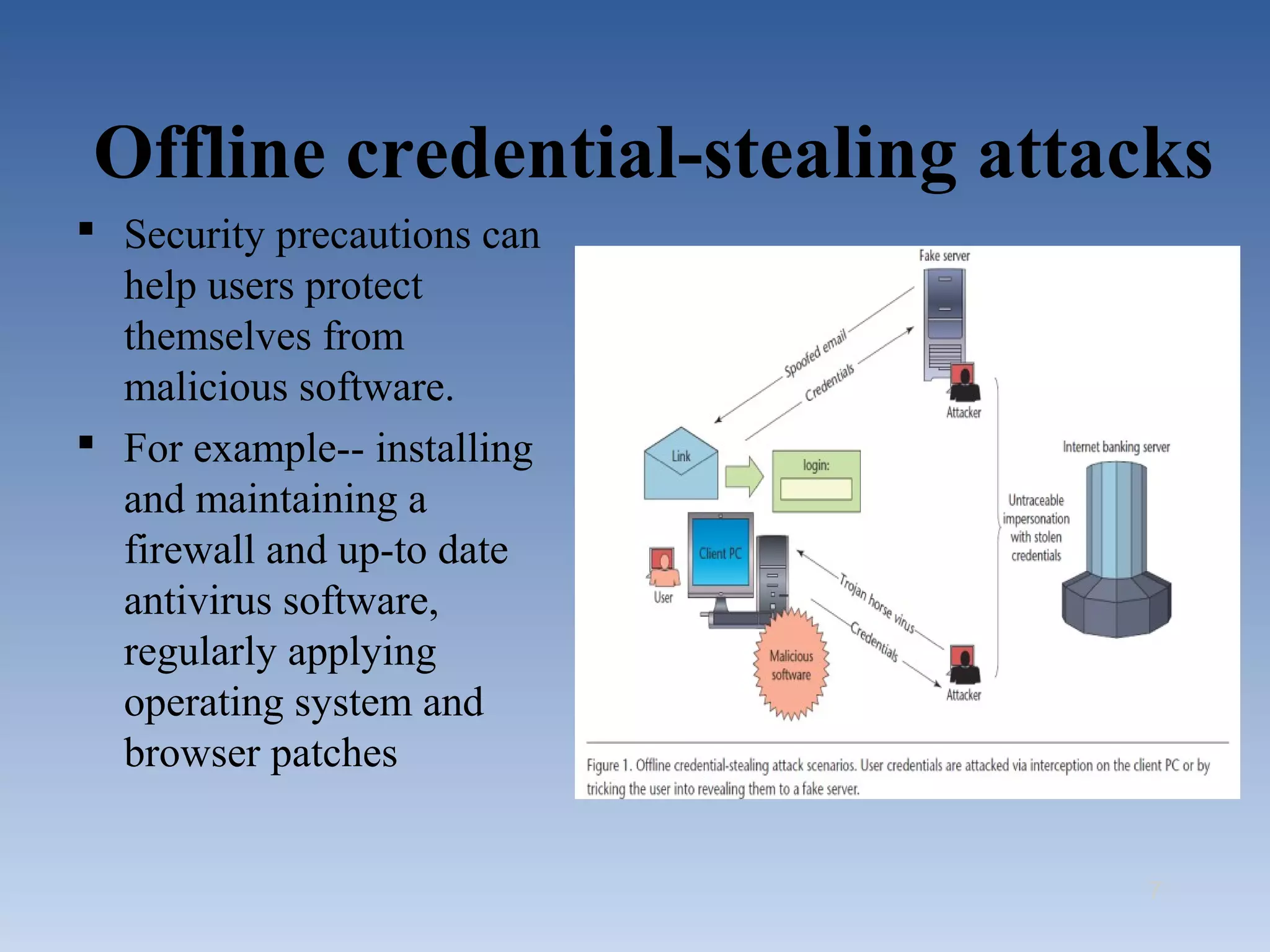
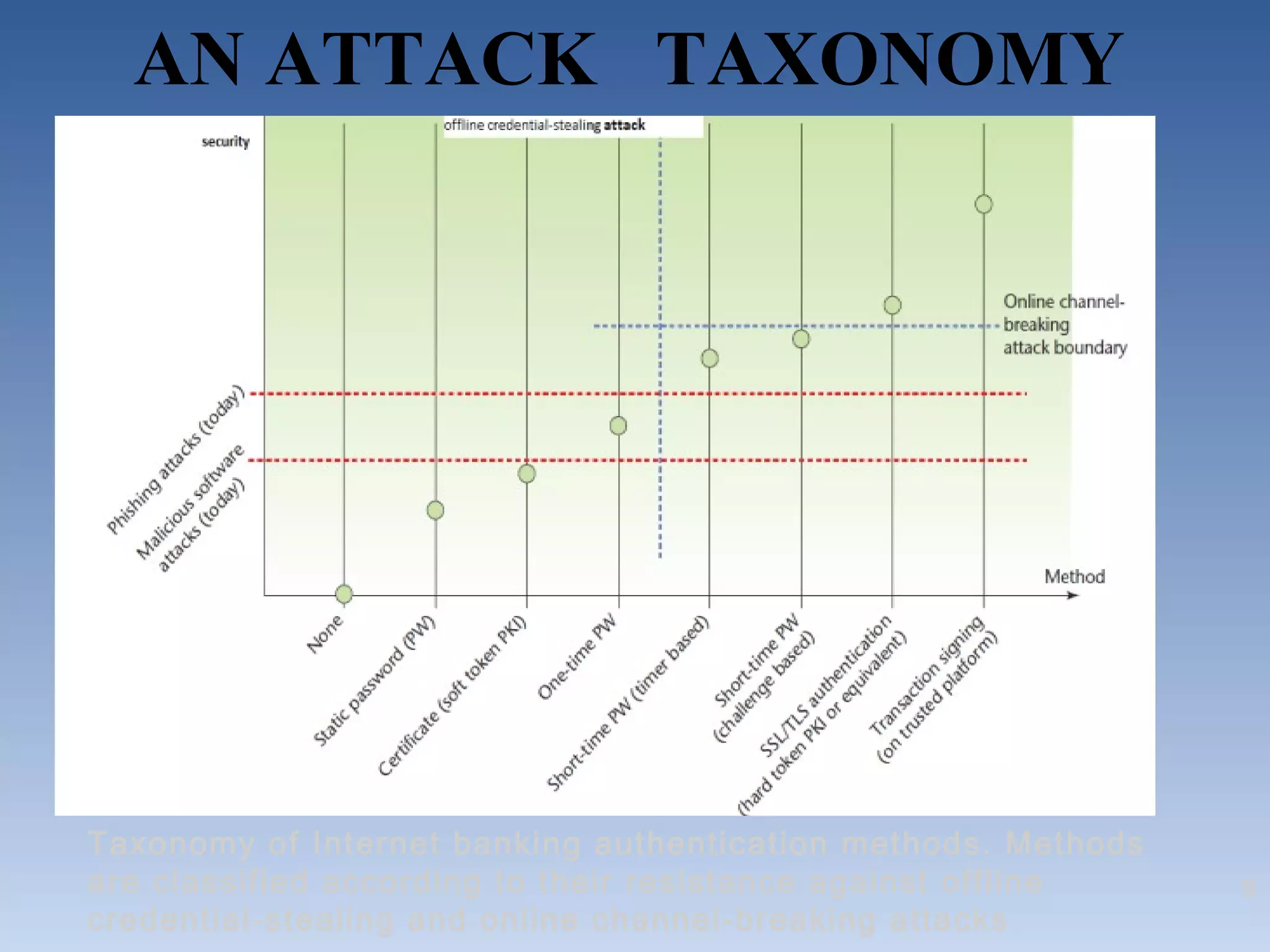
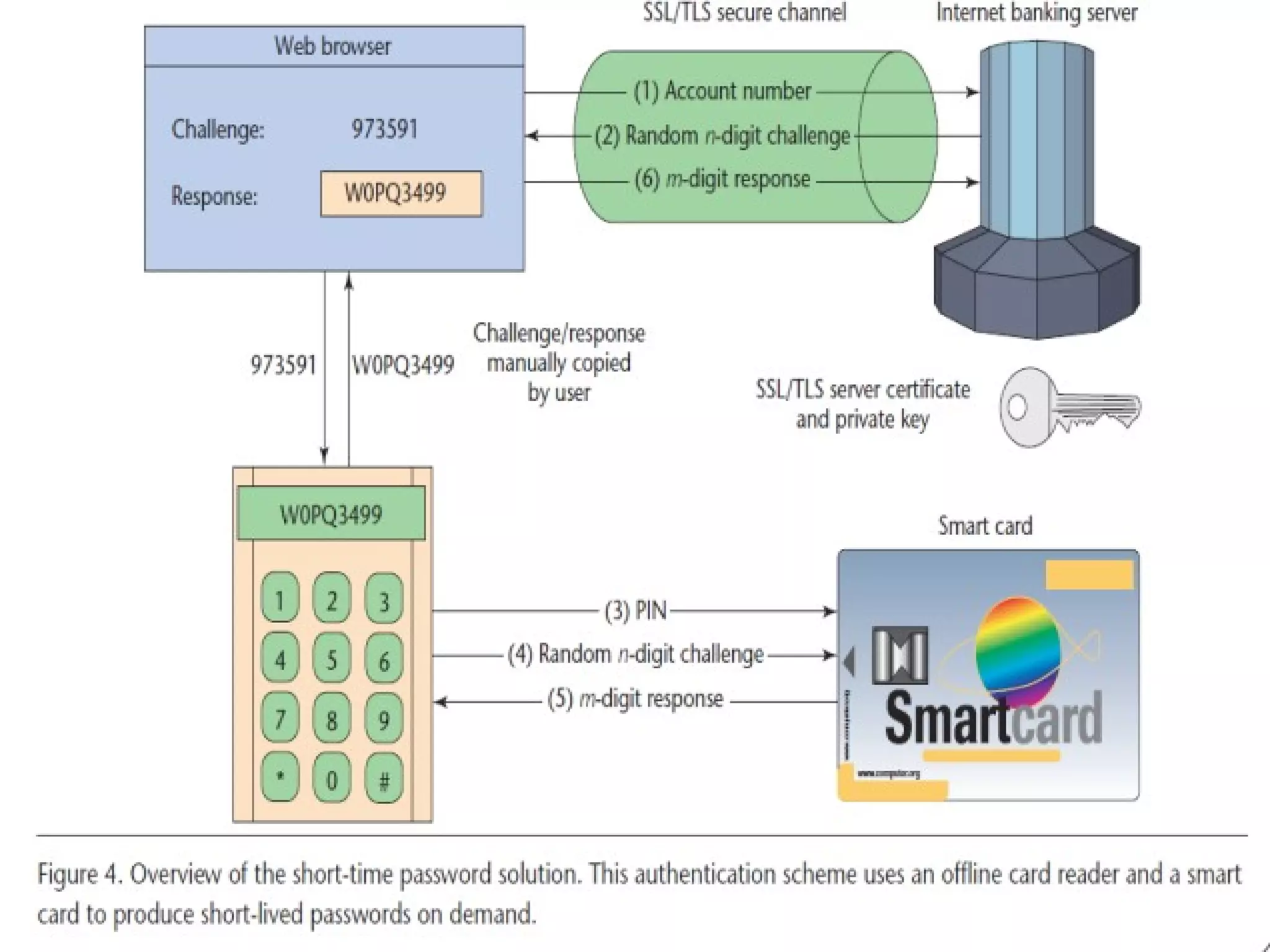
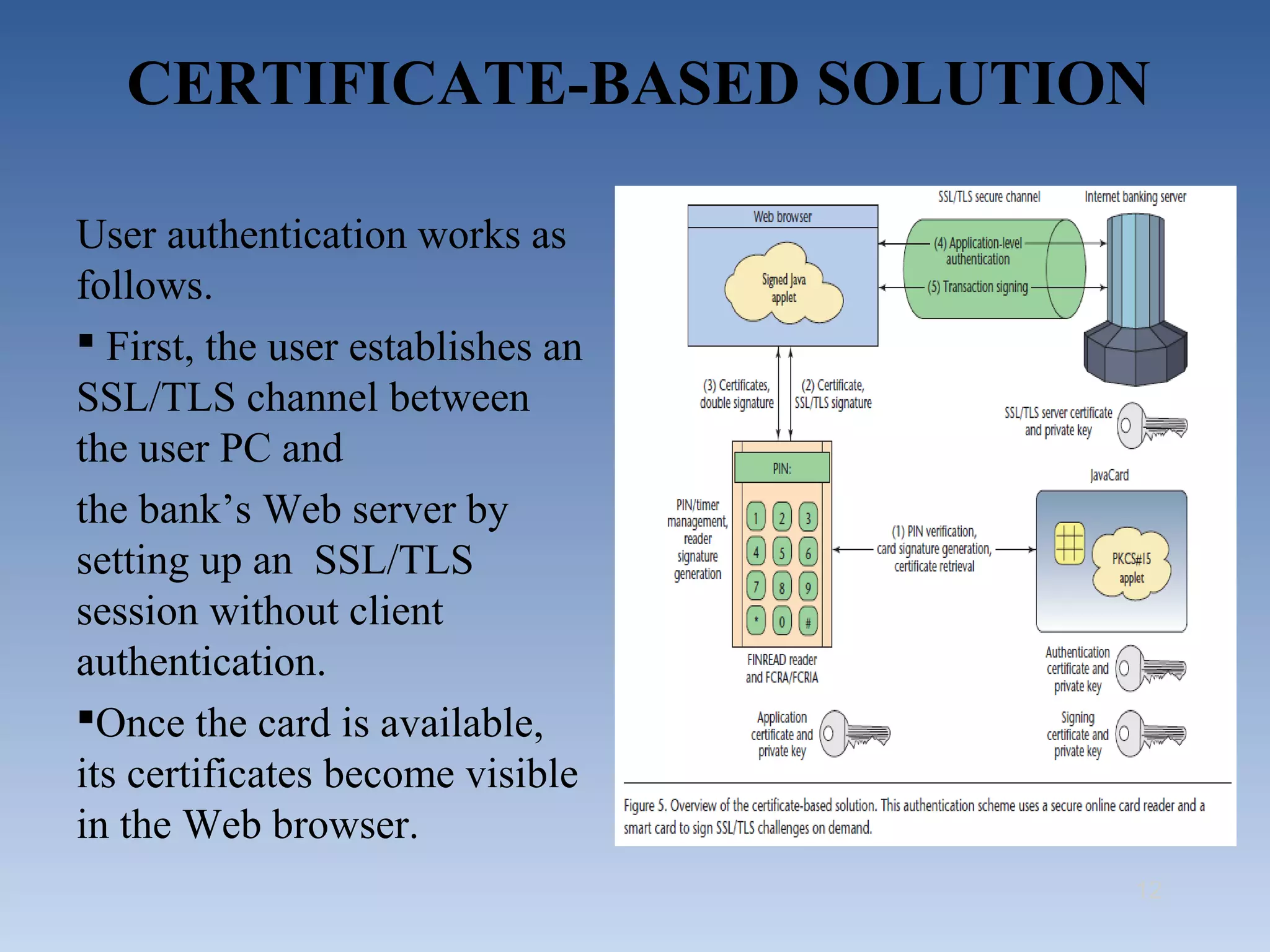
This document summarizes two proposed solutions for secure internet banking authentication - one based on short-time passwords and the other on certificates. It begins by outlining the objectives, describing common attacks on authentication like offline credential stealing and online channel breaking. It then details how each solution works, providing security against such attacks through symmetric cryptography and hardware security modules for short-time passwords and SSL/TLS sessions and browser certificates for the certificate-based approach. The document concludes that while both solutions offer high security now, certificate-based e-IDs may become a more attractive long-term solution.