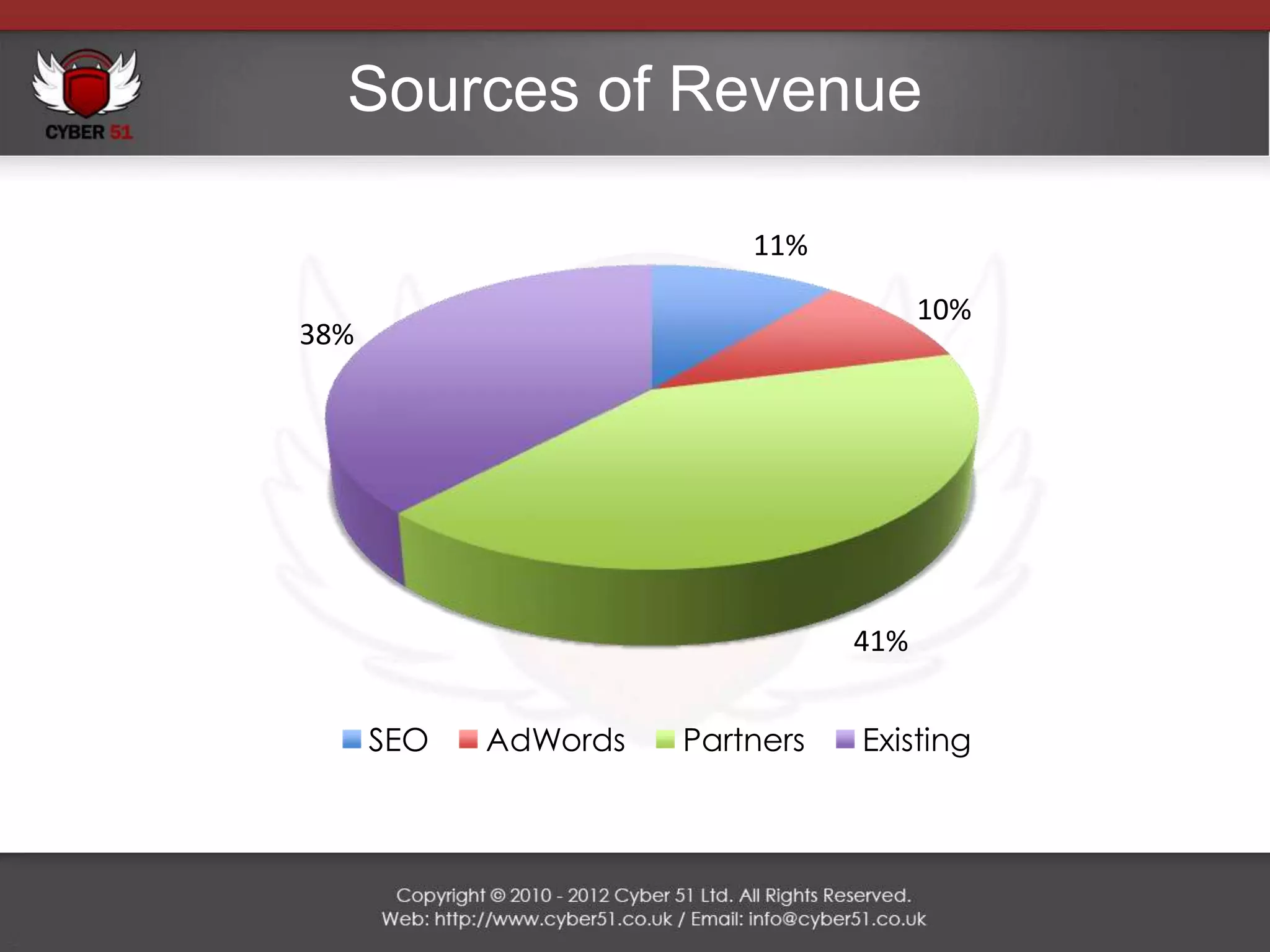
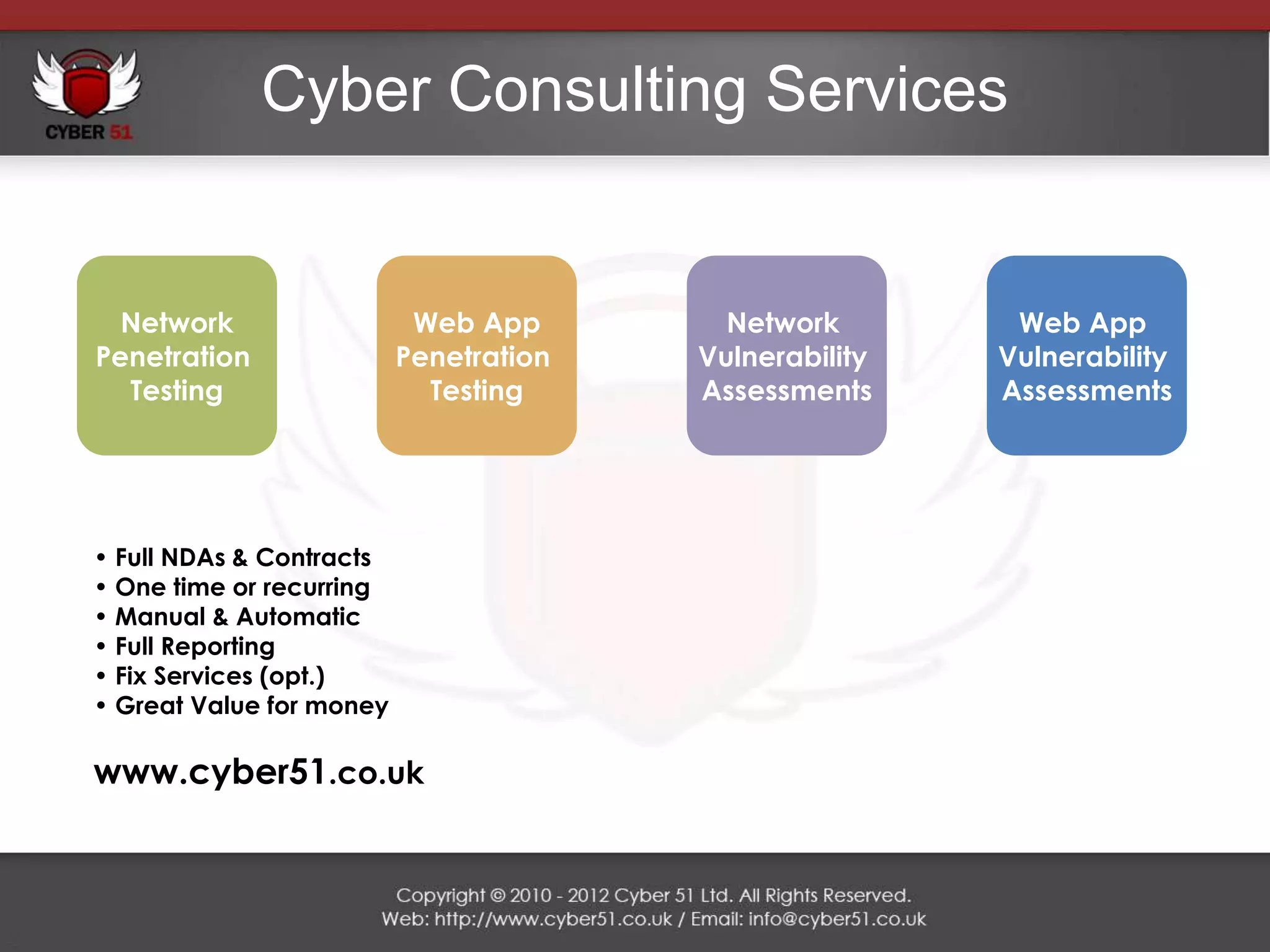
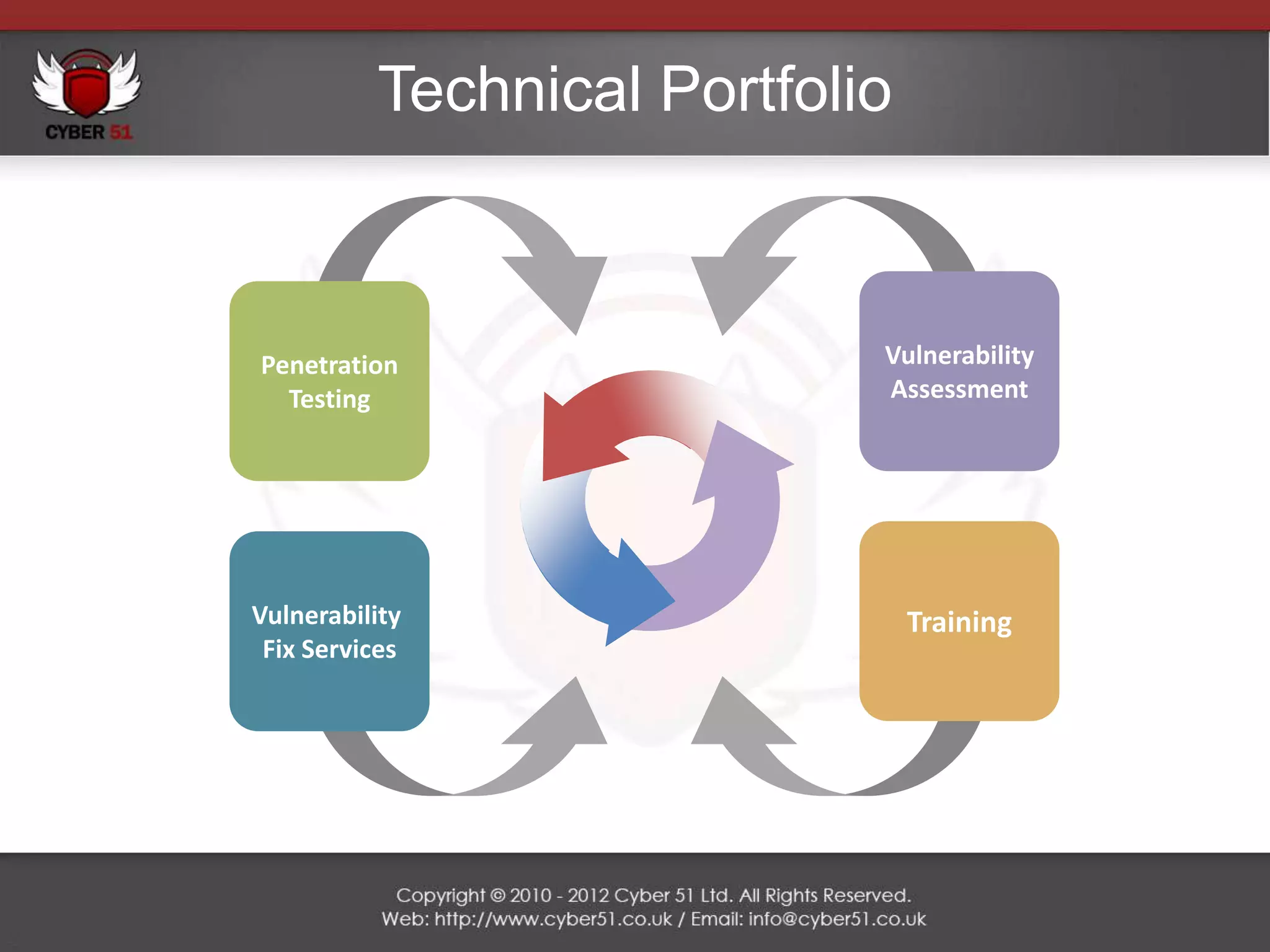
