Embed presentation
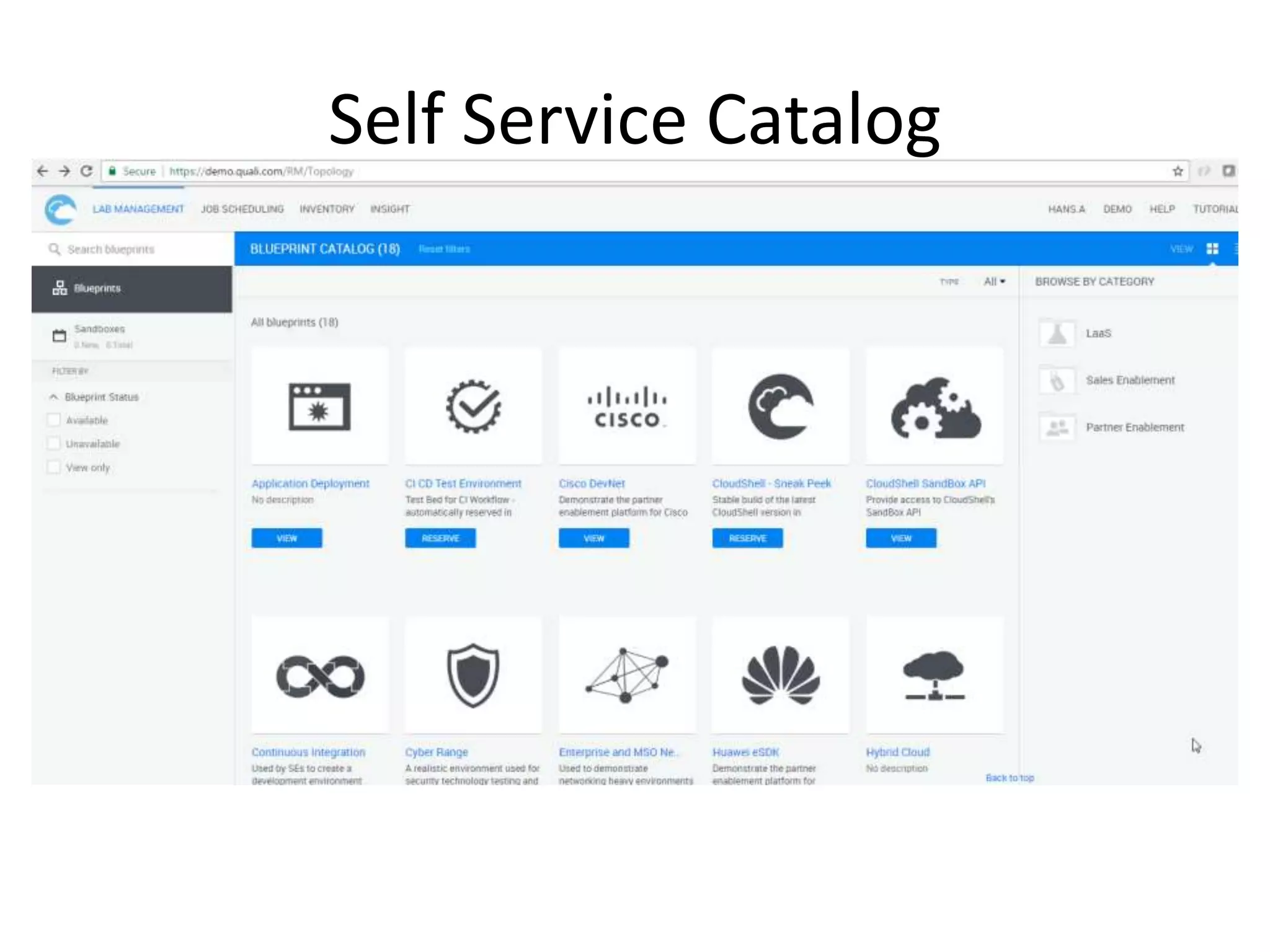
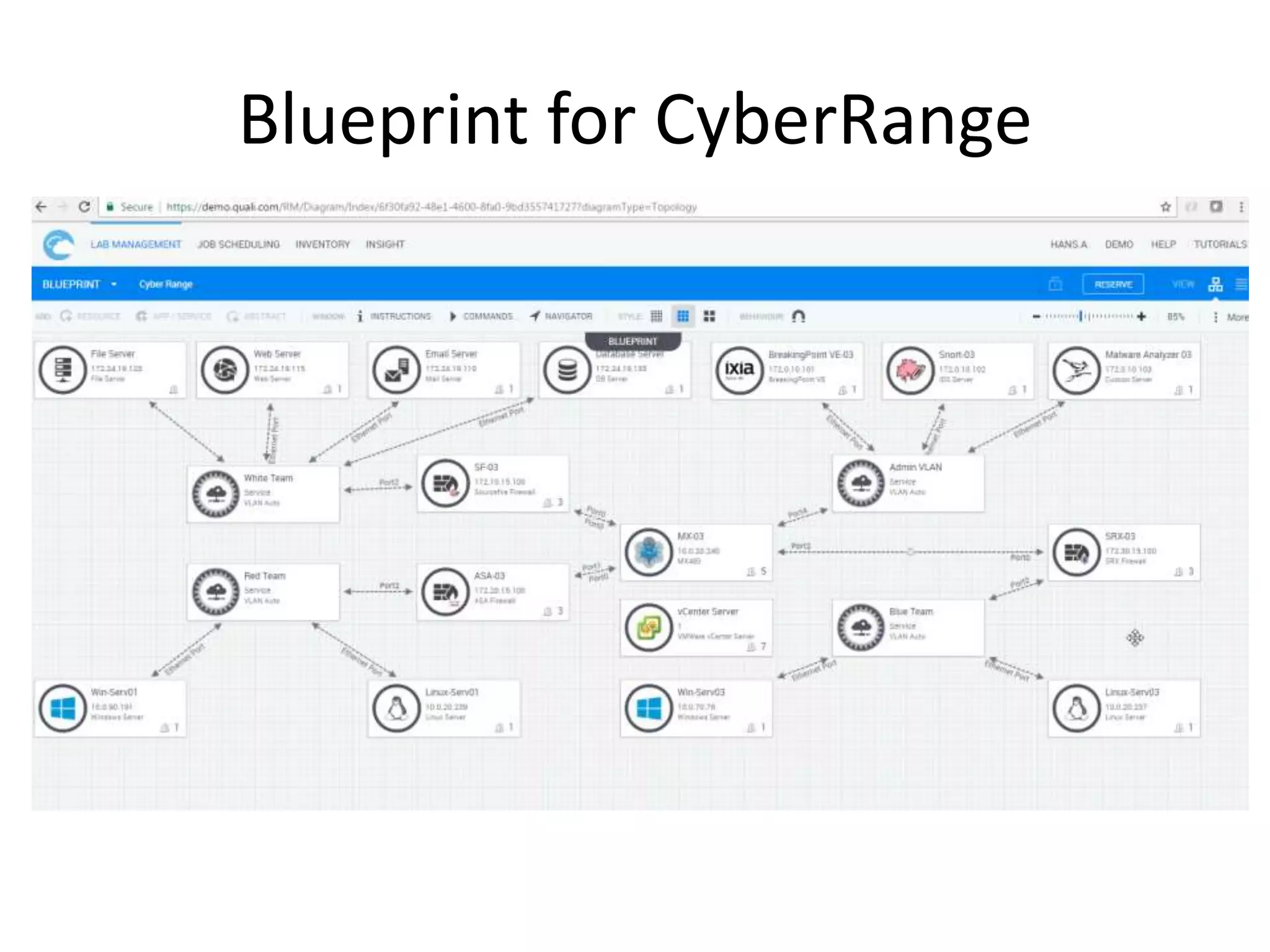
