This document discusses dependency injection, including:
- Dependency injection is a technique for loosely coupling code through composition rather than inheritance and programming to interfaces rather than implementations.
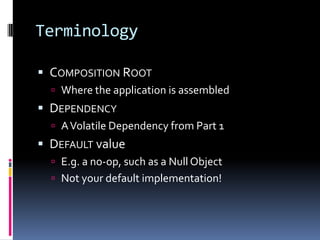
- Volatile dependencies that introduce external configuration or are still in development should be injected, while stable dependencies will not introduce breaking changes.
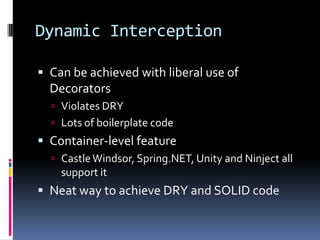
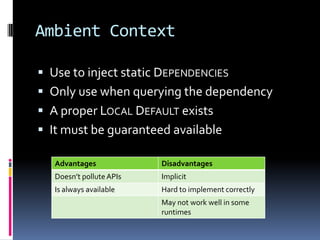
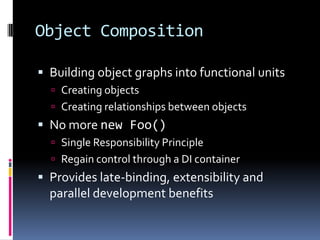
- Different patterns for dependency injection include constructor injection, property injection, method injection, and ambient context.
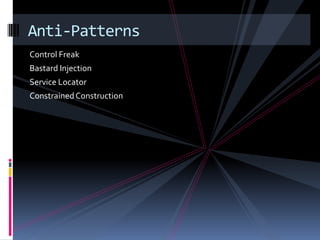
- Anti-patterns to avoid include control freak, bastard injection, service locator, and constrained construction patterns.
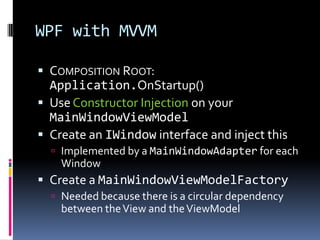
- Frameworks like ASP.NET MVC, WPF, and WCF can implement dependency injection by composing applications in places like the global.asax file, OnStartup method, and service host factories
















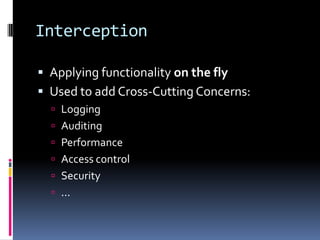
![Aspect-Oriented Programming
Cross-Cutting Concerns applied via attributes
decorating a method
[PrincipalPermission]
[HandleError]
Requires either:
Post-compilation step (e.g., PostSharp), or
A custom host (e.g.,WCF, ASP.NET MVC, NUnit)](https://image.slidesharecdn.com/dependencyinjection-130919172043-phpapp01/85/Dependency-Injection-21-320.jpg)