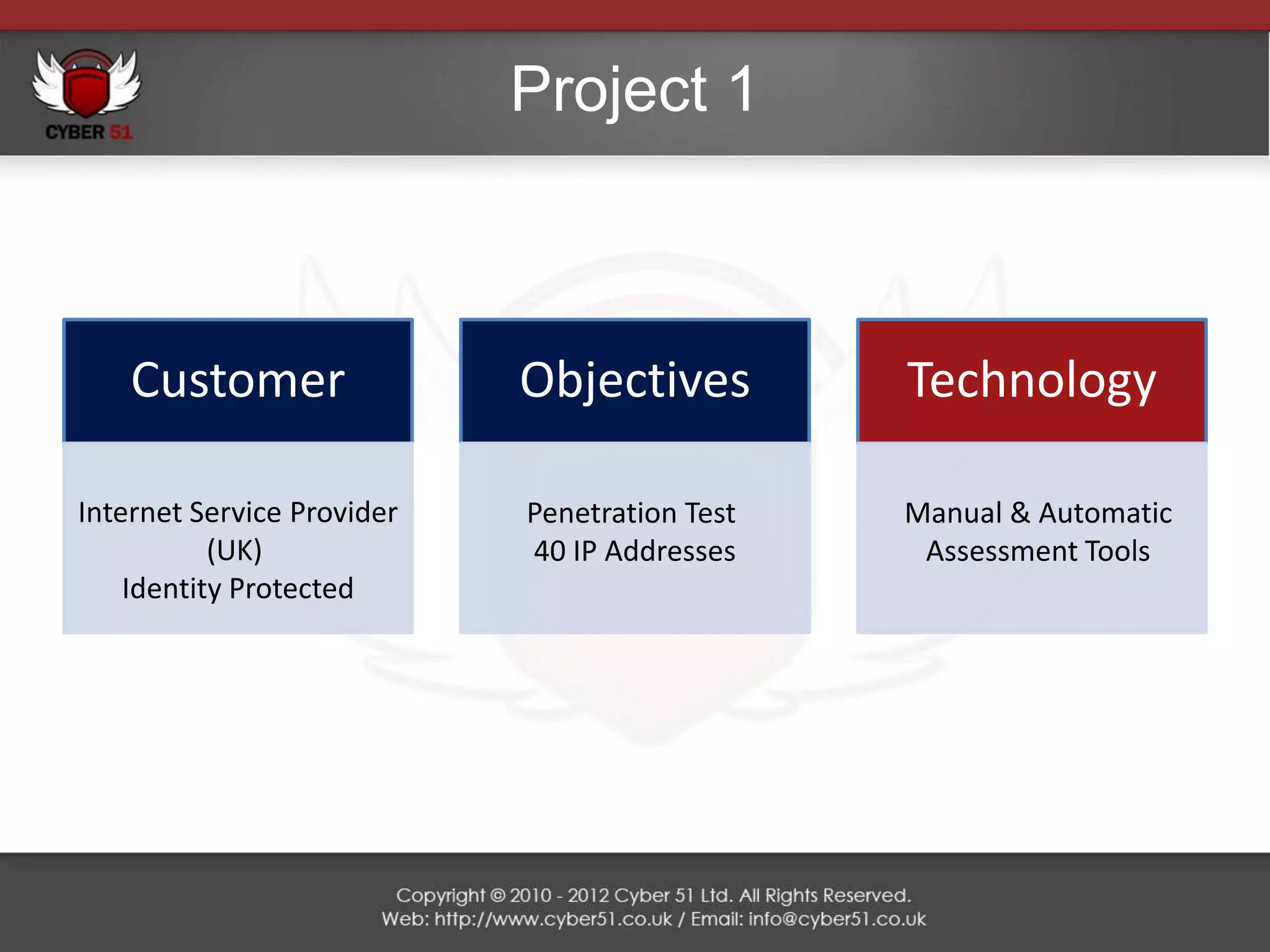
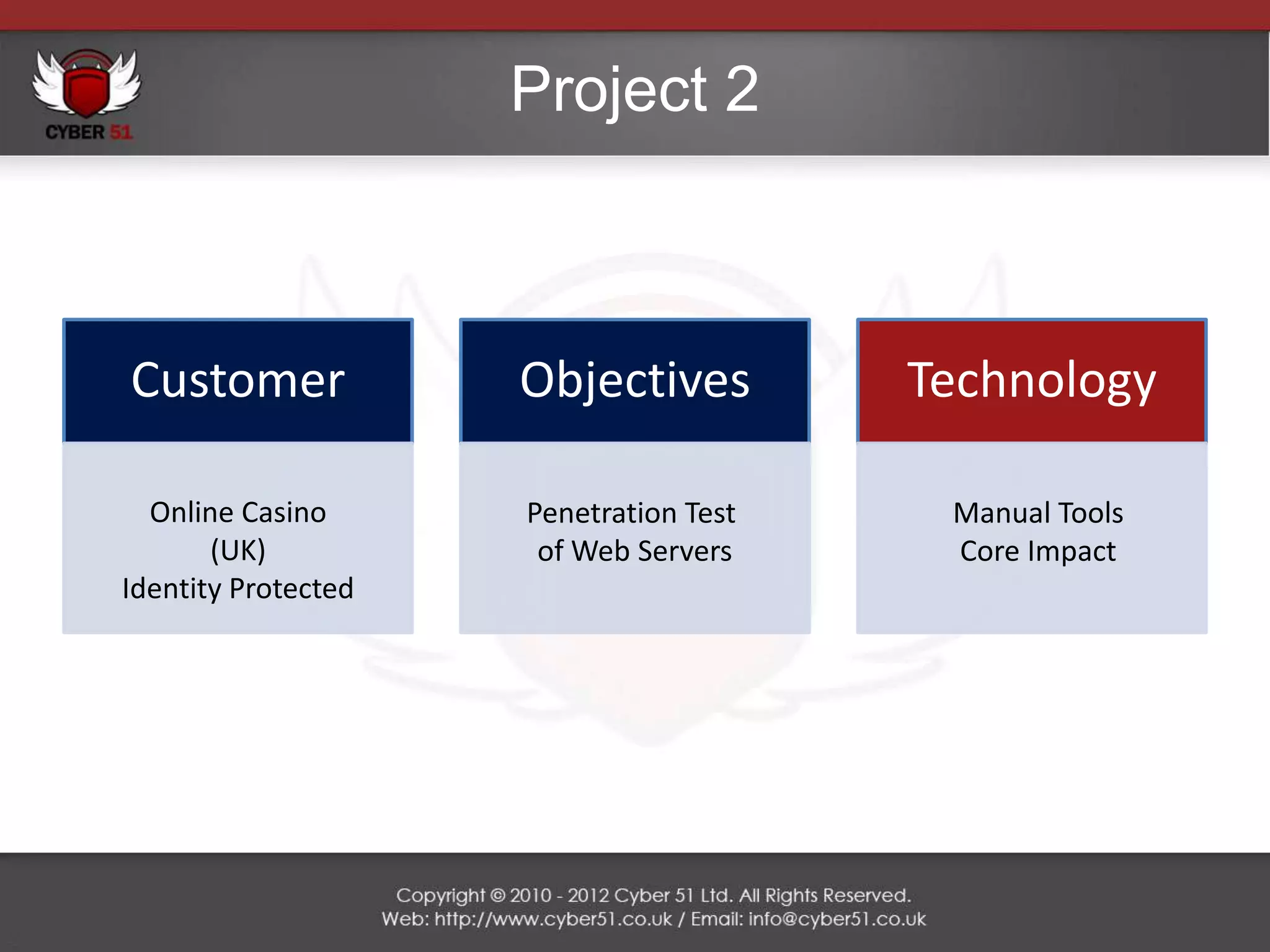
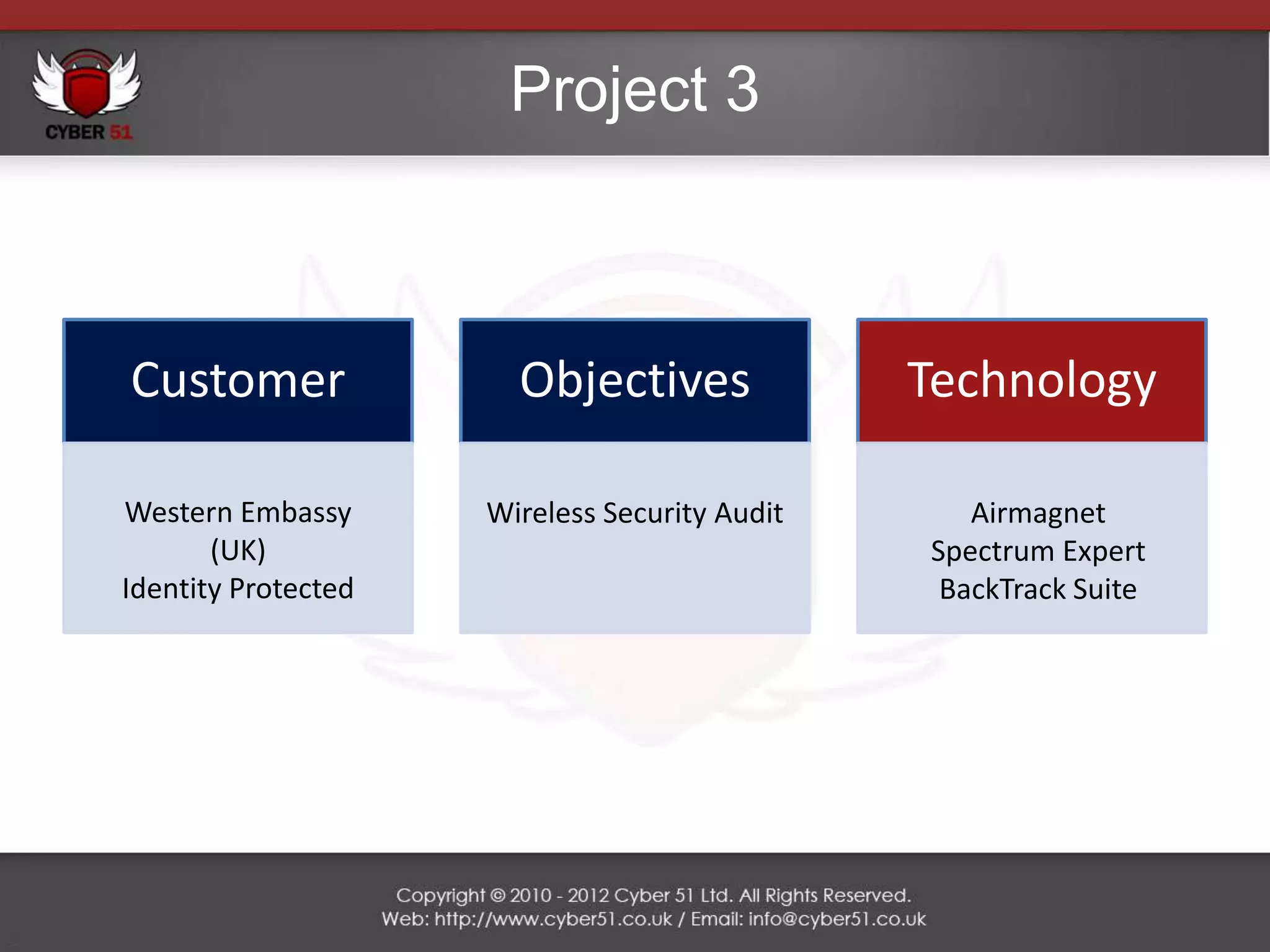
