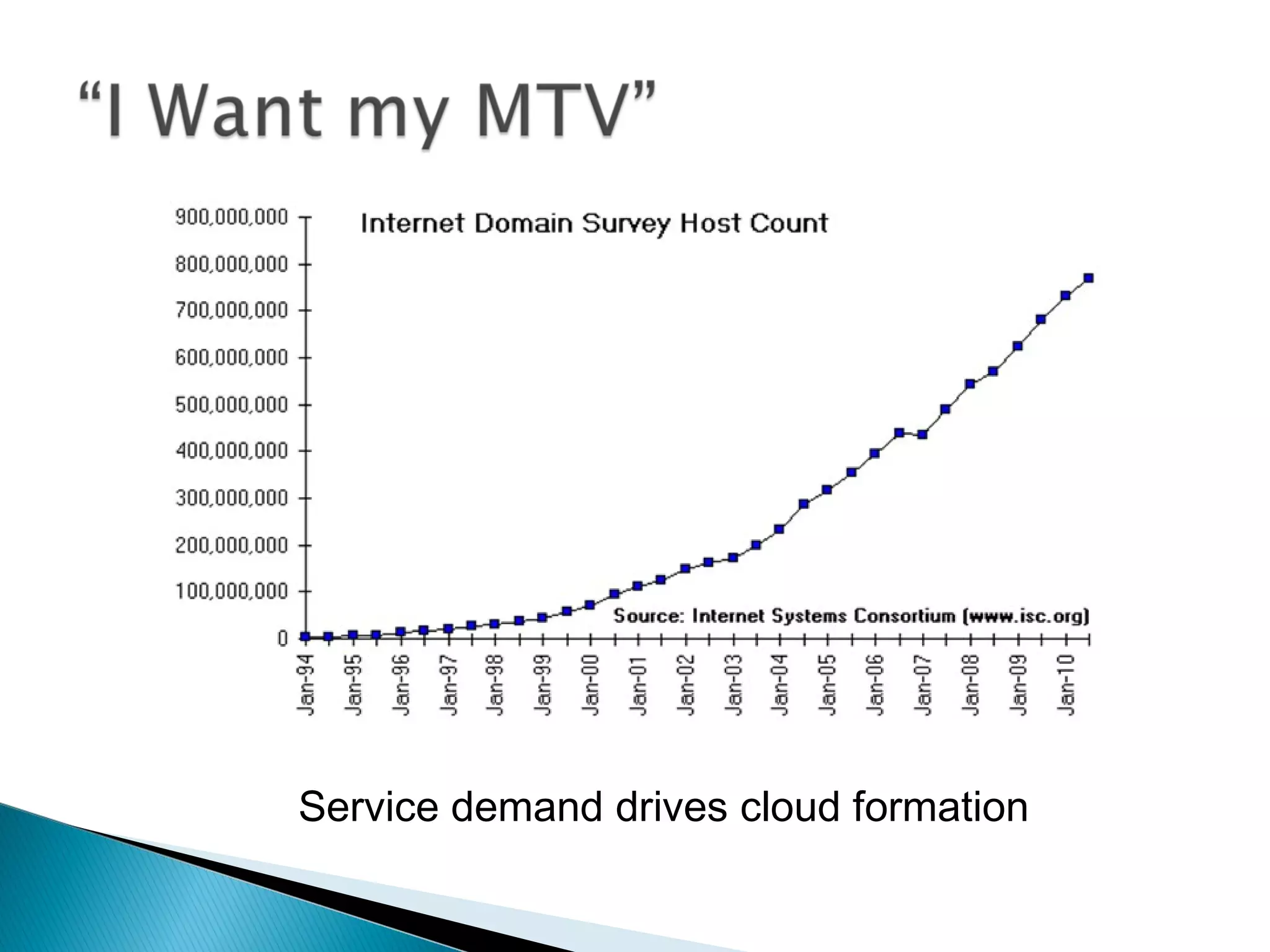
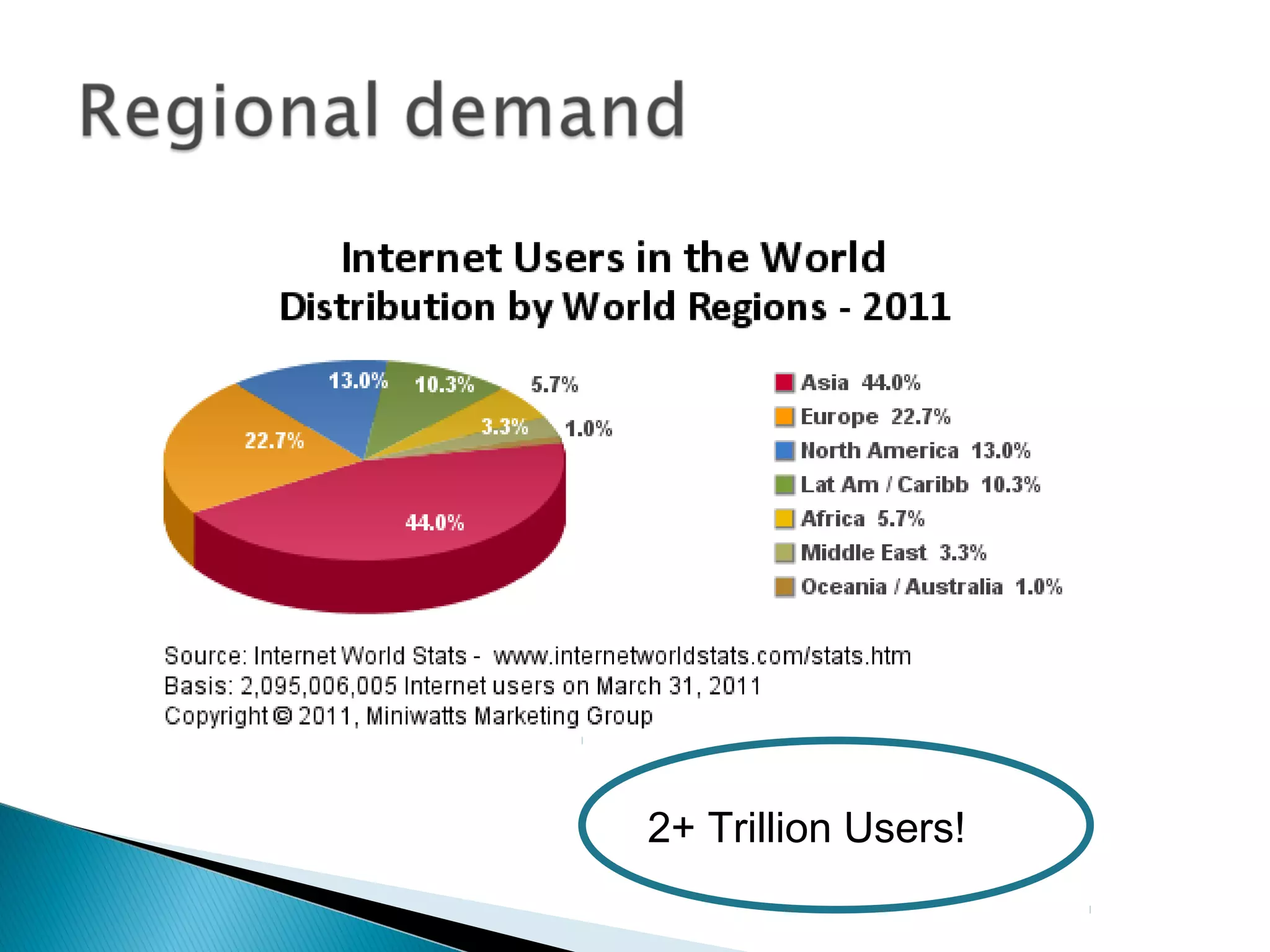
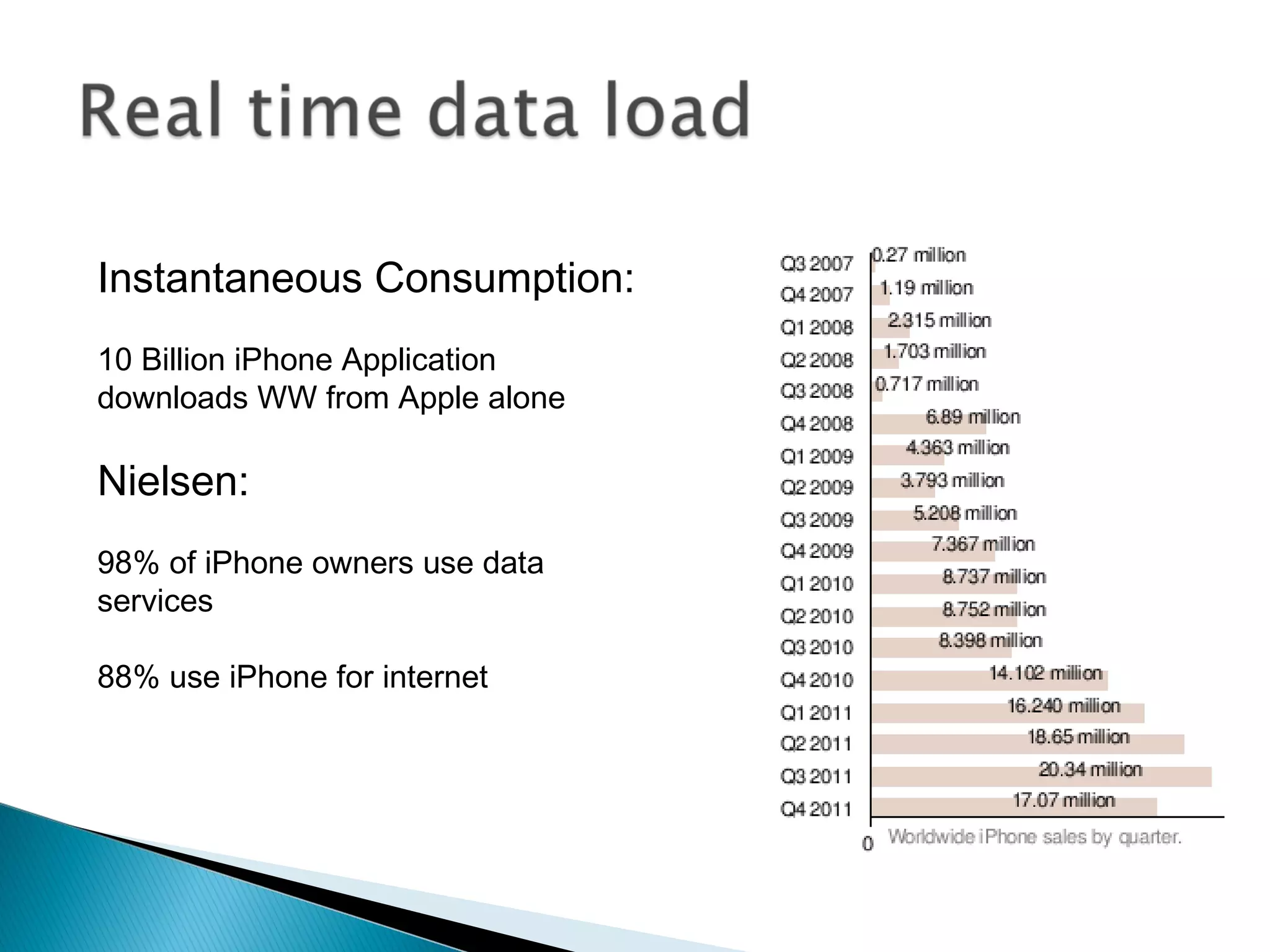
