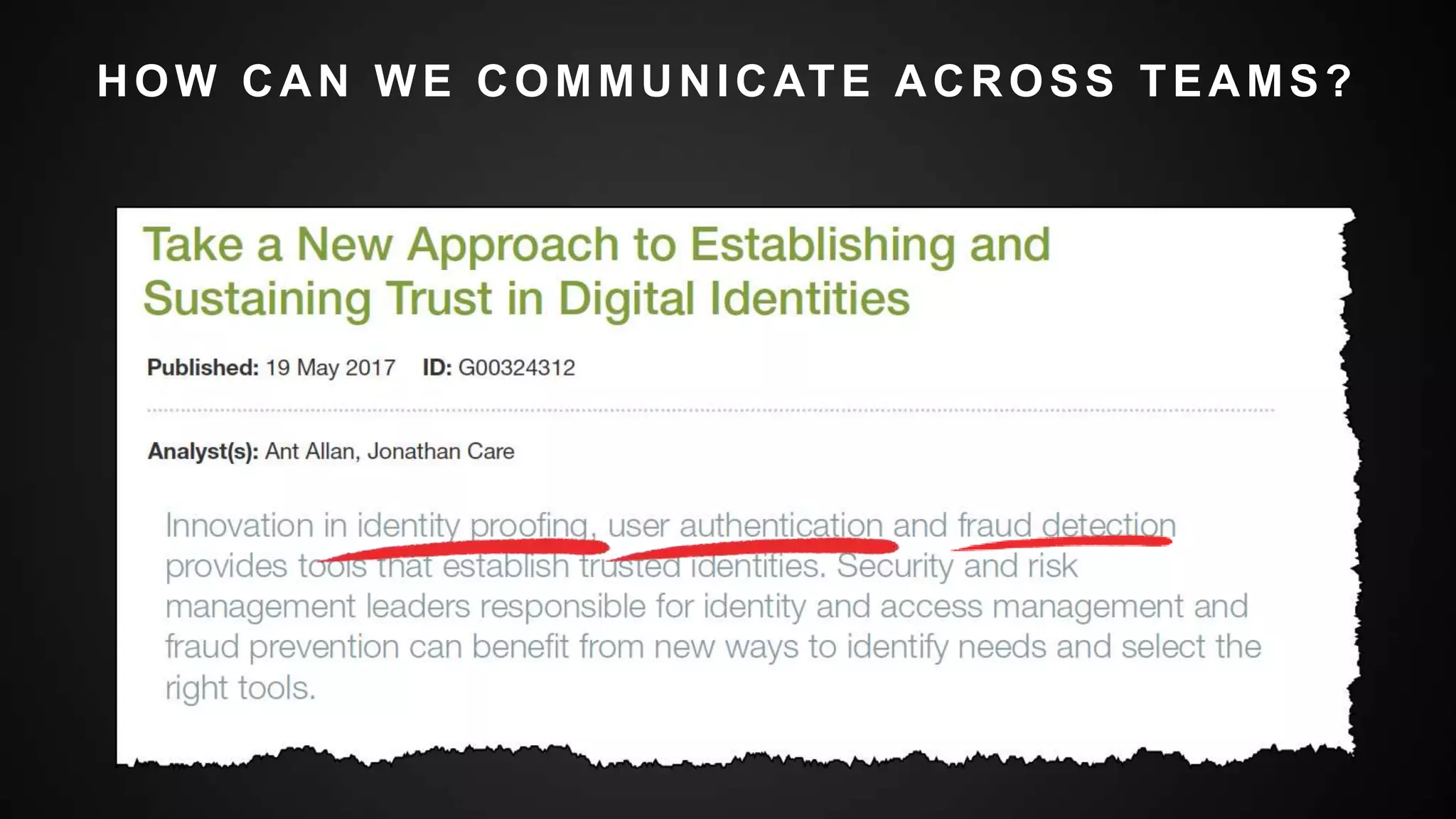
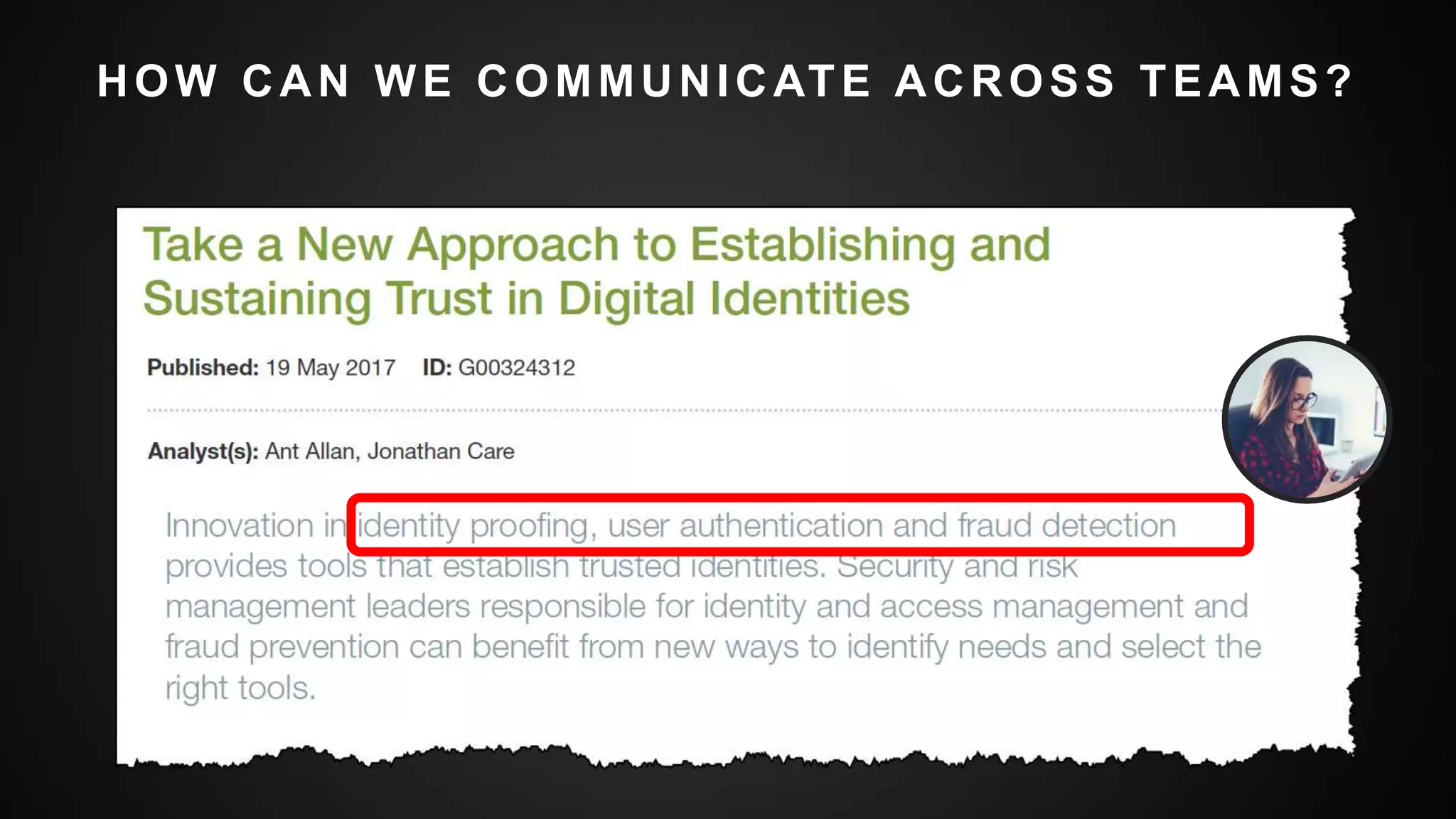
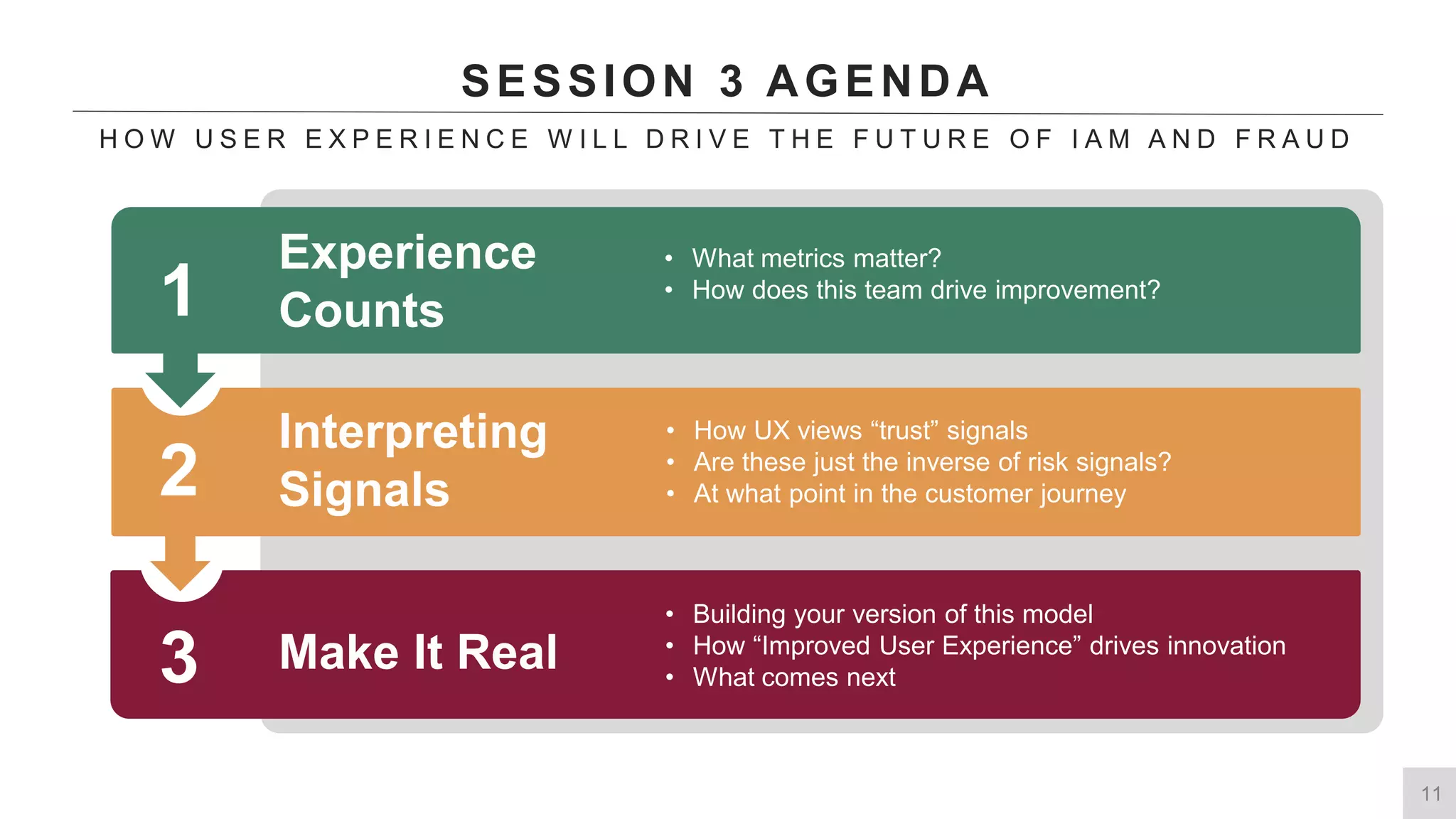
