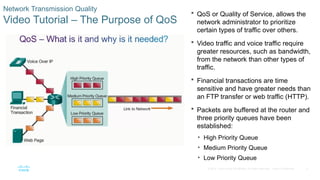
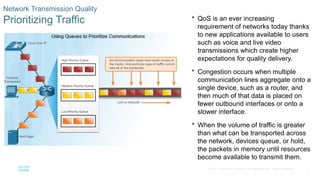
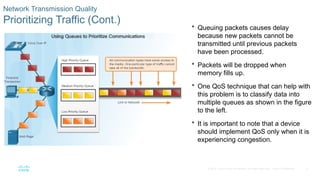
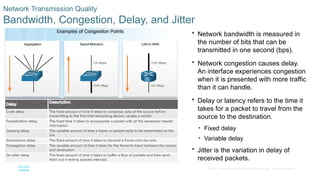
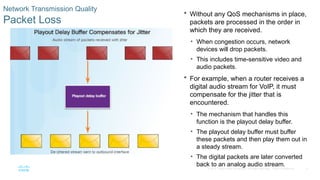
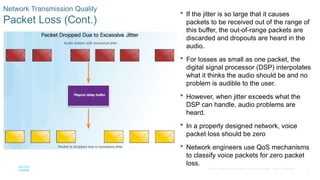
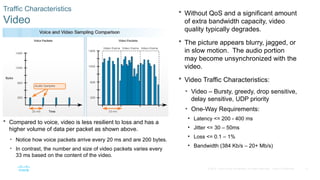
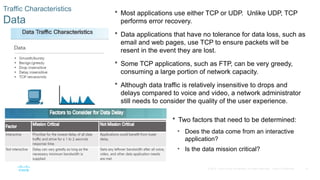
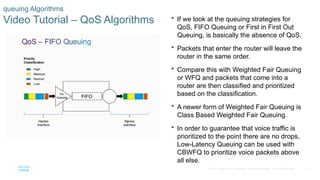
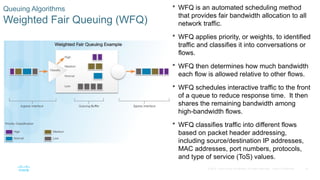
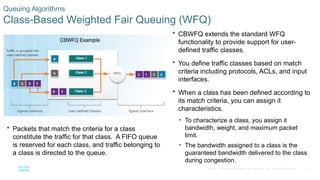
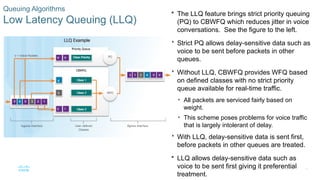
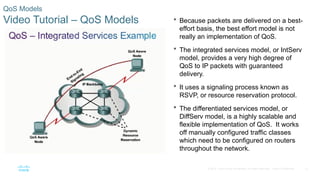
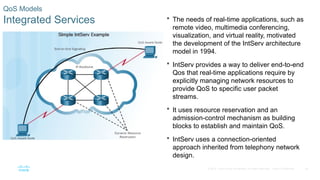
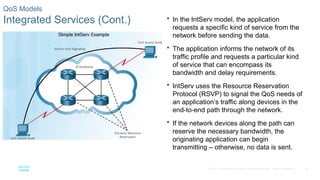
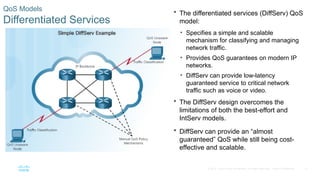
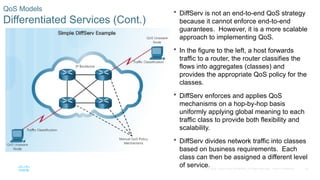
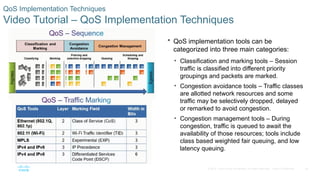
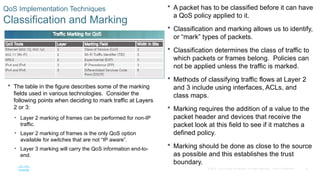
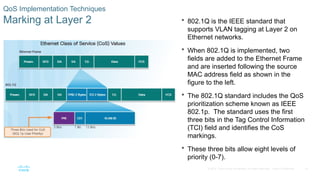
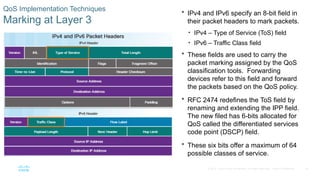
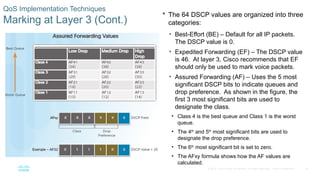
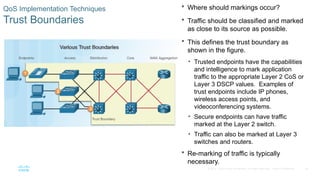
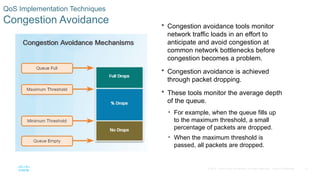
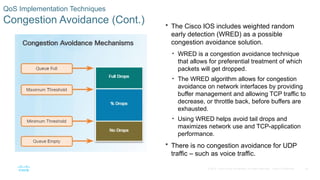
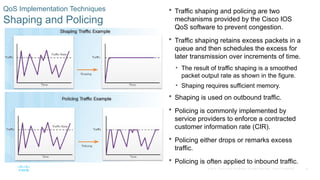
Chapter 6 of the CCNA Routing and Switching Connecting Networks v6.0 discusses Quality of Service (QoS), explaining its purpose in prioritizing network traffic, particularly for voice and video, which require greater resources and lower latency. It details various mechanisms and queuing algorithms, including FIFO, WFQ, CBWFQ, and LLQ, to manage congestion and ensure efficient packet transmission. The chapter also covers QoS models such as IntServ and DiffServ, highlighting their roles in providing guaranteed service levels for different types of network traffic.