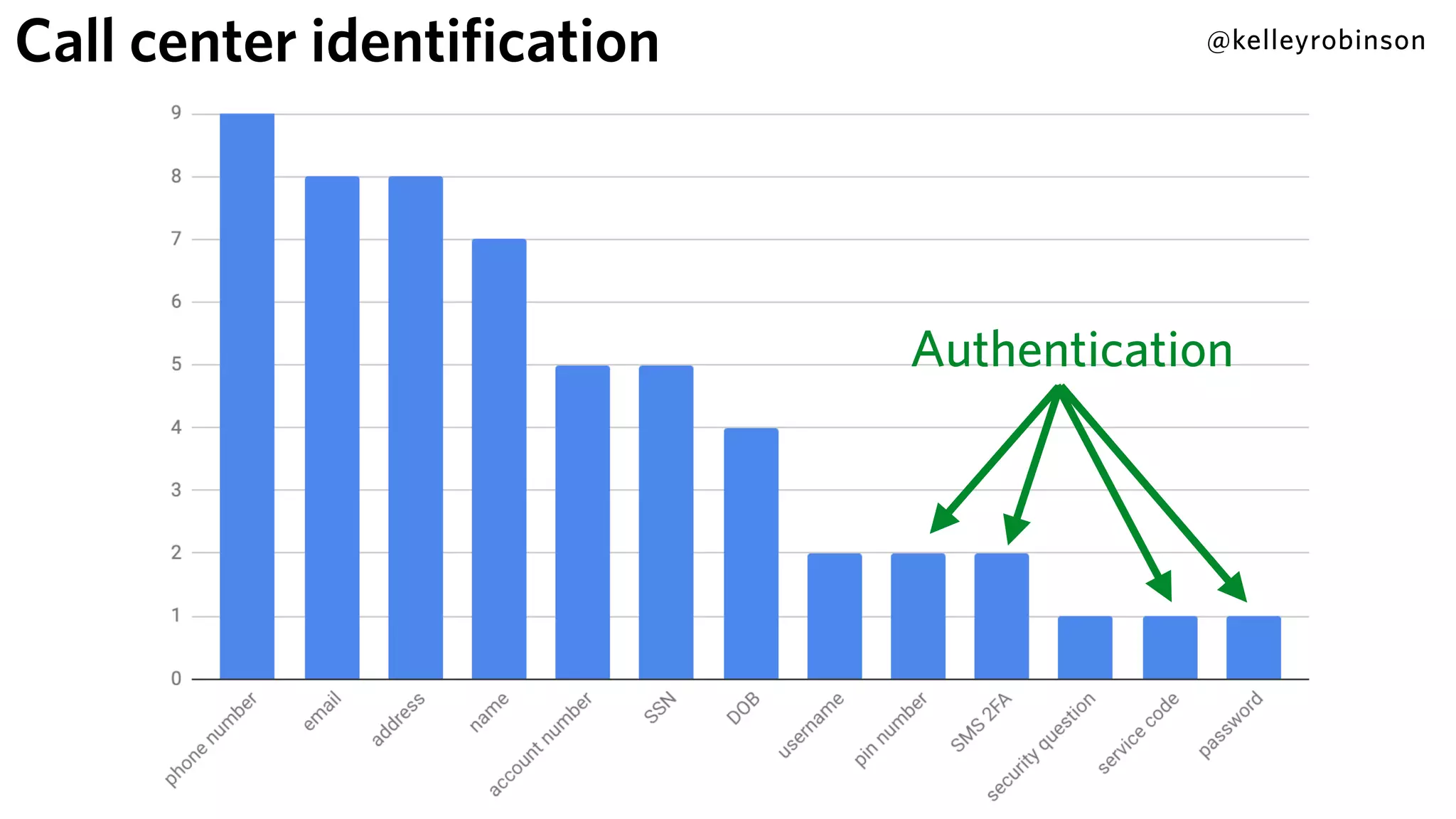
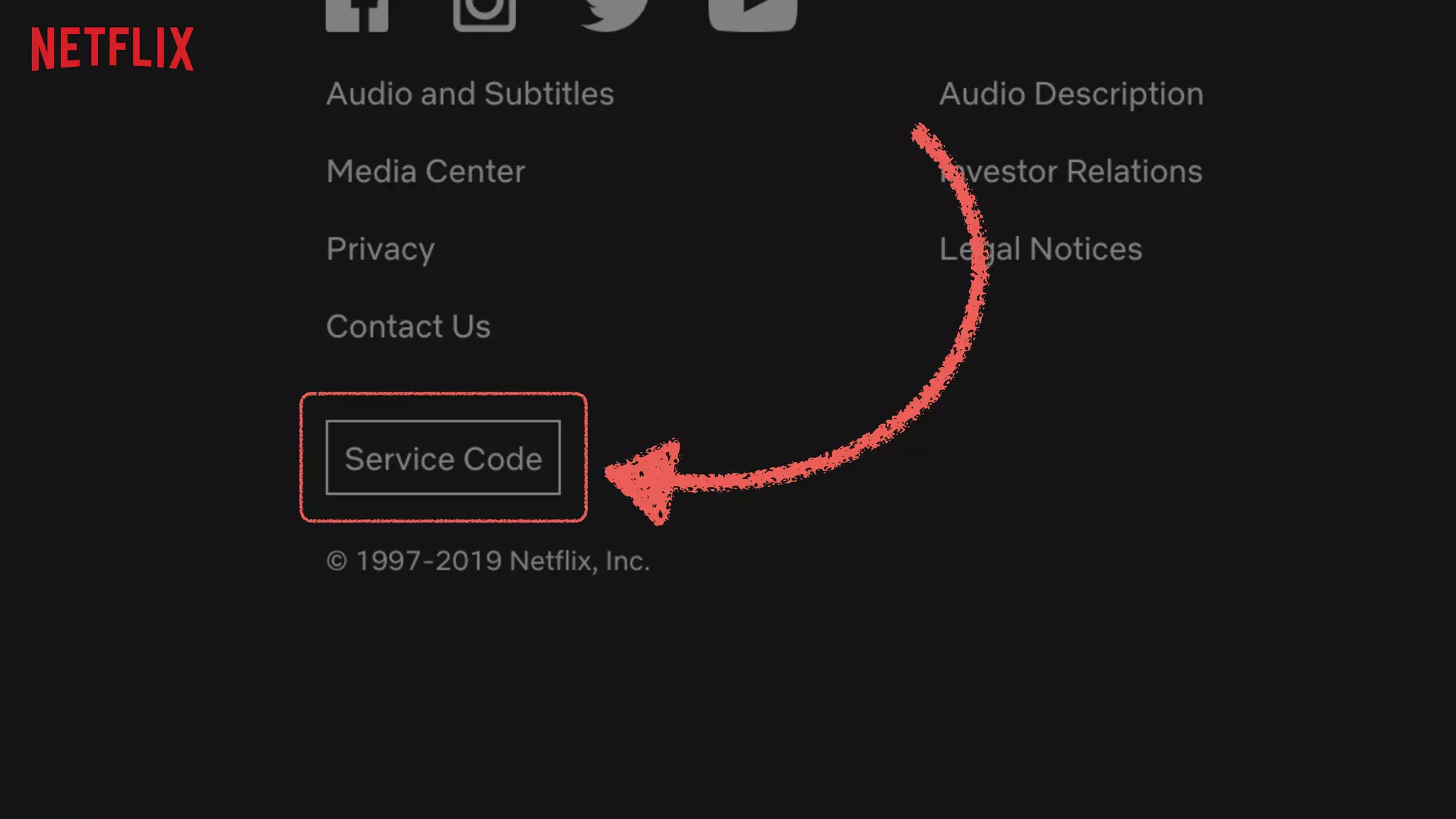
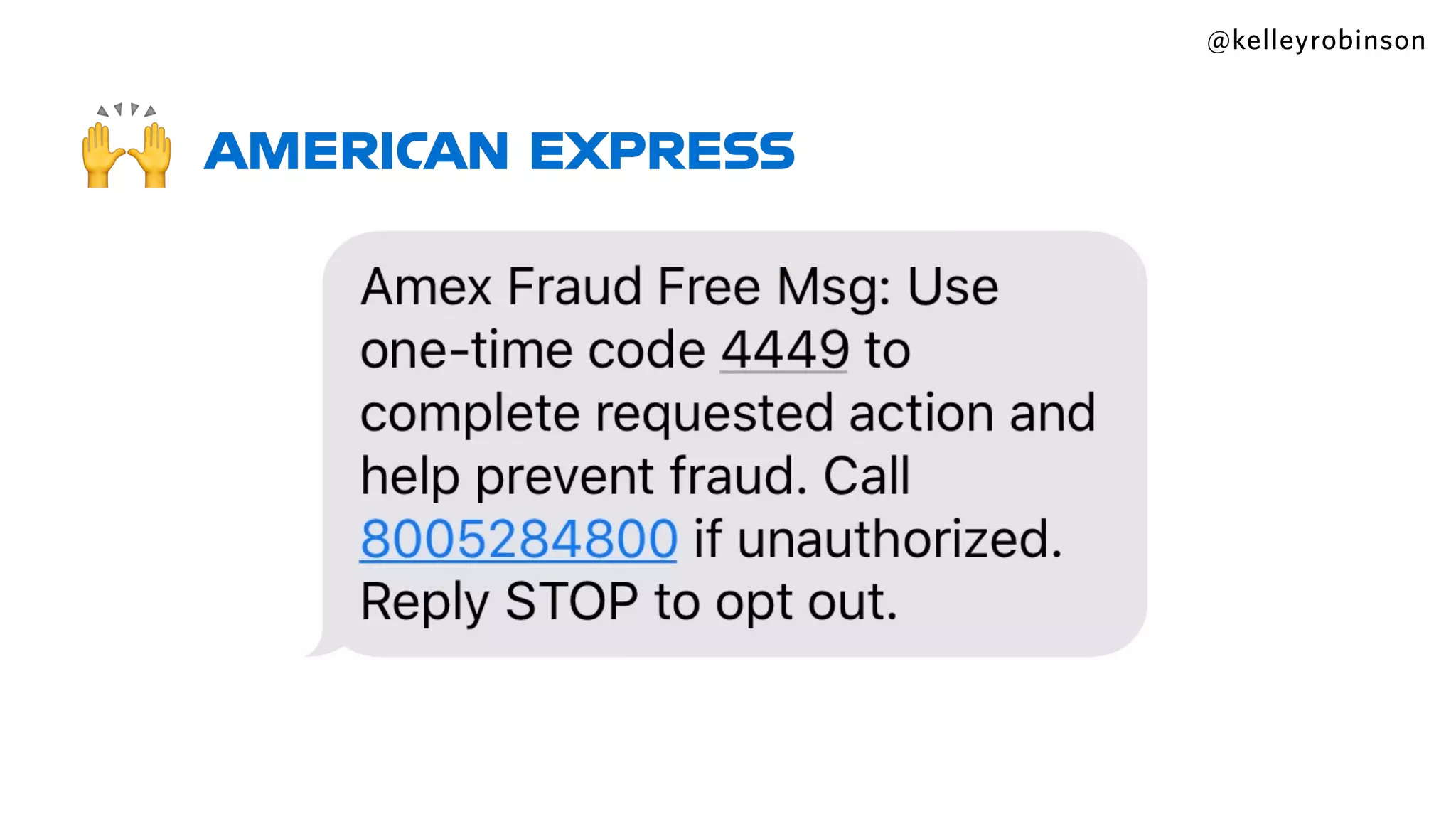