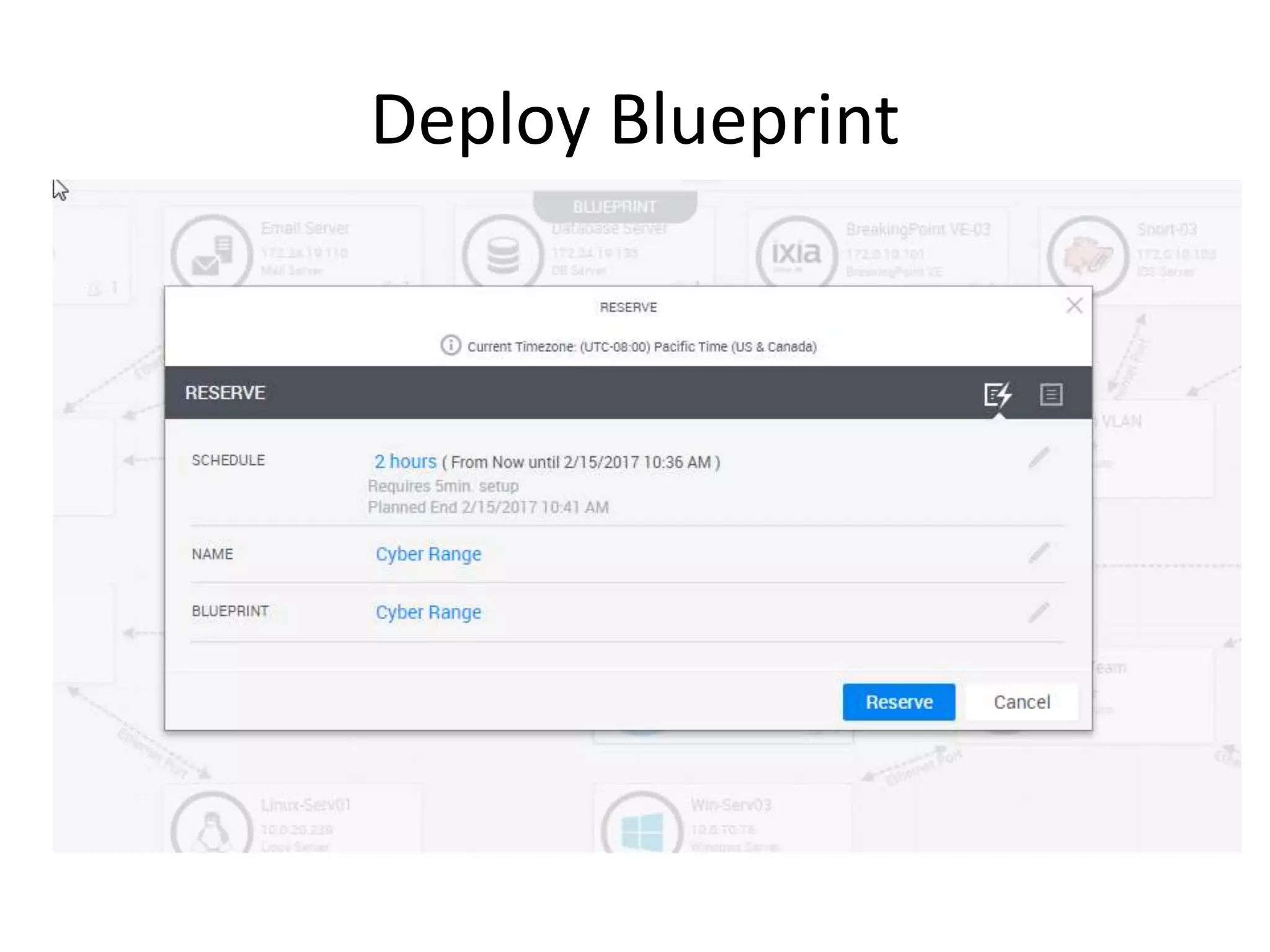
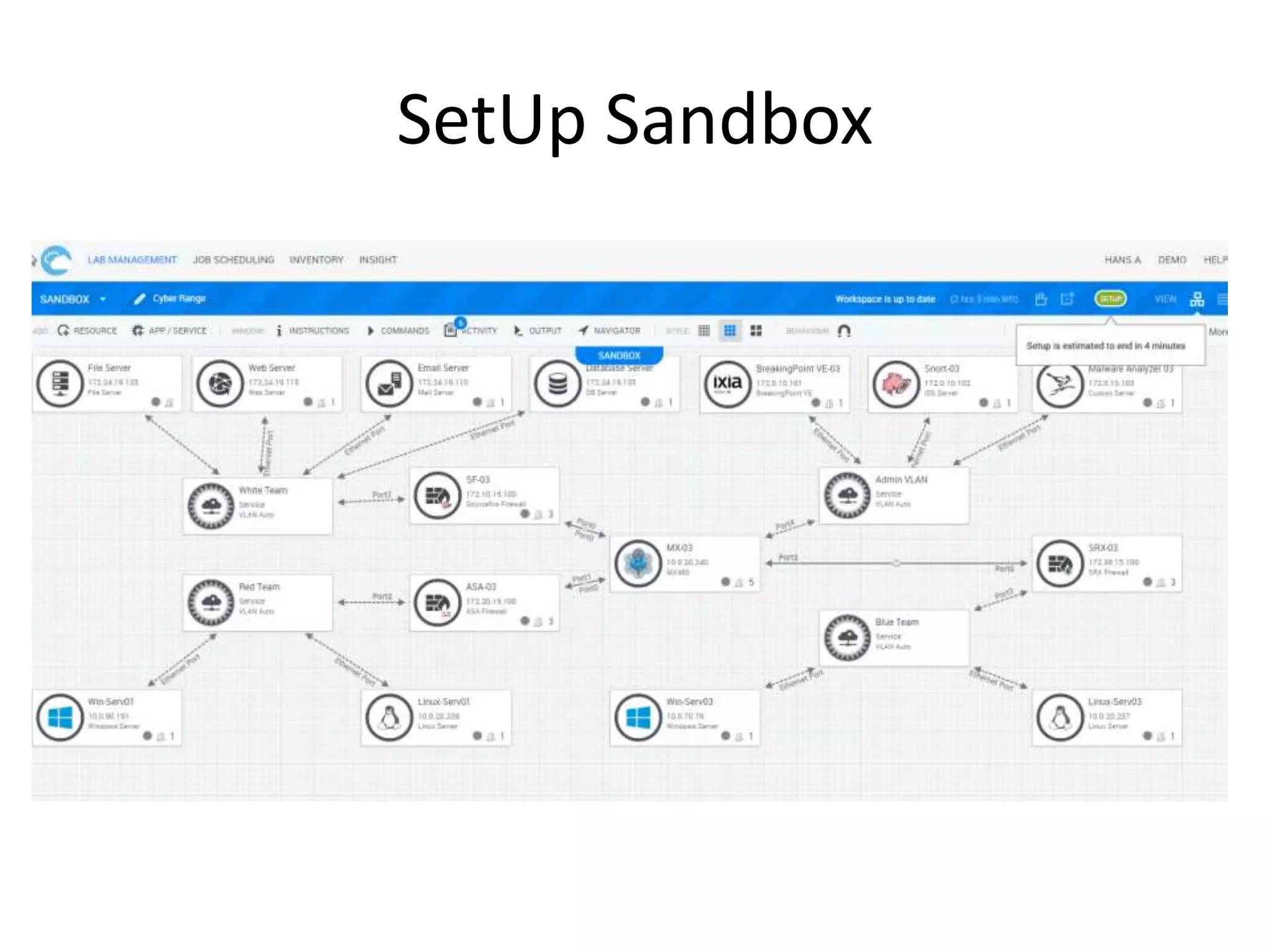
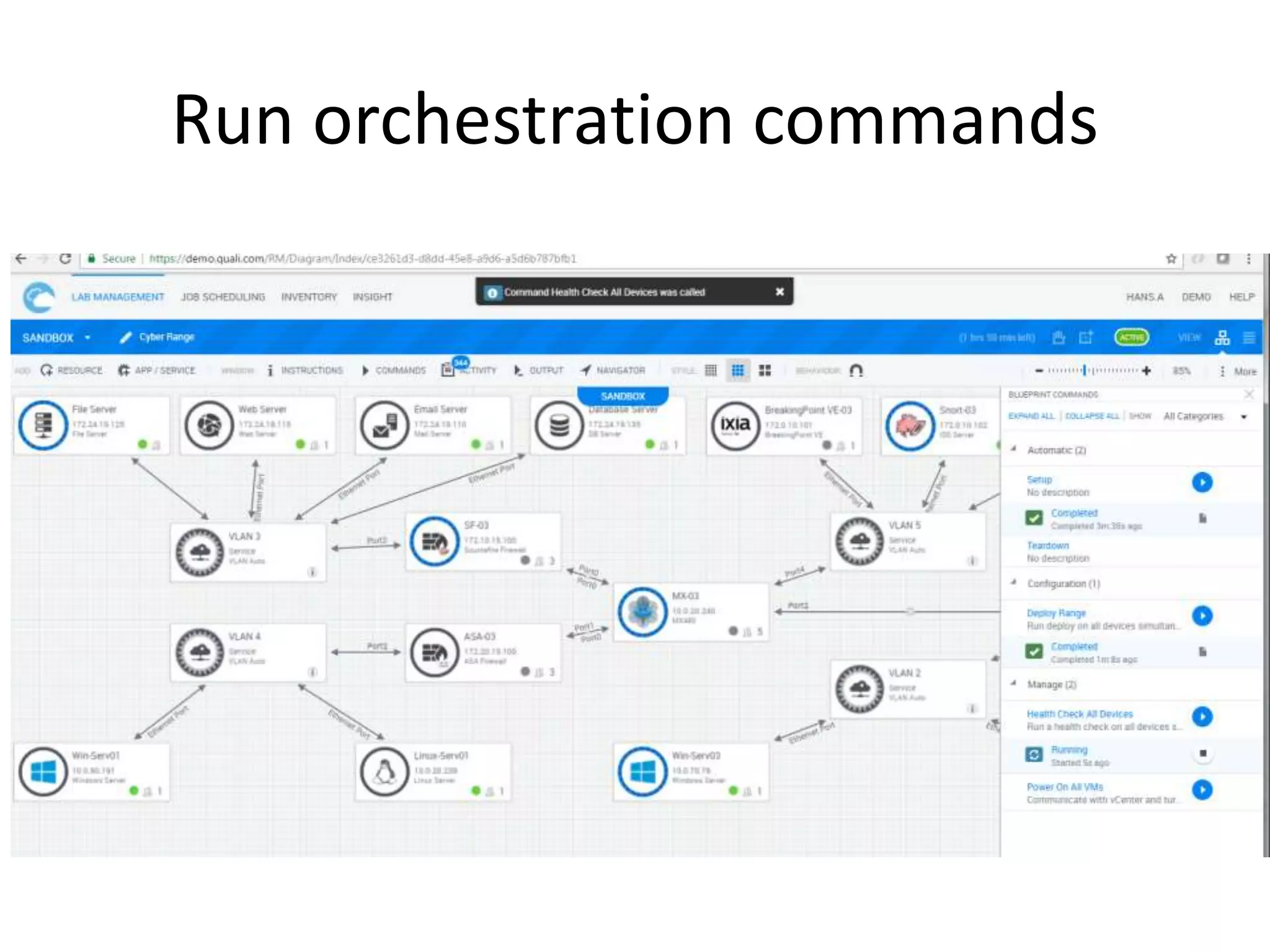
