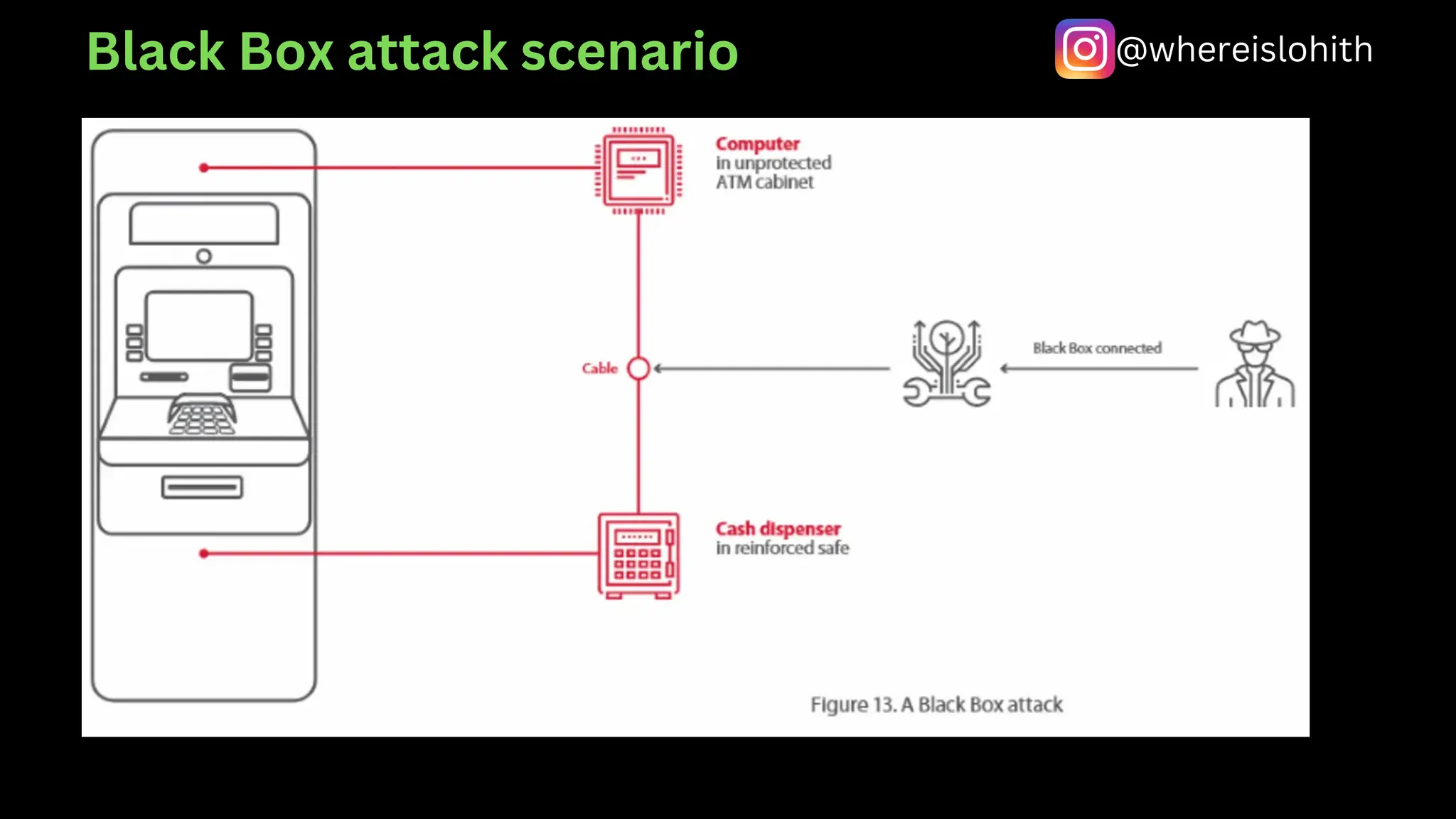
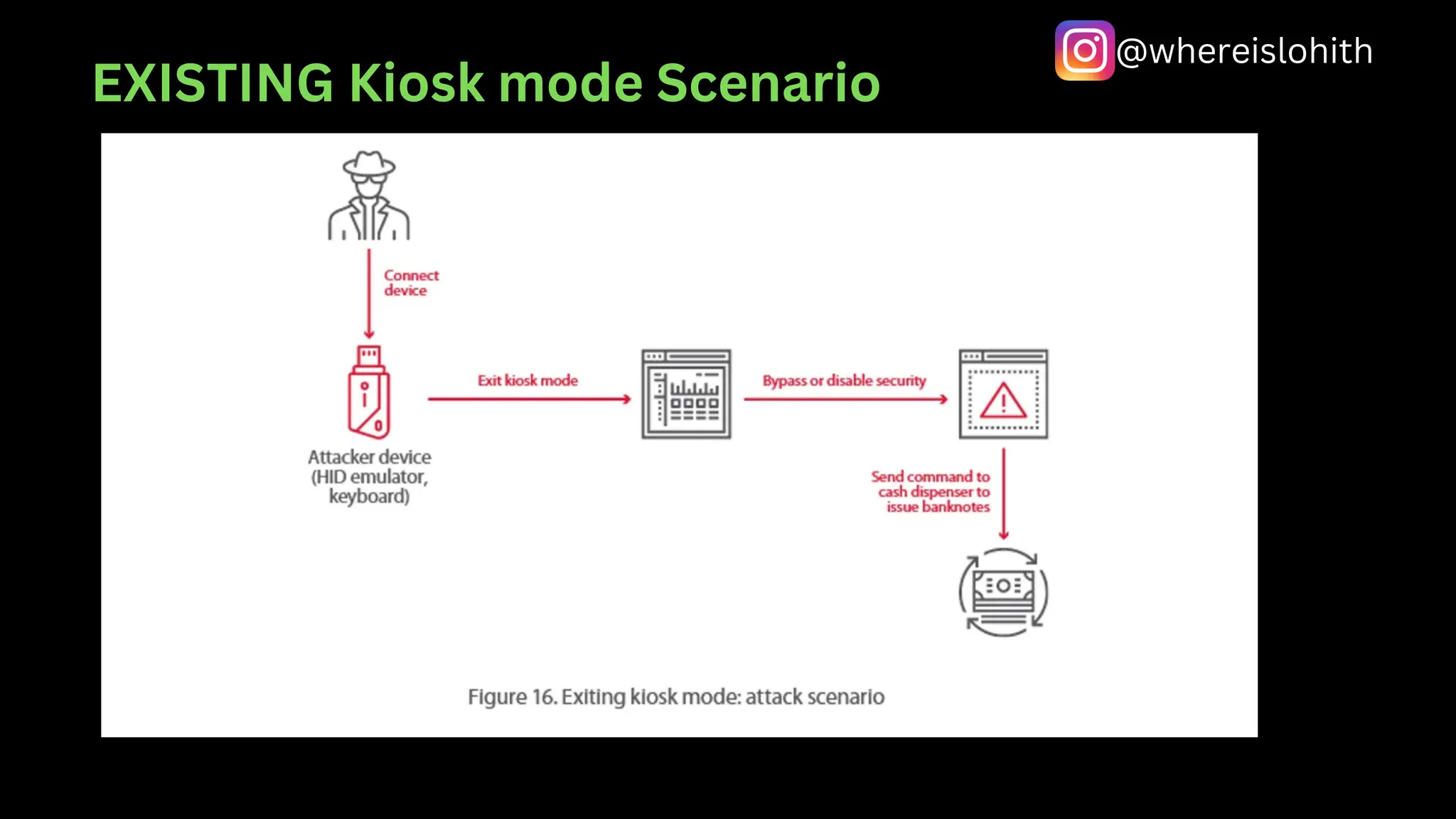
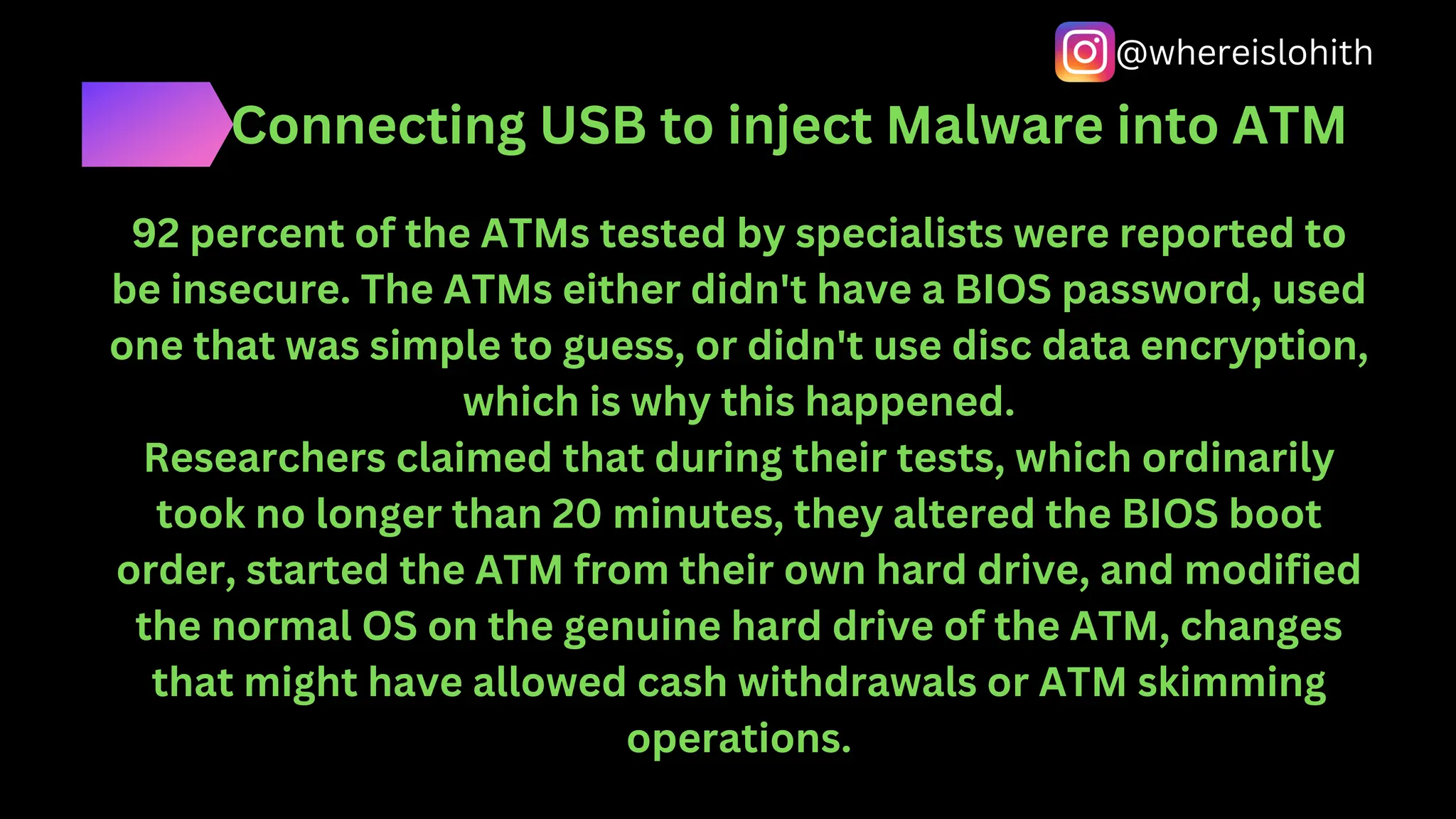
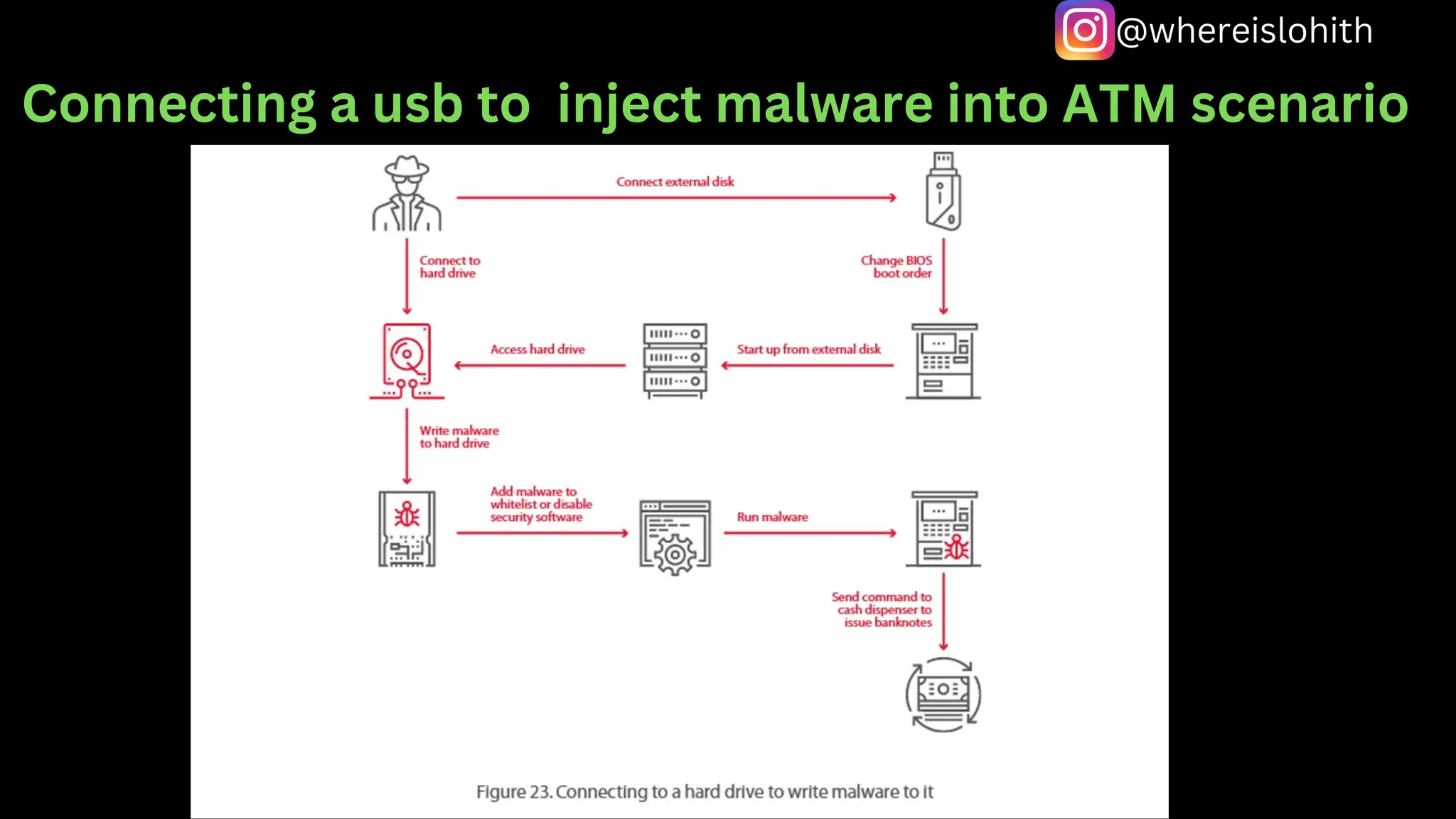
This document outlines various aspects of Automated Teller Machines (ATMs), including their functions, cash capacity, and security vulnerabilities. It details different types of ATM hacking methods, such as skimming, jackpotting, and network attacks, noting the high level of vulnerability in many tested machines. Researchers discovered that a significant percentage of ATMs lack adequate security measures, making them susceptible to various forms of fraud and attacks.