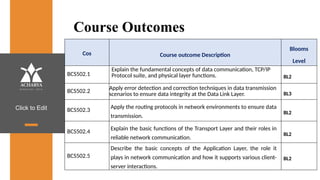
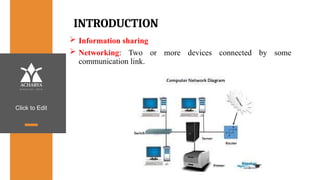
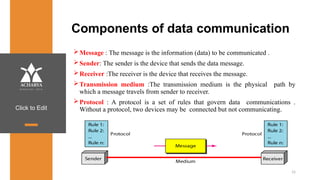
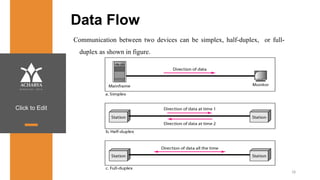
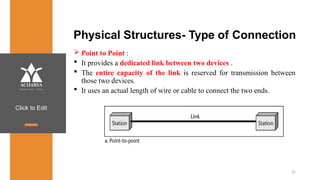
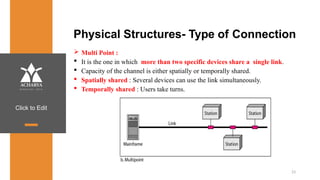
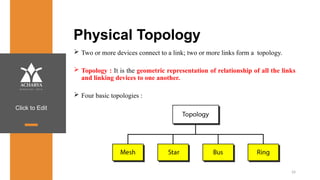
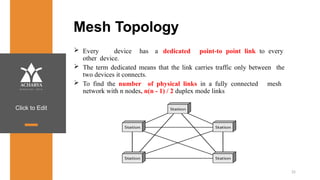
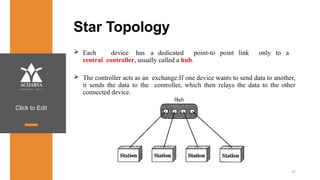
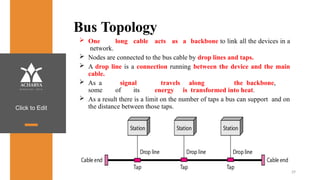
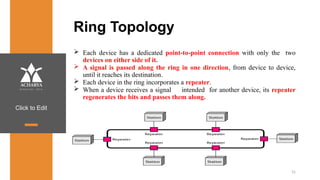
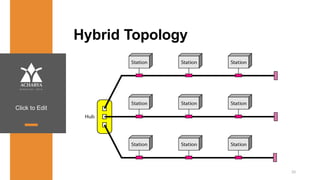
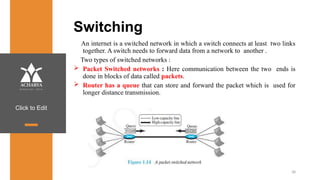
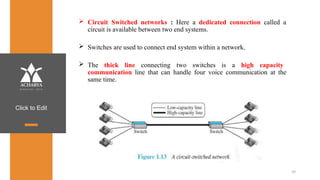
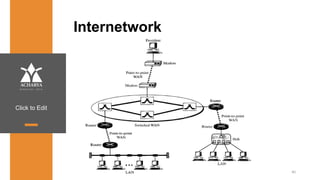
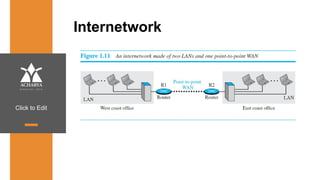
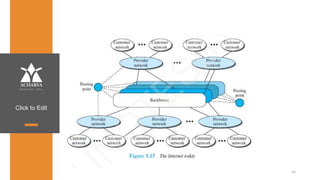
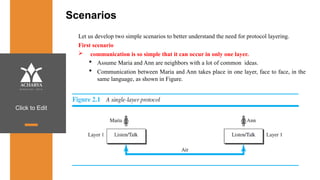
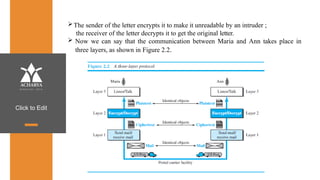
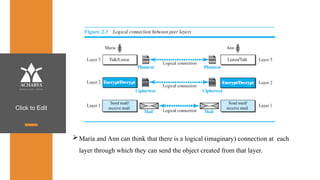
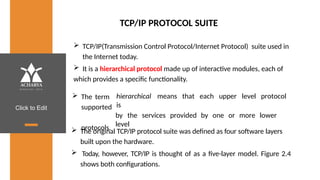
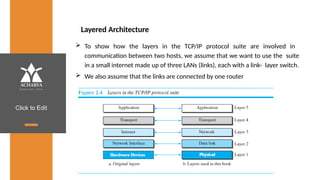
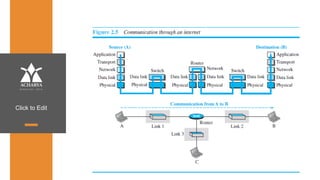
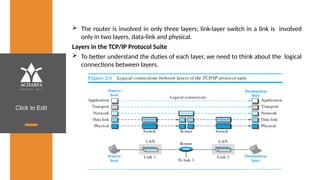
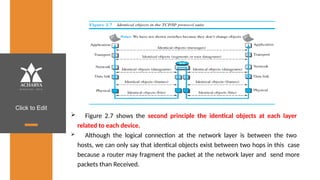
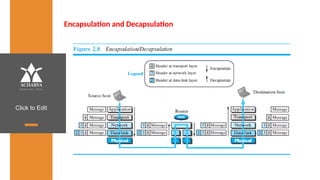
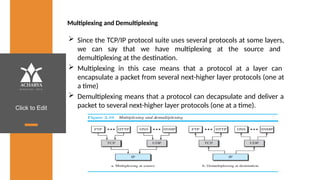
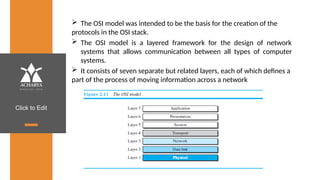
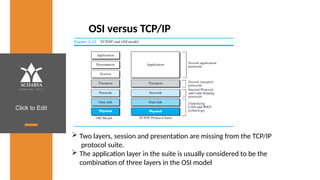
The document provides an overview of a course on data communications and networking, detailing the syllabus, course objectives, and outcomes across five modules covering layers from physical to application. It includes key concepts, protocols, and network types, while emphasizing the importance of protocols for effective data exchange. The educational material draws on textbooks and reference books to support learning in the field.