This document summarizes key concepts in information security models and engineering from Chapter 4 of the CISSP certification preparation material. It describes 10 common security models including Bell-LaPadula, Biba, and Clark-Wilson models. It also covers security concepts like security domains, the ring model, and evaluation methods like the Orange Book, ITSEC, and Common Criteria. Finally, it summarizes secure hardware architecture principles such as layering, abstraction, and memory protection.











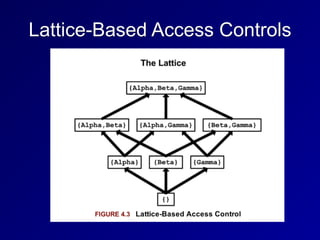
![Lattice-Based Access Controls
• Subjects and objects have various
classifications, such as clearance, need-
to-know, and role
• Subjects have a Lease Upper Bound and
a Greatest Lower Bound of access
• The highest level of access is "[Alpha,
Beta, Gamma]"](https://image.slidesharecdn.com/ch4a-160509170305/85/CISSP-Prep-Ch-4-Security-Engineering-Part-1-13-320.jpg)