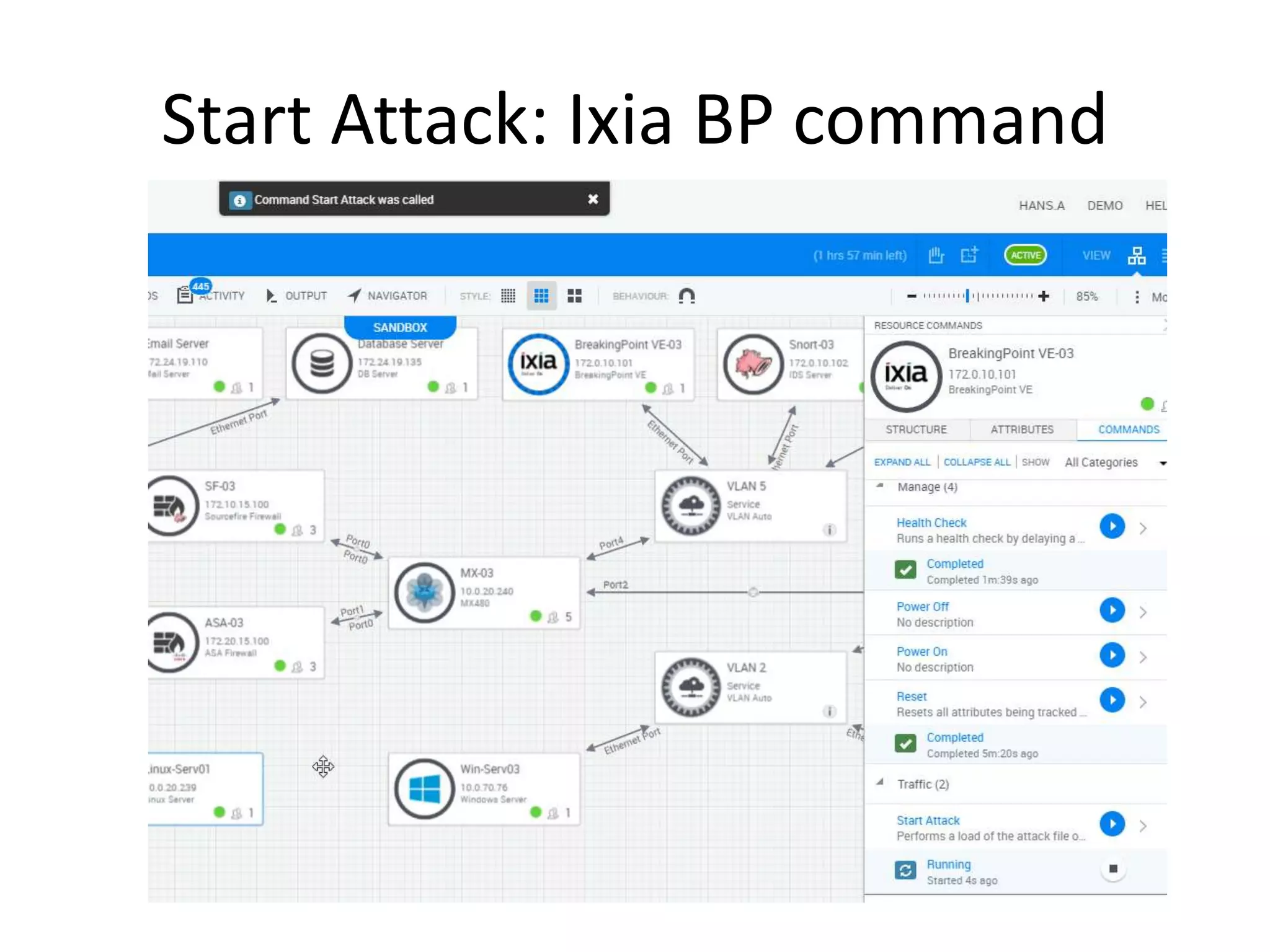
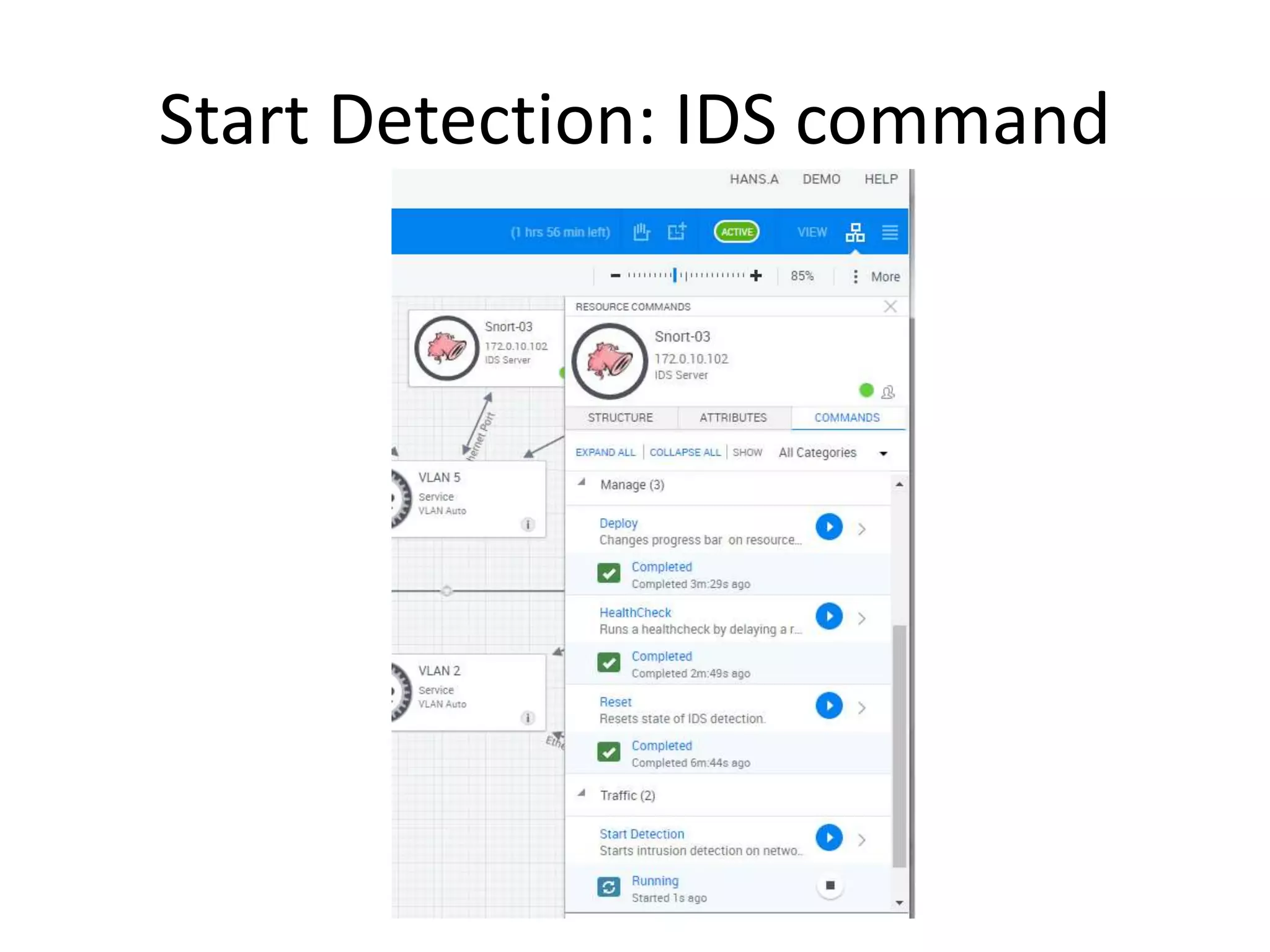
