The document discusses digital warfare, which involves using internet-based tools to compromise government systems and resources, with a historical overview from the 1980s to present. It highlights various cyber-attack methods such as malware, DDoS attacks, and advanced persistent threats, alongside notable examples like the Russia-Ukraine conflict and security recommendations for mitigating risks. Recommendations emphasize keeping systems updated, controlling access, and implementing endpoint protection to safeguard networks against potential cyber threats.


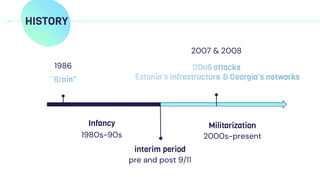
![HISTORY
Militarization
2000s-present
2007 & 2008
formation of cyber strategies and cyber
militarization around the world
reference:[2][3][4]](https://image.slidesharecdn.com/digitalwarfarebyr6-230414145222-aeb90c60/85/Digital-warfare-by-R6-pptx-4-320.jpg)
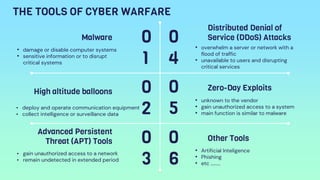








![REFERENCE
[1]Paulo Shakarian, Jana Shakarian, Andrew Ruef, Chapter 1 - Cyber Warfare: Here and Now, Editor(s): Paulo
Shakarian, Jana Shakarian, Andrew Ruef, Introduction to Cyber-Warfare, Syngress, 2013, Pages 1-8, ISBN
9780124078147, https://doi.org/10.1016/B978-0-12-407814-7.00001-4.
[2]Leyden, J. (2006, January 19). PC virus celebrates 20th birthday. The Register® - Biting the hand that feeds
IT. Retrieved February 18, 2023, from https://www.theregister.com/2006/01/19/pc_virus_at_20/
[3]Haizler, O. (2017). The United States’ cyber warfare history: Implications on modern cyber operational
structures and policymaking. Cyber, Intelligence, and Security, 1(1), 31-45.
[4]Stiennon, R. (2015). A short history of cyber warfare. In Cyber Warfare (pp. 7-32). Routledge.
[5]Norton. (n.d.). What is malware? Definition and examples. https://us.norton.com/internetsecurity-malware-
definition-examples.html
[6]Digital Guardian. (n.d.). What is a DoS attack? https://digitalguardian.com/blog/what-dos-attack
[7]Norton. (n.d.). What is phishing? How to recognize and avoid phishing scams.
https://us.norton.com/internetsecurity-online-scams-phishing-scams.html
[8]Norton. (n.d.). What is social engineering? Definition and examples. https://us.norton.com/internetsecurity-
emerging-threats-what-is-social-engineering.html
[9]Digital Guardian. (n.d.). What are advanced persistent threats (APTs)?
https://digitalguardian.com/blog/what-are-advanced-persistent-threats-apts](https://image.slidesharecdn.com/digitalwarfarebyr6-230414145222-aeb90c60/85/Digital-warfare-by-R6-pptx-17-320.jpg)
![REFERENCE
[10]CSO Online. (2019, October 28). What is cyber espionage? How nations use cyber spying against one
another. https://www.csoonline.com/article/3516924/what-is-cyber-espionage-how-nations-use-cyber-spying-
against-one-another.html
[11]Dark Reading. (2018, August 10). Physical attacks against digital infrastructure.
https://www.darkreading.com/vulnerabilities---threats/physical-attacks-against-digital-infrastructure/d/d-
id/1331589
[12]“How Does Wiper Malware Work?,” Packetlabs, Apr. 14, 2022. https://www.packetlabs.net/posts/how-
does-wiper-malware-work/ (accessed Feb. 23, 2023).
[13]“Native technologies used in Russia-Ukraine cyber attacks,” IT Brief Australia.
https://itbrief.com.au/story/native-technologies-used-in-russia-ukraine-cyber-attacks
[14]“How Does Wiper Malware Work?,” Packetlabs, Apr. 14, 2022. https://www.packetlabs.net/posts/how-
does-wiper-malware-work/ (accessed Feb. 23, 2023).
[15]“Native technologies used in Russia-Ukraine cyber attacks,” IT Brief Australia.
https://itbrief.com.au/story/native-technologies-used-in-russia-ukraine-cyber-attacks
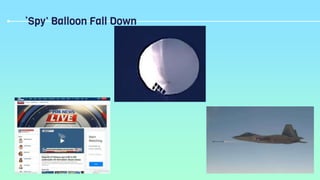
[16]High-Altitude Balloon.” Wikipedia, Wikimedia Foundation, 13 Feb. 2023,
https://en.wikipedia.org/wiki/High-altitude_balloon.](https://image.slidesharecdn.com/digitalwarfarebyr6-230414145222-aeb90c60/85/Digital-warfare-by-R6-pptx-18-320.jpg)