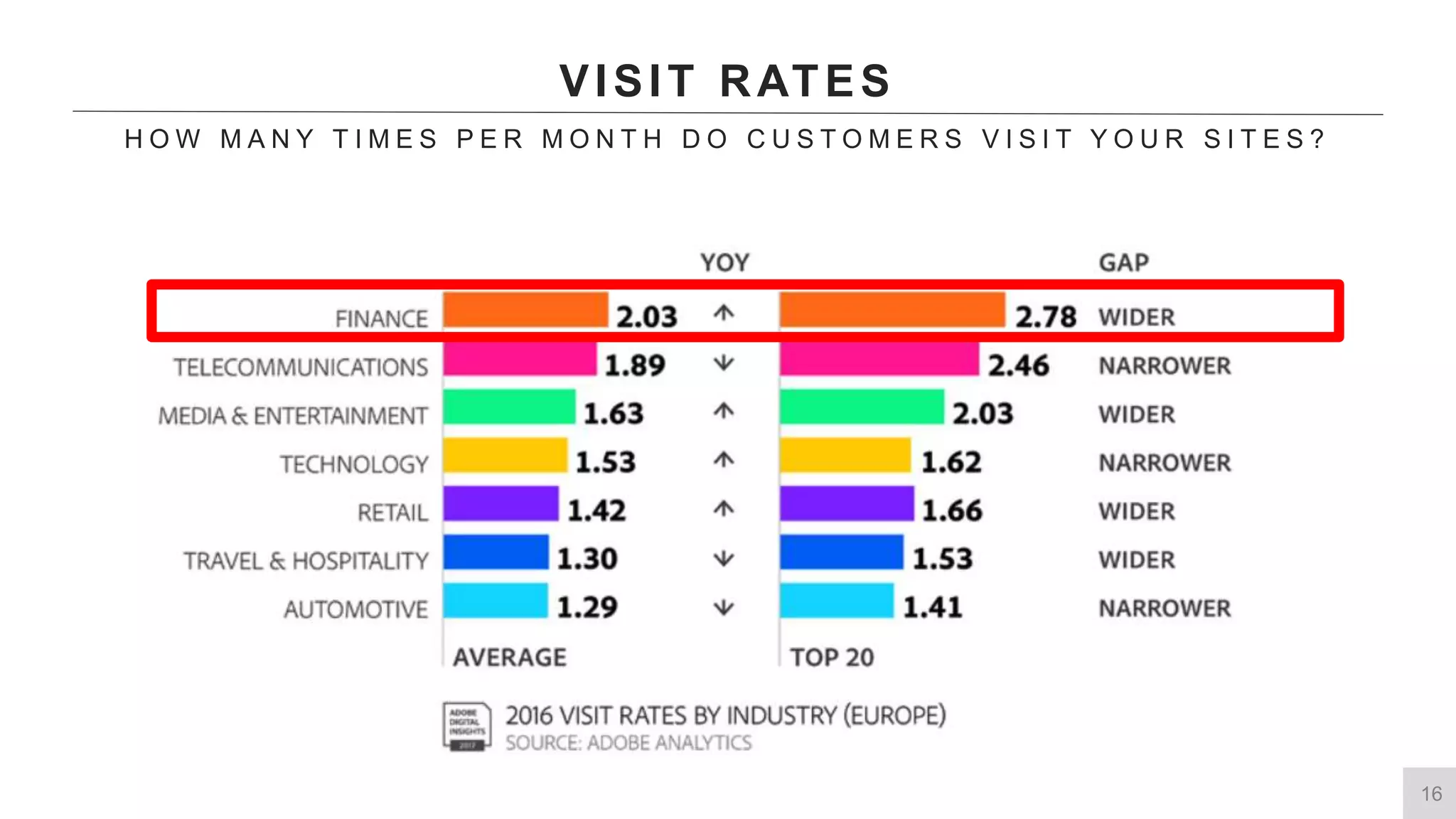
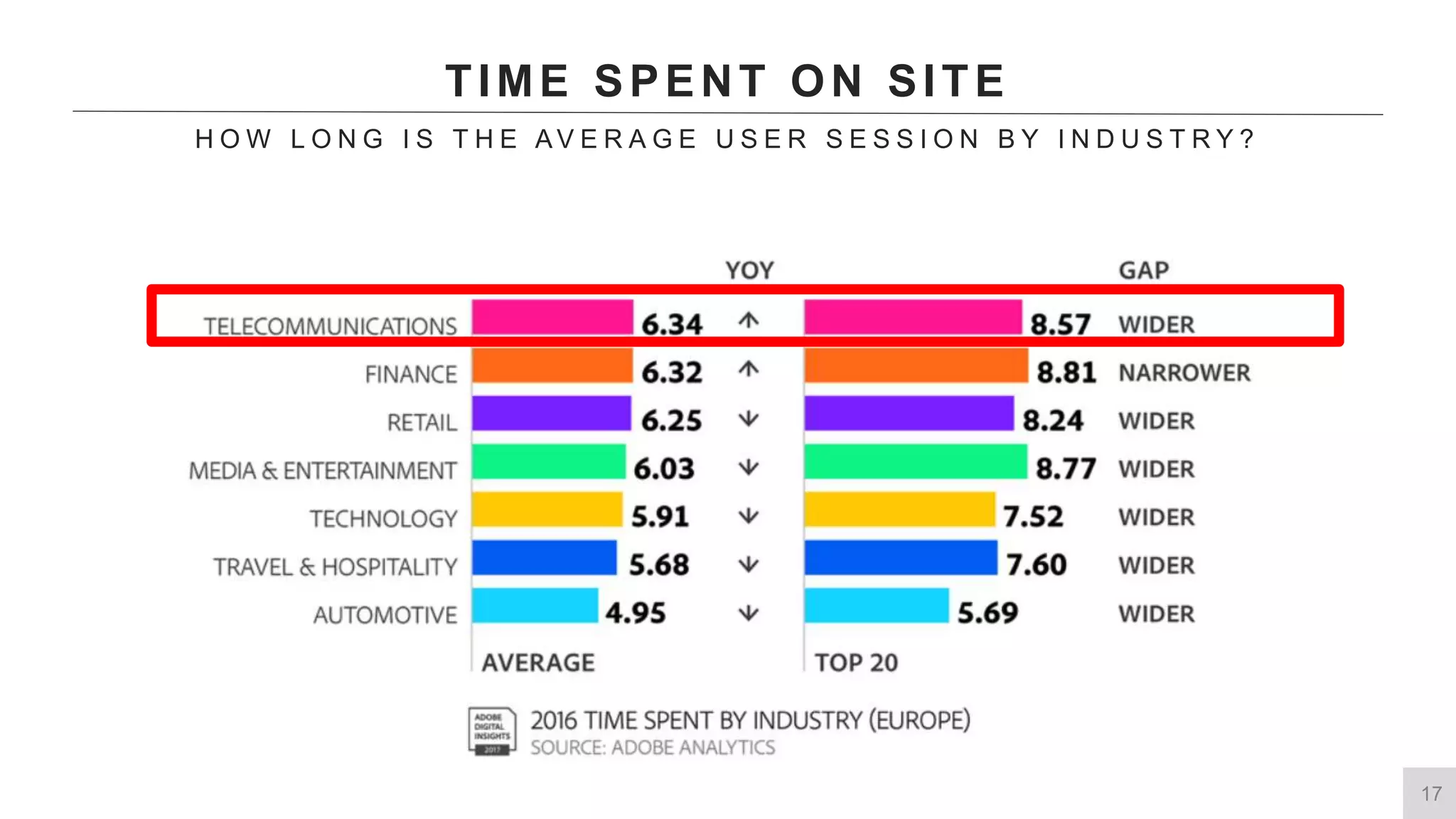
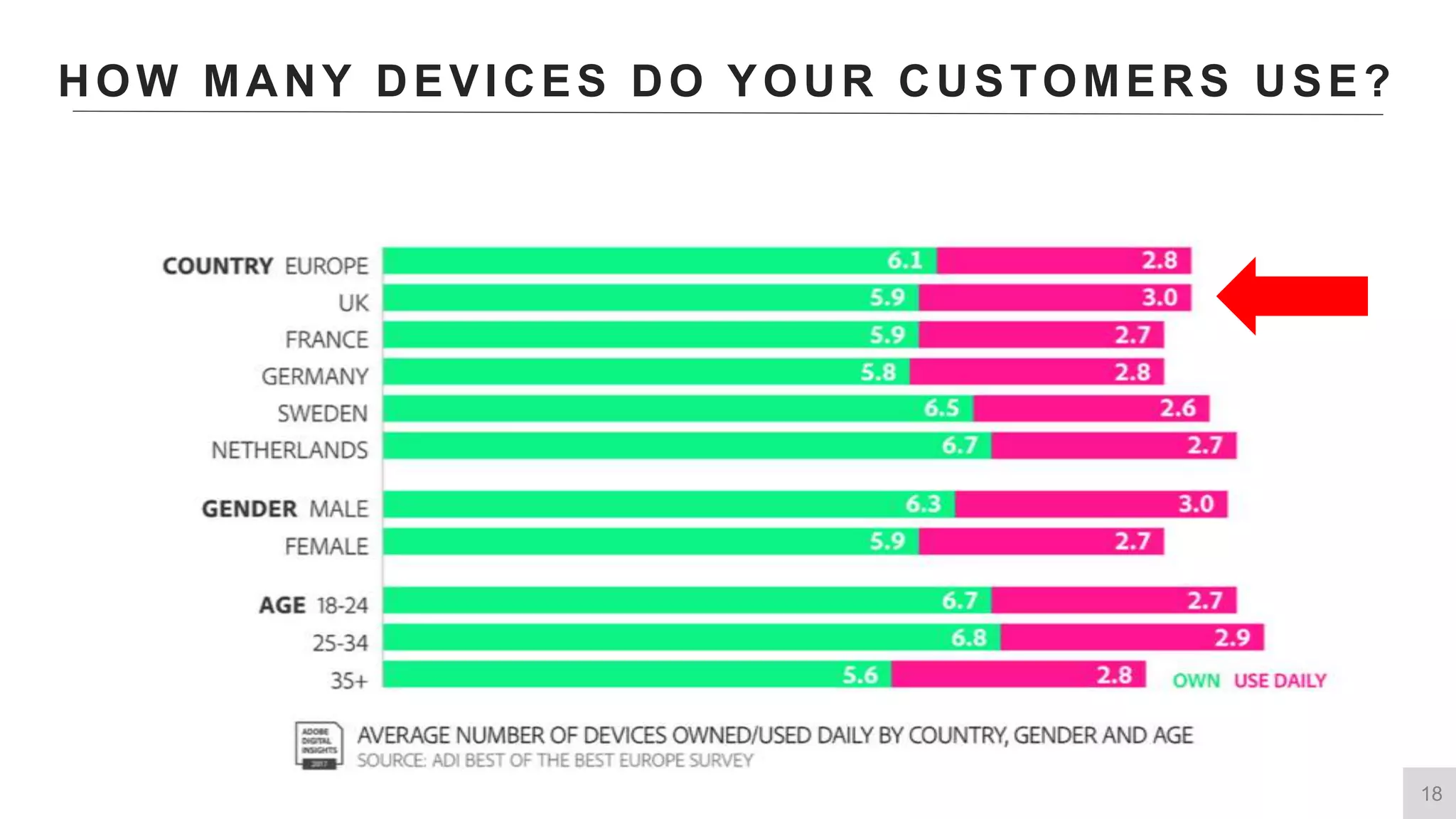
