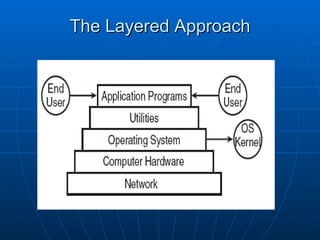
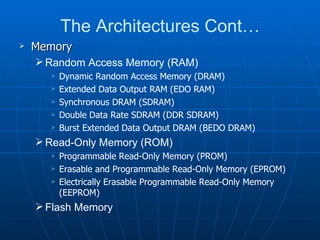
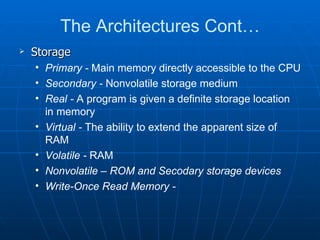
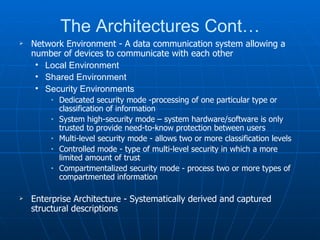
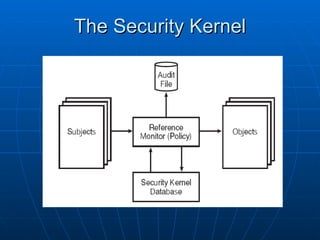
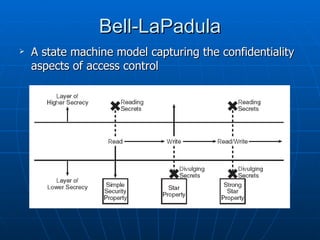
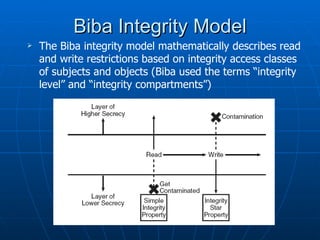
This document discusses security architecture and models at a high level. It covers security models related to confidentiality, integrity and information flow. It also discusses differences between commercial and government security requirements. The document outlines the role of evaluation criteria such as TCSEC, ITSEC and CC. It briefly discusses security practices for the Internet like IPSec. It provides an overview of technical platforms involving hardware, firmware and software. It also touches on system security techniques including preventative, detective and corrective controls.