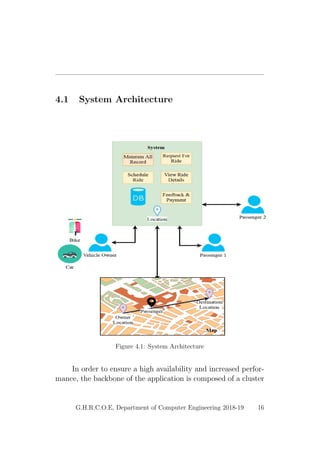
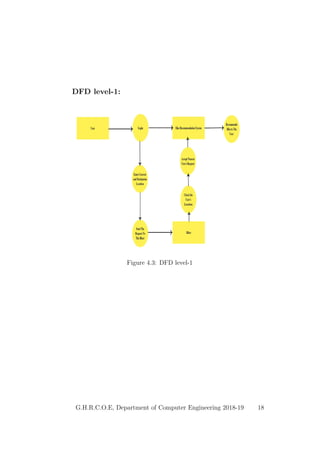
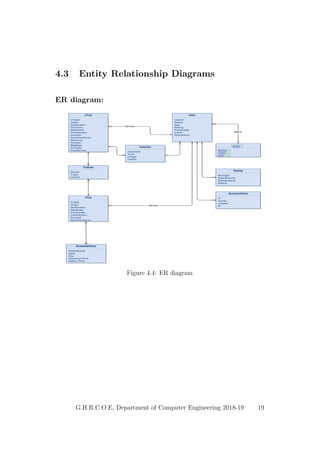
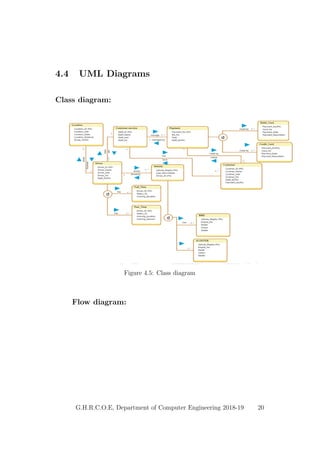
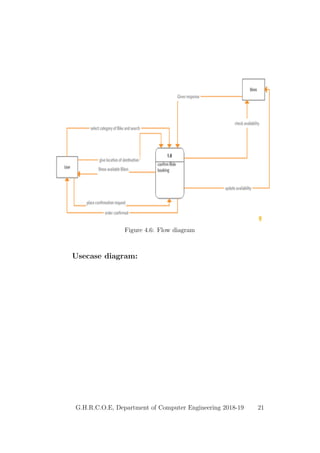
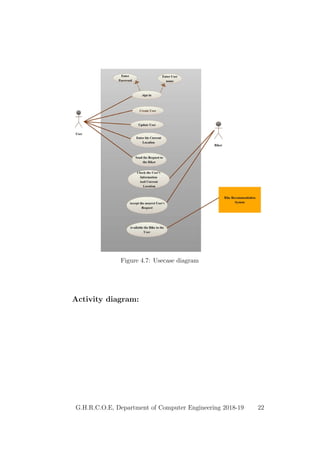
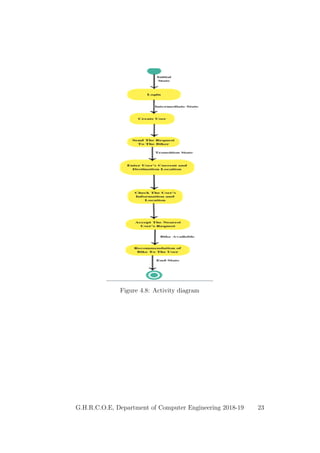
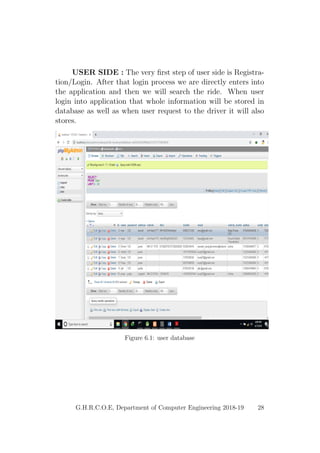
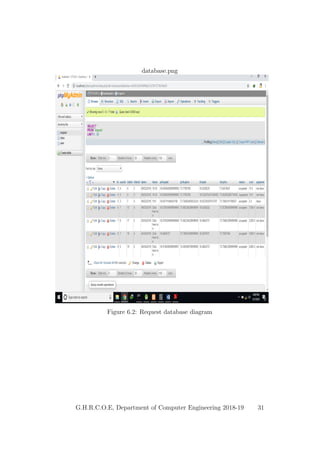
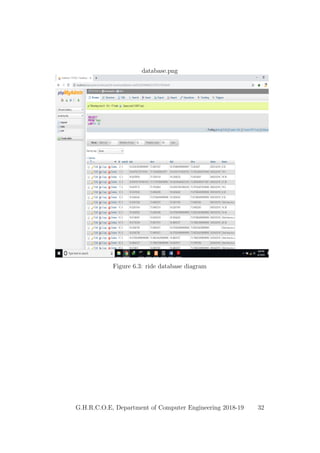
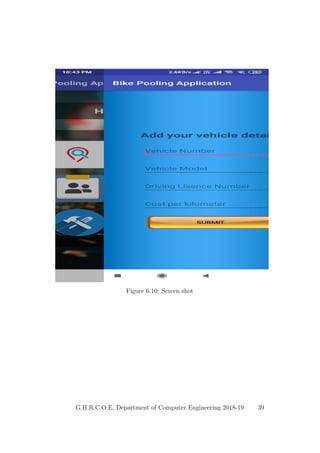
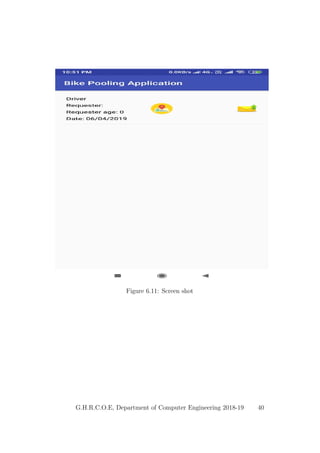
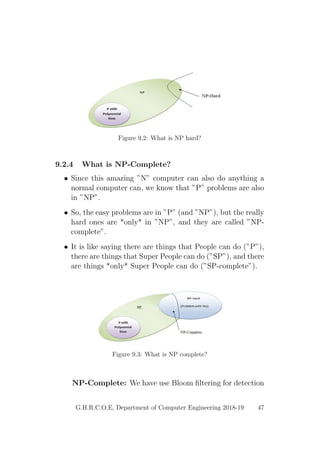
This document provides a project report on developing a bike sharing Android application. It includes an introduction describing the motivation for the project, a literature survey reviewing papers on related topics like bike and public transport integration, a software requirements specification outlining the requirements, a system design section with diagrams, and plans for system implementation and testing. The report was submitted by students to fulfill the requirements for a degree in computer engineering.