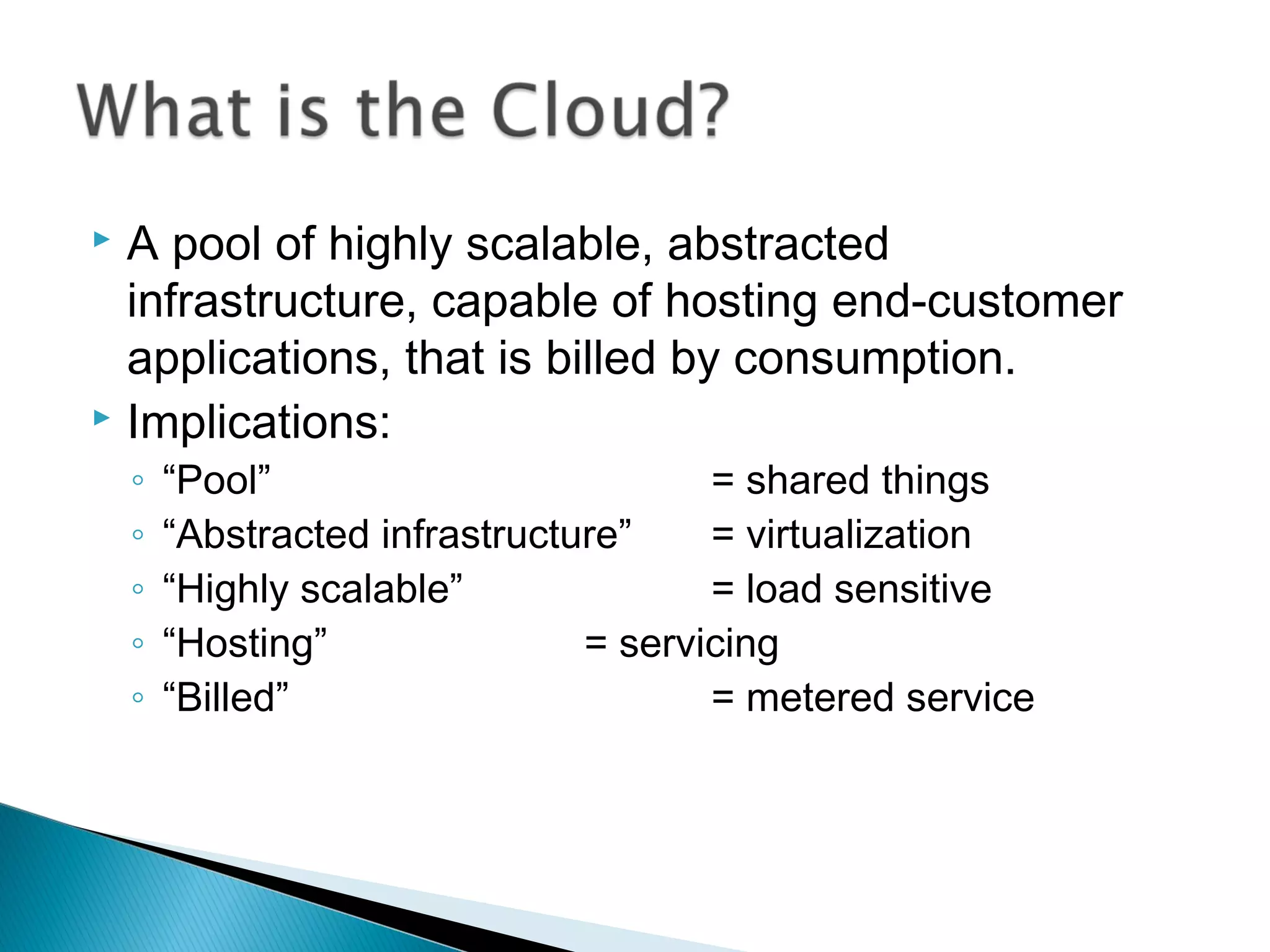
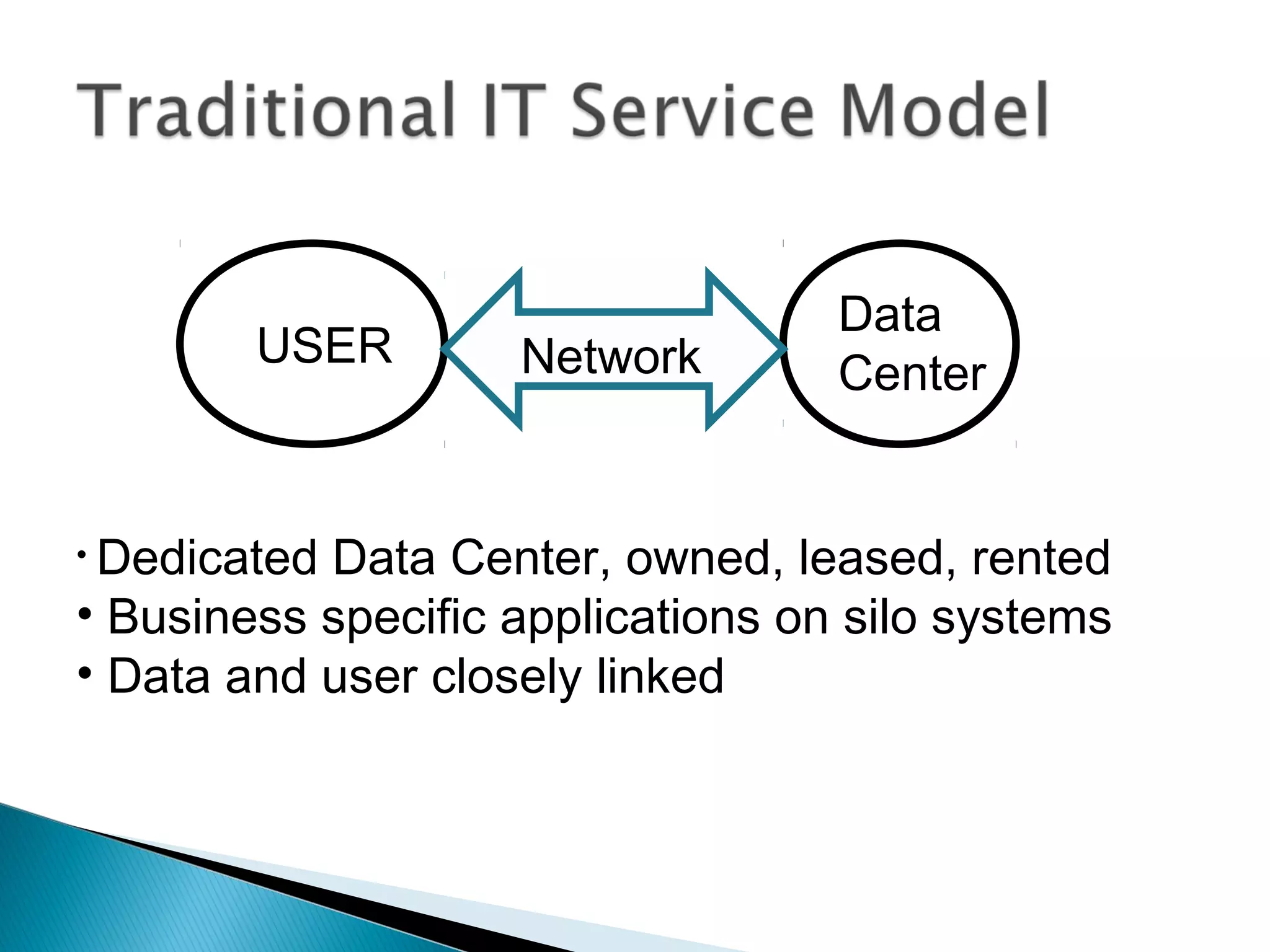
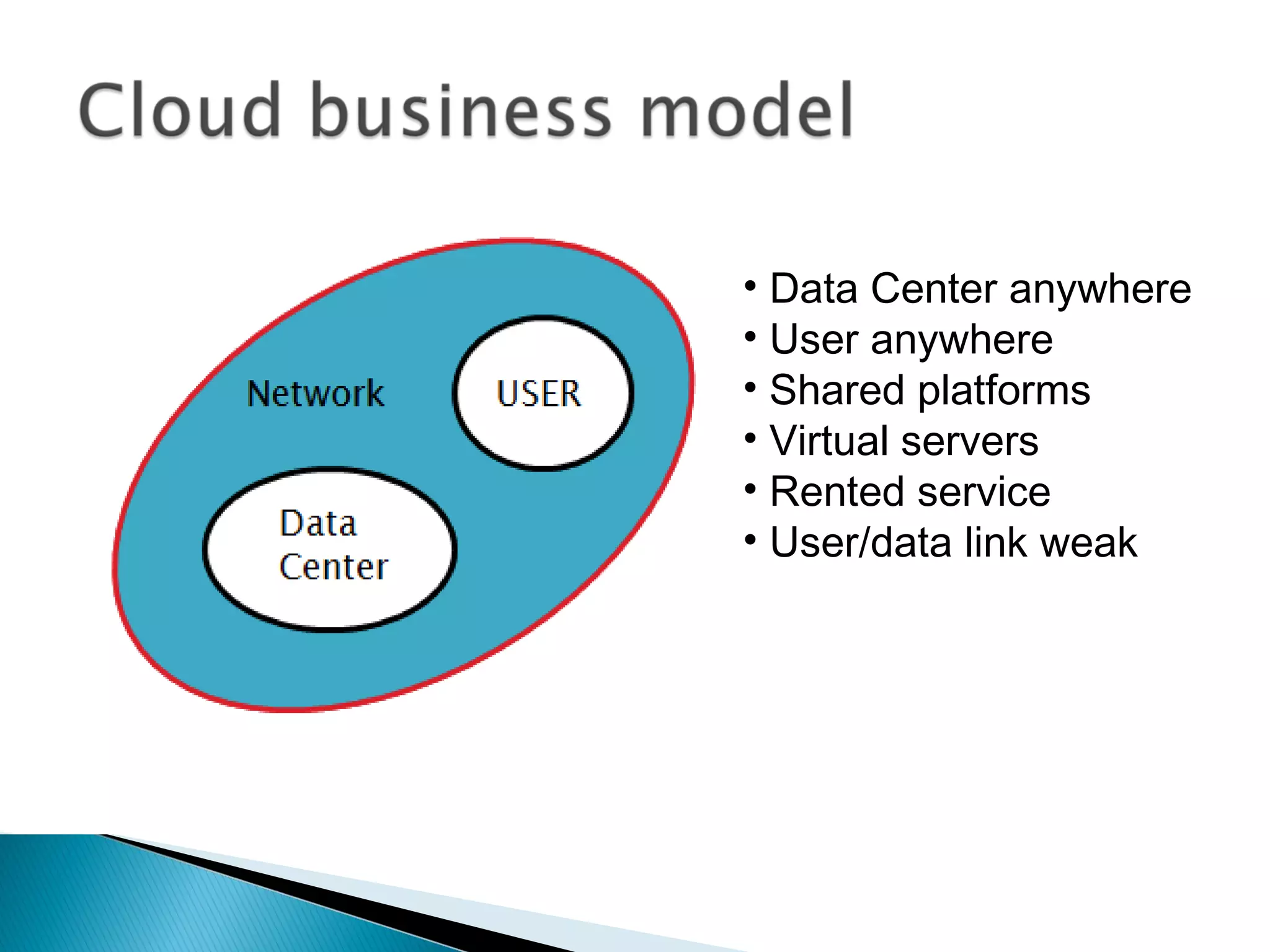
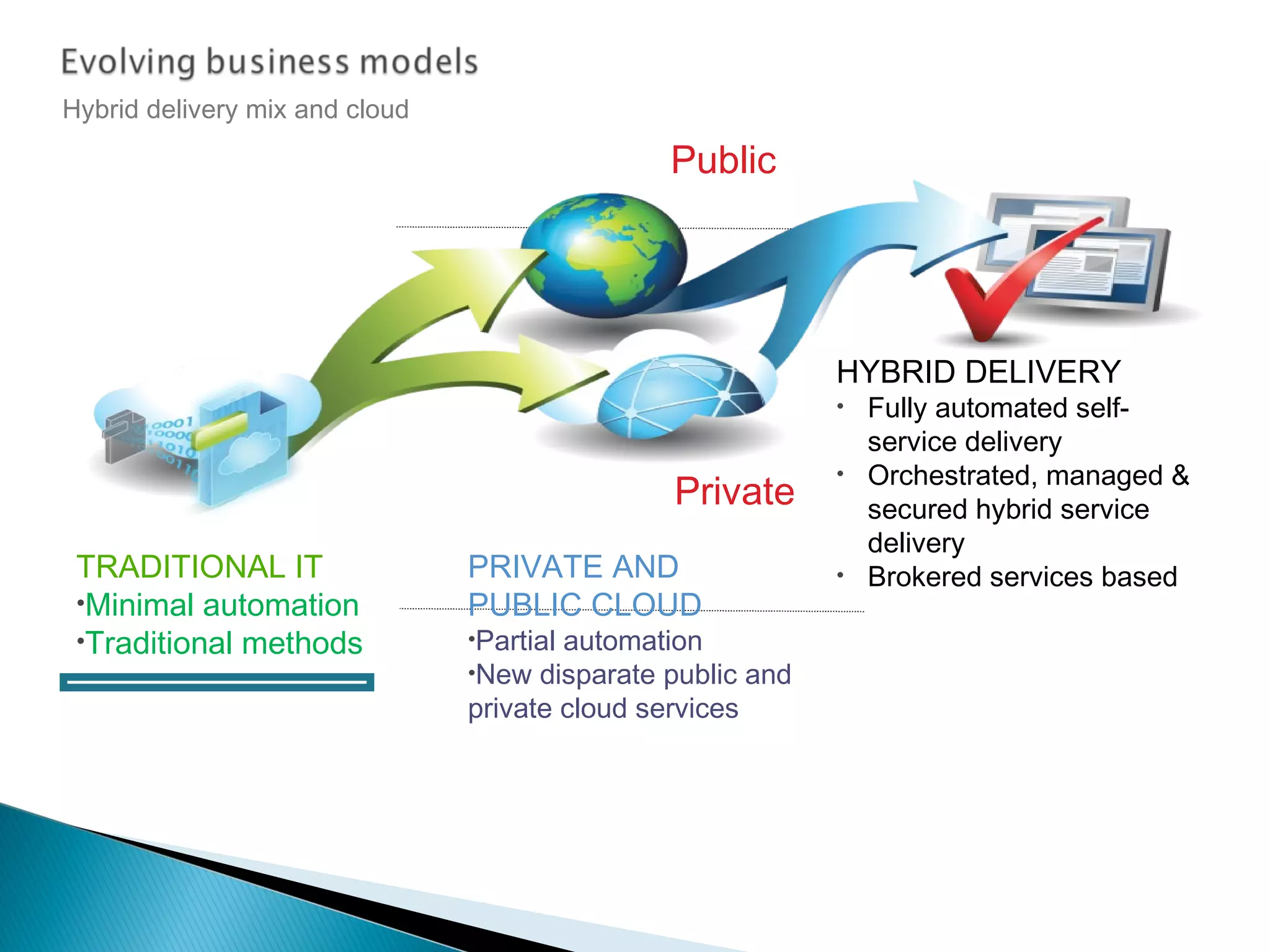
