CIOs and CISOs to Help Businesses Adapt to New Cyberthreat Landscape
•
0 likes•494 views
It will be up to CIOs and CISOs to help businesses adapt to new security threats in 2017, according to 66% of business decision makers and 65% of IT decision makers. While CIOs and CISOs are seen as leaders on security issues, 91% of CEOs and 83% of business decision makers believe their own actions could pose security risks to their organizations. Many enterprises have suffered breaches in the last 18 months, with 51% of business decision makers and 45% of IT decision makers admitting their companies have experienced recent breaches.
Report
Share
Report
Share
Download to read offline
Recommended
Automobile comapanies and institutions can boost safety and security with Bio...

Automobile comapanies and institutions can boost safety and security with Bio...Star Link Communication Pvt Ltd
More Related Content
Similar to CIOs and CISOs to Help Businesses Adapt to New Cyberthreat Landscape
Automobile comapanies and institutions can boost safety and security with Bio...

Automobile comapanies and institutions can boost safety and security with Bio...Star Link Communication Pvt Ltd
Similar to CIOs and CISOs to Help Businesses Adapt to New Cyberthreat Landscape (20)
Cybersecurity Compliance can Make or Break Your Business - DigiCert - Symantec

Cybersecurity Compliance can Make or Break Your Business - DigiCert - Symantec
CompTIA Second Annual Trends in Enterprise Mobility: BYOD Uncovered

CompTIA Second Annual Trends in Enterprise Mobility: BYOD Uncovered
SMB IT CONFIDENCE INDEX from Symantec™ | RapidSSLOnline

SMB IT CONFIDENCE INDEX from Symantec™ | RapidSSLOnline
Tech Update Summary from Blue Mountain Data Systems June 2015

Tech Update Summary from Blue Mountain Data Systems June 2015
Cyber Security, User Interface, and You - Deloitte CIO - WSJ

Cyber Security, User Interface, and You - Deloitte CIO - WSJ
Cyber Security, User Interface, and You - Deloitte CIO - WSJ

Cyber Security, User Interface, and You - Deloitte CIO - WSJ
Automobile comapanies and institutions can boost safety and security with Bio...

Automobile comapanies and institutions can boost safety and security with Bio...
ciso-platform-annual-summit-2013-ciso assessment exec summary _ibm

ciso-platform-annual-summit-2013-ciso assessment exec summary _ibm
FOSE: Perspectives on Mobility & BYOD in the Government Market

FOSE: Perspectives on Mobility & BYOD in the Government Market
Will factory cybersecurity keep up with the accelerating IoT.docx

Will factory cybersecurity keep up with the accelerating IoT.docx
Cisco IoT World Forum 2014: Airwatch Breakout Session

Cisco IoT World Forum 2014: Airwatch Breakout Session
KEY TAKEAWAYS FROM SATYA NADELLA’S KEYNOTE AT MICROSOFT IGNITE 2018, ORLANDO

KEY TAKEAWAYS FROM SATYA NADELLA’S KEYNOTE AT MICROSOFT IGNITE 2018, ORLANDO
More from Code42
More from Code42 (6)
Insider Threat: Protect Yourself from Departing Employees

Insider Threat: Protect Yourself from Departing Employees
The New Threat on Campus: Ransomware Locks Down Education

The New Threat on Campus: Ransomware Locks Down Education
How to Spot the 6 Archetypes of Insider Exfiltration

How to Spot the 6 Archetypes of Insider Exfiltration
The New Threat on Campus: Ransomware Locks Down Education

The New Threat on Campus: Ransomware Locks Down Education
Recently uploaded
VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS...

VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS...Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE AbudhabiAbortion pills in Kuwait Cytotec pills in Kuwait
Recently uploaded (20)
9599632723 Top Call Girls in Delhi at your Door Step Available 24x7 Delhi

9599632723 Top Call Girls in Delhi at your Door Step Available 24x7 Delhi
Call Girls in Delhi, Escort Service Available 24x7 in Delhi 959961-/-3876

Call Girls in Delhi, Escort Service Available 24x7 in Delhi 959961-/-3876
Enhancing and Restoring Safety & Quality Cultures - Dave Litwiller - May 2024...

Enhancing and Restoring Safety & Quality Cultures - Dave Litwiller - May 2024...
KYC-Verified Accounts: Helping Companies Handle Challenging Regulatory Enviro...

