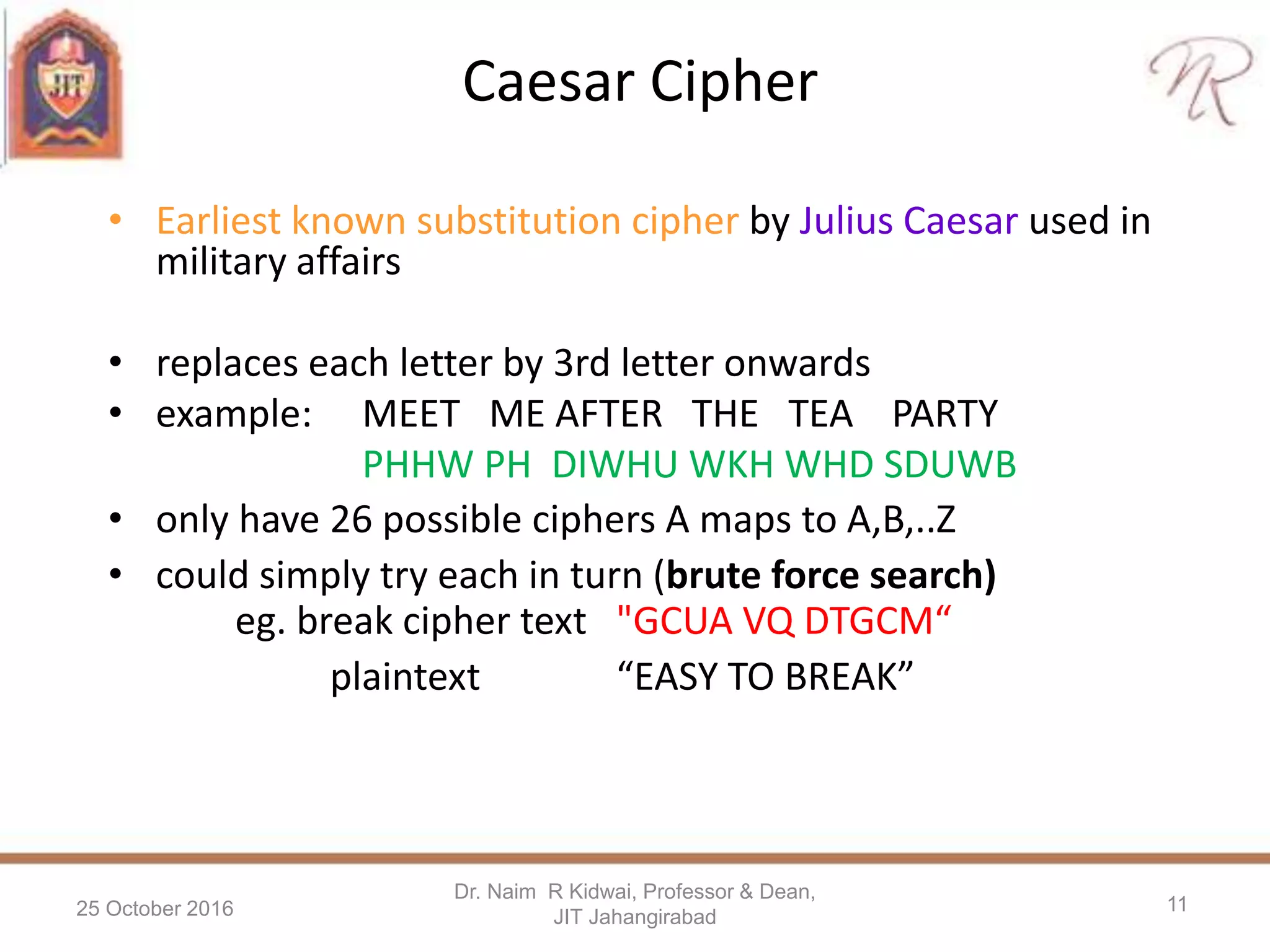
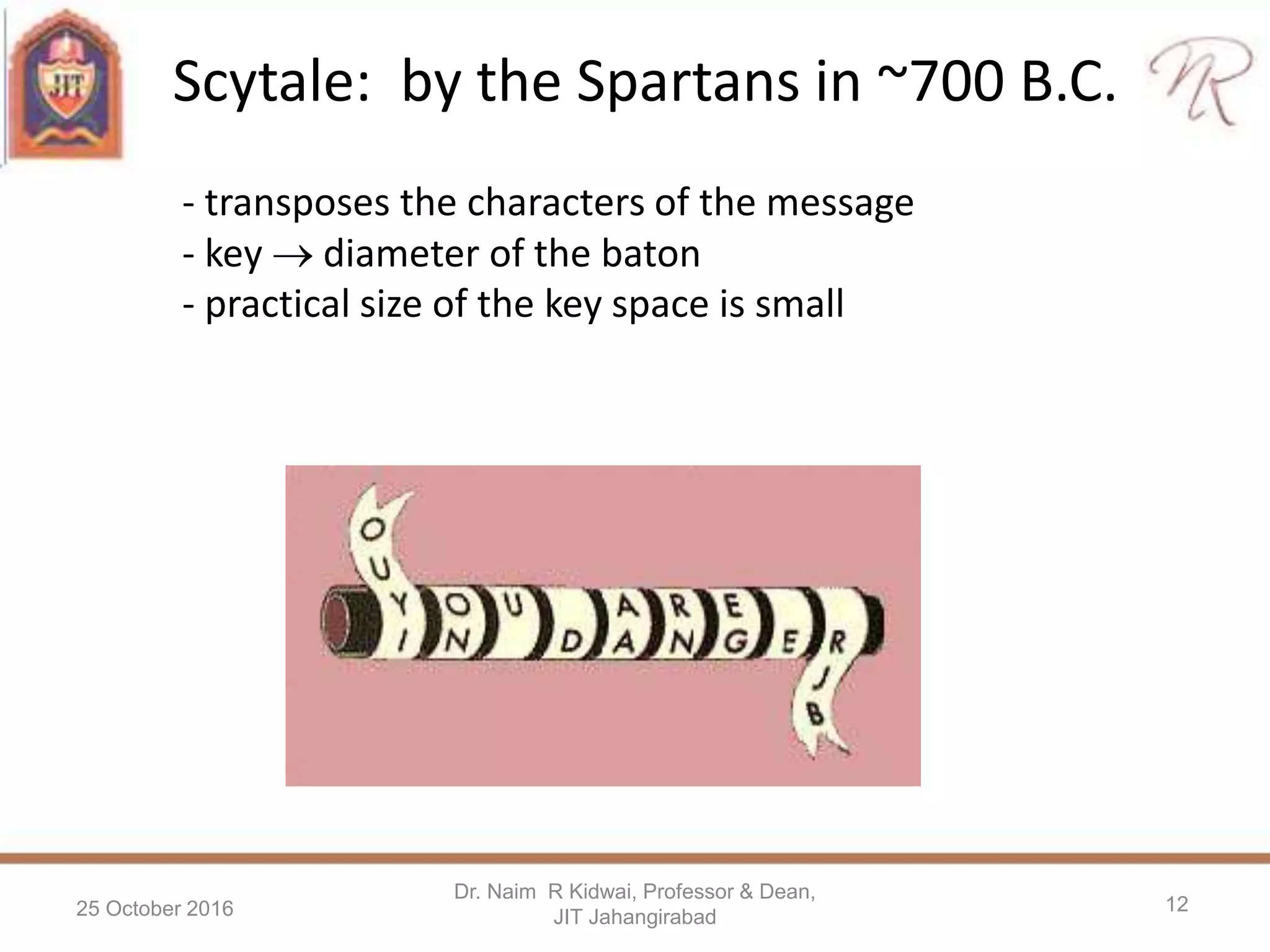
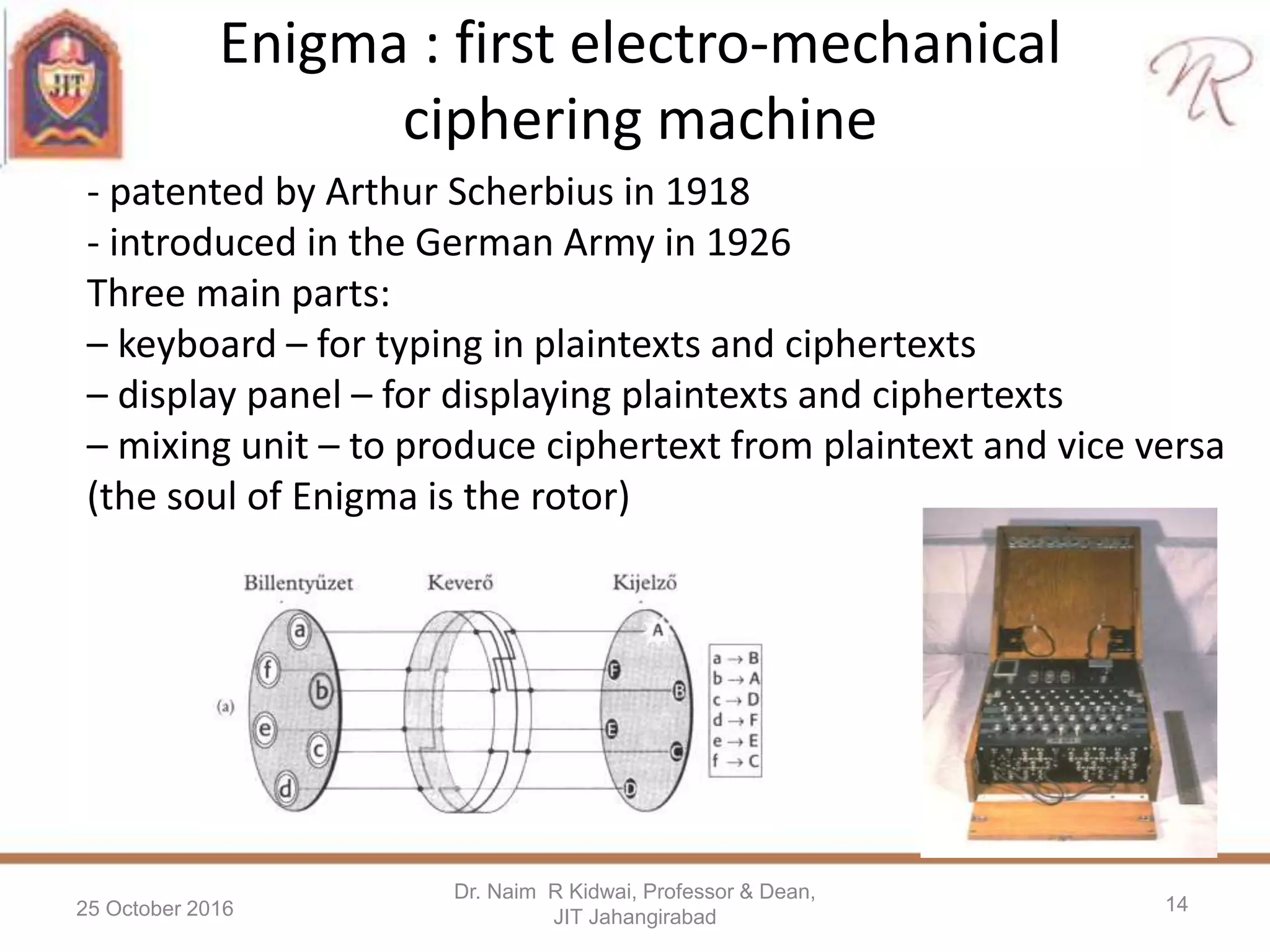
The presentation by Dr. Naim R. Kidwai discusses the critical role of cryptography in protecting information in the digital era, emphasizing concepts such as encryption, decryption, and key management. It highlights the essential goals of cryptography including authentication, confidentiality, data integrity, and non-repudiation, and provides examples of historical ciphers and modern techniques like symmetric and asymmetric key cryptography. Additionally, the document addresses common threats to information security and the importance of key size in determining the security of encryption methods.

![Asymmetric (Public Key) Cryptography Ex.