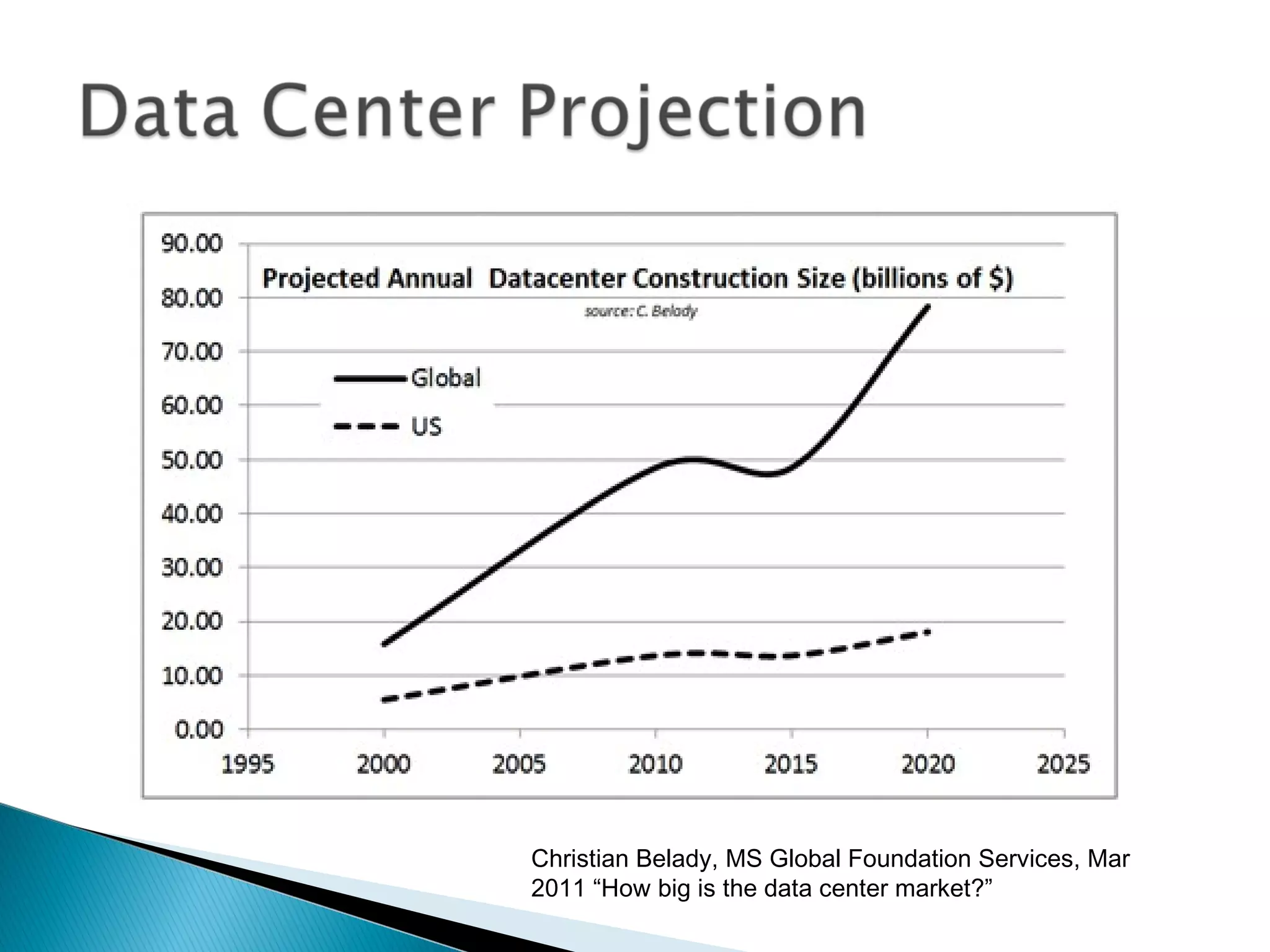
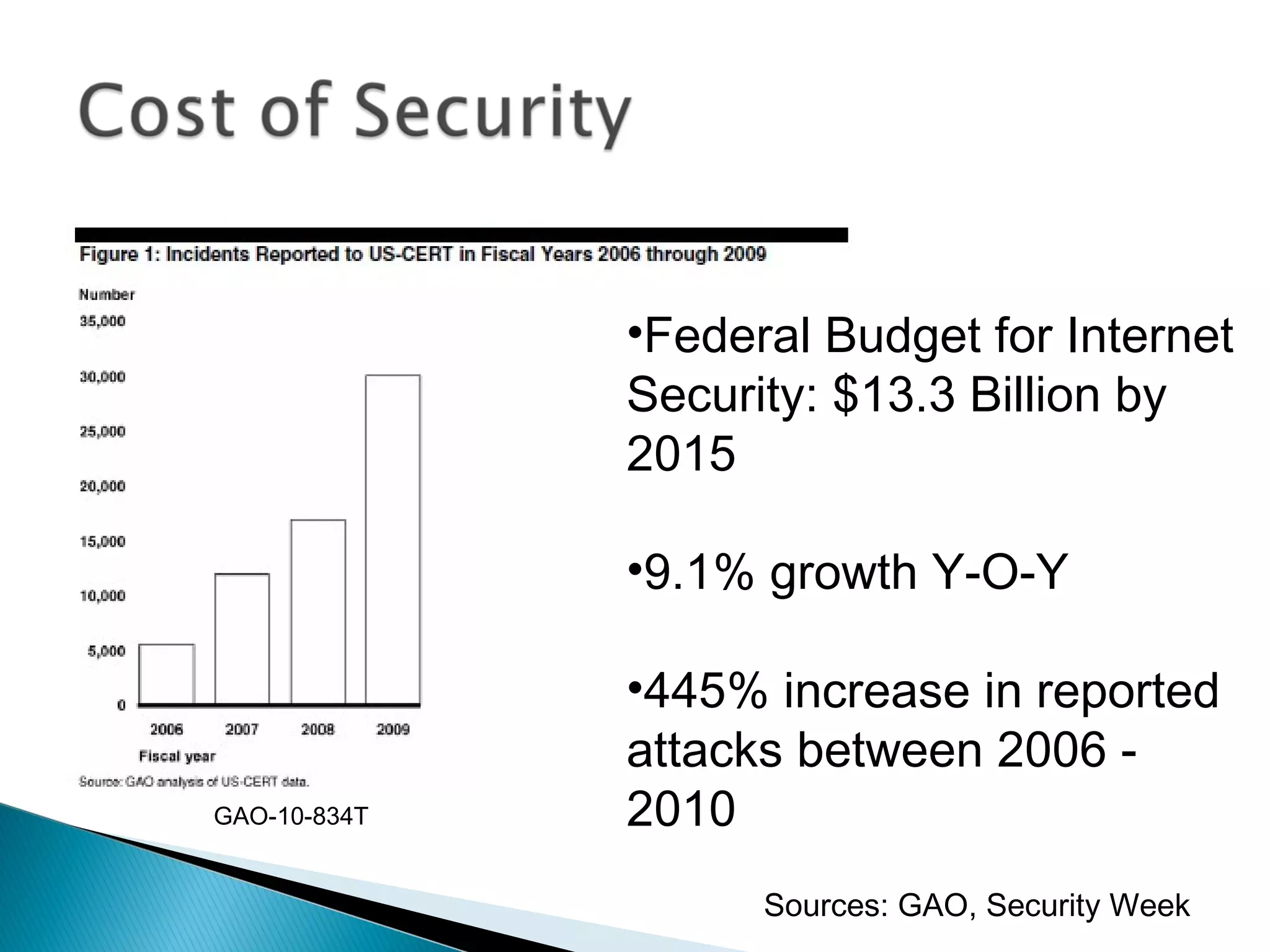
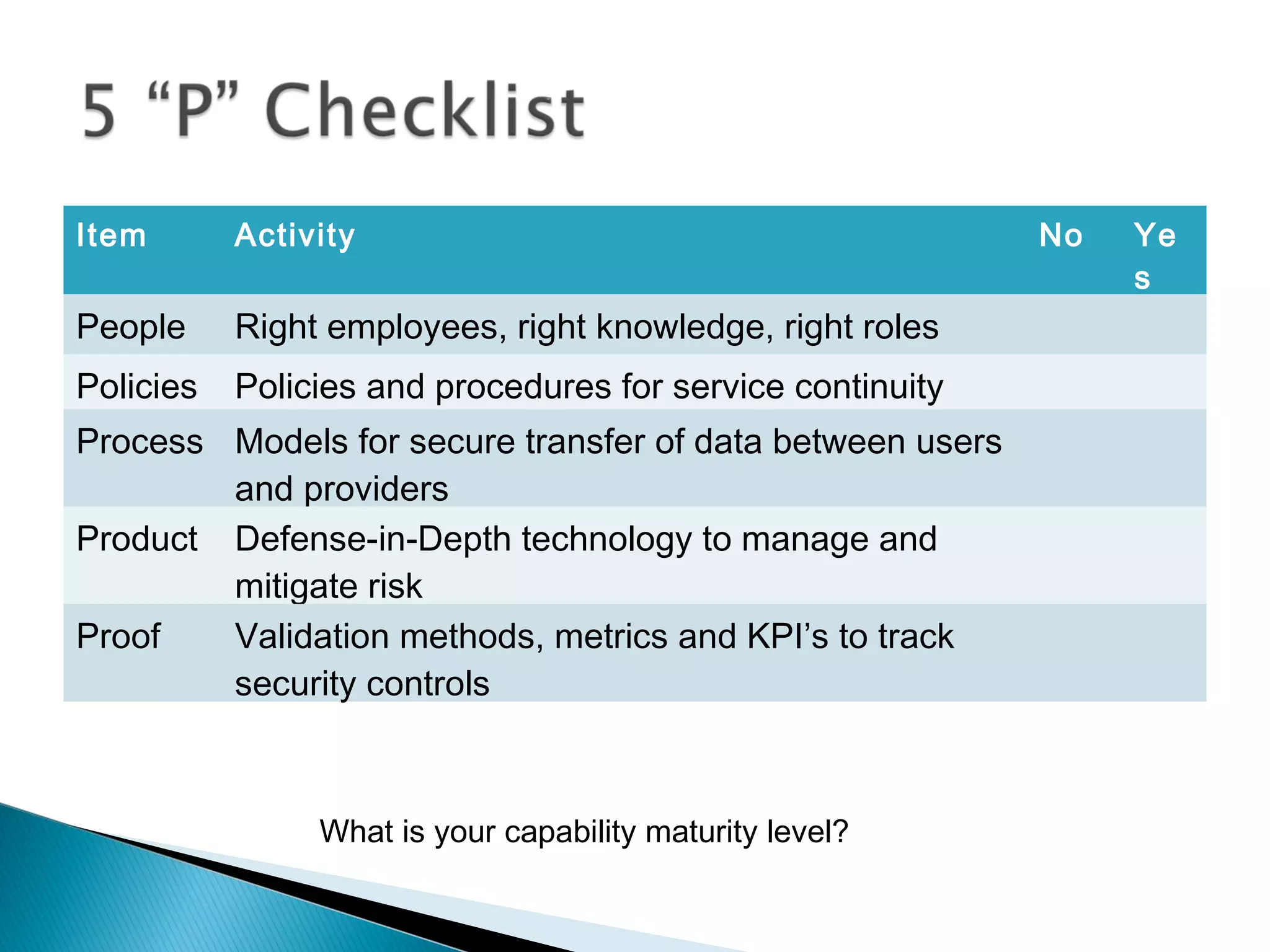