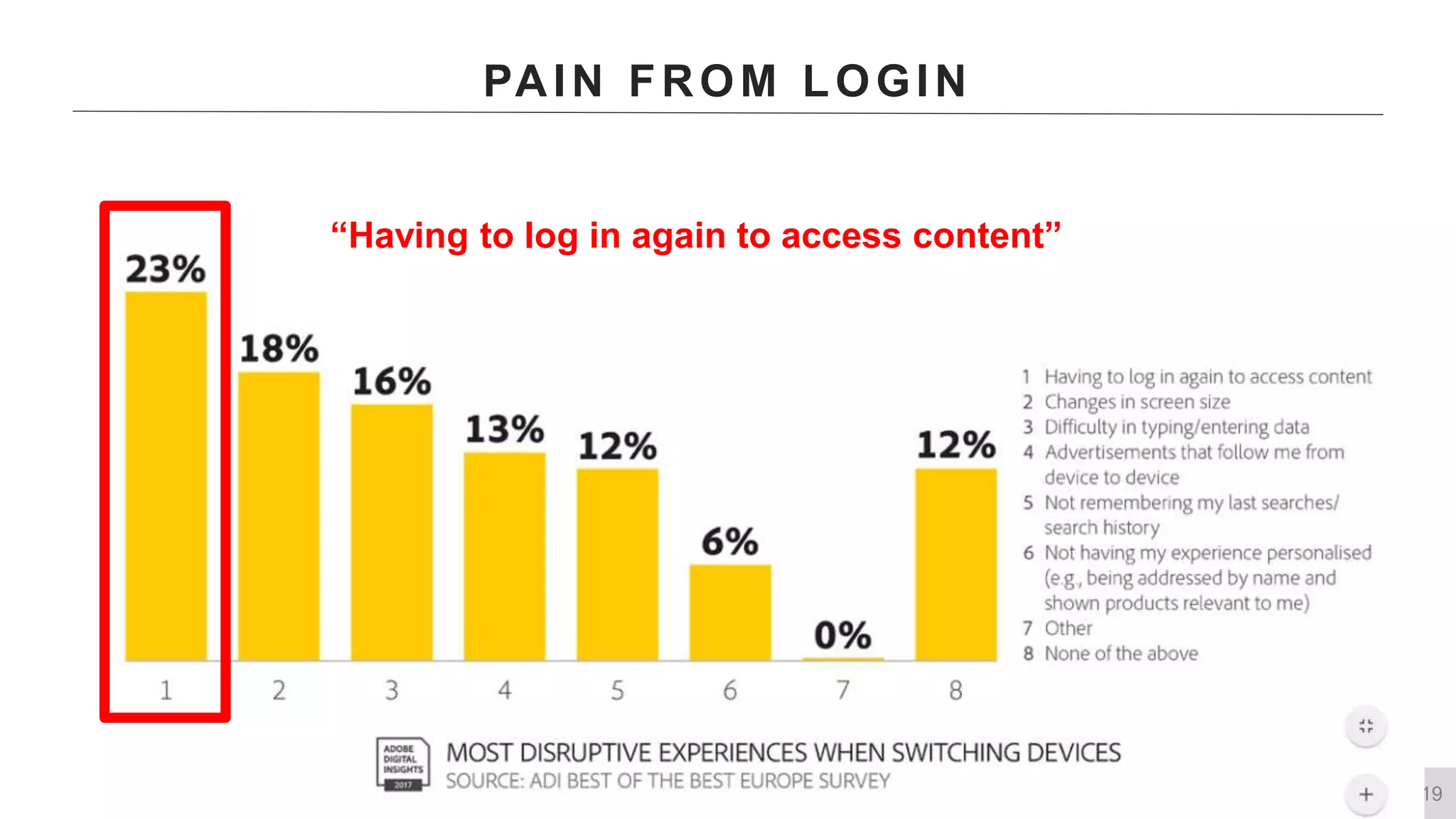
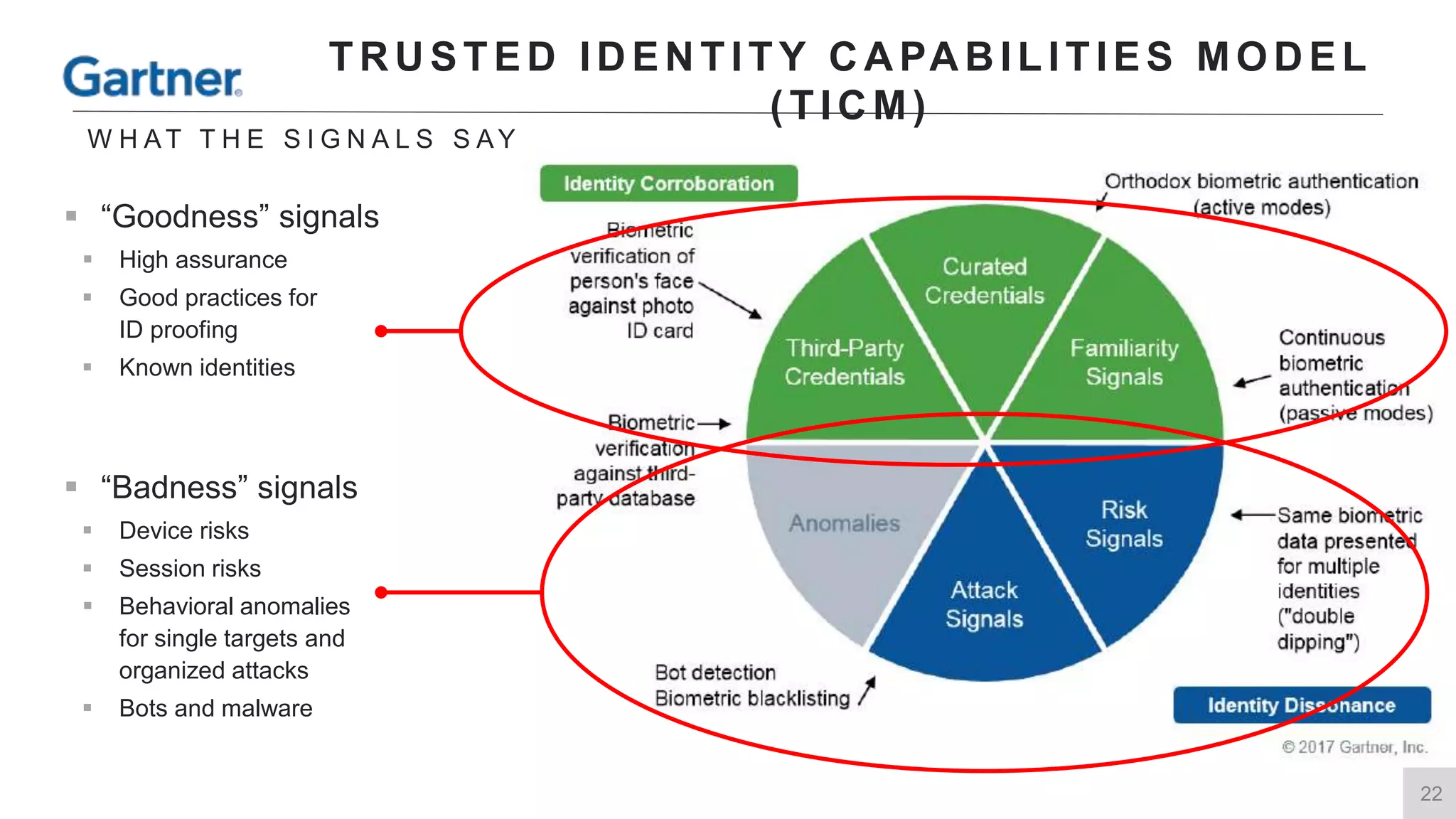
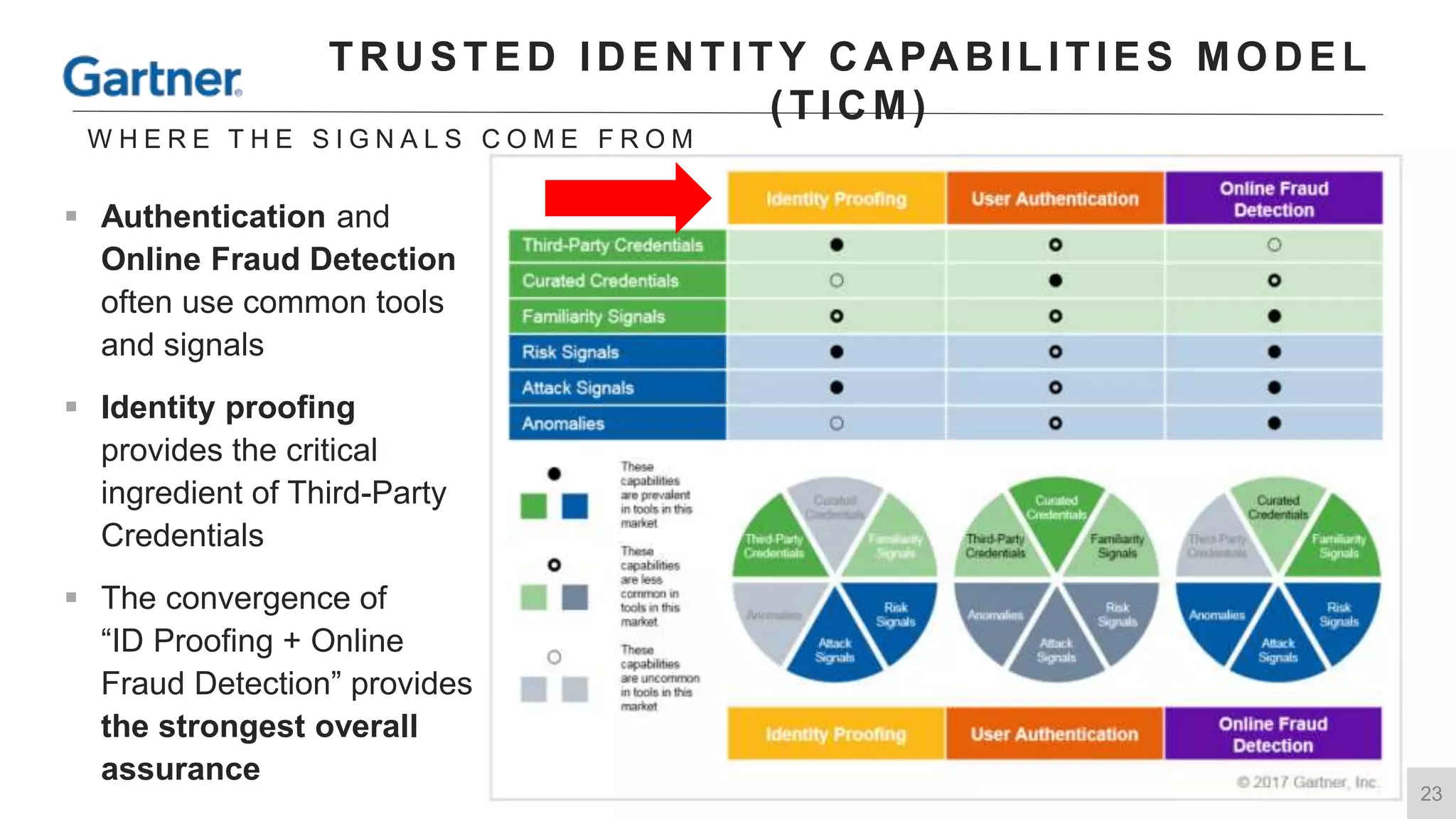
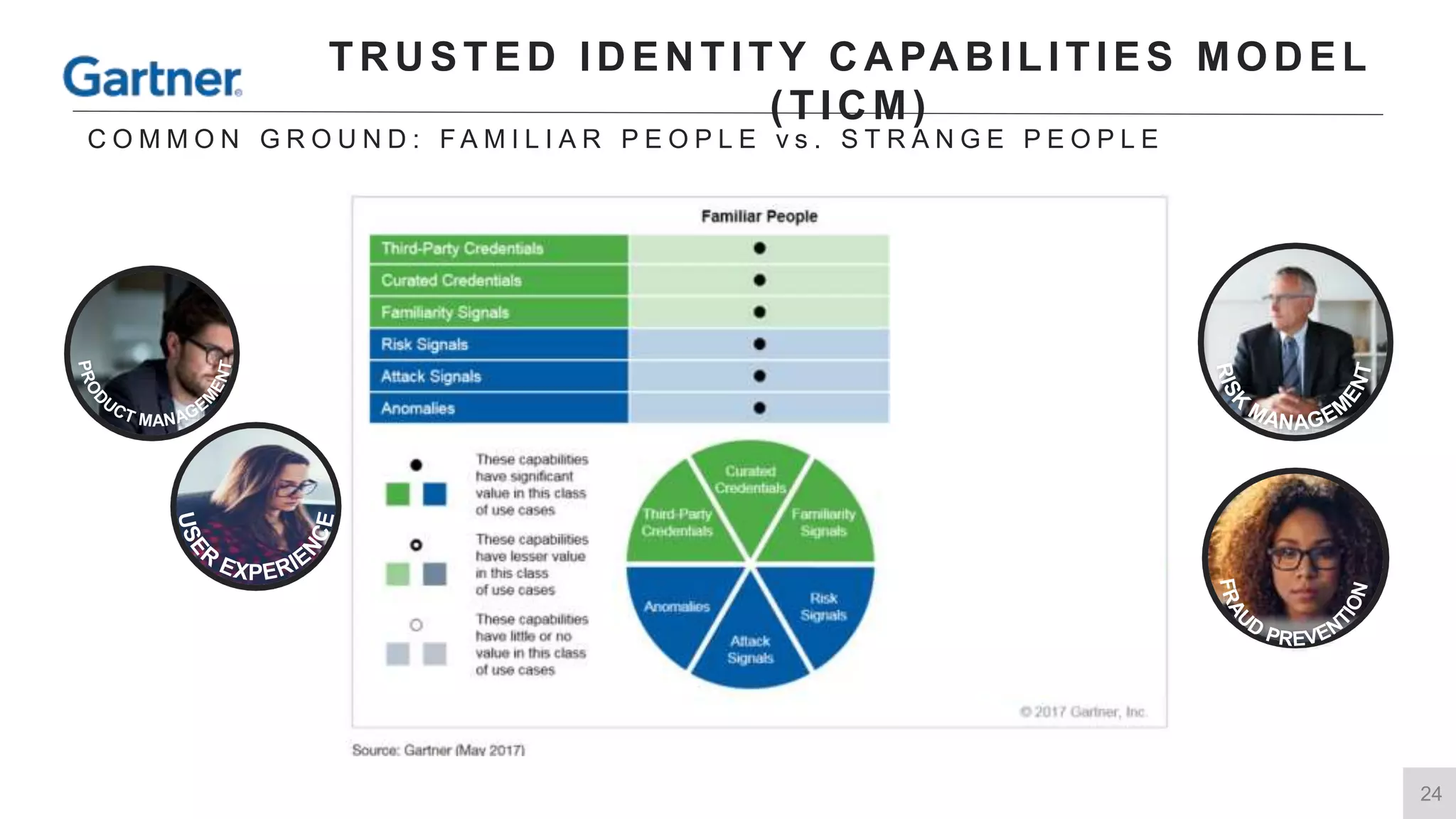
