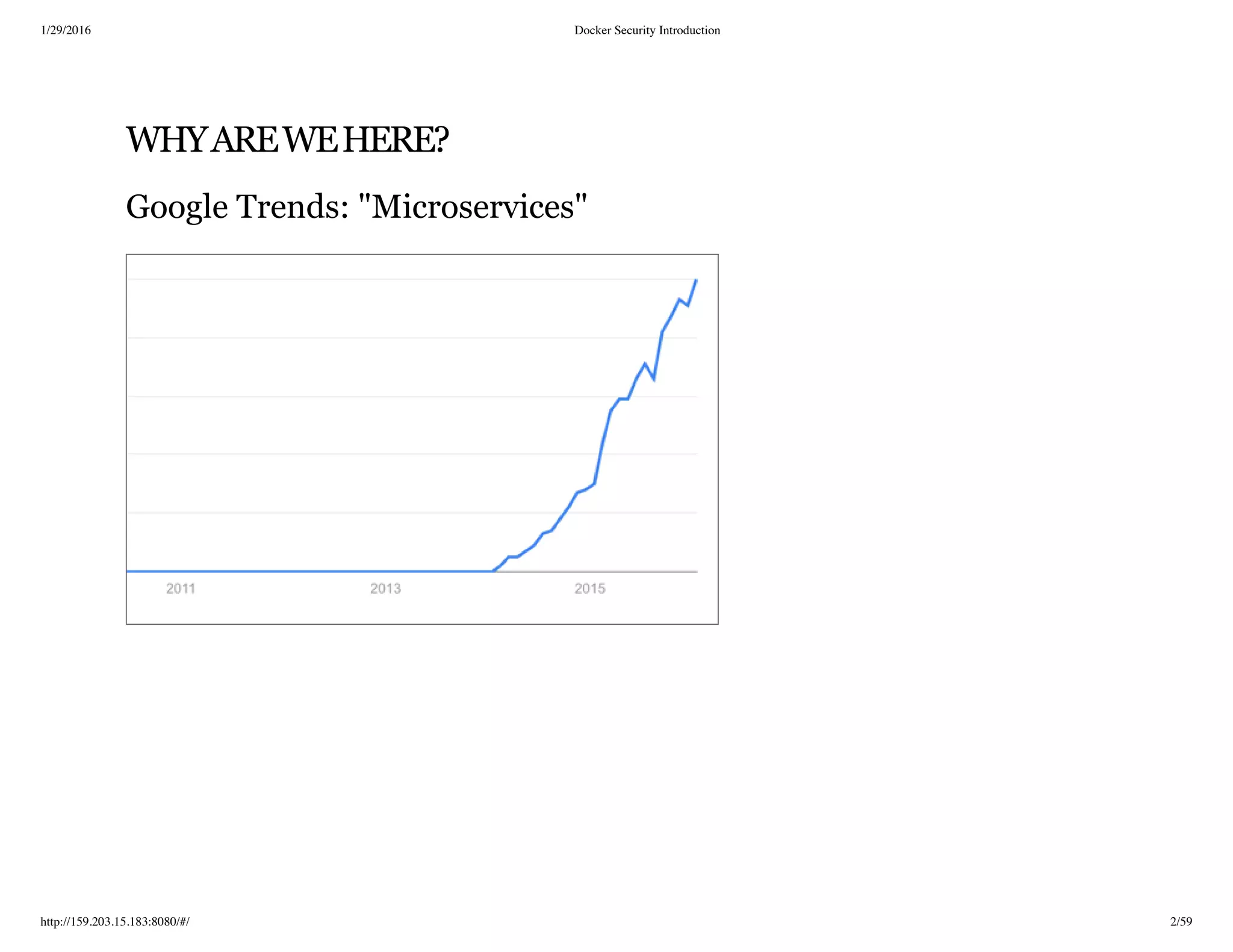
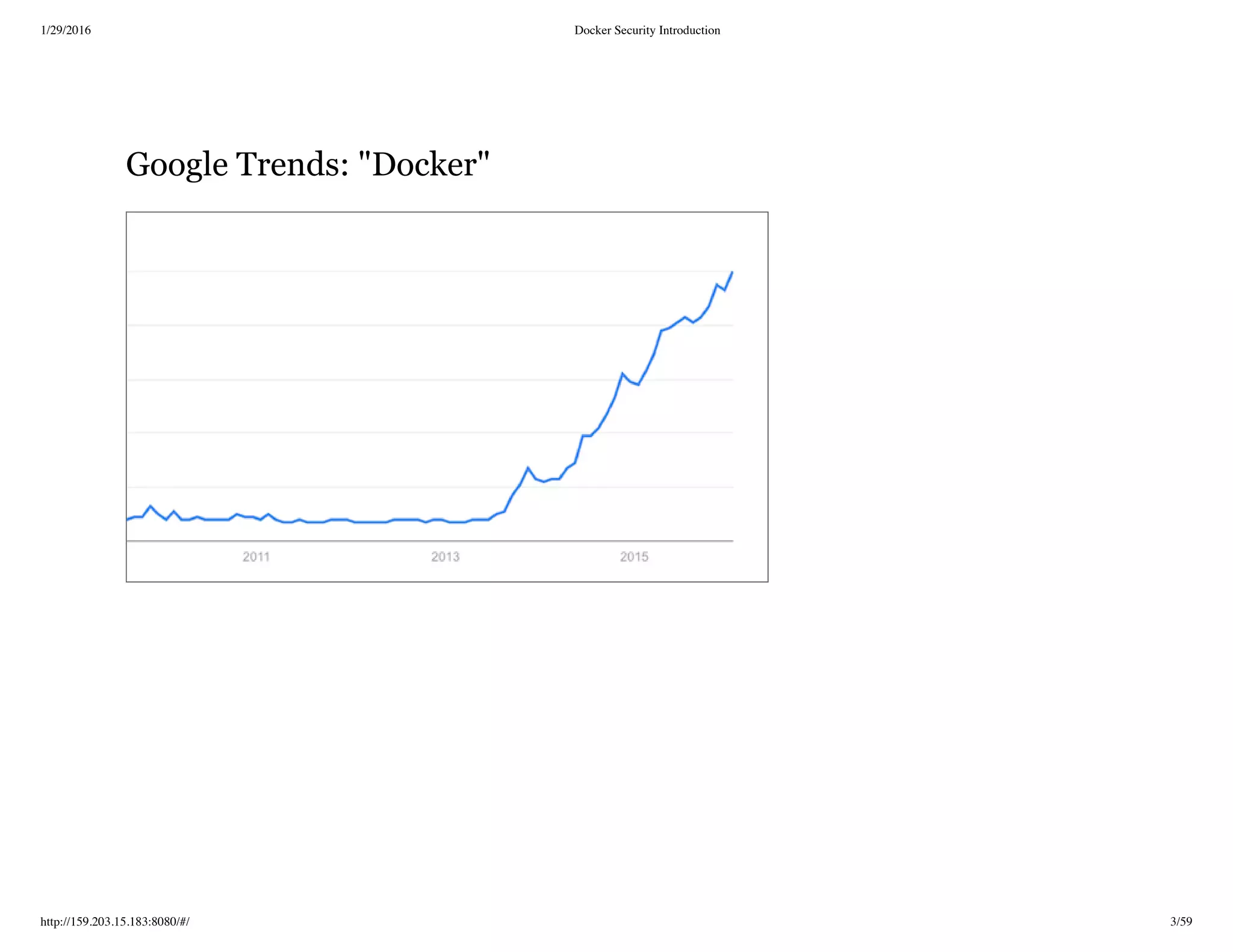
The document is a presentation on Docker security, detailing the importance and challenges of securing Docker containers and images. It covers various topics, including container versus VM isolation, best practices for security, and considerations for deploying Docker in different environments. The document also discusses operational aspects, monitoring solutions, and the future of container technology.











![1/29/2016 Docker Security Introduction
http://159.203.15.183:8080/#/ 33/59
SECURITYFORDOCKERIMAGES
Secure Registry/Mirror Access
Getting trustworthy images
trusted sources - docker hub, private registry
building secure
Docker Content Trust (1.8) [Notary]
"only signed content in production"
Yubico Keys](https://image.slidesharecdn.com/dockersecurityintroduction-160129135557/75/Docker-security-TASK-Jan-2016-28-2048.jpg)