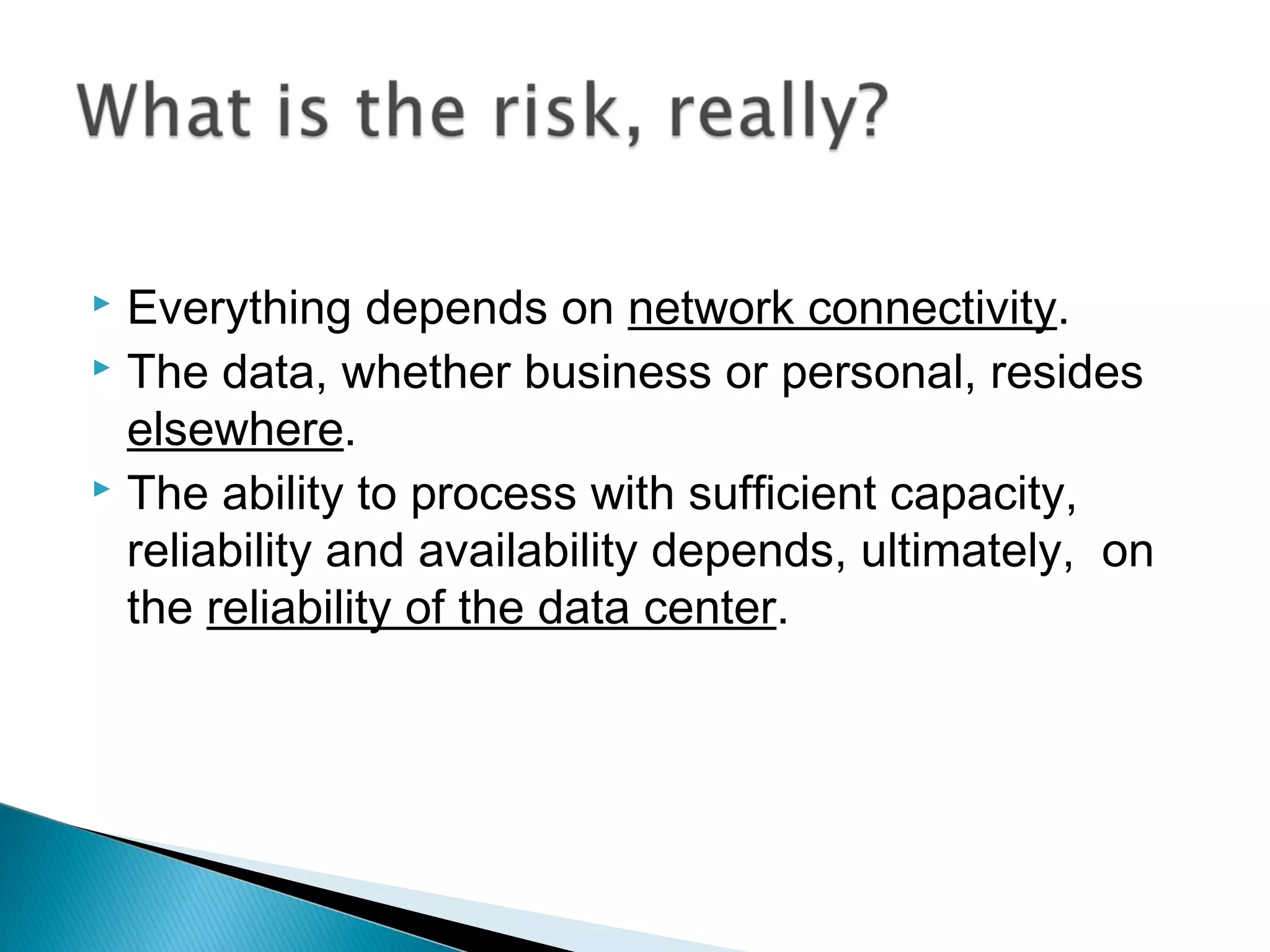
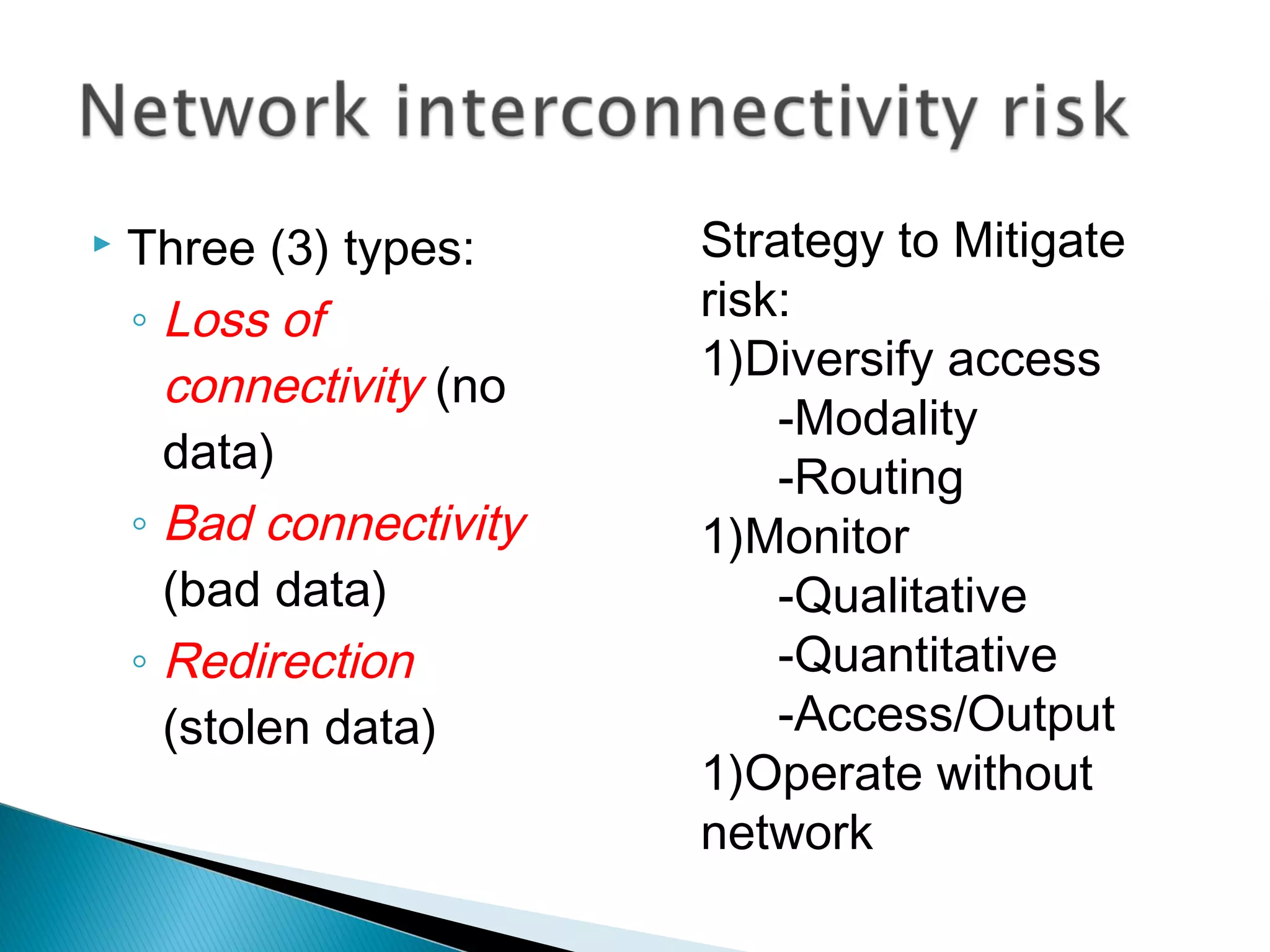
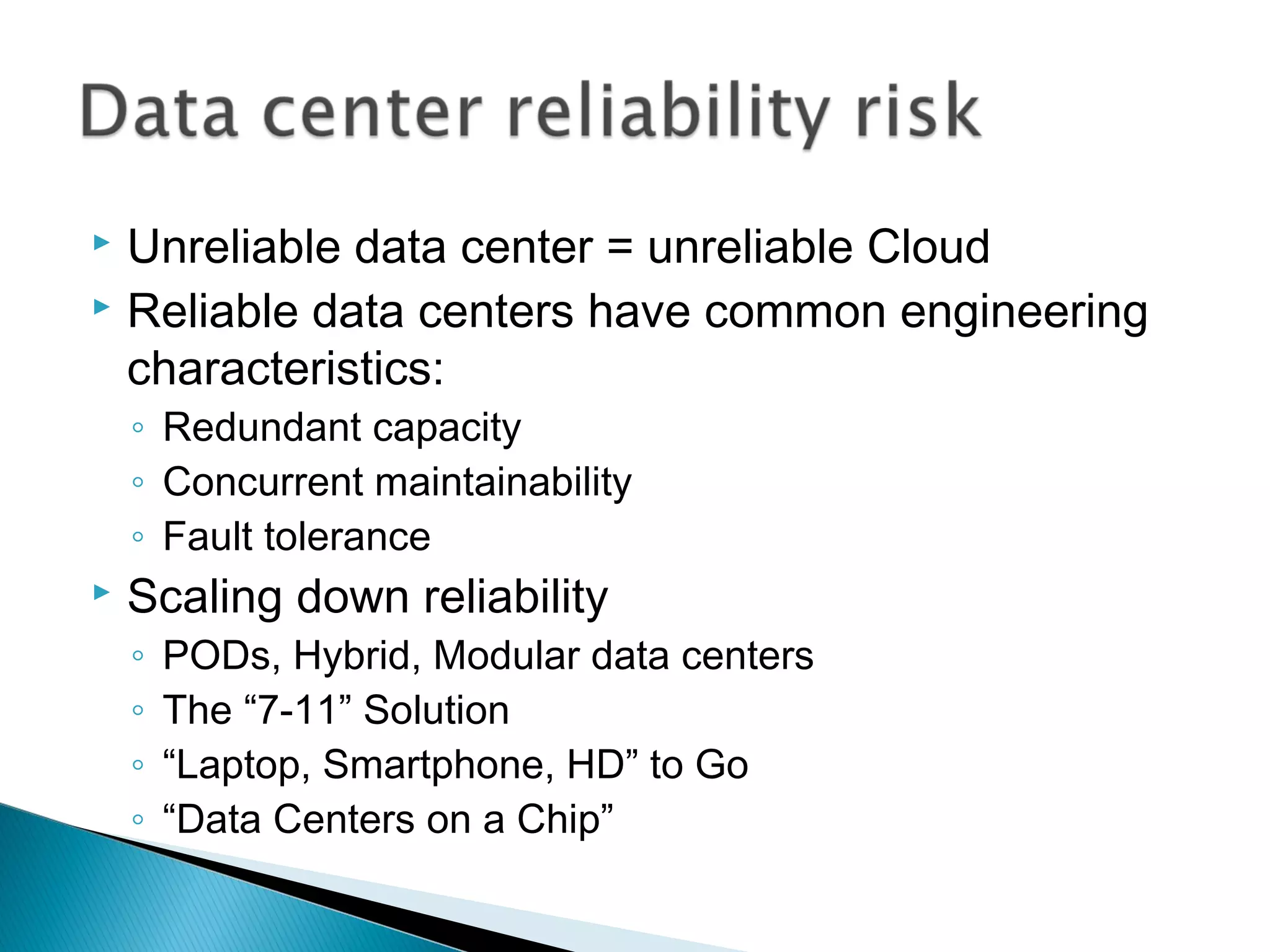