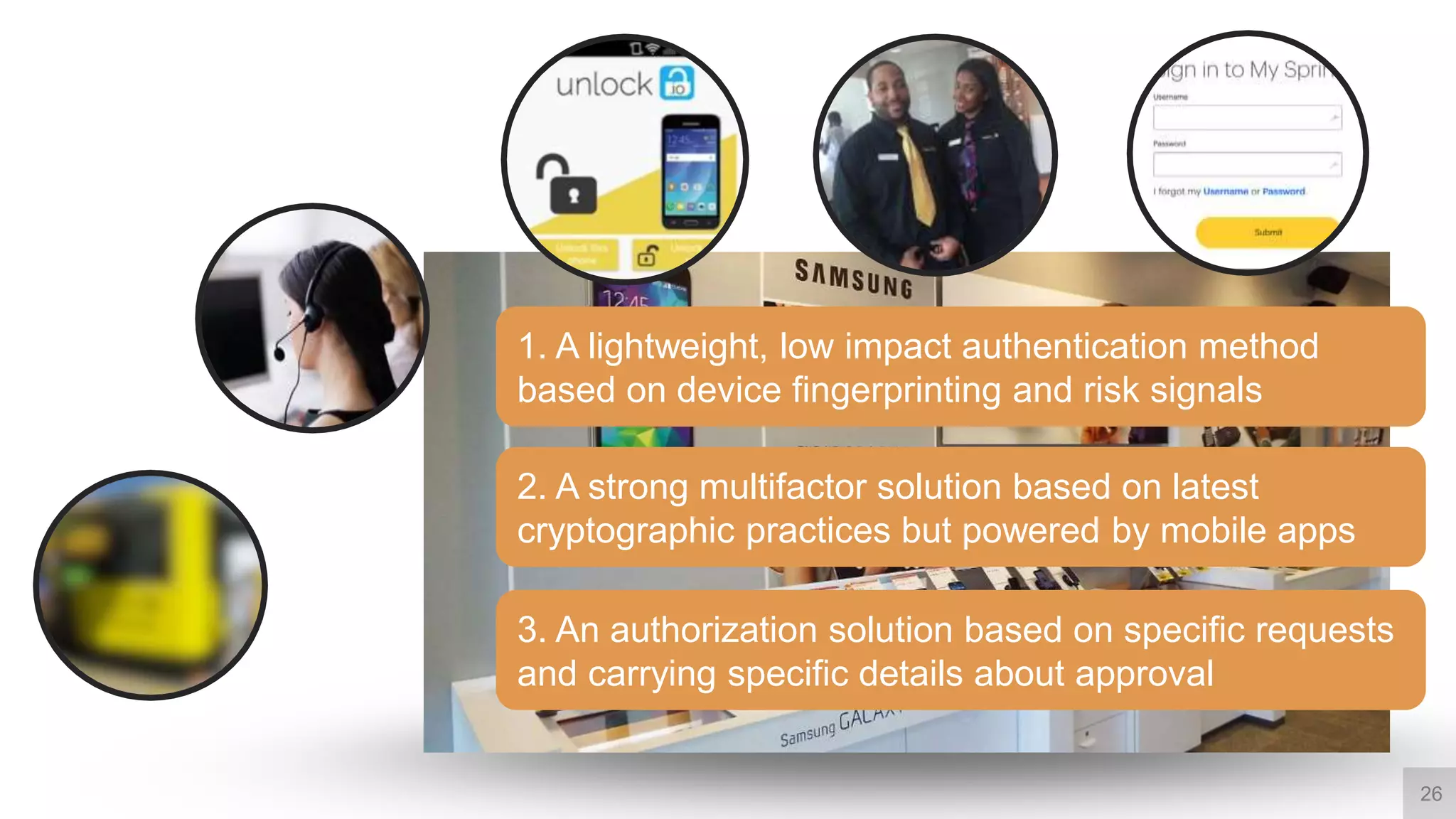
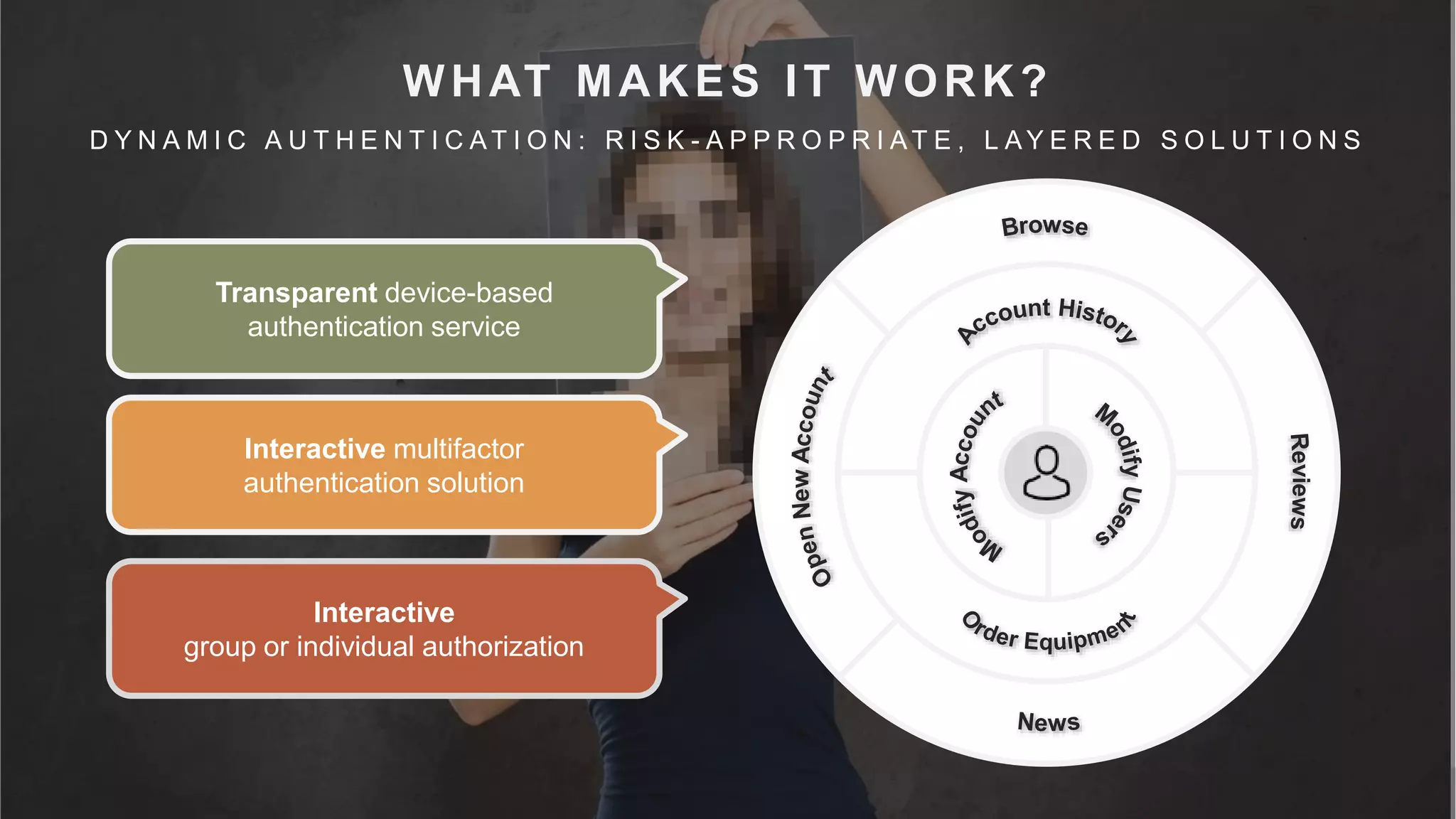
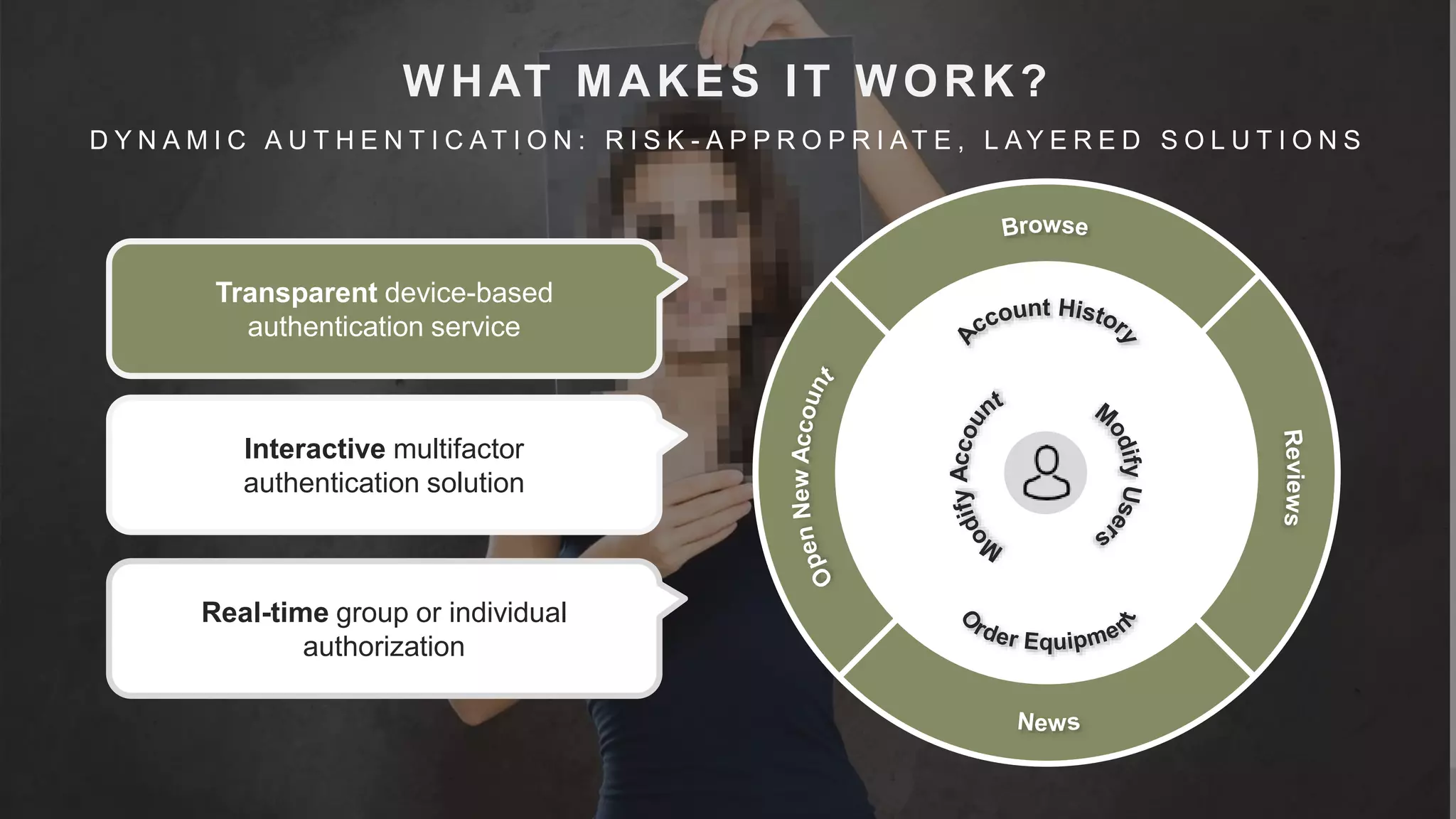
