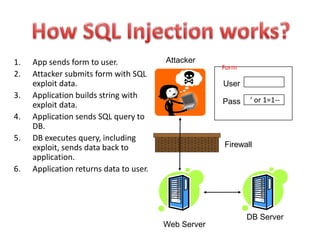
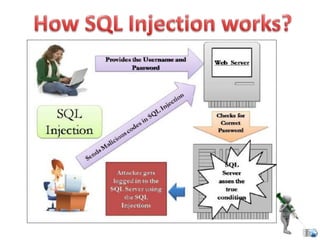
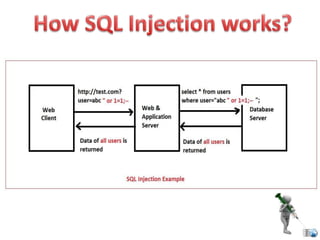
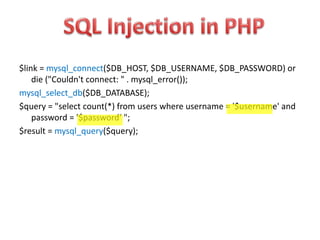
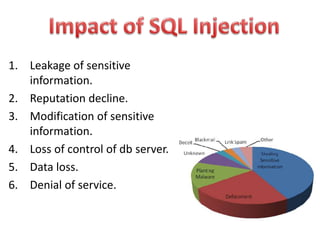
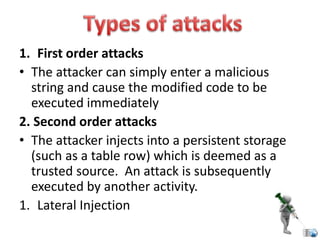
SQL injection is a code injection technique used to attack data-driven applications by inserting malicious SQL statements into entry fields. It allows attackers to gain unauthorized access, modify, or delete data, leading to significant security breaches as demonstrated by high-profile cases. Defenses against SQL injection include data sanitization, the use of web application firewalls, and limiting database privileges.