25 October 2016
Dr. Naim R Kidwai, Professor & Dean,
JIT Jahangirabad
20
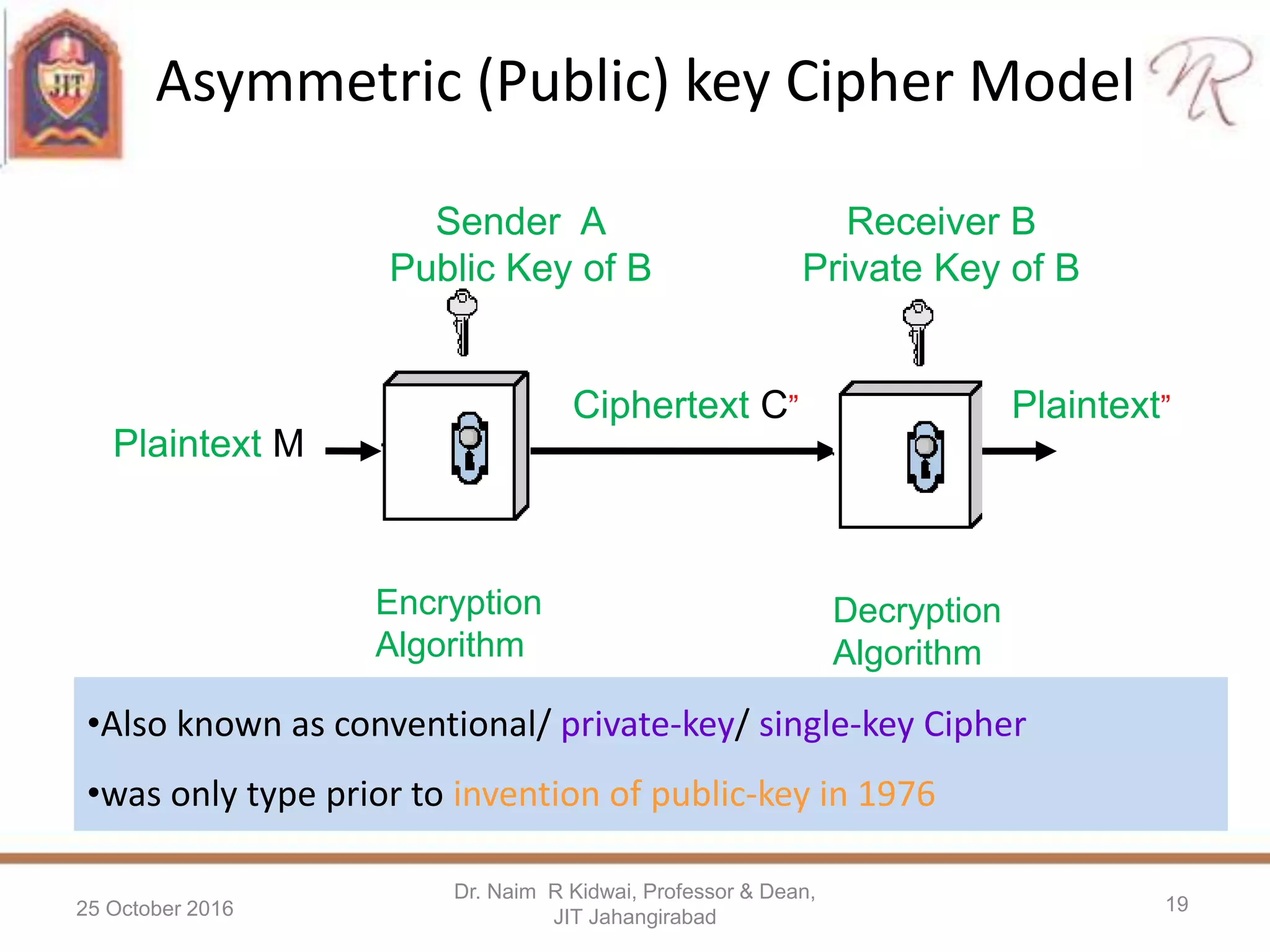
Private Key d
e*d=1 mod[(p-1)*(q-1)]
7d=1mod(12*18)
7d=1mod(216)
d=31
Public Key
N=247
e=7
Encryption
Plaintext : 4
Encryption C=Me mod[N]
C=47mod(247)
C = 16384 mod(247)
Ciphertext =82
Let N=p x q, N=247, p=13, q=19 a prime number
Pick another prime number e=7
Decryption
Ciphertext: 82
M=Cd mod[N]
M=8231mod(247)
M=4](https://image.slidesharecdn.com/jitschvisitcryptography-161025135742/75/Cryptography-and-Information-Security-20-2048.jpg)