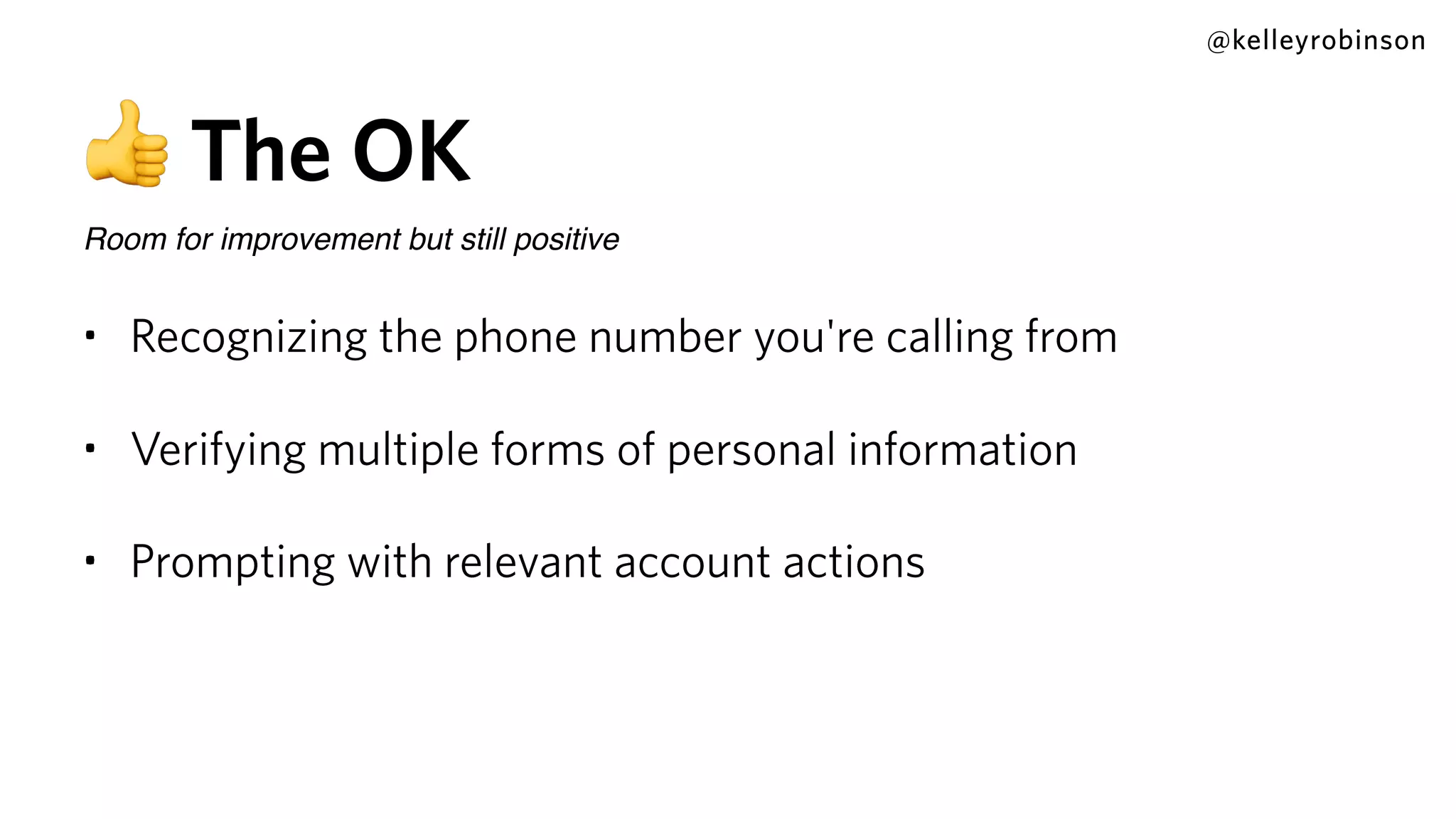
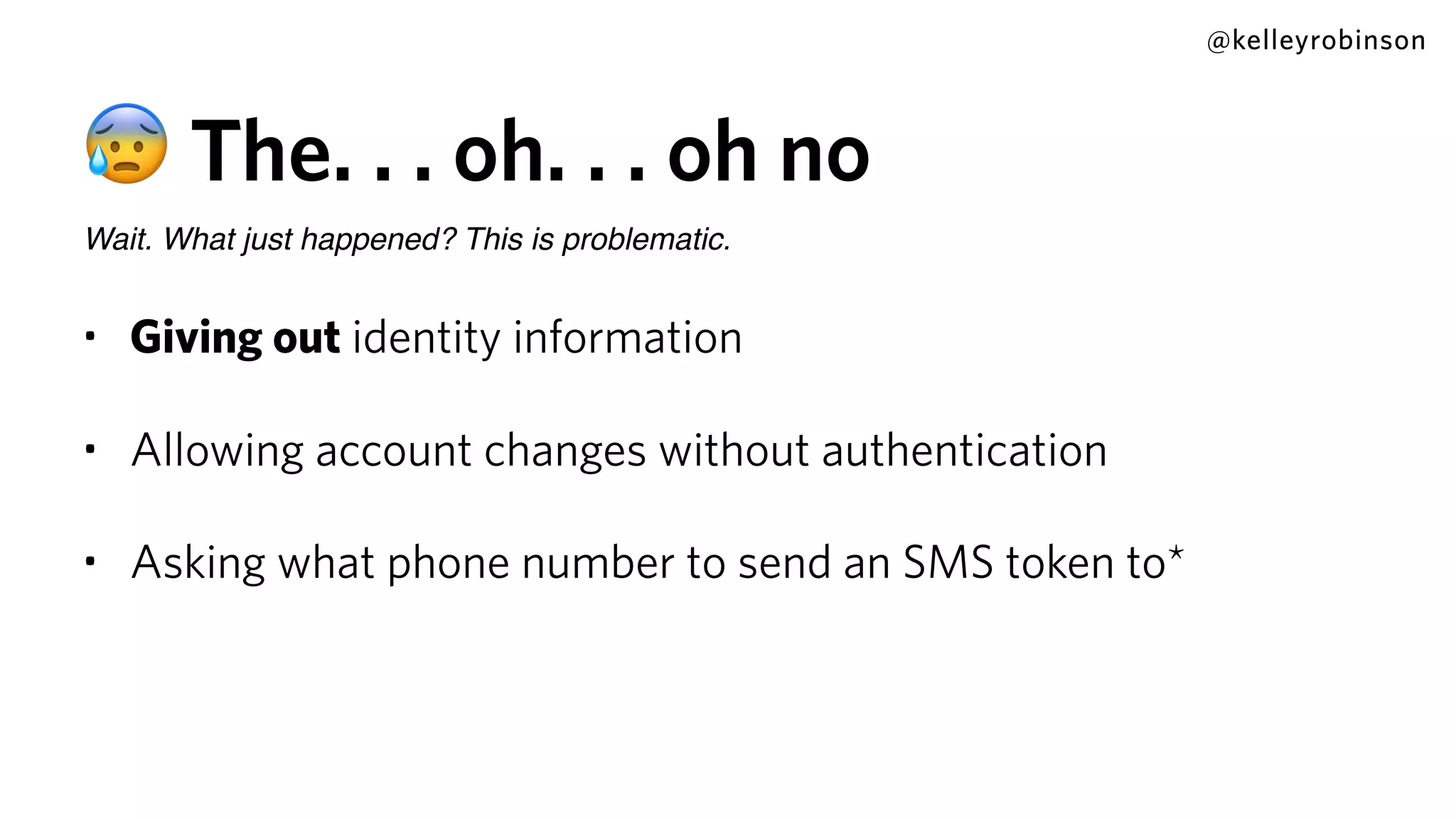
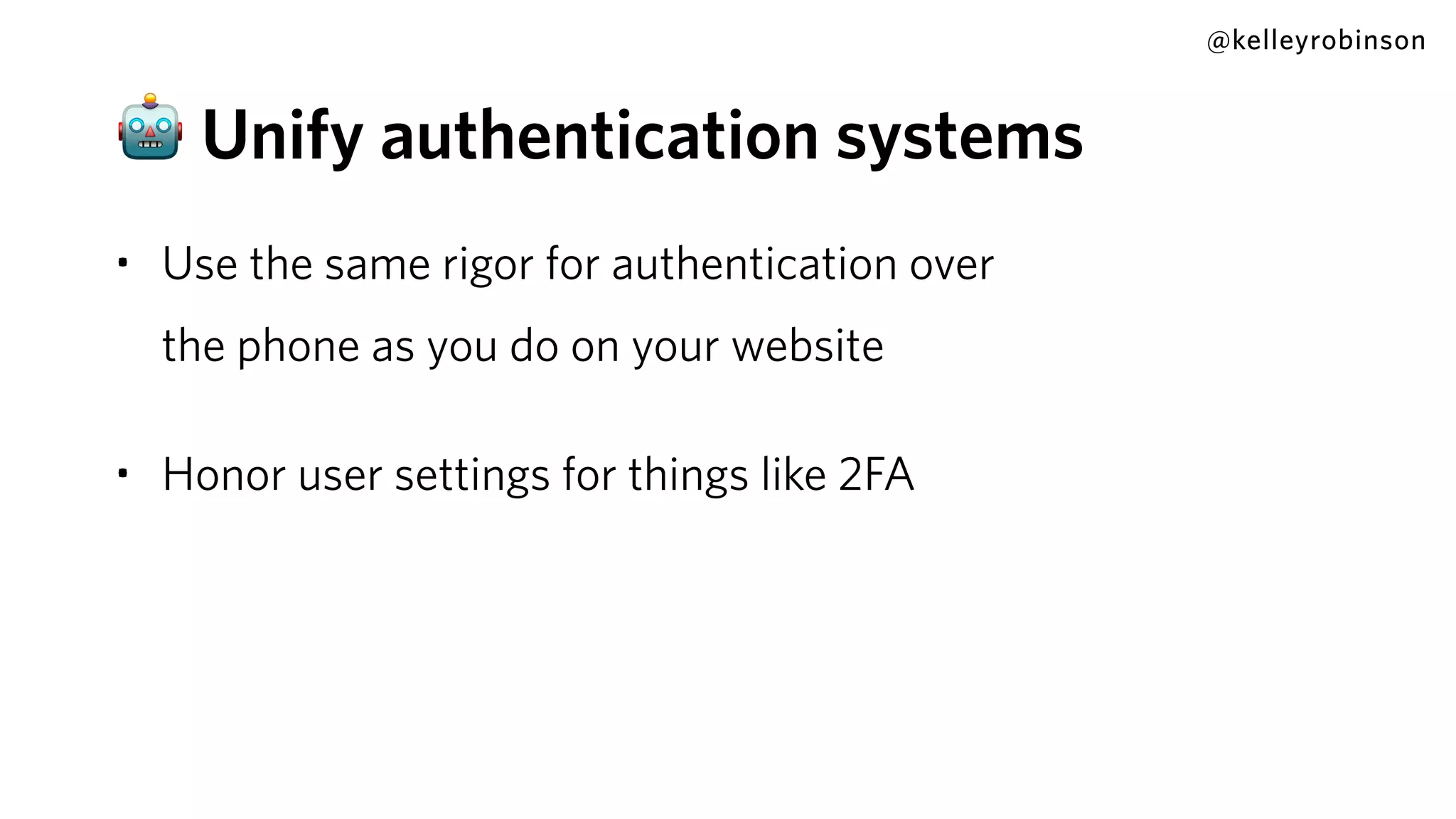