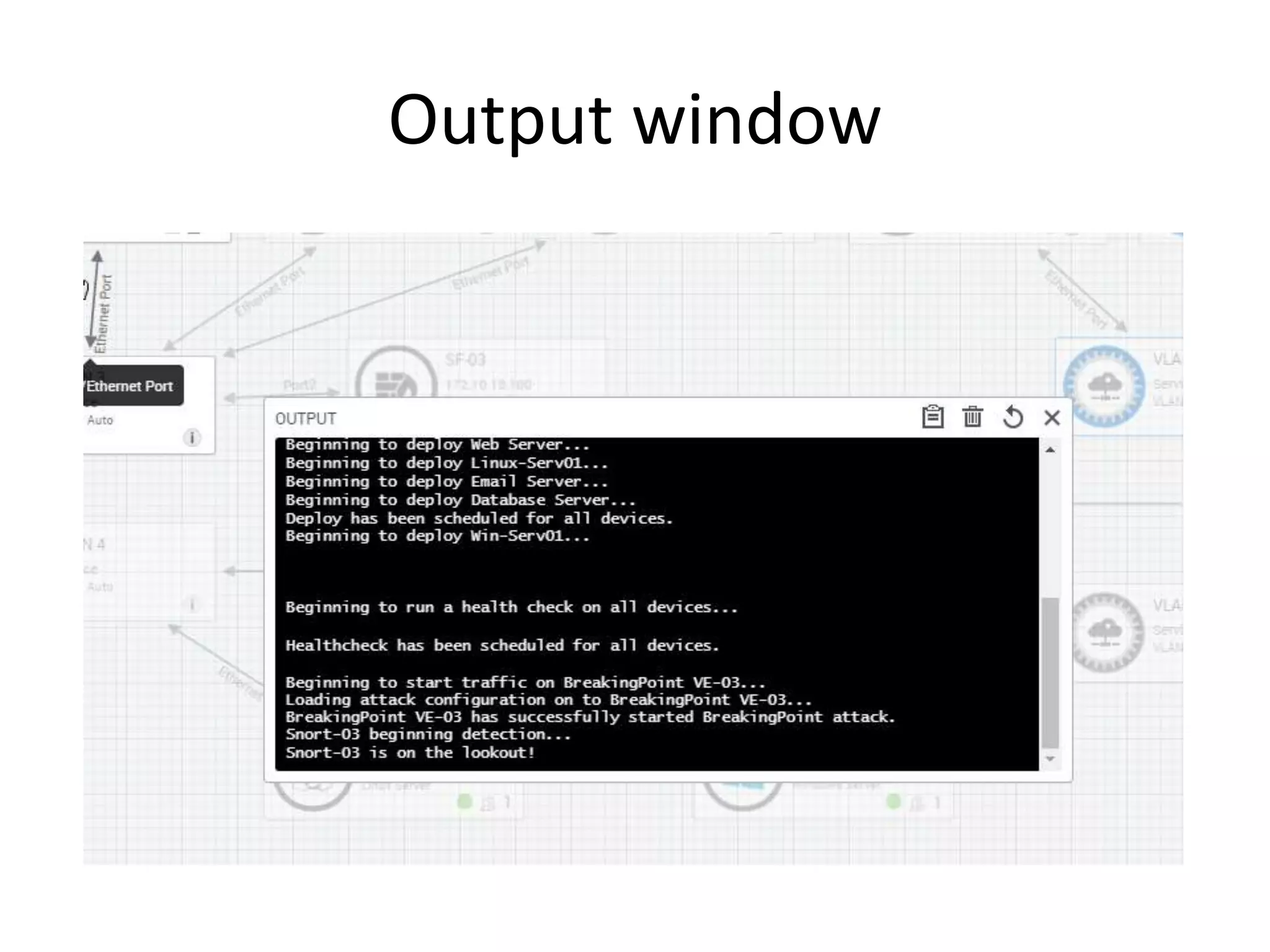
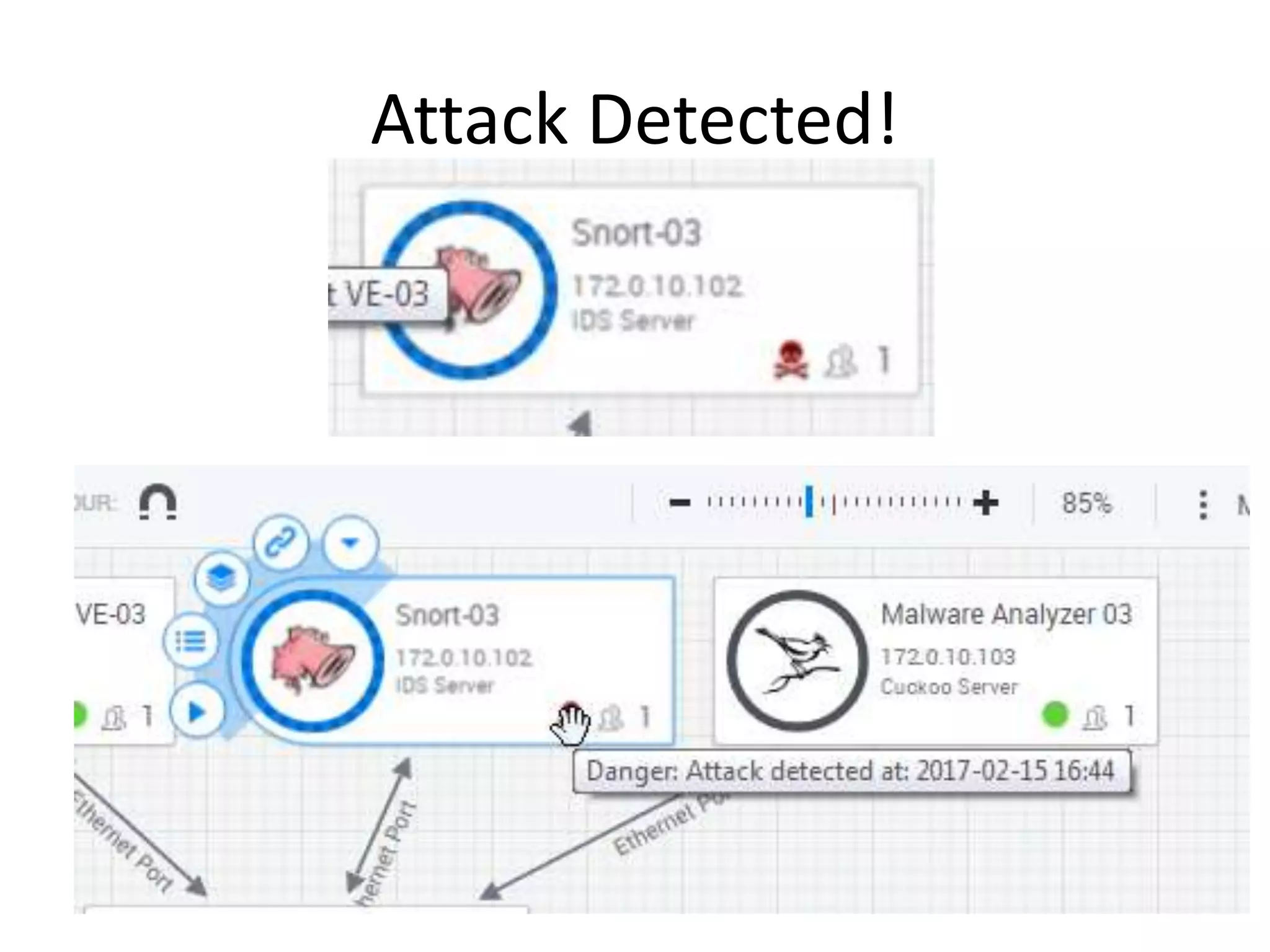
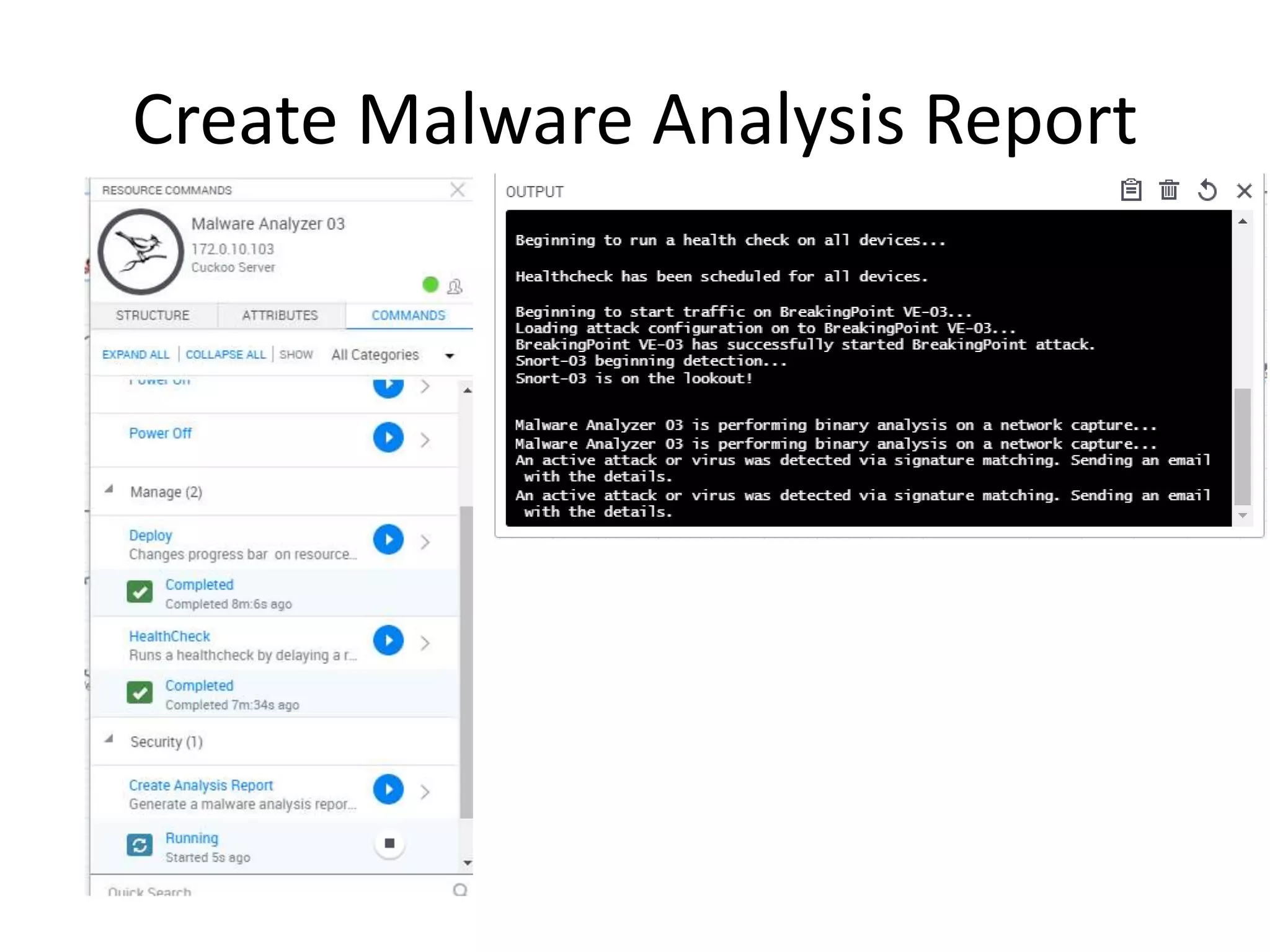