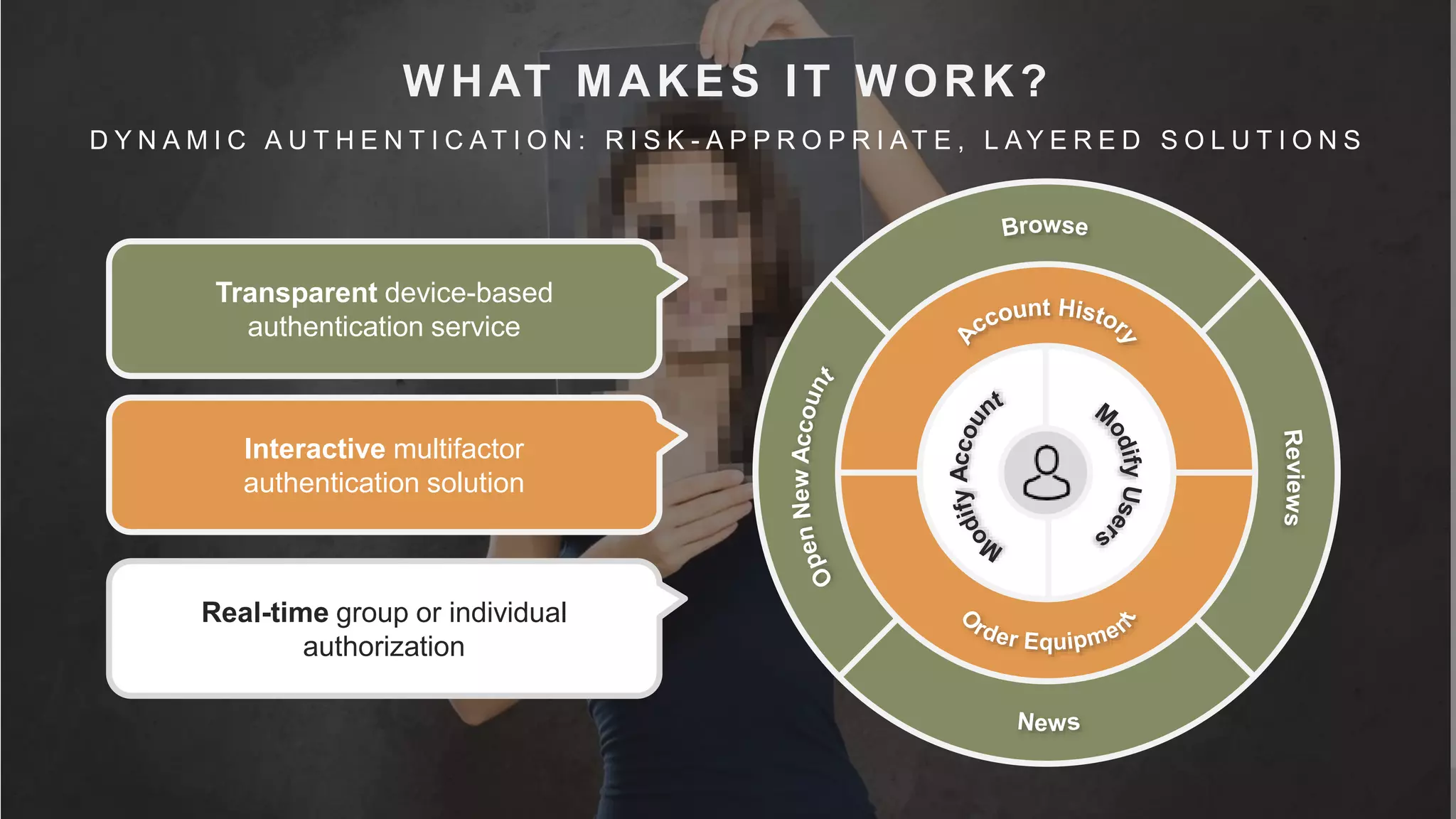
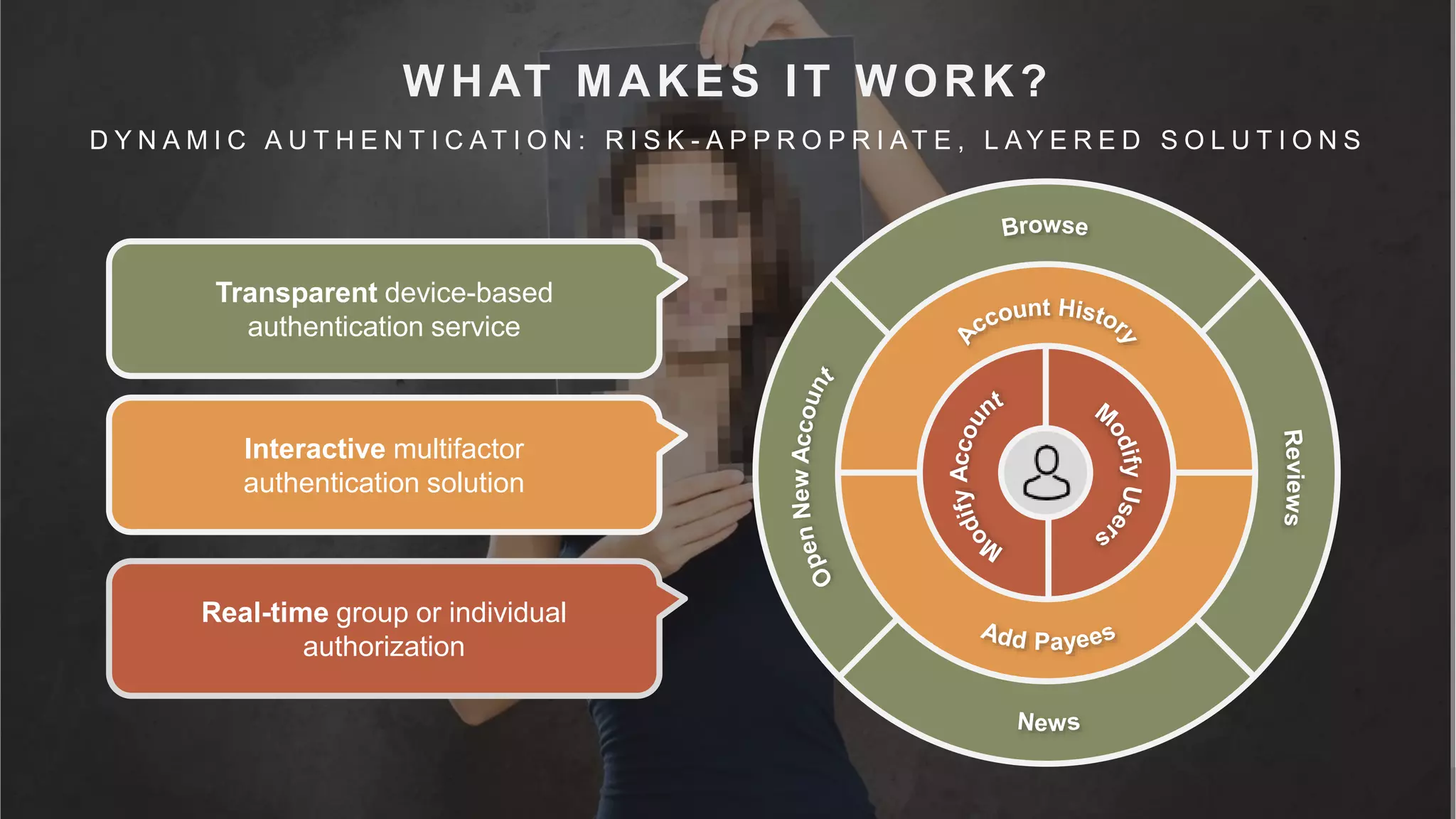
This document summarizes a presentation by Michael Thelander on leveraging trusted identity capabilities. The presentation discusses how fraud, cybersecurity, and user experience teams can better communicate by taking a risk-based approach to dynamic authentication. It provides examples of lightweight and multifactor authentication solutions and emphasizes engaging cross-functional teams to improve security while enhancing the user experience.