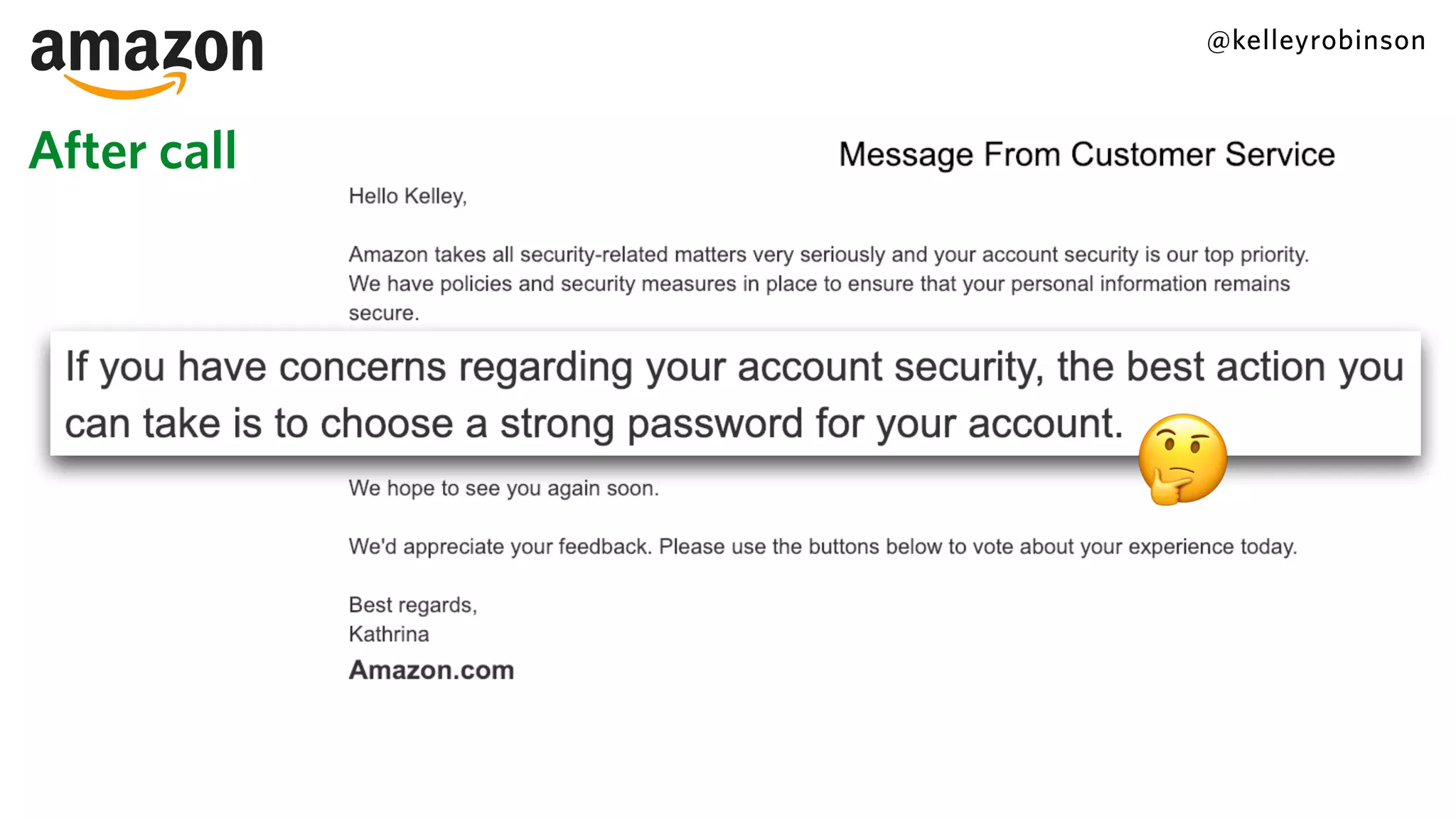
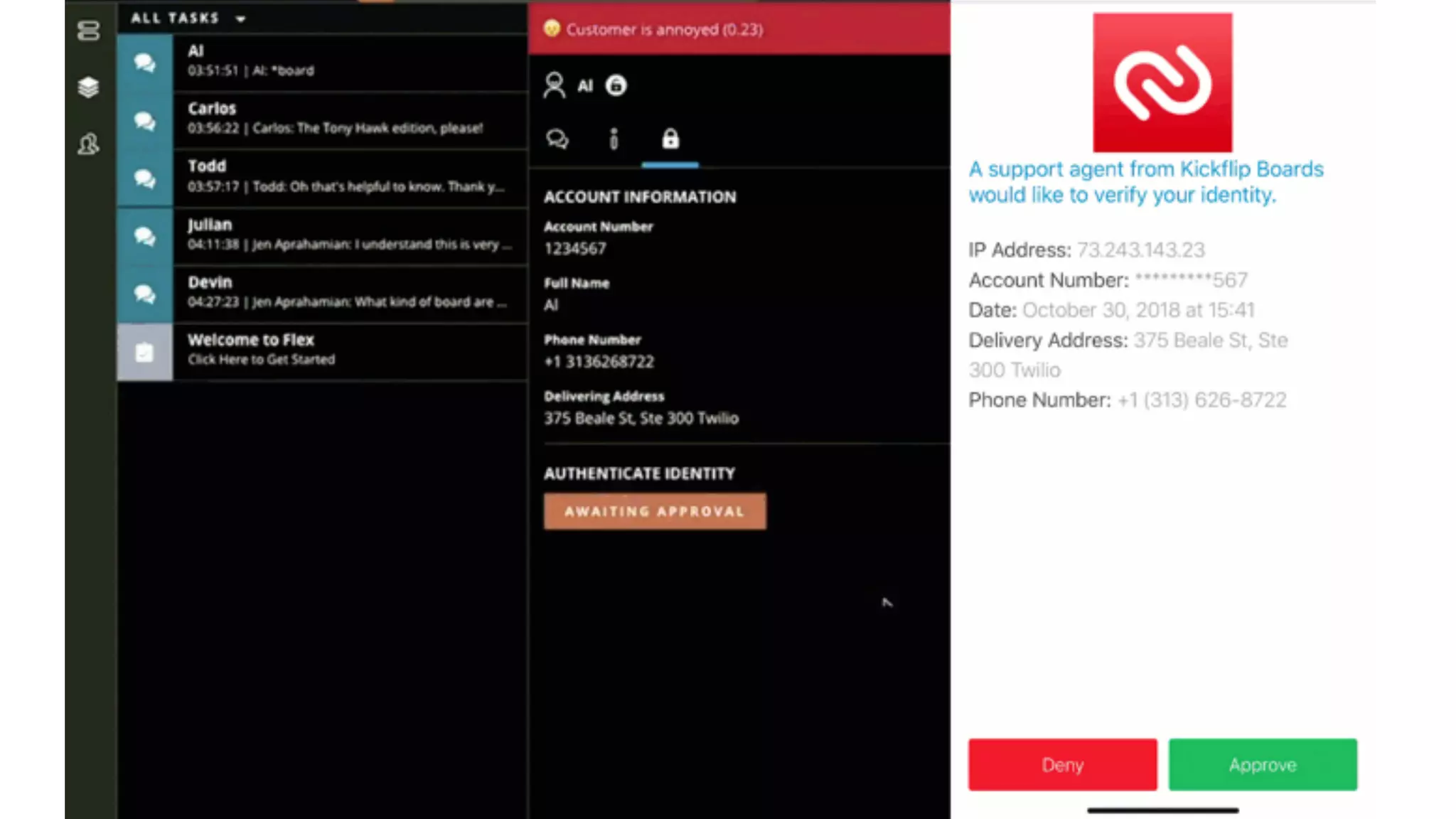