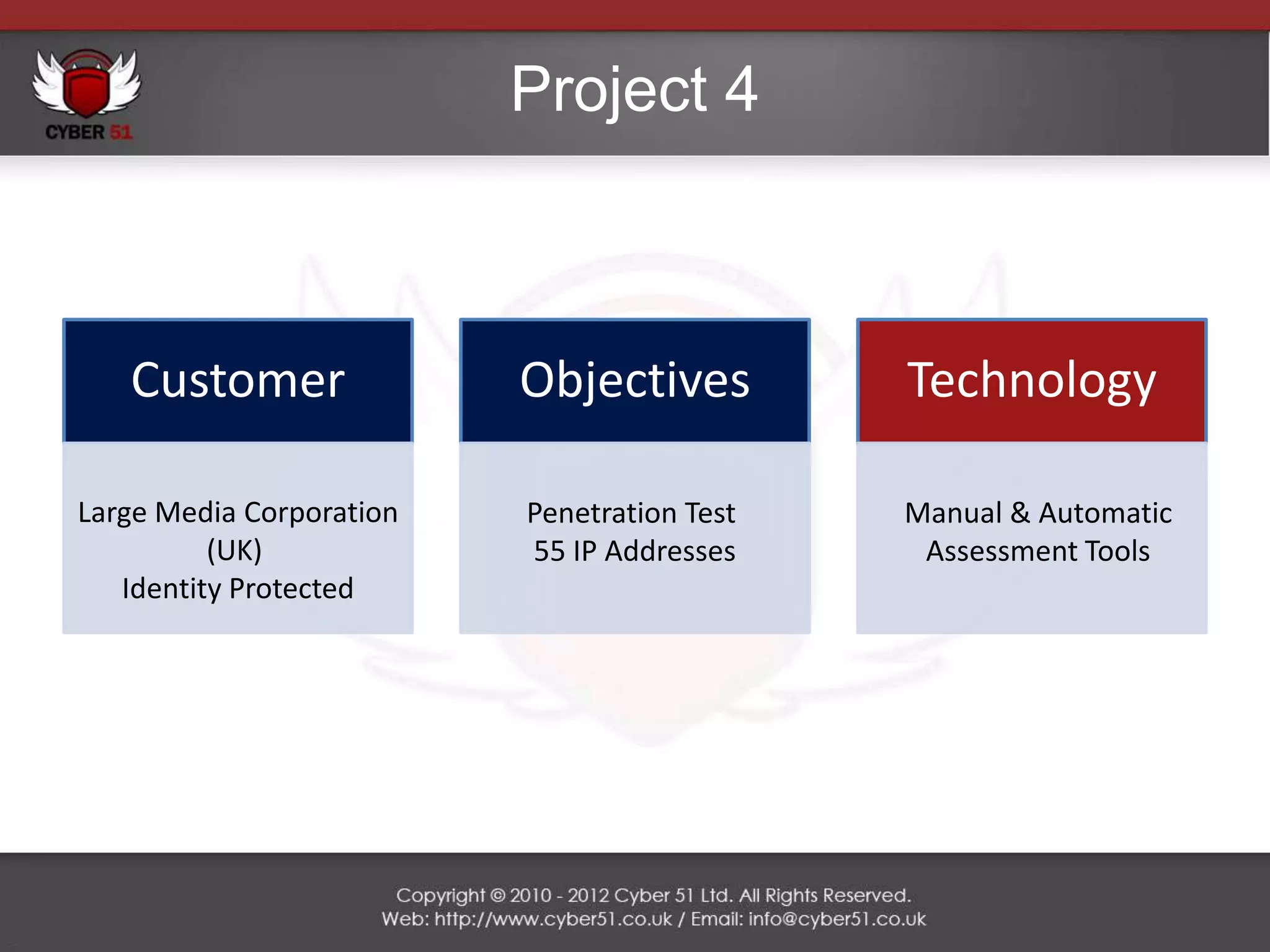
Cyber 51 is an IT security consulting firm founded in 2011 by Martin Voelk and Diego Spahn. The company has grown 114% in revenue since 2011 and now has 25 certified consultants with experience in network penetration testing, vulnerability assessments, and security training. Cyber 51 serves clients across industries like gambling, media, and financial services through manual and automated security assessments, vulnerability fixes, and tailored training programs. Recent projects include penetration tests for an internet service provider, online casino, embassy, and media corporation.