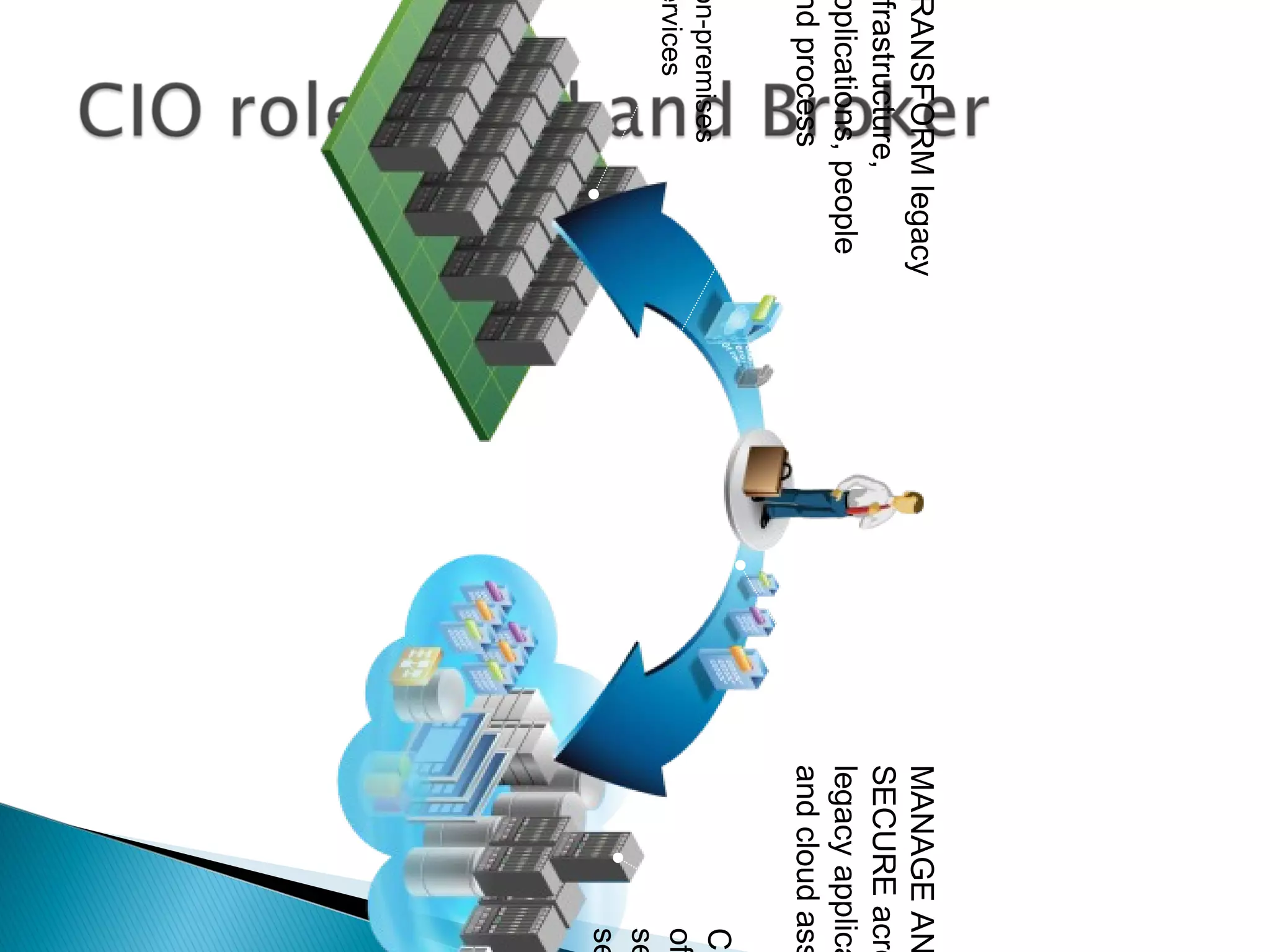
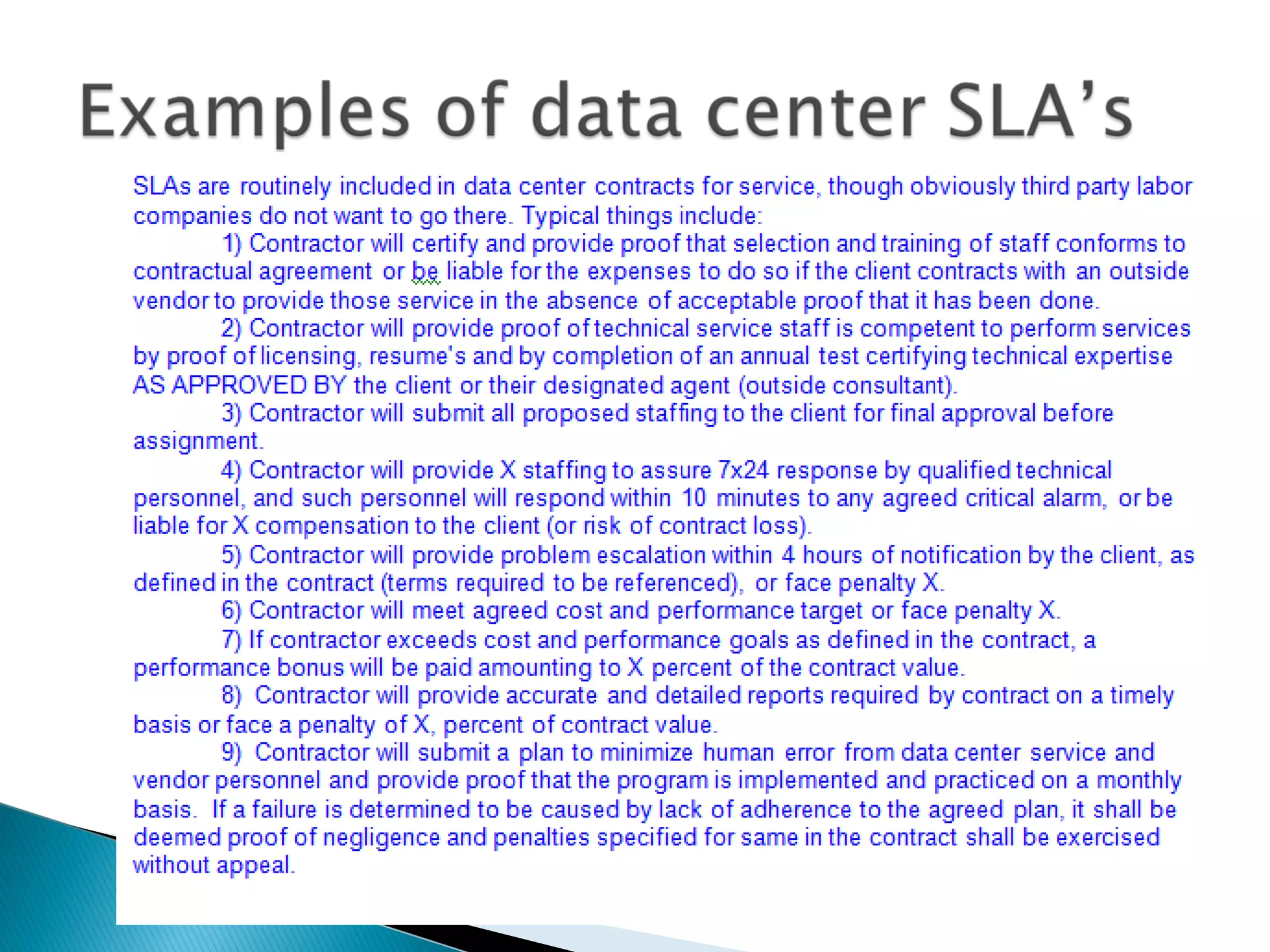
The document discusses the increasing demand for cloud services and data centers, emphasizing the importance of reliable infrastructure and security measures in managing cloud operations. It outlines key challenges such as fraud and data access loss, along with best practices for ensuring data integrity and service continuity. The author encourages organizations to ask critical questions before adopting cloud solutions and highlights the necessity of effective recovery plans.