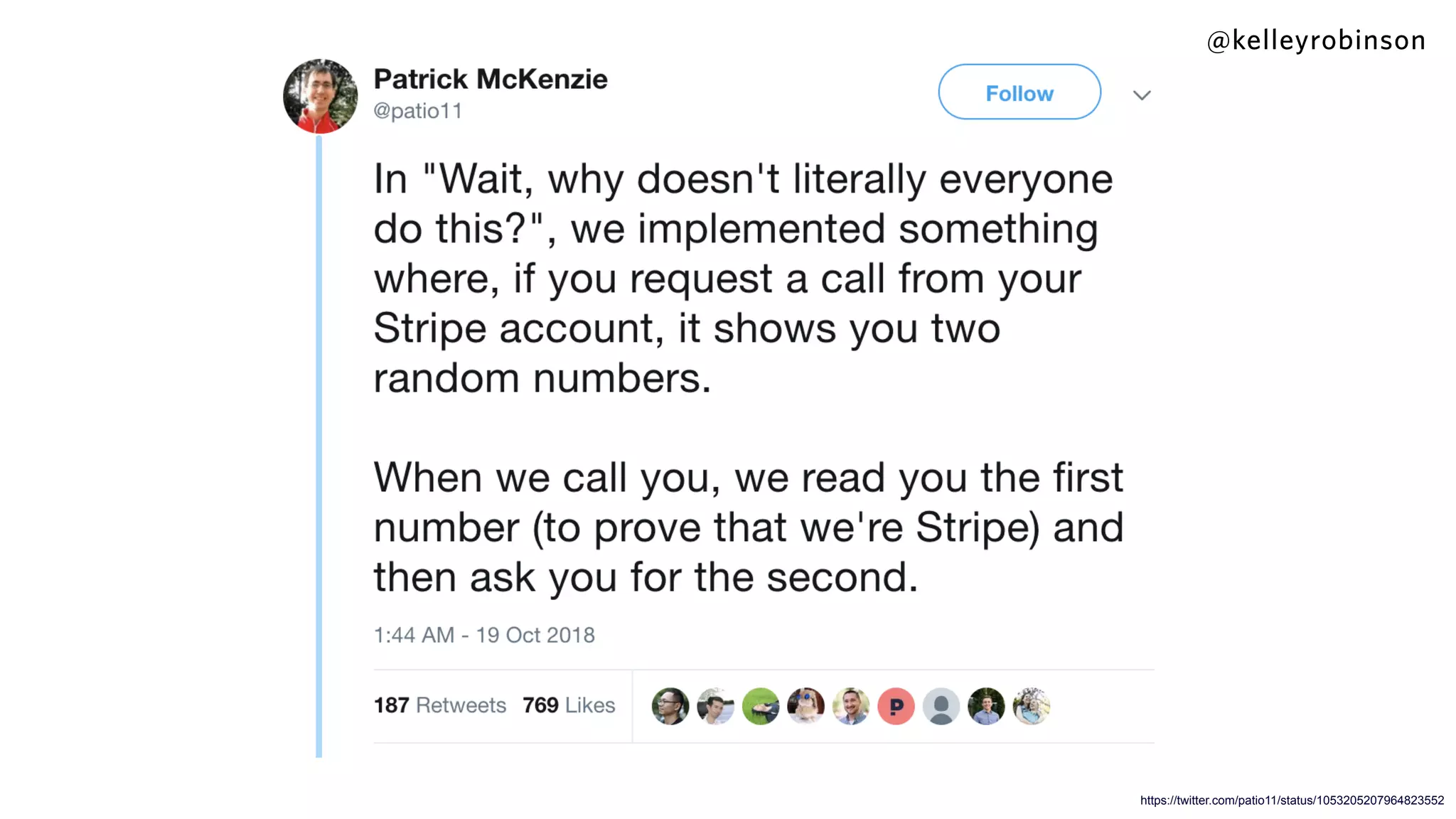
Kelley Robinson's talk addresses the challenges of contact center authentication, particularly highlighting vulnerabilities such as the reliance on easily accessible personal information. The presentation emphasizes the need for improved security measures, including the unification of authentication systems and the implementation of stricter identity verification protocols for customer support interactions. Recommendations include establishing guardrails for agents and considering the threat model to limit sensitive actions without proper authentication.