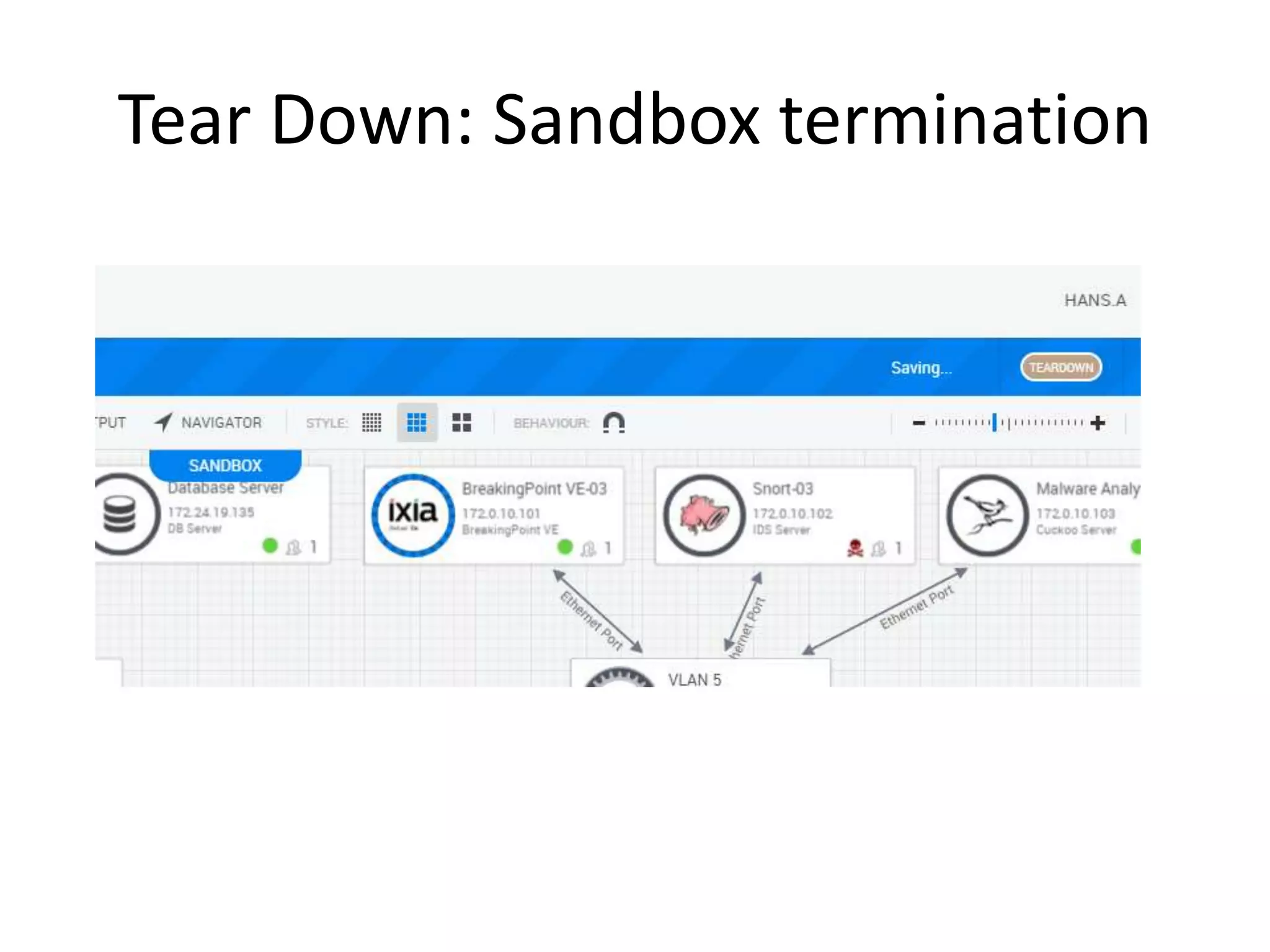
The document outlines a self-service catalog for deploying a cyber range, detailing steps for setting up a sandbox environment and executing orchestration commands to initiate attacks. It includes commands for starting detection systems and generating malware analysis reports. Additionally, it covers the process for terminating the sandbox after analysis.