KYC-Verified Accounts: Helping Companies Handle Challenging Regulatory Enviro...
Call Girls In Panjim North Goa 9971646499 Genuine Service

Call Girls In Panjim North Goa 9971646499 Genuine Service
VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS...

VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS...
0183760ssssssssssssssssssssssssssss00101011 (27).pdf

0183760ssssssssssssssssssssssssssss00101011 (27).pdf
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi
Boost the utilization of your HCL environment by reevaluating use cases and f...

Boost the utilization of your HCL environment by reevaluating use cases and f...
MONA 98765-12871 CALL GIRLS IN LUDHIANA LUDHIANA CALL GIRL

MONA 98765-12871 CALL GIRLS IN LUDHIANA LUDHIANA CALL GIRL
The Coffee Bean & Tea Leaf(CBTL), Business strategy case study

The Coffee Bean & Tea Leaf(CBTL), Business strategy case study
CIOs and CISOs to Help Businesses Adapt to New Cyberthreat Landscape
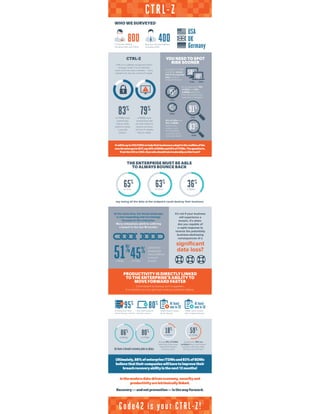
- 1. ItwillbeuptoCIO/CISOstohelptheirbusinessesadapttotherealitiesofthe newthreatscapein2017,say66%ofBDMsand65%ofITDMs.Thequestionis, ifnottheCIOorCISO,thenwhoshouldtakeleadershiponthisfront? CTRL-Z 800 400IT Decision Makers, including CIOs and CISOs Business Decision Makers, including CEOs WHO WE SURVEYED CTRL-Z CTRL-Z is a globally recognised means of saying “undo.” It is an instinctive action when we make a mistake — and a metaphor for security, control and agility. 83% 79% of ITDMs have wished they had an undo button to erase a security breach. of BDMs have wished they had an undo button to remove all traces of of an IT mistake they’ve made. YOU NEED TO SPOT RISK SOONER According to ITDMs and BDMs, almost half of all corporate data is held on endpoint devices. 50% 49% At the same time, 75% of CEOs and 52% of BDMs admit that they use unauthorized applications/ programs. 75% ITDMs BDMs CEOs 52% BDMs 91% of CEOs and 83% of BDMs believe their actions could be considered a security risk to their organization. 91% CEOs 83% BDMs USA UK Germany THE ENTERPRISE MUST BE ABLE TO ALWAYS BOUNCE BACK 65% 63% 36% of CIOs of CEOs of BDMs say losing all the data at the endpoint could destroy their business. At the same time, the threat landscape is ever-expanding and increasingly focused on the enterprise. Many enterprises admit to suffering a breach in the last 18 months: 51% 45% of BDMs of ITDMs It’s not if your business will experience a breach, it’s when. Are you capable of a rapid response to reverse the potentially business-destroying consequences of a significant data loss?admit their companies have suffered a recent breach. PRODUCTIVITY IS DIRECTLY LINKED TO THE ENTERPRISE’S ABILITY TO MOVE FORWARD FASTER Commitment to backup isn’t in question. It is whether you can get back what you lost that matters. 95% of enterprises have server backup in place. 80% also have endpoint backup in place. ITDMs haven’t tested server backup. At least one in 20 ITDMs haven’t tested their endpoint backup. At least one in 10 do have a breach recoveryplan in place. 86% of BDMs 80% of ITDMs 18% of BDMs 59% of ITDMs At least 18% of ITDMs admit they have never tested their breach recovery plans. Despite this, 59% are confident they could restore business continuity within 24 hours, but can they? Ultimately,88%ofenterpriseITDMsand83%ofBDMs believethattheircompanieswillhavetoimprovetheir breachrecoveryabilityinthenext12months! Inthemoderndata-driveneconomy,securityand productivityareintrinsicallylinked. Recovery—andnotprevention—isthewayforward. Code42 is your CTRL-Z!
